Xbox Privilege Escalation is a serious security vulnerability on Xbox gaming platforms that could allow an attacker to escalate user privileges and gain system-level access through gaming Service components that aren’t part of default installations, using directory change processes against Microsoft to gain system-level access through directory change manipulation attacks. We will explore its details, its impact, and any mitigations.
Introduction
Microsoft’s Xbox gaming platform has quickly become one of the world’s favourite entertainment hubs, yet like all software, it is vulnerable to security vulnerabilities. One such latest flaw found in Xbox by Filip Dragović Privilege Escalation, which allows an attacker to elevate privileges and take control over a system by exploiting Gaming Service components, which are not default services but can be installed onto systems.
Understanding Gaming Service
The Gaming Service is an essential component that supports various gaming-related functionalities on Xbox. It is responsible for managing game saves configuration files and other gaming-related files. When users attempt to change directories, when opening specific files within that directory the Gaming Service attempts to open them using MoveFileW API calls in impersonation of calling user.
Exploitation of Vulnerability
The Xbox Privilege Escalation vulnerability arises from the Gaming Service’s behaviour during the directory change process. If an access denied error arises during move operation, if successful move operation reverts impersonation and performs move as a system instead. Low-privileged users can exploit this behaviour by manipulating target directory naming conventions, dropping DLL files that might contain their desired code, and adding deny delete ACL for themselves. So, when the Gaming Service attempts to move the directory, it will fail while impersonating the user but succeed when operating system’s impersonation rather than user impersonation and succeed when operating under system control instead.
Exploit in Action
To better understand how an exploit works, a proof-of-concept (PoC) was constructed. The PoC involves fooling the Gaming Service into believing its installation directory is safe but then redirecting it just before moving the folder – leading it into unintentionally loading an arbitrary DLL file as the system and thus giving an attacker elevated privileges for malicious code execution. Microsoft claims this exploit crosses no security boundaries.
Practical (PoC)
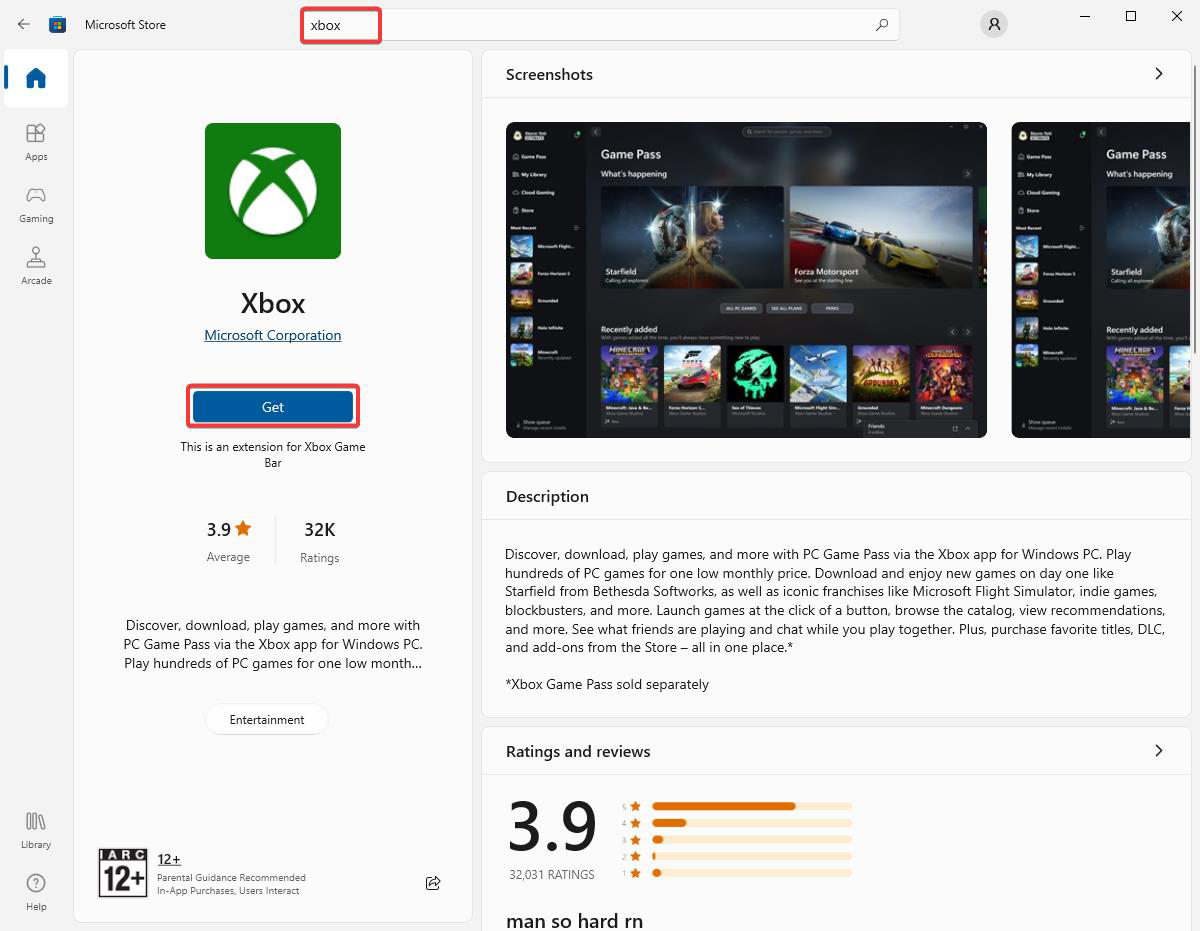
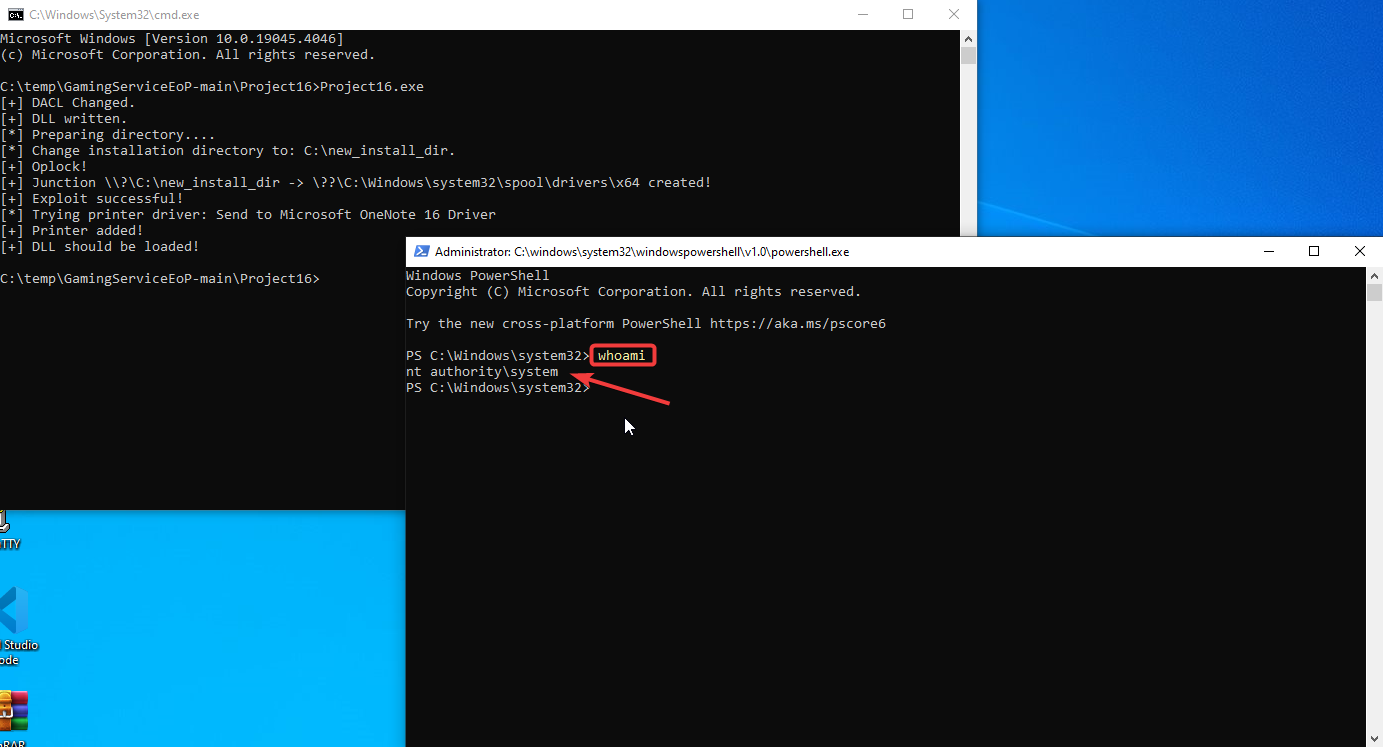
A low-privileged user can install Xbox from the Microsoft Store and exploit it to escalate privileges and become an administrator.
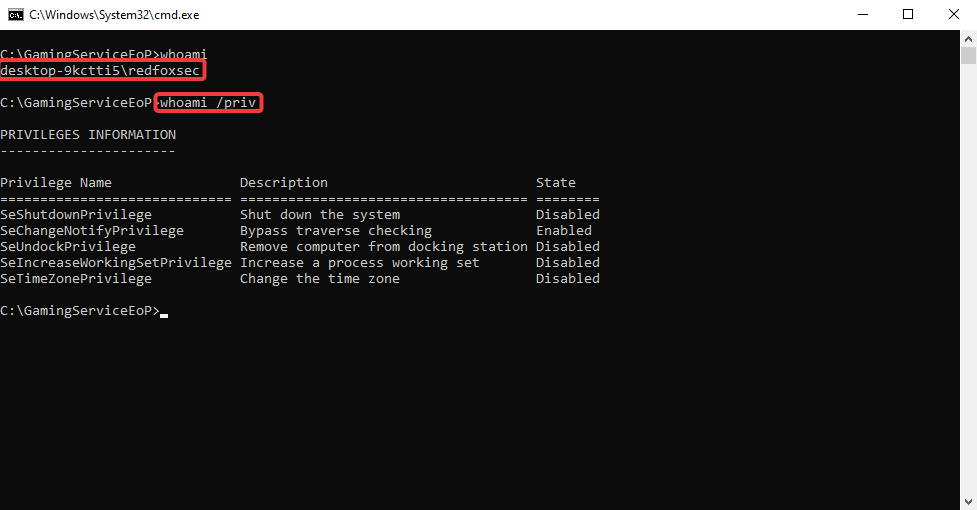
Installing Xbox as low-privileged user redfoxsec.
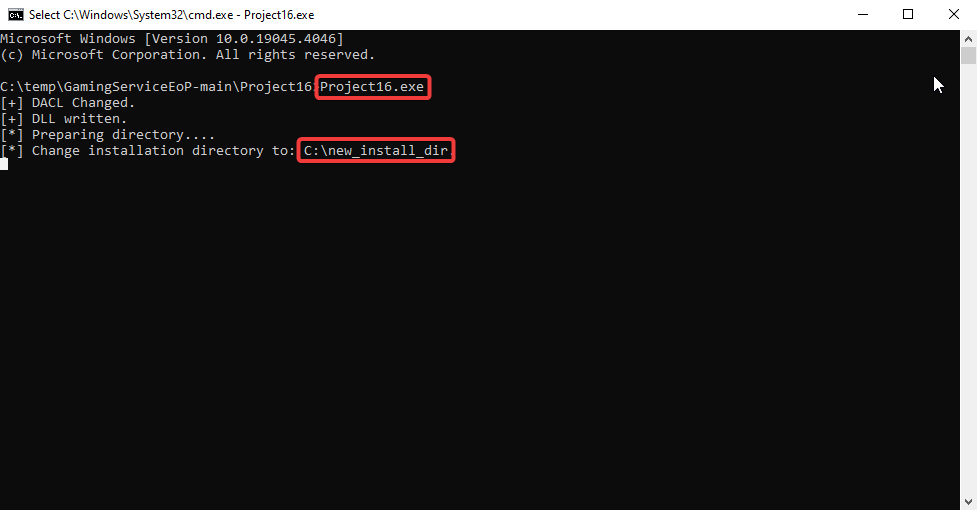
After installation of Xbox, running “Project16.exe” exploit and changing the following Xbox Installation directory.
Exploit link:- https://github.com/Wh04m1001/GamingServiceEoP
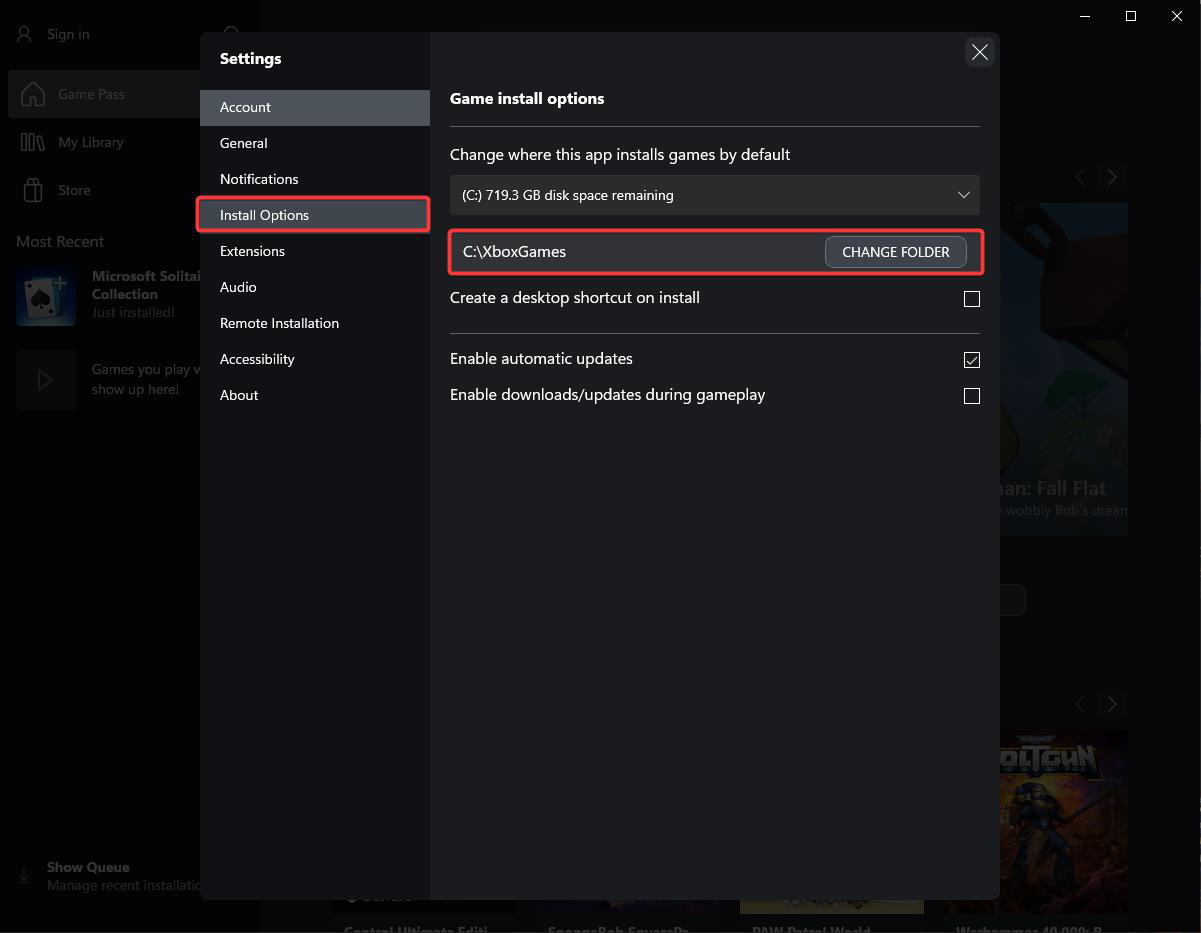
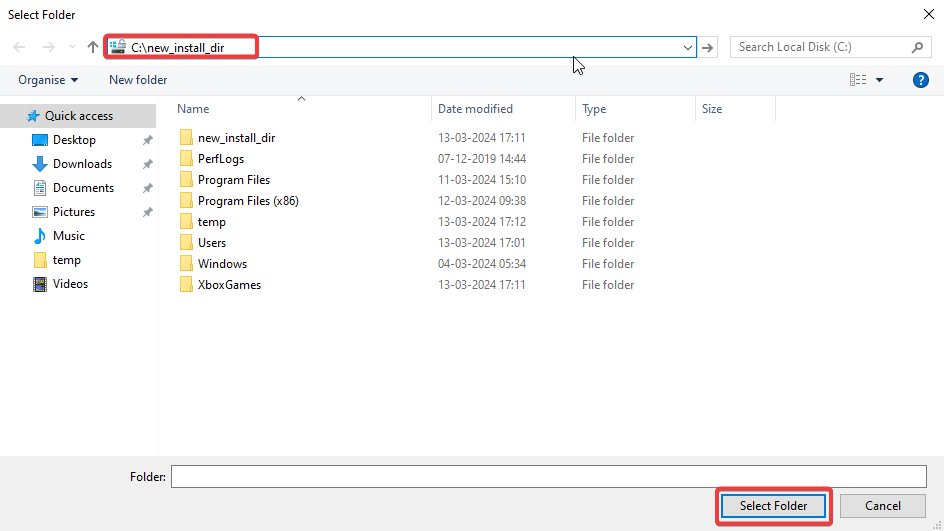
Follow the steps to Change Xbox Installation directory.
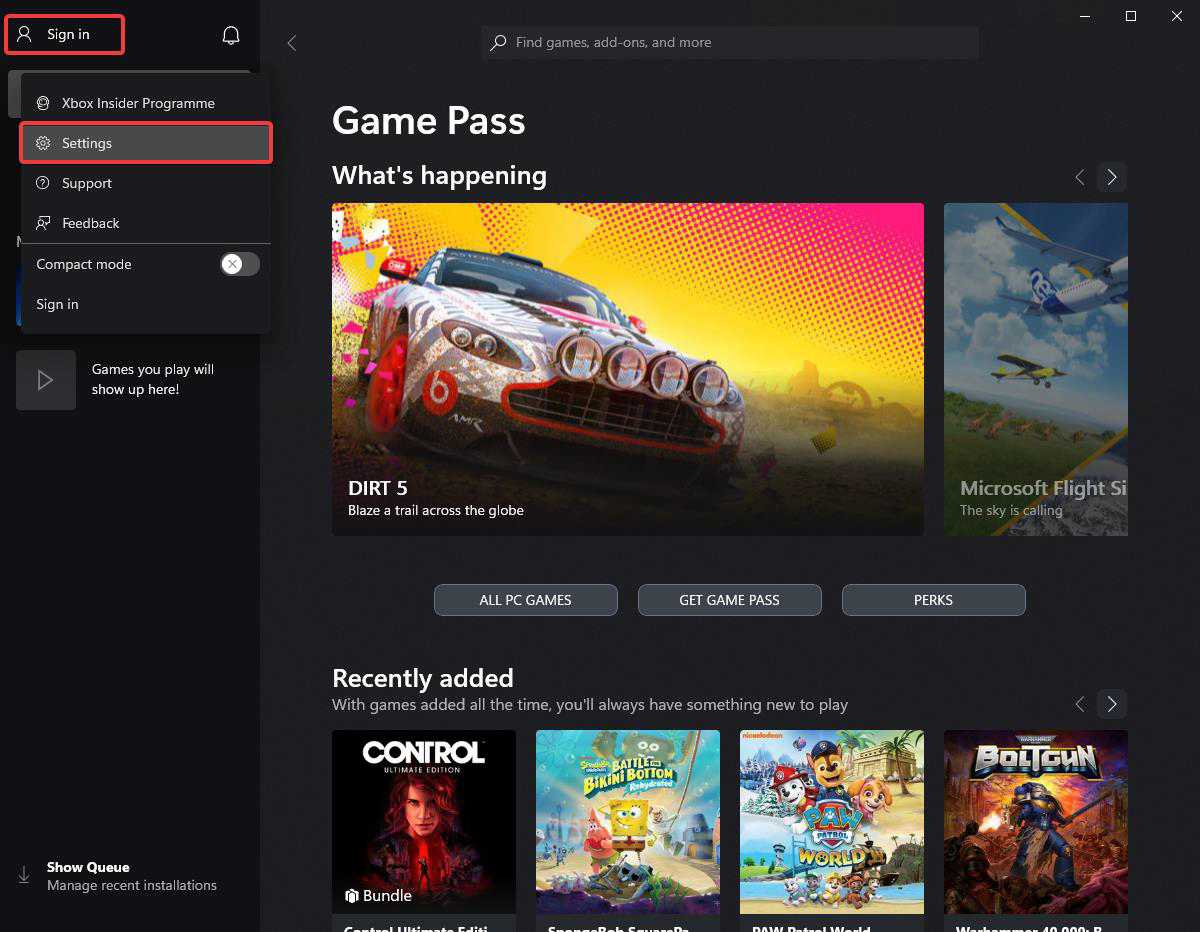
Open Xbox, click on “Sign In” and then open Settings.
After that, click on “Install Options” and “CHANGE FOLDER” to “C:\new_install_dir”.
After changing the Installation directory, script get executed and spawned new cmd as “NT AUTHORITY\SYSTEM”.
PoC and Security Boundaries
The Proof-of-Concept shows how a low privileged user can exploit the Spooler Service to load an arbitrary DLL file as system-wide code by tricking the Gaming Service and redirecting the folder to another directory.
Impact and Risks
It’s Exploiting the Xbox Privilege Escalation vulnerability could have serious repercussions. An attacker with elevated privileges could gain control of a system, leading to unauthorized access, data theft, and further compromise. Microsoft has yet to take any measures to address this vulnerability.
Mitigations
As of now, Microsoft commented on this issue that, no security boundary is crossed, following Twitter post of Filip Dragović found that Microsoft think that this is a valid issue, as of now of no mitigation is provided by Microsoft nor any CVEs.
Note: Microsoft fixed this vulnerability https://msrc.microsoft.com/update-guide/vulnerability/CVE-2024-28916
Redfox Security will recommend updating the latest version of Xbox as soon as possible when they will give new update and restrict actions of low-privileged user to not make any changes into HOST, and if possible, remove Xbox software from system.
TL; DR
The Xbox Privilege Escalation Vulnerability highlights the importance of ensuring a safe gaming environment for users. Although this vulnerability poses risks, Microsoft responded, which showed its commitment to addressing security concerns. Users can enjoy Xbox gaming experiences while minimizing adverse impacts from vulnerabilities by remaining vigilant and following security practices.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.”