This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognizing you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Active Directory Security Assessments
Overview
Active Directory (AD) often holds the keys that grant ultimate access to an organization’s most valuable assets. They store attributes, objects and policies which protect, organize, and manage IT information, network resources, policies, security configurations and other important details within an organization’s infrastructure. A misconfigured Active Directory can demolish an organization’s security posture, often leading to a domain compromise.
At Redfox Security, we perform an Active Directory Security Assessment by enumerating and analyzing datasets that include users, groups, computers, domains, domain controllers, trusts, forests, password policies, ACLs, GPOs, shares and several other touchpoints that adversaries or malicious insiders can exploit. These activities reveal crucial details on the security hygiene of an organization’s Active Directory environment and are aimed toward the smooth and secure functioning of IT operations.
What is an Active Directory Security Assessment?
An Active Directory security assessment is a comprehensive evaluation of the security controls, configurations, and permissions within your AD environment. It aims to identify potential weaknesses and misconfigurations that could lead to unauthorized access, data breaches, or compromise of sensitive information.
During an Active Directory security assessment, our experienced team of cybersecurity professionals performs a thorough analysis of your AD infrastructure, focusing on areas such as user accounts, group policies, permissions, domain controllers, trust relationships, and authentication mechanisms. By conducting in-depth assessments, we can identify vulnerabilities and provide actionable recommendations to strengthen the security of your Active Directory environment.
How do we carry out Active Directory Security Assessments?
Securing your Active Directory environment is crucial for protecting your organization’s critical assets and ensuring a strong security posture. Our Active Directory Security Assessment includes (but not limited to) the following:
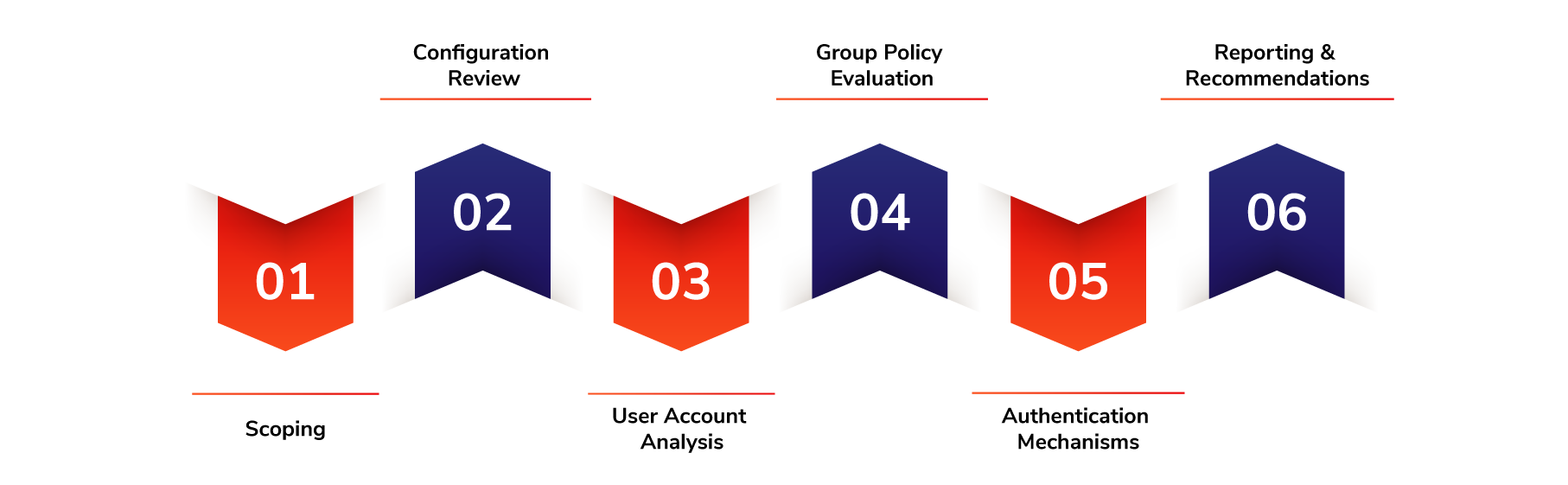
Scoping
We work closely with you to define the scope of the assessment, taking into account your specific AD environment, business requirements, and compliance needs. This ensures that our assessment aligns with your objectives.
Configuration Review
Our team conducts a comprehensive review of your Active Directory configurations, including domain controllers, group policies, domain structure, replication settings, and trust relationships. We assess the adherence to security best practices and identify any misconfigurations or weaknesses.
User Account Analysis
We analyze user accounts within your AD environment to identify potential security risks, such as weak passwords, excessive privileges, dormant or orphaned accounts, and improper access controls. This helps in strengthening the overall security of user identities and access management.
Group Policy Evaluation
Our experts assess the effectiveness of your group policies and evaluate their impact on security. We identify any misconfigurations, overly permissive policies, or conflicting settings that may introduce vulnerabilities into your AD environment.
Authentication Mechanisms
We review the authentication mechanisms used within your Active Directory infrastructure, including password policies, multi-factor authentication, and smart card usage. In addition, Active Directory Security Assessment helps identify potential weaknesses and suggests improvements to bolster authentication security.
Reporting and Recommendations
We provide a detailed report that outlines the findings of the assessment, including identified vulnerabilities, potential risks, and actionable recommendations for remediation. Our team is available to guide you through the implementation of security measures and best practices to enhance the security of your Active Directory environment.
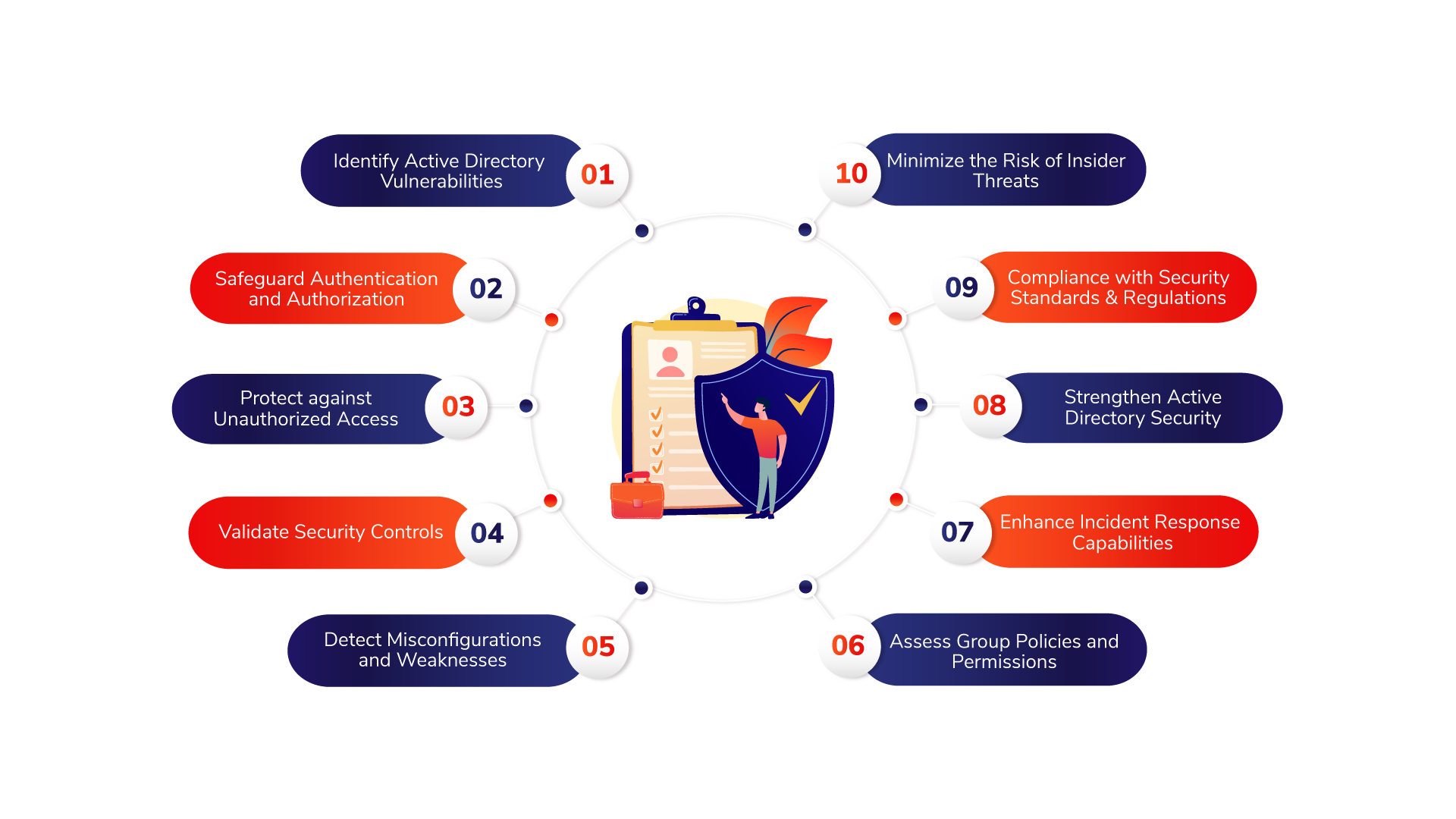
Benefits of Active Directory Security Assessments
Our Approach
![]() Fixing common AD misconfigurations
Fixing common AD misconfigurations
![]() Analyzing common AD attack vectors
Analyzing common AD attack vectors
![]() Understanding domain risk levels
Understanding domain risk levels
![]() Hardening the existing AD attack surface
Hardening the existing AD attack surface




