Firmware customization is a crucial aspect of hardware hacking and cybersecurity exploration. With the right tools and techniques, you can unlock the full potential of embedded systems and push the boundaries of innovation. In this tutorial, we’ll walk through the step-by-step process of firmware customization using the ESP-01 module and the Ch341A programmer tool.
Setting Up the Hardware
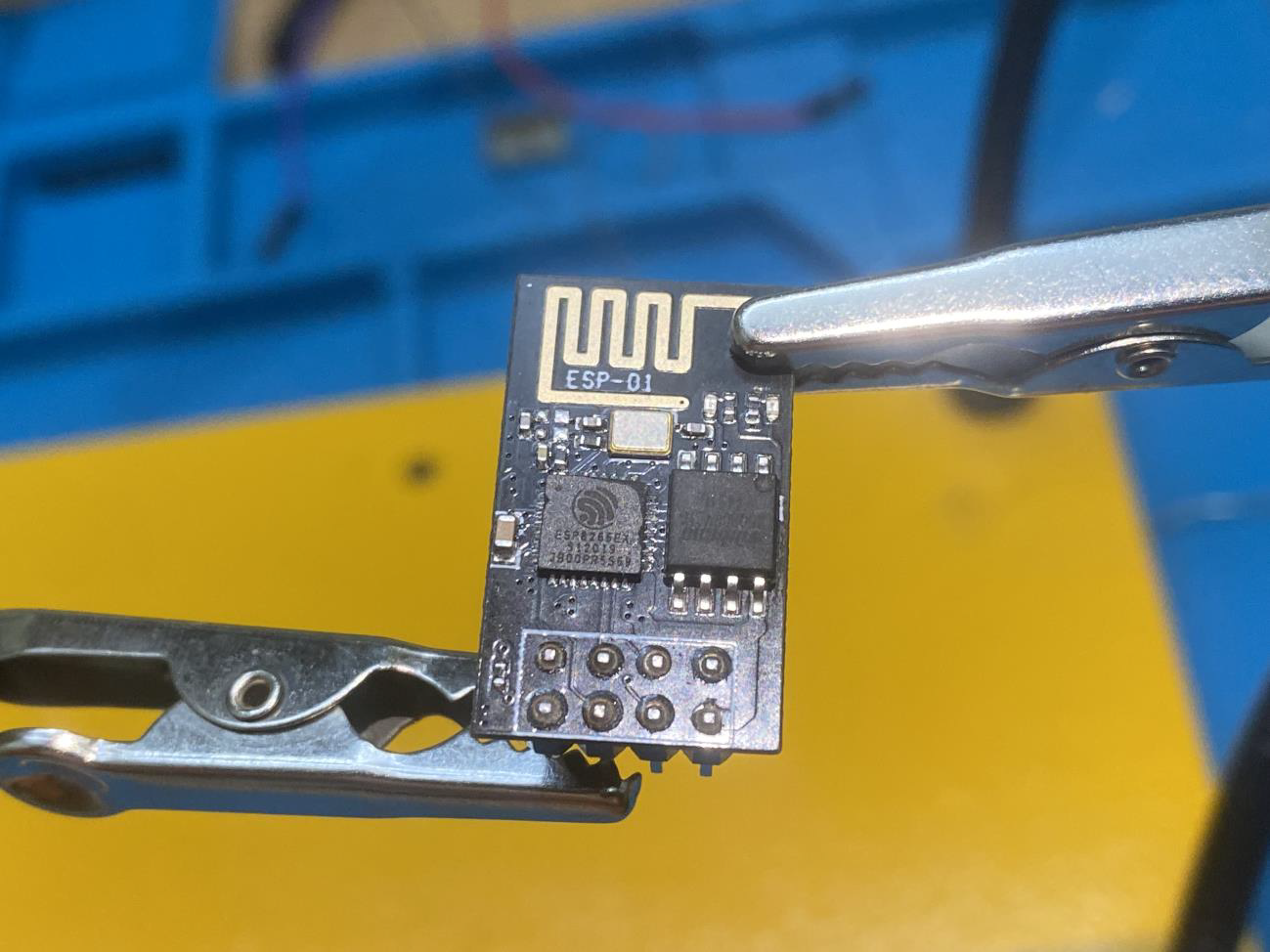
ESP-01 Module:
The ESP-01 module is indeed a compact Wi-Fi module that offers a variety of features for IoT projects. Here’s a more detailed overview:
- Power Supply: The ESP-01 requires a 3.0 to 3.6V power supply.
- Microcontroller: It has a built-in microcontroller and can be programmed directly, acting as a standalone unit.
- Connectivity: Supports 802.11 b/g/n Wi-Fi standards and operates at a frequency of 2.4 GHz.
- Security: Provides WPA/WPA2 security for Wi-Fi connections.
- GPIO Pins: Offers General Purpose Input/output (GPIO) pins for interfacing with other devices.
- Programming: Can be programmed using AT commands or through the Arduino IDE with the appropriate firmware.
- Modes: Operates in multiple modes, including Access Point (AP) and Station (STA).
- Memory: Comes with 1MB of memory, which is sufficient for many simple applications.
Ch341A Programmer:
The CH341A Programmer is a versatile USB interface chip that can emulate various communication protocols such as UART, I2C, SPI, and JTAG. It’s commonly used for programming EEPROM and BIOS chips, as well as debugging serial devices. Here are some essential details:
- Compatibility: Works with a range of operating systems including Windows (7 SP1 and up), Android (3.x and up), Linux (2.6.25 and up), and MacOSX (10.12.x and up).
- Supported Chips: It can program a variety of chips including the 24XXX series EEPROM and 25XXX series SPI Flash.
- Software: Various software tools are available for use with the CH341A, such as ASProgrammer, Neo Programmer, and CH341A Programmer.
- Connectivity: Typically connects to the PC via USB and to the chip via a SOIC8 SOP-8 Test Clip or a ZIF (zero insertion force) socket.
- Voltage Support: It often includes a 3.3V voltage regulator to ensure compatibility with chips that require this voltage.
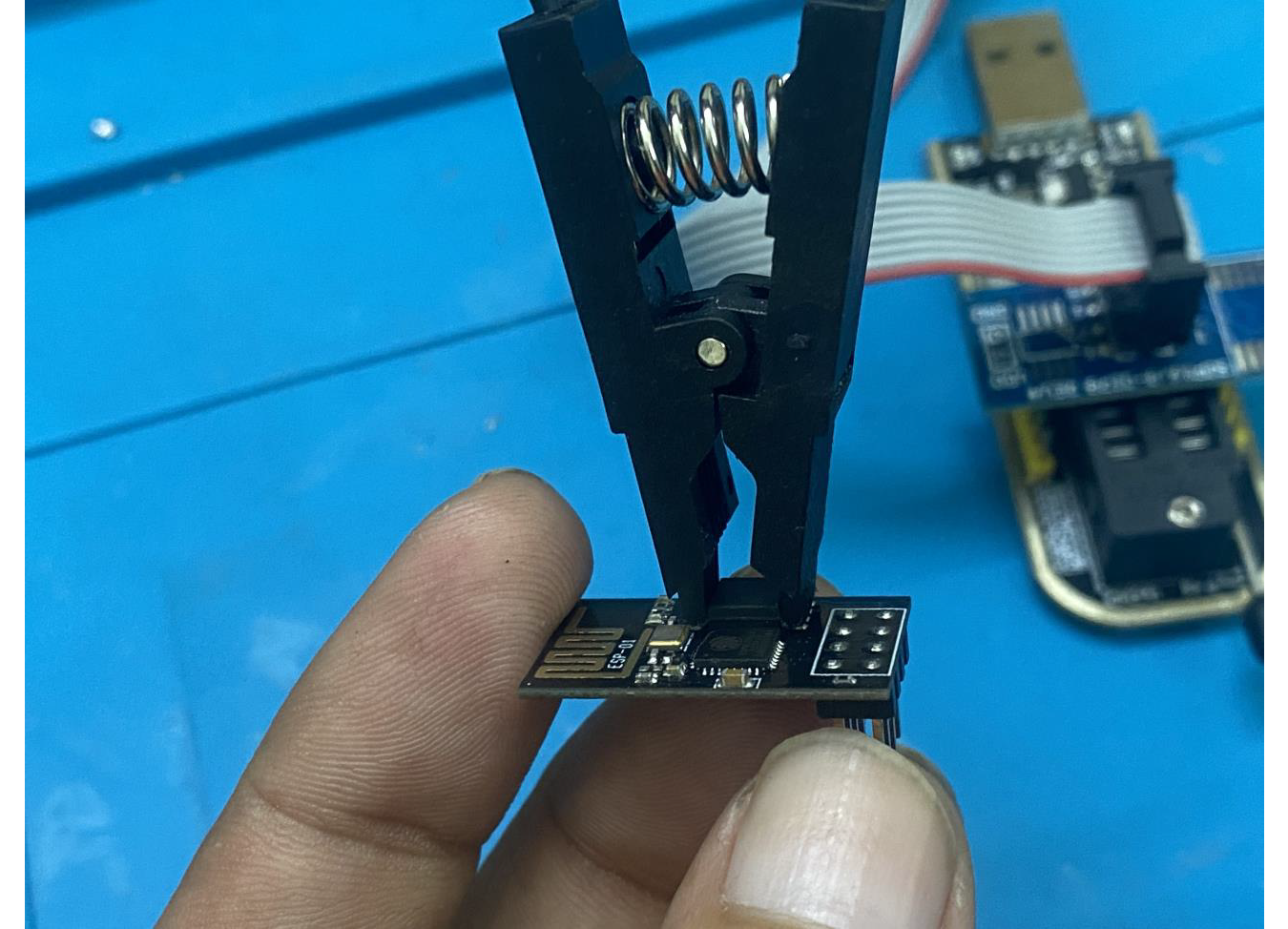
Ch341A-ESP-01 Connection:
Establish a connection between the ESP-01 module and the Ch341A programmer ensuring proper wiring for communication.
Software Setup
AsProgrammer / SNANDer / NeoProgrammer:
AsProgrammer is a software utility that provides a graphical interface for programming a variety of memory chips through different protocols like SPI, I2C, and MicroWire. It supports a range of devices, including CH341A, UsbAsp, AVRISP-MKII, and others. Initially developed for the UsbAsp, it has evolved to support additional programmers and is widely used due to its open-source nature and active maintenance. It’s particularly useful for tasks such as reading, erasing, and writing EEPROM and BIOS chips.
https://www.onetransistor.eu/2018/11/use-ch341a-with-asprogrammer-on-windows.html
Setup
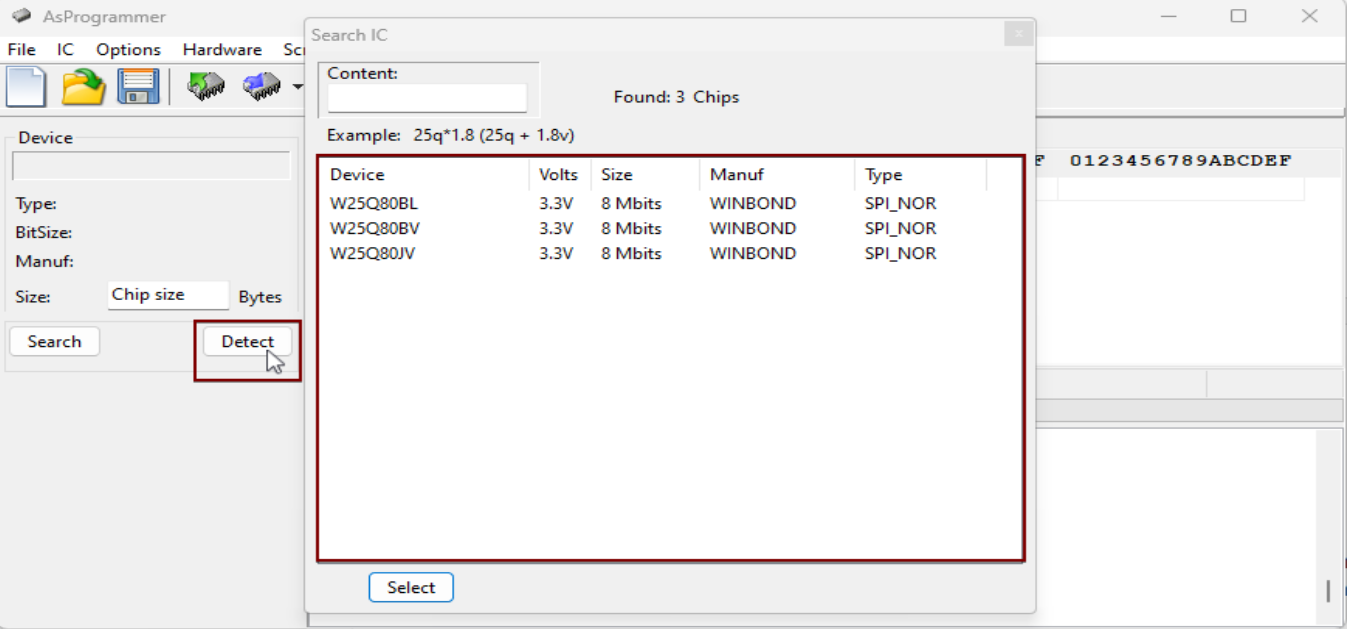
Configure the programming software to establish a connection with the ESP-01 module. Set the appropriate communication parameters and ensure proper detection of the device.
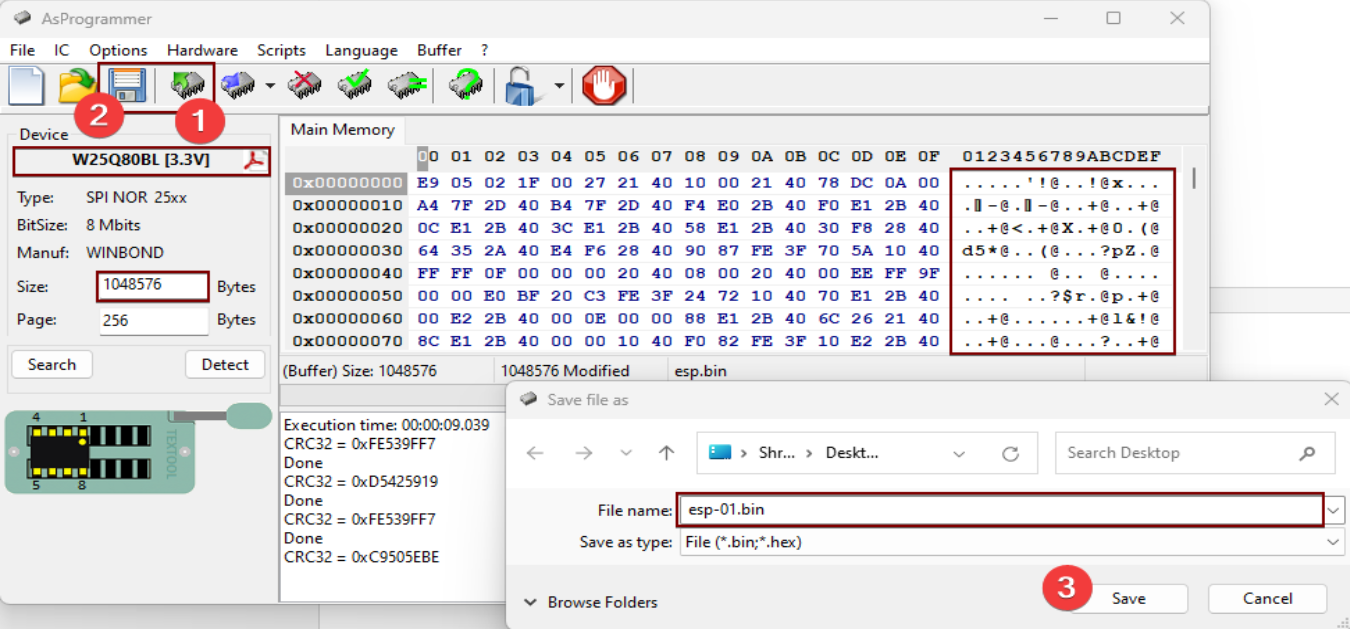
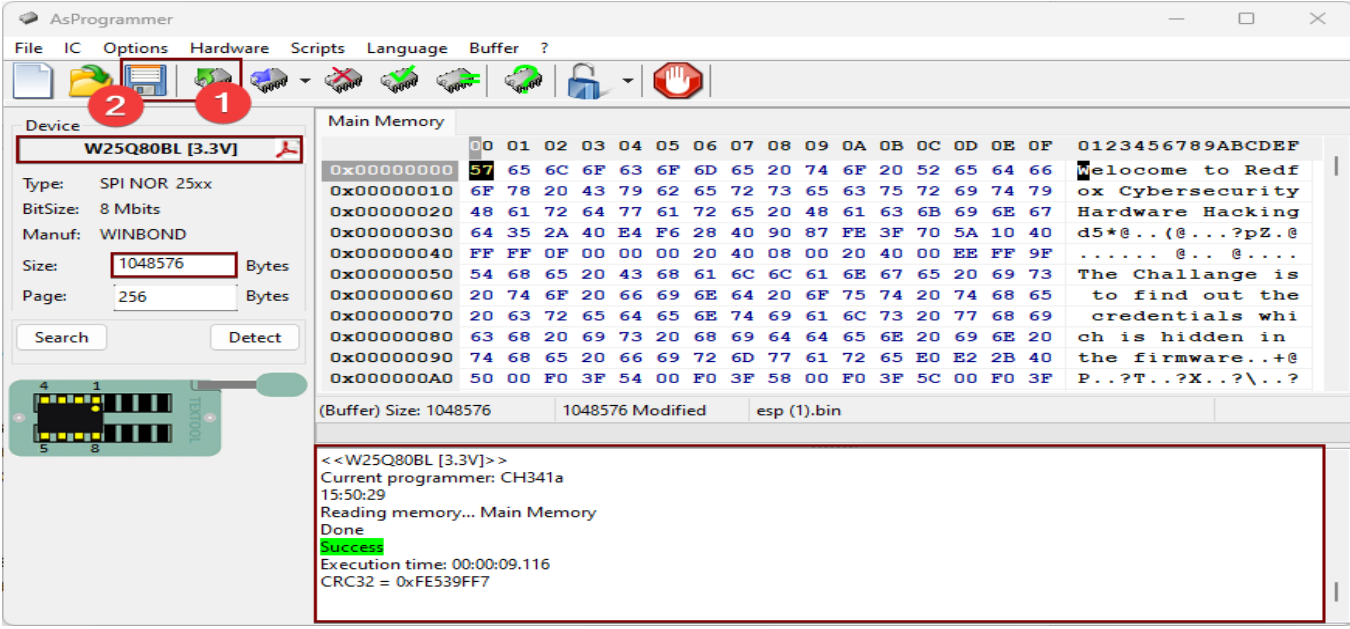
Reading and Dumping Firmware
Read Bin File and Dump: Use programming software to read the binary firmware file from the ESP-01 module and create a backup of the original firmware for further analysis and modification.
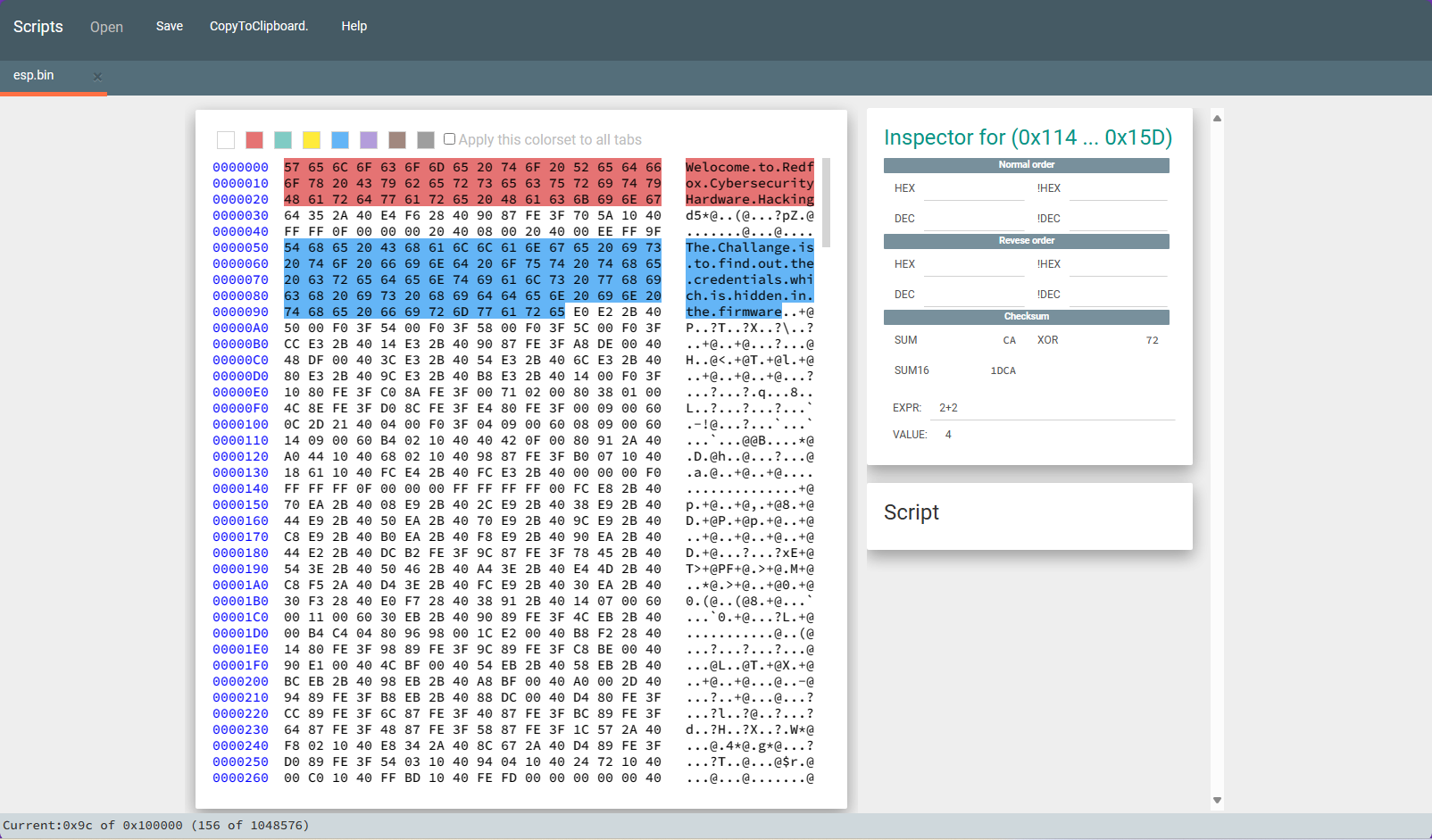
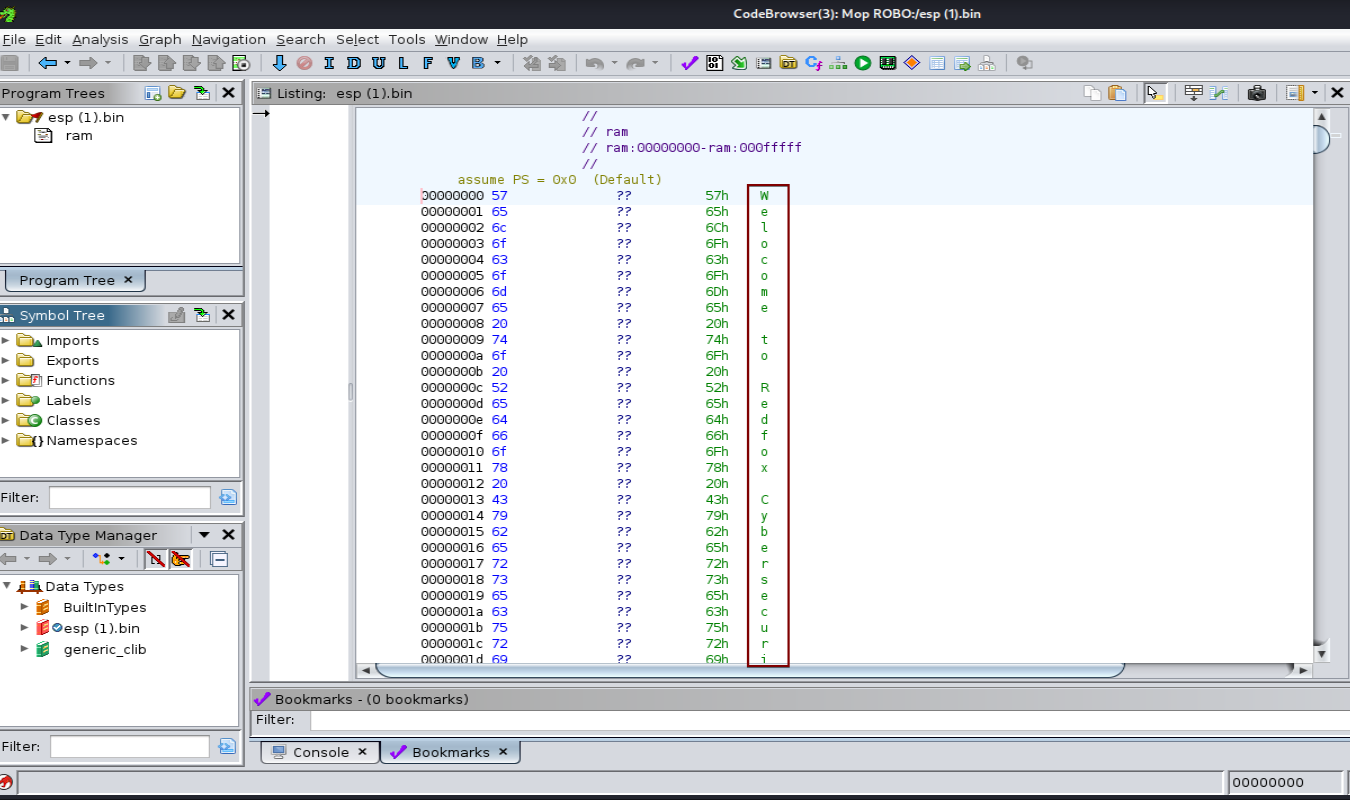
Extract and Check Integrity:
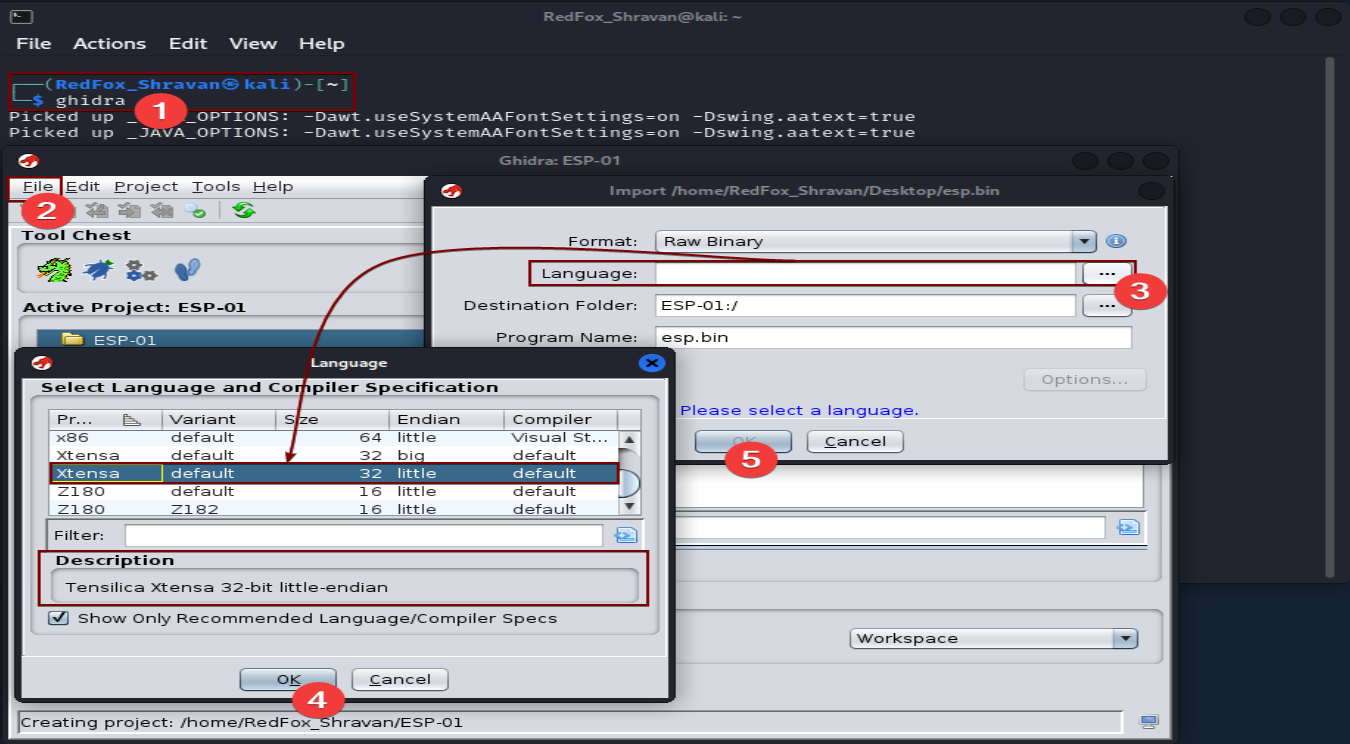
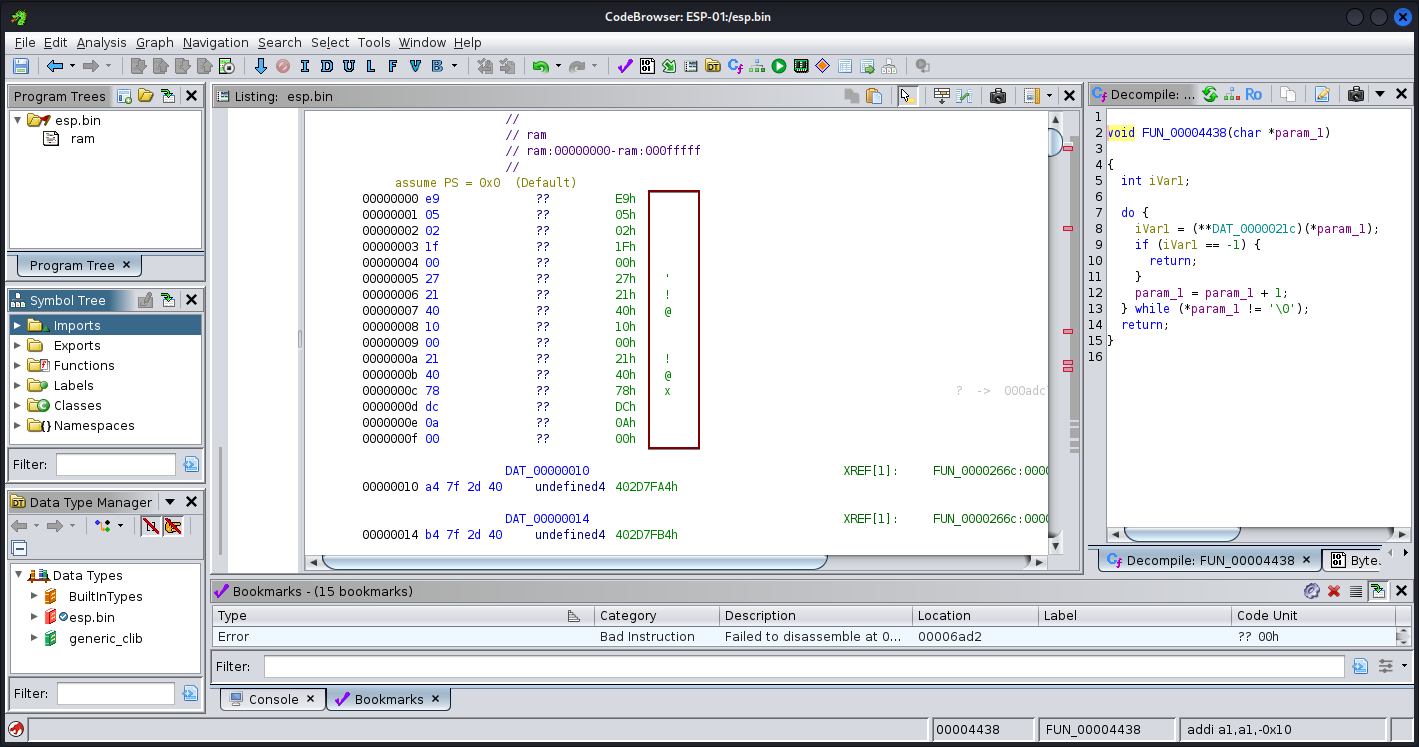
For the analysis of firmware files, it is recommended to extract it or use reverse engineering tools for a thorough binary file analysis. One such tool is Ghidra, but it requires basic knowledge of assembly language. The language selection can be found in the datasheet of the flash chip of the EEPROM chipset. Alternatively, we can use binwalk to determine the file structure and the little or big endian of the bin file.
Firmware Modification
- Online Hex Editing: To modify, Utilize tools like Hex-Works or HexEd.it modify. These tools allow you to edit the firmware’s hexadecimal representation, enabling you to change variables, insert custom code, or add sensitive information for analysis.
https://hexed.it/
Online Hex editor tool (hex-works.com)
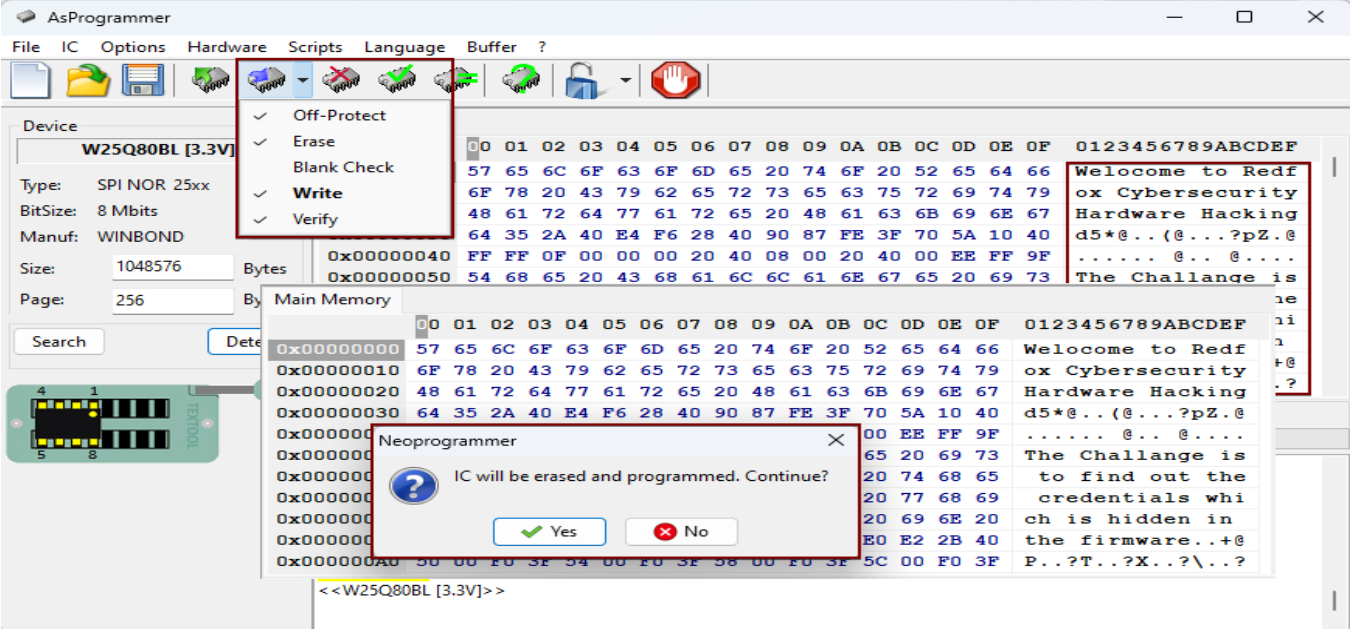
Write Modified Firmware: After completing the required modifications to the firmware, save the altered binary file securely. Utilize the designated programming software to write the modified firmware back onto the ESP-01 module. During this process, ensure a seamless write operation by carefully following the software instructions and confirming successful completion. It’s vital to verify the integrity and functionality of the newly programmed firmware post-writing. This can be achieved through comprehensive testing procedures, including functional tests, stress tests, and compatibility checks. By confirming the integrity of the firmware, any potential errors or inconsistencies can be detected and rectified, ensuring the reliability and effectiveness of the updated firmware.
Cross-Verification and Analysis
 Re-Read Bin File: After disconnecting and reconnecting the ESP-01 module, carefully re-read the firmware binary file to validate that the modifications were successfully applied. Additionally, conduct thorough checks to verify the integrity and functionality of the firmware. This may include examining key features, testing various functionalities, and ensuring compatibility with target devices or systems. By thoroughly evaluating firmware, any potential issues or discrepancies can be quickly identified and addressed ensuring optimal performance and reliability of the system.
Re-Read Bin File: After disconnecting and reconnecting the ESP-01 module, carefully re-read the firmware binary file to validate that the modifications were successfully applied. Additionally, conduct thorough checks to verify the integrity and functionality of the firmware. This may include examining key features, testing various functionalities, and ensuring compatibility with target devices or systems. By thoroughly evaluating firmware, any potential issues or discrepancies can be quickly identified and addressed ensuring optimal performance and reliability of the system.
Analysis with Ghidra: Use reverse engineering tools like Ghidra to analyse the modified firmware further. Cross-verify the changes made and assess the impact on the device’s behavior and functionality.
TL;DR
Utilizing cutting-edge technologies like the Chipzilla Hacker and ESPi-Oh-Uno Module into firmware development could transform our experience with devices. By taking advantage of their power, developers can bring creativity and innovation to their projects while crafting firmware that not only functions seamlessly but also delight users with its special features and capabilities.
With the Chipzilla Hacker, developers gain access to powerful debugging and reverse engineering capabilities, enabling them to identify and rectify vulnerabilities in their firmware more efficiently than ever before. Additionally, the ESPi-Oh-Uno Module offers seamless integration with IoT devices, allowing firmware to interact with the physical world in ways previously unimaginable.
By harnessing the Hex-Works platform, developers can further enhance their firmware with custom hex-based animations and effects, adding a visually stunning dimension to the user experience. Hex-Works gives developers tools that allow them to bring firmware alive through vibrant LED patterns or immersive gaming elements that were once reserved only for science fiction novels.
In conclusion, the combination of the Chipzilla Hacker, ESPi-Oh-Uno Module, and Hex-Works opens a world of possibilities for firmware developers. By adopting these technologies, developers can push the limits of what is possible – creating firmware that meets both functional requirements and delights and engages users on an entirely different level. The future of firmware development is bright, and with these tools at our disposal, the possibilities are truly endless.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.”