This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognizing you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Cloud Penetration Testing
Overview
In today’s digital landscape, businesses rely heavily on cloud infrastructure to store and process critical data. However, ensuring the security of your cloud environment is paramount to safeguarding your organization from cyber threats. At Redfox Security, Cloud Penetration Testing services are designed to identify vulnerabilities and weaknesses within your cloud infrastructure, enabling you to fortify your defenses and maintain a secure cloud environment.
What is Cloud Penetration Testing?
Cloud Penetration Testing is a comprehensive security assessment that evaluates the security of your cloud infrastructure, platform, and applications. Our skilled penetration testers simulate real-world attacks on your cloud environment to identify vulnerabilities and assess the effectiveness of your security controls. By adopting the mindset of a malicious attacker, we uncover potential weaknesses that cyber-criminals could exploit, helping you mitigate risks and enhance your cloud security posture. Here are some key features about cloud penetration testing:
-
Cloud-specific Expertise
-
Assessment of Configuration and Access Controls
-
Application Security Testing
-
Data Security and Privacy
-
Identity and Access Management
-
Cloud-specific Attacks
-
Compliance and Regulatory Requirements
-
Comprehensive Reporting
Why Choose our Cloud Penetration Testing Services?
Redfox Security offers comprehensive Cloud Penetration Testing services to help companies identify and address security weaknesses within their cloud infrastructure. Cloud technology is becoming increasingly popular, so it’s important to protect the data in the cloud.
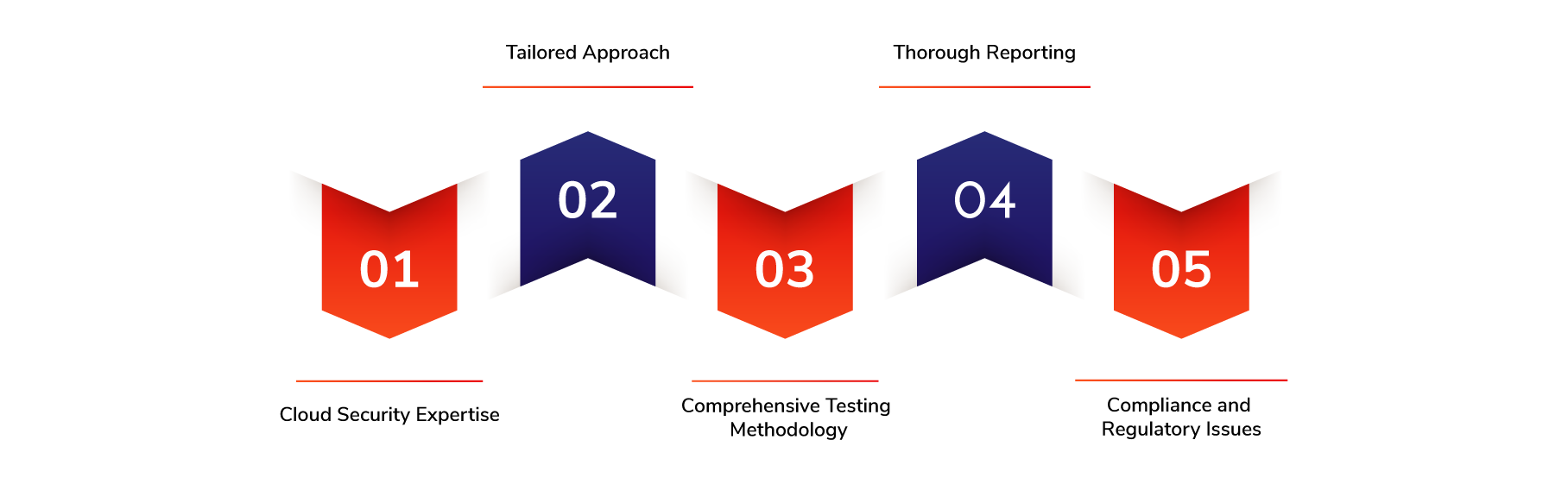
Cloud Security Expertise
Our team comprises experienced security professionals with an in-depth understanding of cloud platforms such as Amazon Web Services (AWS), Microsoft Azure, and Google Cloud Platform. We keep up with the latest trends in cloud security, compliance requirements, and best practices.
Tailored Approach
We recognize that each organization has unique security requirements and needs. Cloud Penetration Testing is tailored to your cloud environment. We work with you closely to understand your cloud infrastructure, data, and applications. This allows us to create a testing strategy tailored to your business.
Comprehensive Testing Methodology
We use a comprehensive testing methodology to cover all aspects of the cloud environment. We comprehensively analyze your cloud’s architecture, configurations, and security controls. We also examine identity and access management, encryption mechanisms, and other aspects.
Thorough Reporting
We provide a comprehensive report with actionable insights. After the Cloud Penetration Testing is completed, you will receive a detailed document that details the vulnerabilities identified, their severity level, and the recommended remediation measures. Our reports are easy to read and comprehensive so that you can prioritize the issue.
Compliance and Regulatory Issues
We know the importance of adhering to industry regulations. Cloud Penetration Testing considers specific compliance standards relevant to your industry, such as PCI, HIPAA, and GDPR.
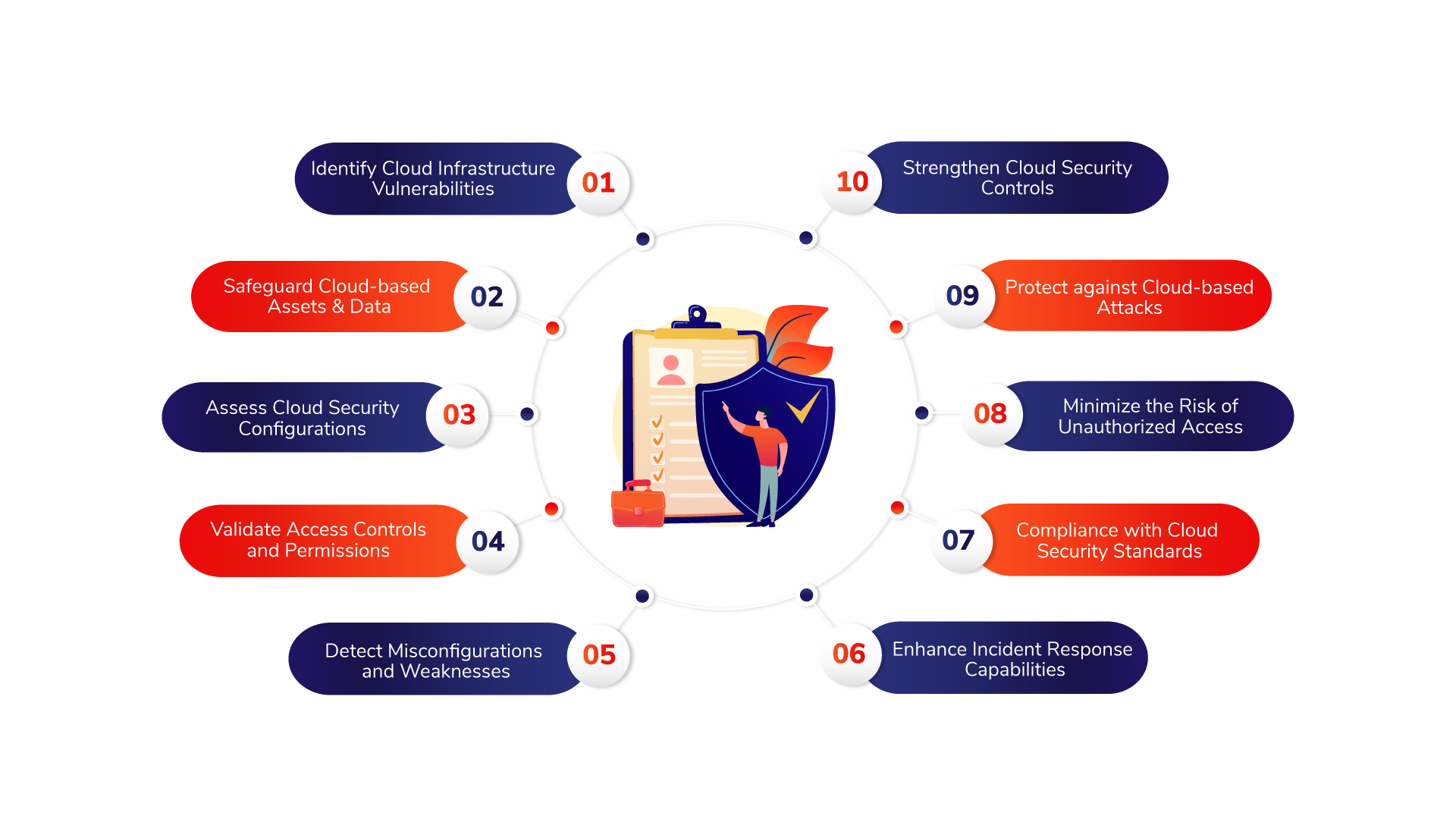
Benefits of Cloud Penetration Testing
Our Approach




