Smart devices have quickly become a mainstay of our homes, offering convenience and efficiency. They’re akin to new friends, capable of performing remarkable tasks. However, as with meeting new people, it’s essential to exercise caution and ensure their safety. This guide offers a friendly chat on keeping our smart devices safe, averting accidental mishaps. We’ll delve into EXPLIoT, a detective tool designed to assess whether our smart device friends are operating securely or require assistance to enhance their safety measures. Throughout this journey, we’ll equip ourselves with knowledge and strategies to foster a harmonious relationship with our digital allies.
What is EXPLIoT?
EXPLIoT is an investigation into IoT device security flaws. The concept comprises diverse approaches and strategies designed to recognize and address these weaknesses. EXPLIoT aims to identify vulnerabilities in IoT ecosystems, protocols, and devices, providing attackers with exploitable information.
Types of EXPLIoT:
- Passive Analysis: Entails observing and analyzing network traffic, device conduct, and communication protocols without directly engaging with the system.
- Active Testing: Involves actively probing IoT devices for vulnerabilities using techniques like fuzzing, injection attacks, and reverse engineering.
- Exploitation: This exploits known vulnerabilities to gain illegal access, alter data, or launch attacks on IoT networks or devices.
Common IoT Security Vulnerabilities:
- Weak Passwords: Numerous IoT devices feature default passwords that are easily guessable, rendering them susceptible to unauthorized access.
- Lack of Encryption: Without encryption, hackers can intercept and manipulate data transmitted between IoT devices and servers.
- Firmware Vulnerabilities: Outdated firmware in IoT devices can harbour security flaws, allowing attackers to gain control.
EXPLIoT Tools and Techniques:
Hackers use several tools and techniques to exploit vulnerabilities in IoT devices. They may employ specialized scanning tools like Shodan to identify vulnerable devices exposed to the internet. Hackers can utilize exploit frameworks such as Metasploit to remotely seize control of vulnerable devices once identified.
Installation Steps:
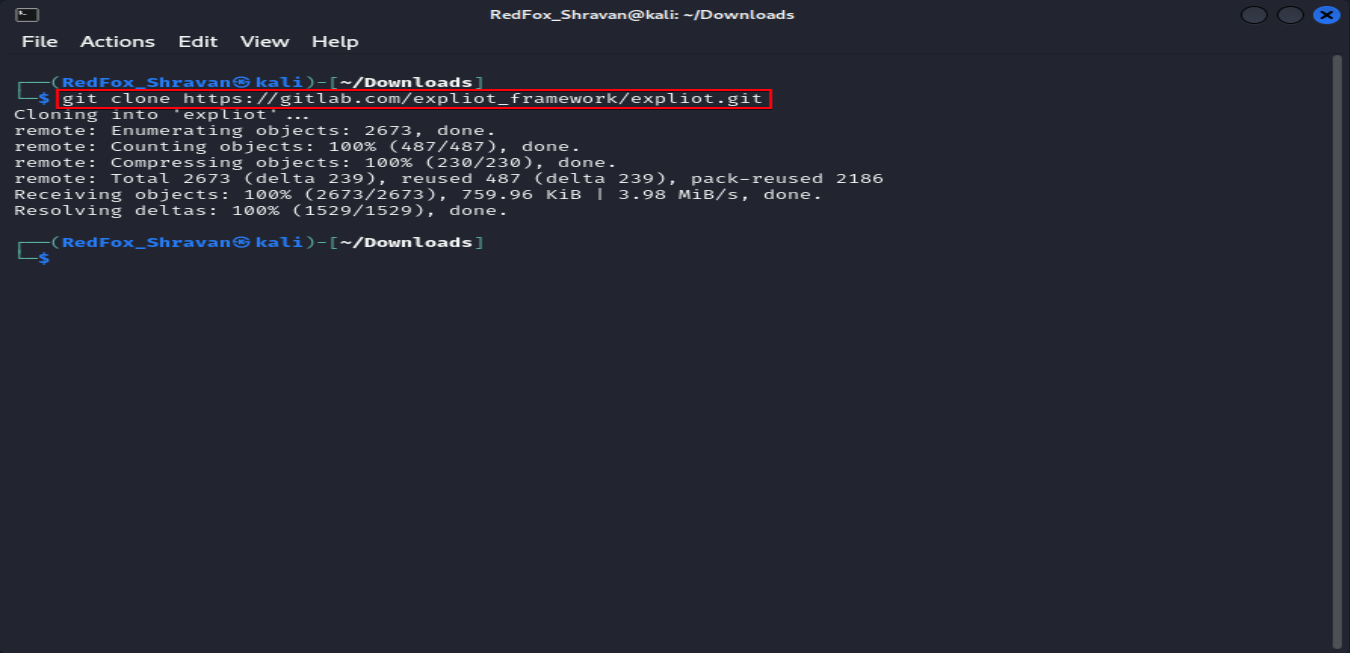
To install the EXPLIoT framework, follow these steps: The command git clone https://gitlab.com/expliot_framework/expliot.git creates a local copy of the EXPLIoT framework’s repository from GitLab.
git clone https://gitlab.com/expliot_framework/expliot.git
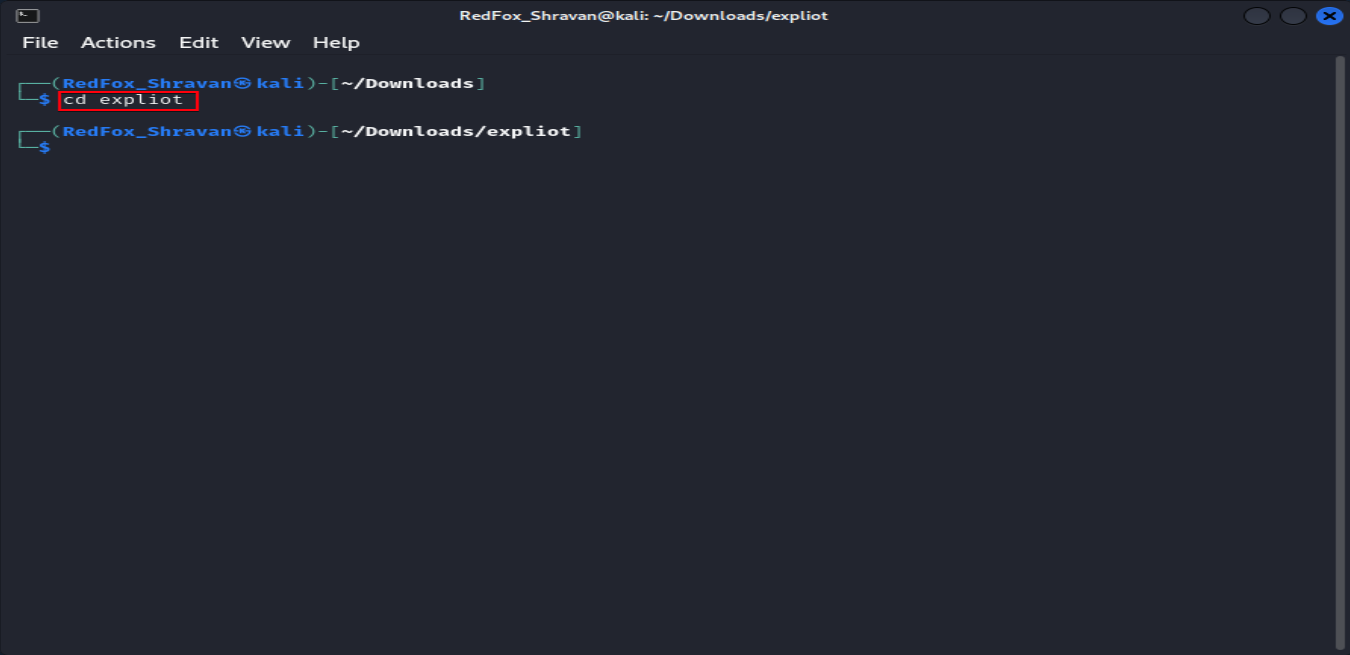
The command cd expliot changes the current directory to the ‘expliot’ directory, which is the local repository of the EXPLIoT framework.
cd expliot
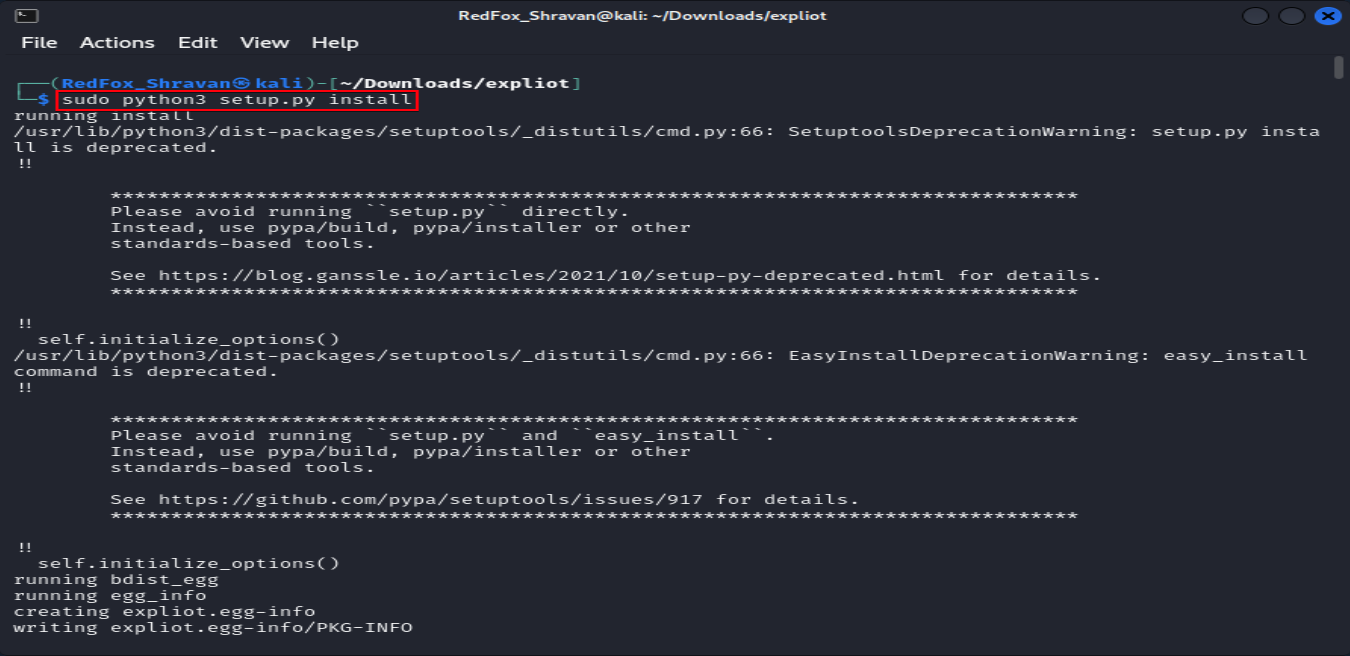
The command sudo python3 setup.py install installs the Python package in the current directory system-wide using the setup script provided.
sudo python3 setup.py install
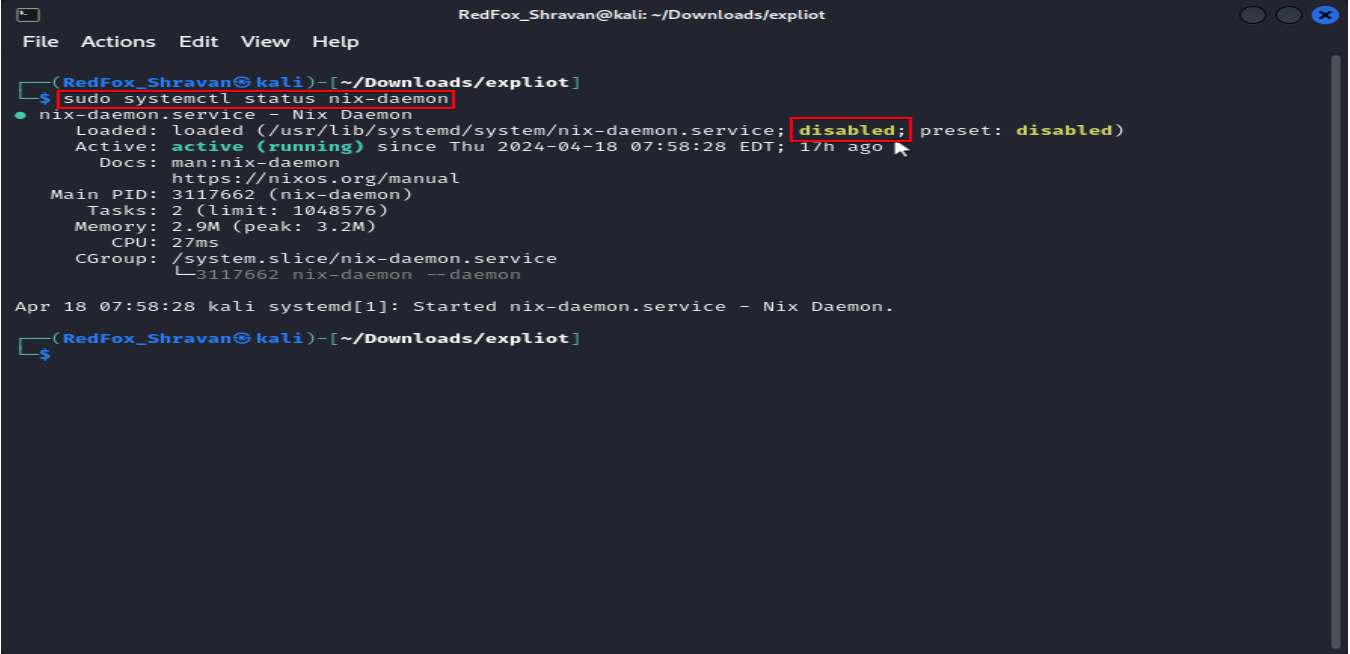
The command sudo systemctl status nix-daemon checks and displays the current status of the Nix daemon service.
sudo systemctl status nix-daemon
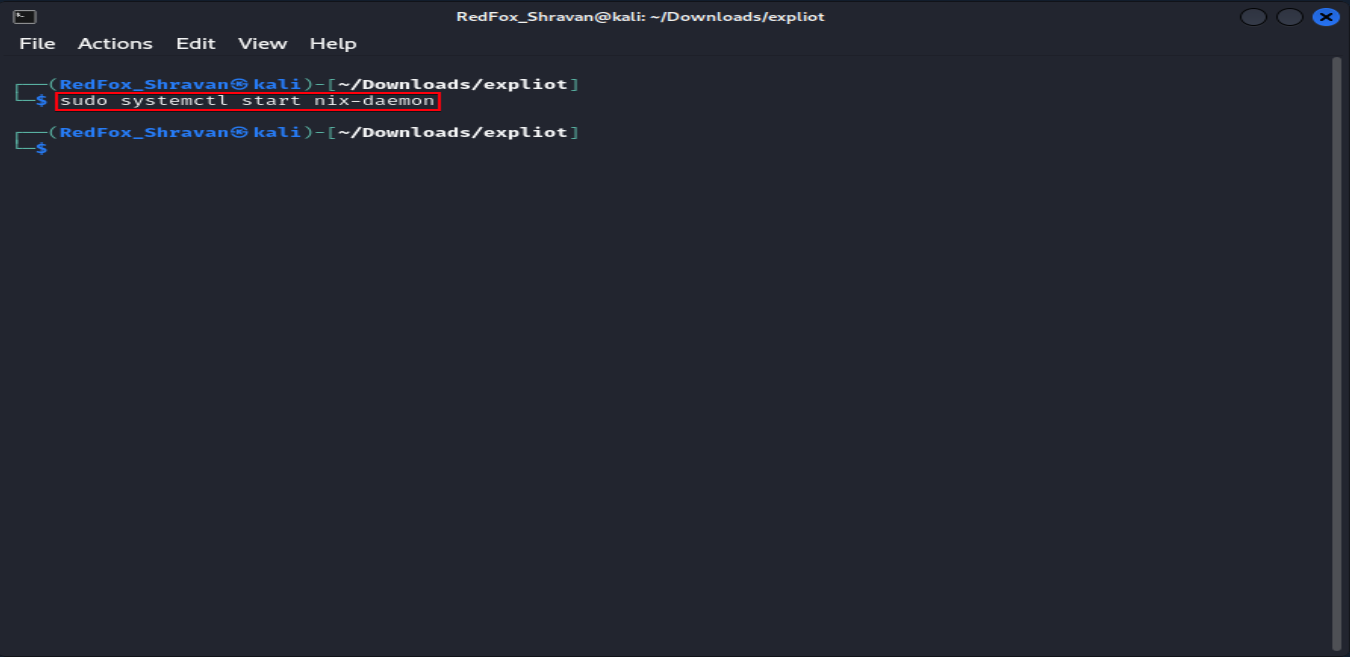
The command sudo systemctl start nix-daemon initiates the Nix daemon service, enabling it to manage system processes related to Nix.
sudo systemctl start nix-daemon
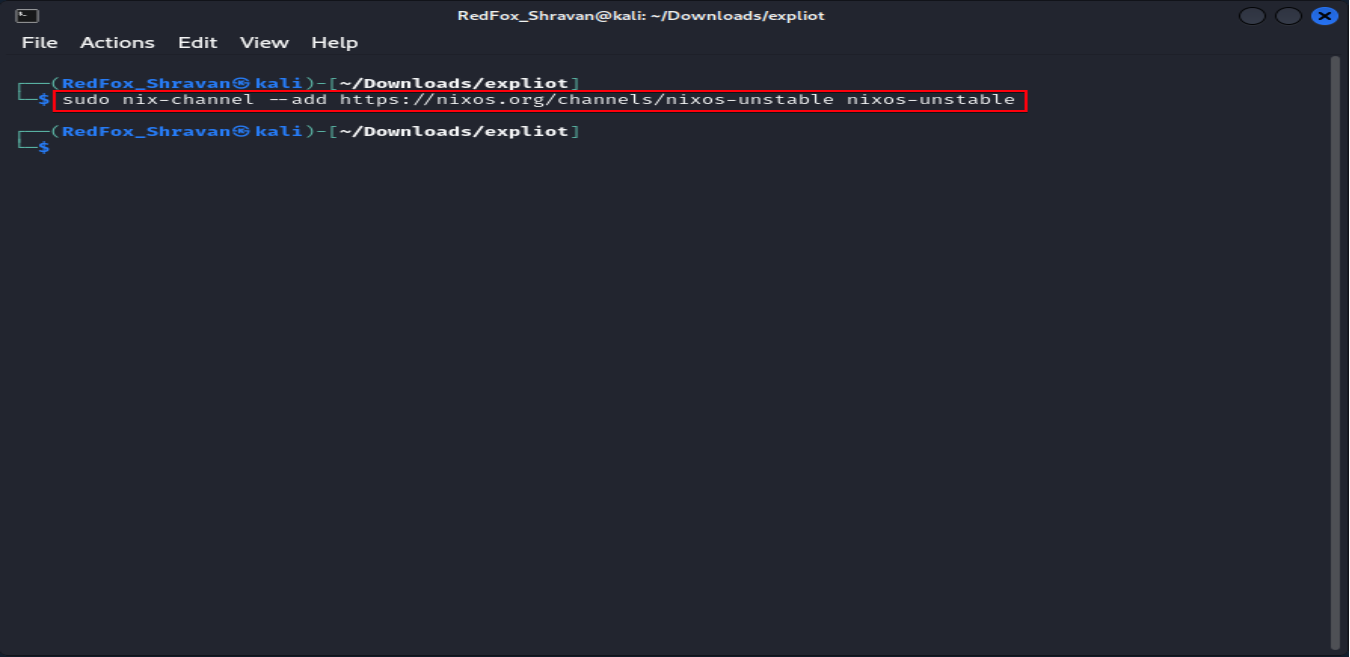
The command sudo nix-channel –add https://nixos.org/channels/nixos-unstablenixos-unstable adds the NixOS unstable channel to the Nix package manager for access to the latest packages.
sudo nix-channel --add https://nixos.org/channels/nixos-unstable nixos-unstable
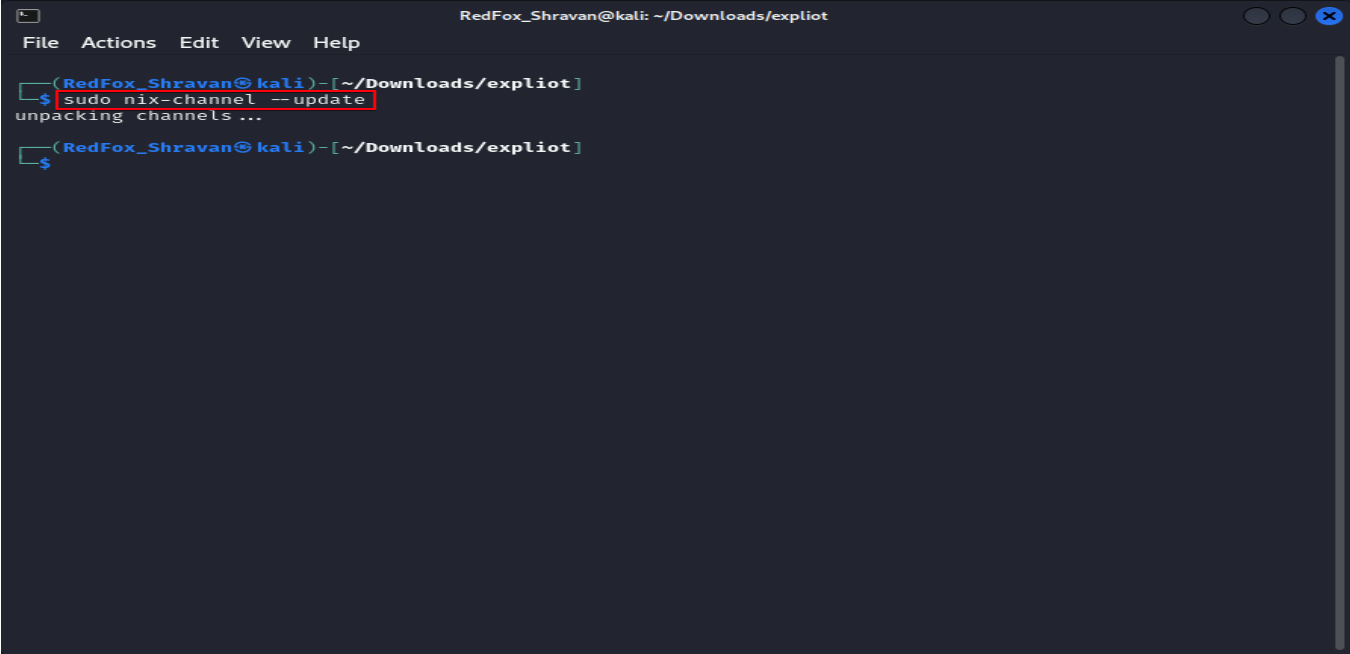
The command sudo nix-channel –update refreshes the list of packages available from the channels that the Nix package manager is subscribed to.
sudo nix-channel --update
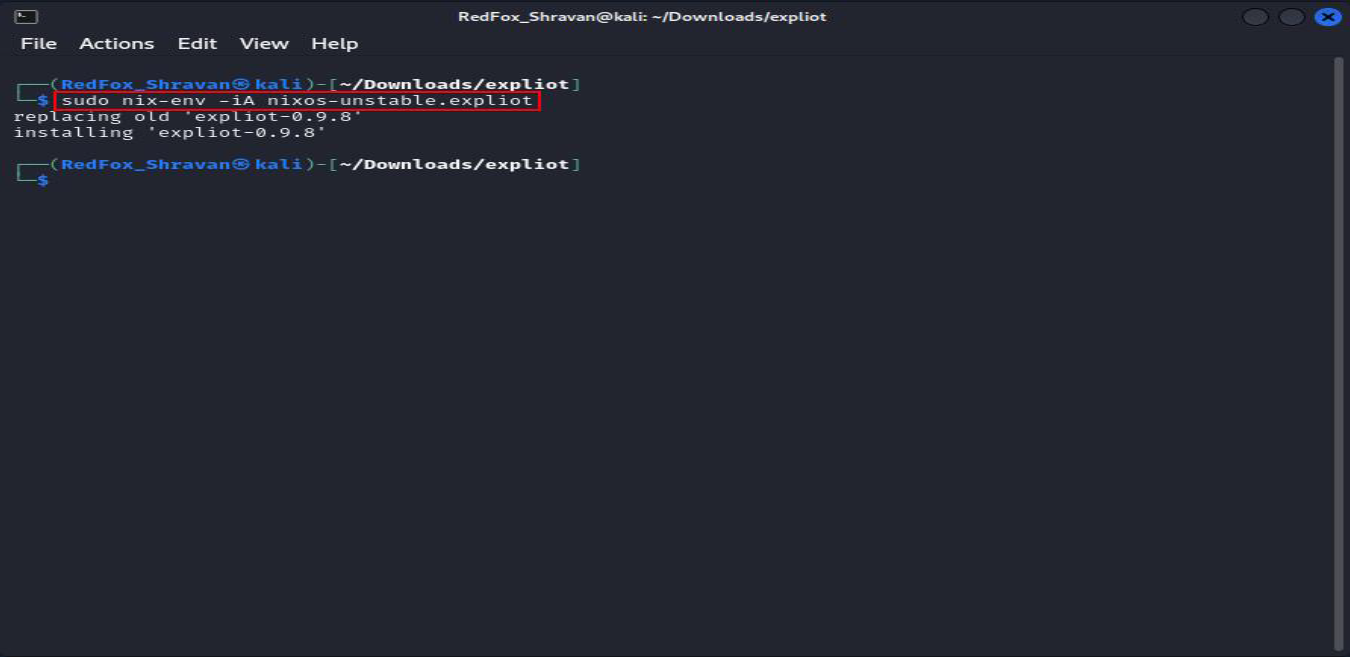
The command sudo nix-env -iA nixos-unstable.expliot installs the EXPLIoT package from the NixOS unstable channel using the Nix package manager.
sudo nix-env -iA nixos-unstable.expliot
Begin the exploit framework by configuring the necessary modules laying the groundwork for targeted security assessments and vulnerability analysis.
exploit
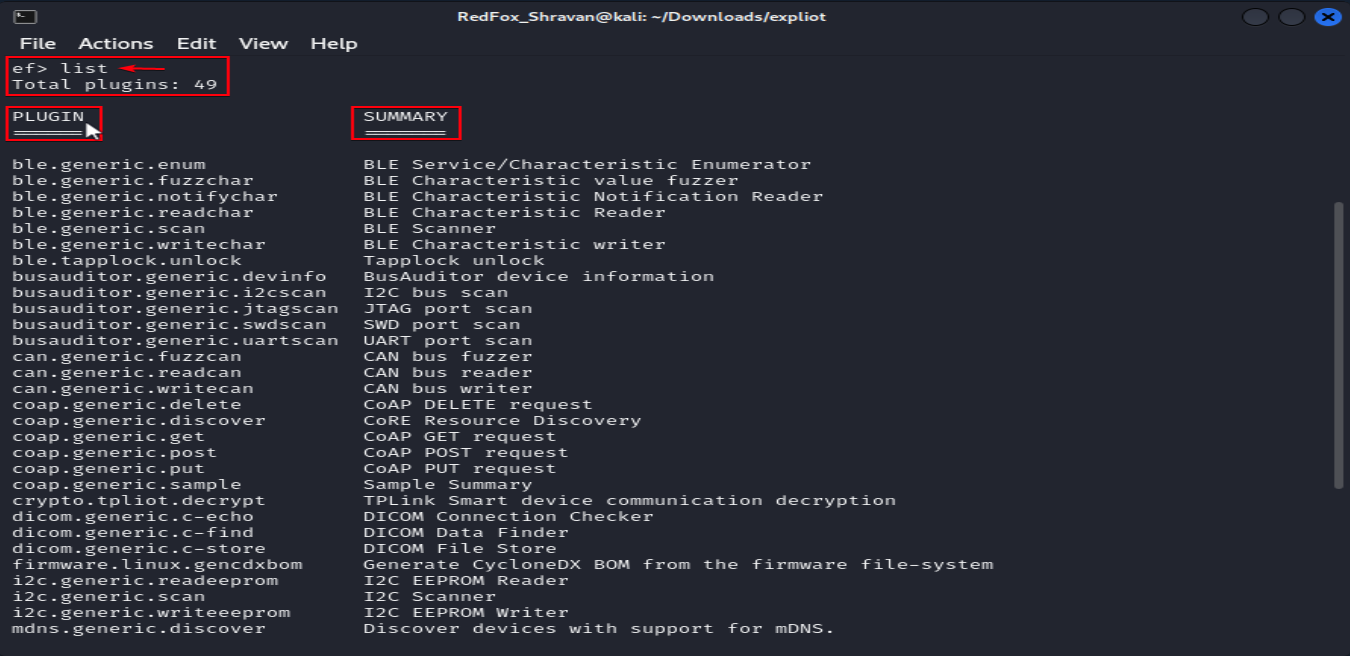
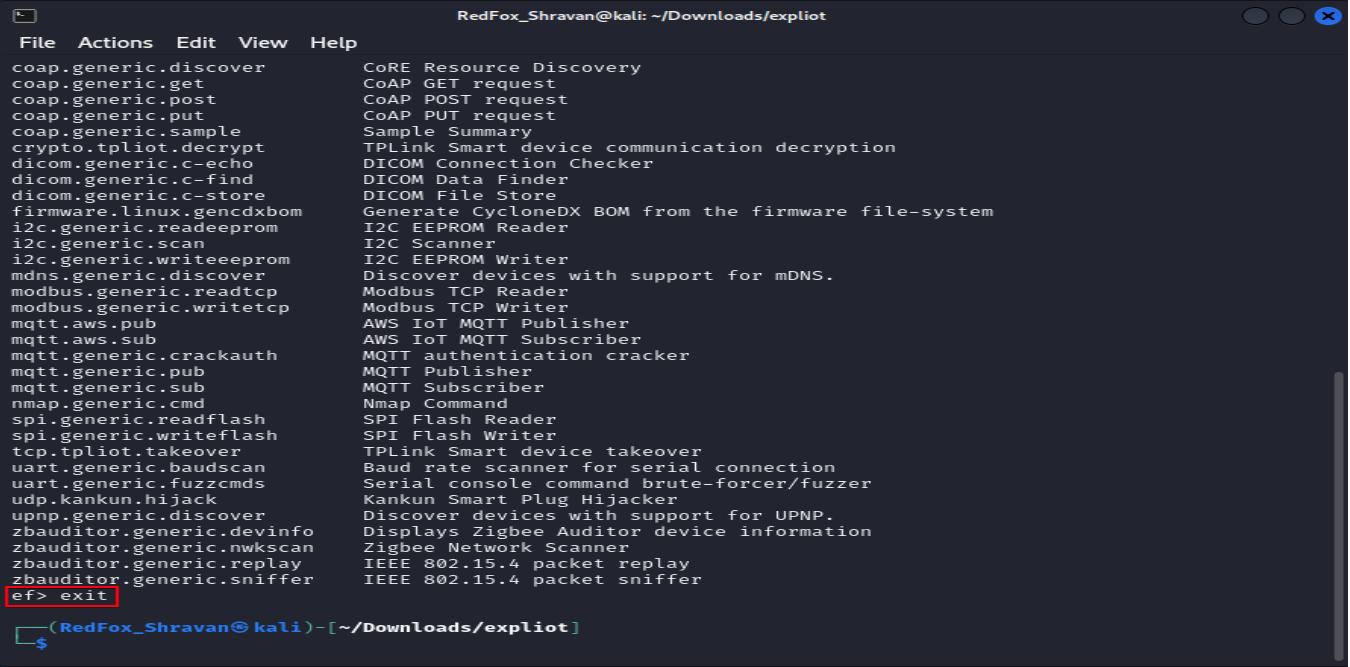
In this framework, we can see a list of plugins and command-line interfaces that can be utilized. Below is the command to list them:
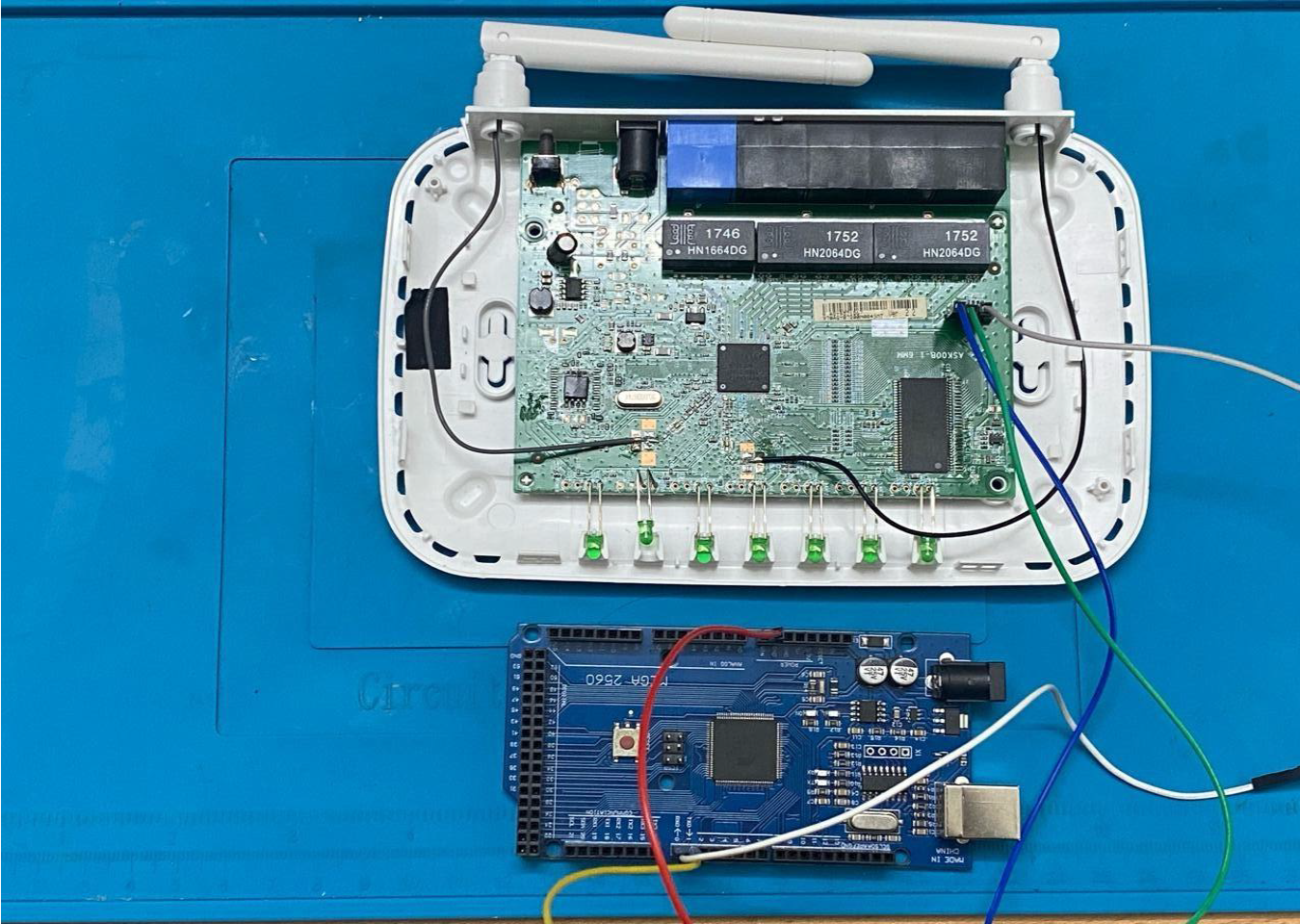
To perform the baud rate scan, we’re utilizing an Arduino Mega microcontroller board interfaced with the UART pins of the router. This setup allows us to execute EXPLIoT commands for analyzing the communication baud rates between the router and external devices. The Arduino Mega acts as a versatile hardware platform with ample digital pins, facilitating seamless integration with the router’s UART interface for robust data transmission and reception. This hardware configuration enables precise assessment of baud rates, ensuring comprehensive testing and analysis within the EXPLIoT framework.
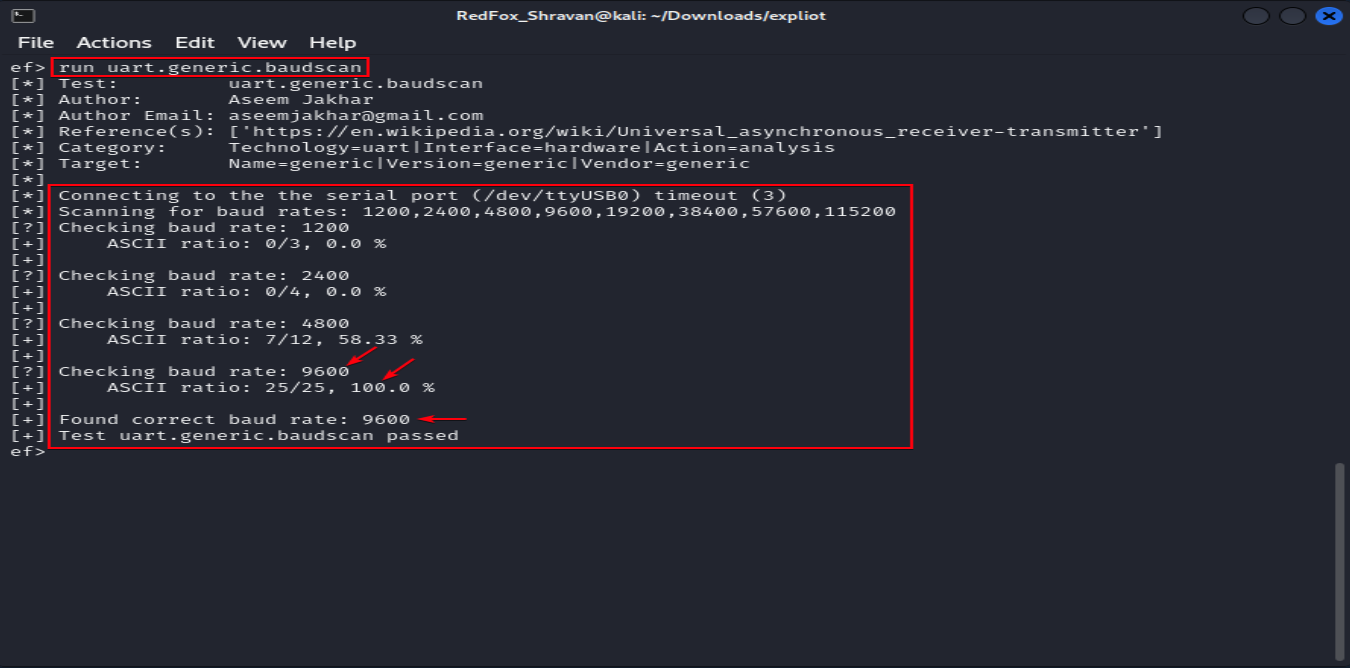
Execute a specific plugin within the EXPLIoT framework by using the syntax run [plugin_name]. In this case, we are considering the command for a plugin is baud rate detection, as shown below in the picture.
run [plugin_name]
The exit command in the EXPLIoT framework allows you to exit or terminate the current session.
exit
Or refer to the official documentation:
https://expliot.readthedocs.io/en/latest/installation/intro.html
TL; DR
EXPLIoT serves as a reminder that although smart devices provide convenience, they also pose security risks. By understanding these threats and taking measures to secure IoT devices, you can minimize cyberattack risks and enjoy a safer connected home environment.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.”