JTAG headers play an essential role in embedded systems development, allowing developers and engineers to access low-level parts of devices for debugging and testing purposes. Understanding what a JTAG header is and its functions is essential for anyone involved with hardware development. In this article, we’ll dive deeper into its details, exploring its importance while offering methods of verifying its presence on devices.
What is a JTAG Interface?
A Joint Test Action Group (JTAG) interface is a standardized protocol used for accessing and debugging integrated circuits on devices. It communicates with boundary scan cells present within chips to facilitate testing, programming and debugging activities. JTAG interfaces typically consist of pins or signals known as JTAG pins/signals which allow communication between external tools like debuggers that employ this protocol and devices that support it.
Understanding the Role of JTAG Debugger
JTAG debuggers are physical tools designed to connect to the JTAG interface of devices and enable developers to perform various debugging tasks. Monitoring register values, memory contents, and execution flow in real-time aids in debugging tasks by allowing the halting of a device at breakpoints set within its code. This proves particularly beneficial when addressing intricate hardware/software interactions.
Identifying and Analysing JTAG Headers on Your Device
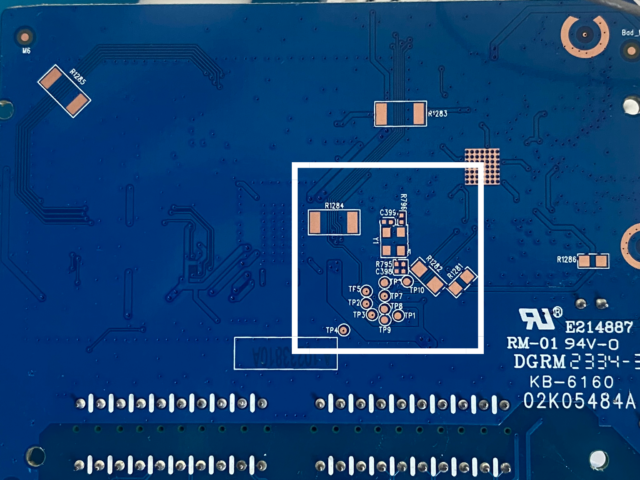
Before delving into JTAG analysis for debugging, it’s crucial to identify the presence of JTAG headers on your device. These physical connectors, situated on the device’s circuit board, offer access to JTAG pins. Recognizing JTAG headers can be done through various methods:
- Documentation and Circuit Diagrams: Refer to device documentation or circuit diagrams provided by the manufacturer.
- Visual Inspection: Physically inspect the circuit board for labelled connectors, often marked with labels directly attached to the connectors.
- Labelling and Pin Configuration: Common types of JTAG headers include 2×5, 2×10, and 2×20 headers, denoting the number of pins per row. However, if the pins are labelled as test pins, identifying JTAG headers might be challenging, requiring additional exploration and analysis.
Understanding the presence, type, and configuration of JTAG headers is essential for effective hardware analysis and debugging.
Verifying the Presence and Functionality of a JTAG header
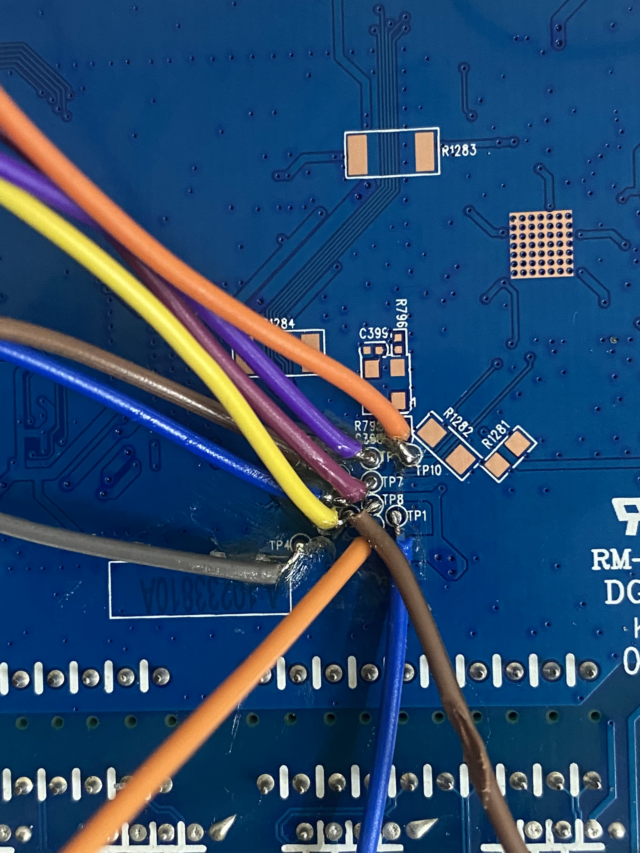
To confirm the presence and functionality of a potential JTAG header on your device, actively use a multimeter or continuity tester to check connectivity between JTAG pins and the device’s circuitry. Utilize an oscilloscope to monitor JTAG pin activity when powering on the device; observable activity indicates a functional JTAG header. Additionally, employ specialized tools like JTAGulator to identify and read device information directly from its pins. This step ensures thorough verification of the JTAG header’s presence and functionality.
JTAG header Identification and Verification Tools
There are various tools and techniques available to you for the identification and verification of JTAG headers on your device. One such device is called the JTAGulator; this hardware device automatically identifies JTAG headers by scanning pins and analysing responses; it can save considerable time when documents or circuit diagrams are unavailable or difficult to interpret. A logic analyzer may also help by recording signals on JTAG pins to gain further understanding of how it behaves within its environment. 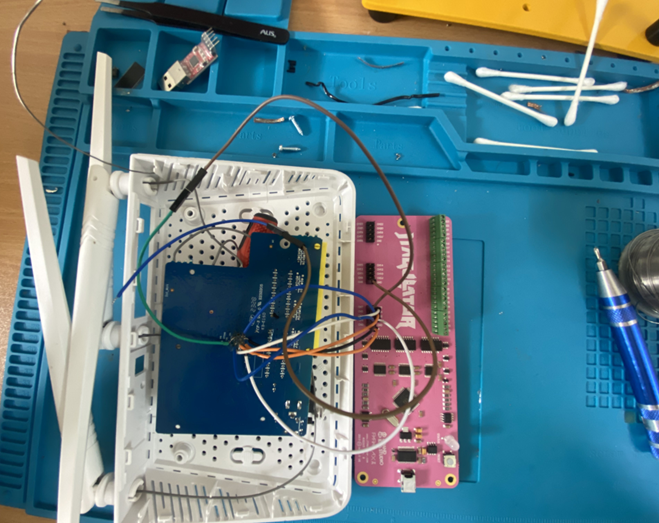
Common Challenges Involved With identifying and Verifying JTAG Headers
Although identifying and verifying JTAG headers may seem straightforward, there can be challenges along the way. The absence of documentation and circuit diagrams complicates the process of locating and pinning out JTAG headers. In some cases, visual inspection and experimentation become necessary. Devices may incorporate security mechanisms that limit access to specific JTAG interfaces or employ non-standard pinouts, restricting ports. To overcome these obstacles, reverse engineering techniques may prove essential for bypassing such measures.
Using the “Screen” Command for JTAG Analysis
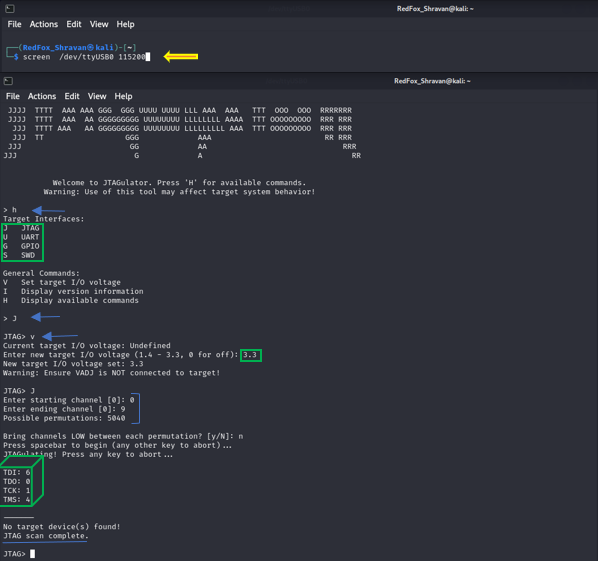
When dealing with JTAG analysis, connecting to the JTAGulator with the appropriate settings is crucial. Utilize the “screen” command with a baud rate of 115200 to establish a connection. Once connected, enter JTAG commands to analyse and identify pinouts from the JTAG pin header. Understanding the layout and functions of JTAG pins is integral for exploring their capabilities and capitalizing on them to further exploitation of the device’s JTAG capabilities.
Best Practices for Working With JTAG Headers
To ensure a seamless and successful experience with JTAG headers, it is vitally important to follow some best practices. Consult device documentation and circuit diagrams when available as this may give useful insight into where a JTAG header may reside. Secondly, take care when applying power as improper handling could damage components; to prevent this happening it may be advisable to temporarily disconnect power before making connections or making modifications on JTAG headers. Lastly, always upgrade firmware/software versions on debugging tools to take full advantage of bug fixes/features added updates/features/add On.
TL;DR
JTAG headers are an indispensable asset to engineers and developers working in hardware development, providing low-level access and debugging capabilities. Discovering and verifying JTAG headers with the right tools is key to unlocking their potential. From troubleshooting hardware to delving into device internals, JTAG headers act as gateways, paving the way for hardware development endeavours.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.”