Understanding Buffer Overflow: Protecting Systems from Vulnerabilities

- April 19, 2024
- Web Application
- Tarak Sakhardande
Introduction to Buffer Overflow
Buffer overflow is an alarming security threat that could allow attackers to gain unauthorized access or execute malicious code in an attack environment. It happens when programs or processes attempt to store more data than their buffers can hold, leading to excess information leaking into adjacent memory locations, creating overflow, and ultimately leading to code execution
What Is Buffer Overflow and Why Does It Occur?
A buffer overflow occurs when a program or process attempts to write data beyond its allocated memory space for a buffer. Buffers are used by programs to temporarily store information before processing it. If properly managed, buffers can stay supplied with information and avoid the overflow of their allocated memory space, leading to buffer overflow.
Understanding x86 architecture is integral for understanding how the buffer overflow works
The x86 architecture, originally developed by Intel and now also produced by AMD and other manufacturers, is one of the most prevalent instruction set architectures (ISAs) worldwide, especially in personal computing. The name “x86” is derived from the 8086 microprocessors, which were introduced by Intel in 1978 and served as the basis for subsequent iterations.
Key points about the x86 architecture include:
- CISC (Complex Instruction Set Computer): x86 architecture is characterized as a CISC architecture, meaning it includes a large set of complex instructions that can perform multiple low-level operations. This design choice was typical of early microprocessors to ease programming, but modern implementations often translate these complex instructions into simpler micro-operations internally.
- 32-bit and 64-bit: Initially, x86 architecture was 16-bit with the 8086 and 8088 processors. It evolved to 32-bit with the 80386 processor (commonly referred to as the 386) and later to 64-bit with the introduction of AMD’s x86-64 architecture, also known as AMD64 or Intel 64. The transition to 64-bit architecture allowed for expanded memory addressing and increased performance in certain scenarios.
- Compatibility: One of the significant strengths of x86 architecture is its backward compatibility. Modern x86 processors can execute code written for older generations of the architecture, ensuring software compatibility across different generations of hardware.
- Widespread Adoption: The x86 architecture is widely used in desktop and laptop computers, servers, and workstations. It dominates the market for personal computing, although ARM-based processors have gained significant ground in mobile devices and embedded systems.
- Extensions and Variants: Over the years, various extensions and enhancements have been introduced to the x86 architecture, including MMX, SSE, AVX, and more, which provide additional capabilities for multimedia processing, cryptography, and parallel computation.
- Virtualization and Security Features: Modern x86 processors often include hardware support for virtualization, which enables multiple operating systems to coexist on one physical machine at the same time. Additionally, security features like Execute Disable (XD) bit and Intel VT-x/AMD-V enable improved security and virtualization performance.
- Performance and Power Efficiency: While x86 processors historically have been criticized for their power consumption compared to other architectures like ARM in mobile devices, advancements in process technology and microarchitecture have led to significant improvements in performance per watt.
Overall, the x86 architecture’s longevity, backward compatibility, and ongoing evolution have ensured its continued relevance in the computing industry.
Registers Are Key in Buffer Overflow Attacks
Registers are small storage areas within a processor which hold data for immediate processing. Understanding how buffer overflow attack’s function is essential for defending against vulnerabilities and securing systems from potential threats.
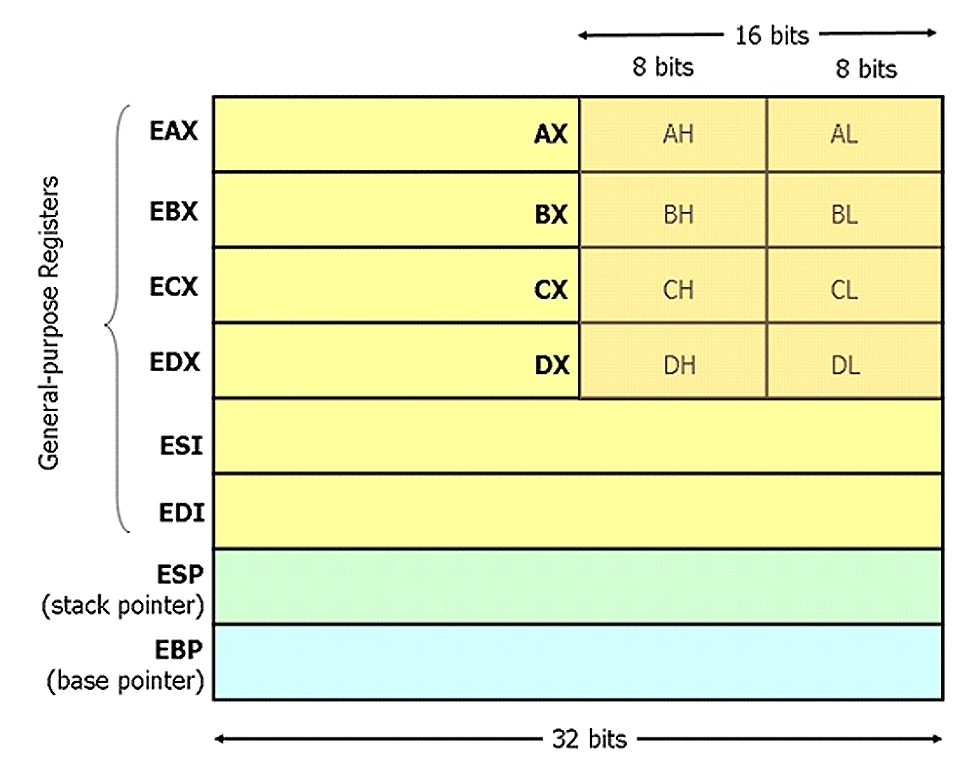
Instruction Pointer Register (EIP) manipulation can be instrumental to buffer overflow attacks since it holds the memory address of the next instruction to be executed. By manipulating EIP with buffer overflow attacks, an attacker can redirect program execution towards malicious shellcode.
Consequences of Buffer Overflow Vulnerabilities
Buffer overflow vulnerabilities can have serious repercussions for individuals and organizations alike. They can be leveraged successfully to gain unauthorised access, data breaches, system crashes and the execution of arbitrary code—potentially disastrous outcomes that must be protected against to ensure businesses survive and their systems continue running as expected.
Financial institutions or government agencies that rely heavily on sensitive systems like the cloud for services may become vulnerable to buffer overflow vulnerabilities that allow highly confidential data to be compromised, disrupting critical services. On an individual level, attacks exploiting buffer overflow vulnerabilities may result in identity theft, financial loss or malware infection of devices used.
Common Buffer Overflow Attack Techniques
Attackers utilize several strategies to exploit buffer overflow vulnerabilities. Common techniques employed by attackers include:
- Stack-based buffer overflow: In a stack-based buffer overflow, attackers aim to flood a stack-based buffer with data or instructions to overwrite crucial information or instructions.
- Heap-based buffer overflow: Heap-based buffer Overflow occurs when an allocated buffer exceeds its capacity in a heap, an area of memory used for dynamic storage allocation.
- Format String Vulnerabilities: Format String Vulnerabilities can enable cyber attackers to gain unauthorized access to memory locations that contain values with unknown or unpredictable values, leading to buffer overflow.
- Return-oriented programming (ROP): Return-oriented Programming (ROP) attacks employ legal code fragments known as gadgets to circumvent security measures and launch malicious programs.
Safeguard Your Systems against Buffer Overflow Vulnerabilities
To effectively defend against buffer overflow vulnerabilities, secure coding practices and appropriate security measures must be observed. Here are some best practices:
- Validate and Sanitize User Input: It is always prudent to verify and sanitize user input so as not to exceed the buffer’s capacity. Use functions that limit how many characters may be copied into one buffer at a time.
- Use secure programming languages: Programming languages that integrate memory protection mechanisms, such as bounds checking and automatic memory management, are ideal choices for memory protection.
- Implement regular code reviews and testing: Conduct routine code reviews and testing sessions to detect any buffer overflow vulnerabilities in your code using static analysis tools and dynamic testing techniques to detect and mitigate them.
- Engaging Address Space Layout Randomization (ASLR): ASLR allows processes to randomly configure their memory layout, making it harder for attackers to identify critical memory areas and predict where important memories reside.
- Use stack canaries: Stack canaries are random values placed before the return address on the stack. They act as buffer overflow protection by monitoring their values to detect whether their status has changed.
Best Practices for Protecting Buffer Overflow Attacks
Adherence to secure coding practices is vital to prevent buffer overflow attacks. Adopting these best practices will significantly lower the risk of buffer overflow vulnerabilities:
- Bounds Checking: Make sure that your code uses bounds checking when copying data into buffers, using functions like strlcpy or strncpy_s that let you specify buffer sizes.
- Avoid unsafe string functions: Be wary of unsafe string functions like gets or sprintf that do not perform bounds checking and could put sensitive data at risk.
- Maintain Updated Libraries and Frameworks: Make regular upgrades of libraries and frameworks to take advantage of security patches and bug fixes that address buffer overflow vulnerabilities.
- Utilize compiler security features: To quickly detect buffer overflow attacks and mitigate them quickly, set up your compiler with security features like stack protection to detect attempts of buffer overflow more rapidly and mitigate them quickly.
Tools and Techniques for Assessing Buffer Overflow Vulnerabilities
There are various tools and techniques available that can help detect and address buffer overflow vulnerabilities, including:
- Static Analysis Tools: Static analysis tools allow users to review source code without running it and are efficient ways to detect buffer overflow vulnerabilities. Popular tools in this space include Coverity and Fortify.
- Fuzz Testing: Fuzz testing involves injecting unexpected or random input into programs to identify vulnerabilities such as buffer overflow. Tools like American Fuzzy Lop (AFL) and Peach Fuzzer are helpful tools in this process.
- Address Sanitizers: Address sanitisers are compiler features designed to detect buffer overflows and memory-related bugs during compilation. They offer runtime checks for potential buffer overflow vulnerabilities. Address sanitisers may be enabled while compiling or when performing runtime vulnerability scans. You can enable address sanitisers when performing these vulnerability checks at runtime.
- Intrusion Detection Systems (IDS): IDS are invaluable tools for real-time detection of buffer overflow attacks on networks or system logs. They monitor these networks closely for suspicious activity and immediately notify authorities should any be identified.
TL;DR
Reconciling buffer overflow vulnerabilities is essential to protecting system and data integrity, as they present serious threats. Understanding their causes and potential repercussions is an integral part of creating effective defence strategies against this vulnerability.
To reduce buffer overflow risks, organizations and individuals must adhere to secure coding practices, conduct regular code reviews and testing, deploy appropriate security measures, maintain up-to-date software versions, and watch for suspicious activities. Implementing such steps ensures systems remain protected.
Avoiding buffer overflow attacks requires aggressive security management during software development, prioritizing security inclusion during design, and staying aware of emerging threats to safeguard systems and data against potentially catastrophic vulnerabilities.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems, and provide recommendations to remediate them. Join us on our journey of growth and development by signing up for our comprehensive courses.




