This website uses cookies so that we can provide you with the best user experience possible. Cookie information is stored in your browser and performs functions such as recognizing you when you return to our website and helping our team to understand which sections of the website you find most interesting and useful.
Kubernetes Configuration Reviews
Overview
Kubernetes is vital to automating varying application deployment elements and offers many business benefits. However, misconfigurations in the Kubernetes platform make it susceptible to attacks. Despite the deployment benefits offered by the Kubernetes platform, misconfigured environments can be under constant attacks, and adversaries can move laterally to compromise an organization’s valuable assets.
Just like traditional environments’ security, the Kubernetes platform’s security becomes crucial for all deployments.
What is a Kubernetes Configuration Review?
Kubernetes Configuration Reviews focus on evaluating the security controls and configurations within your Kubernetes clusters. It involves assessing various aspects of your Kubernetes infrastructure, including container application security, infrastructure-as-code (IAC) configurations, cluster settings, RBAC (Role-Based Access Control) configurations, network security, and overall infrastructure security. The goal is to identify and address potential security gaps, ensuring a robust and secure Kubernetes environment.
How do we carry out Kubernetes Configuration Reviews?
Securing your Kubernetes environment is essential to protect your applications and sensitive data. Our Kubernetes Configuration Reviews service thoroughly assesses your Kubernetes clusters, helping you identify and address security risks.
Container Application Security
We thoroughly review the security posture of your containerized applications deployed in Kubernetes. This includes analyzing container images, identifying vulnerabilities, assessing container security configurations, and validating best practices such as image signing, scanning, and runtime protection. We provide recommendations to strengthen the security of your containerized applications.
Infrastructure-as-Code (IAC) Configuration Review
We assess the IAC configurations used to provision and manage your Kubernetes clusters. This includes examining configuration files, deployment scripts, and Helm charts. We verify that security best practices are followed, such as using secure secrets management, enabling encryption, and enforcing strong access controls. Our review helps identify any potential misconfigurations that could compromise the security of your Kubernetes infrastructure.
Cluster Configuration Review
We analyze the configuration settings of your Kubernetes clusters, including control plane components, pod security policies, admission controllers, and auditing configurations. By assessing these settings, we ensure the cluster is configured securely, minimizing the risk of unauthorized access, privilege escalation, or data leakage.
RBAC Configuration Review
RBAC plays a crucial role in governing access control within Kubernetes. We review your RBAC configurations to ensure that roles, role bindings, and service accounts are properly defined and assigned. This helps prevent unauthorized access to critical resources and ensures that users have the appropriate privileges based on the principle of least privilege.
Kubernetes Network Security
We assess the network security aspects of your Kubernetes clusters, including network policies, ingress/egress controls, and load balancer configurations. Our review ensures that network traffic is properly segmented, communication is encrypted, and external access to your cluster is secure.
Infrastructure Security
In addition to Kubernetes-specific configurations, we assess the overall infrastructure security surrounding your Kubernetes clusters. This includes reviewing the security measures for underlying hosts, monitoring and logging systems, identity and access management, and vulnerability management processes. By addressing infrastructure security, we help you build a comprehensive defense-in-depth strategy.
Benefits of Kubernetes Configuration Reviews
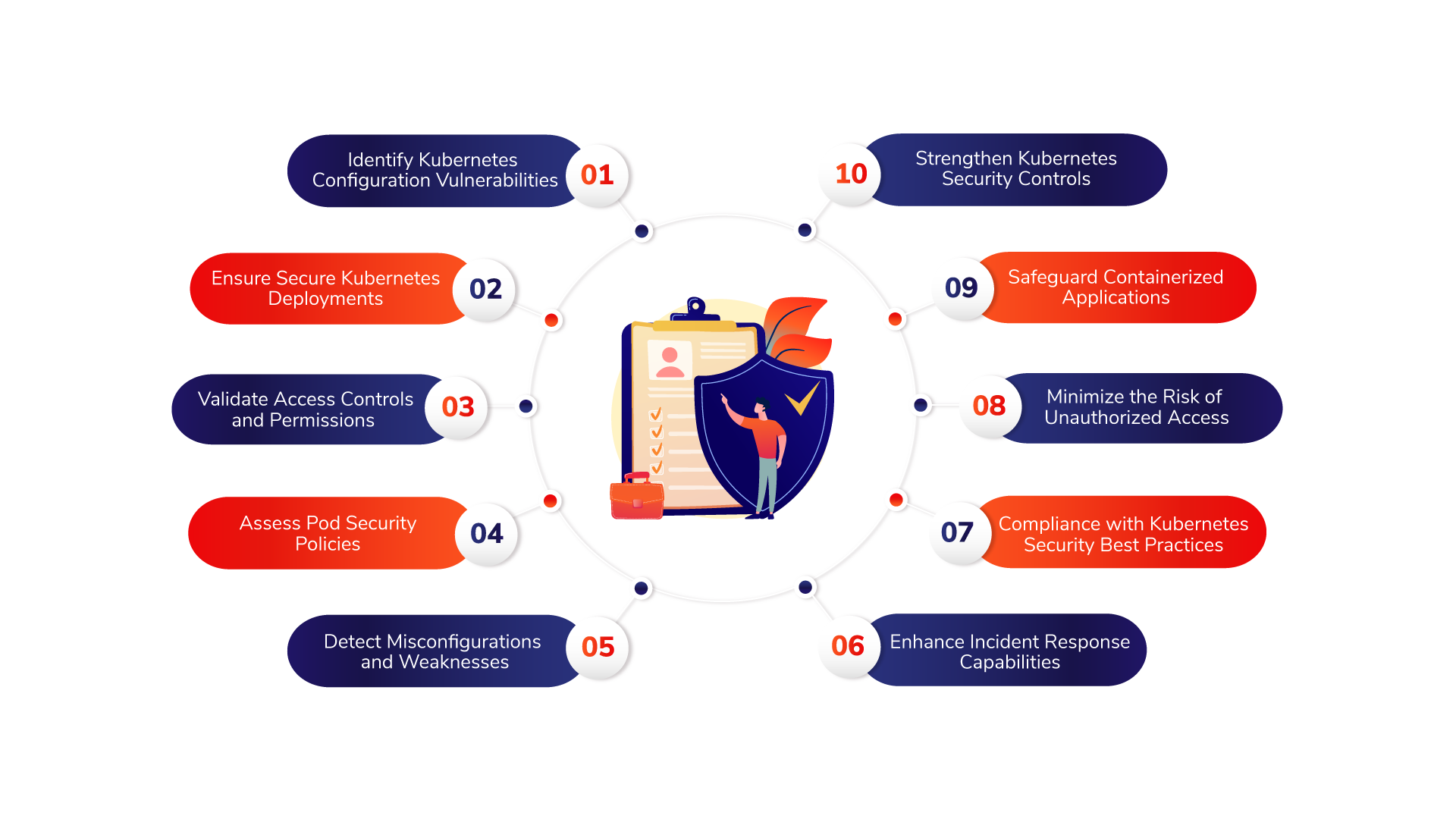
Our Approach
-
Container Application Security
-
IAC Configuration Review
-
Cluster Configuration Review
-
RBAC Configuration Review
-
Kubernetes Network Security
-
Infrastructure Security




