
NoSQL Injection refers to cyber-attacks that inject malicious payloads into non-SQL databases like MongoDB. Due to the new demand for modern-day applications, there has been wide adoption of NoSQL databases which could conveniently facilitate the distribution of data across numerous servers. NoSQL databases give an avenue for wide scalability, and they require a single database node to perform all operations of the same transaction.
NoSQL databases have been existing for a while now, but the term acquired wider popularity in early 2009. There are different types and instances of NoSQL databases, some are listed below:

Some ways NoSQL databases differ from more traditional SQL databases are:
By far the most extensively used NoSQL database is MongoDB.
SQL injection is a well-known vulnerability. SQL is a language where users can run queries into and out of a database and recover data using logical operators. Because these searches regularly involve user-supplied data, they may be vulnerable to an injection attack if the input is not sanitized properly.
SQL is not used to conduct queries in NoSQL databases; however, NoSQL queries are not immune to injection. Because queries still contain user-supplied data, failing to properly sanitize this data may lead to dangerous consequences.
Finding the injection
To begin with, it’s key to find where the application is ingesting any user supplied data. In other words, data that can be controlled by an external user. Some examples include:
Some input parameters may be directly used in the back-end database query, so it’s worth trying to modify the values to trigger an error or an unexpected behavior.
Some input characters that may break the query are listed below:
‘ ” \ ; { } ( )
NoSQLMap can sometimes be leveraged to catch the low-hanging fruit, although more advanced cases almost always require manual testing, static analysis, and code review.
Commonly used operators in NoSQL injection vulnerabilities include:
To simulate this vulnerability, we used the “OWASP juice shop vulnerable” application.
In this application, after authentication, users are allowed to submit a review for a product. Once the review is submitted, users only have permission to edit their own reviews, and not reviews given by other users of the application.
For example, in this application, the user has an email id: bender@juice-sh.op
Step 1: User clicks on any one product and submits a review.
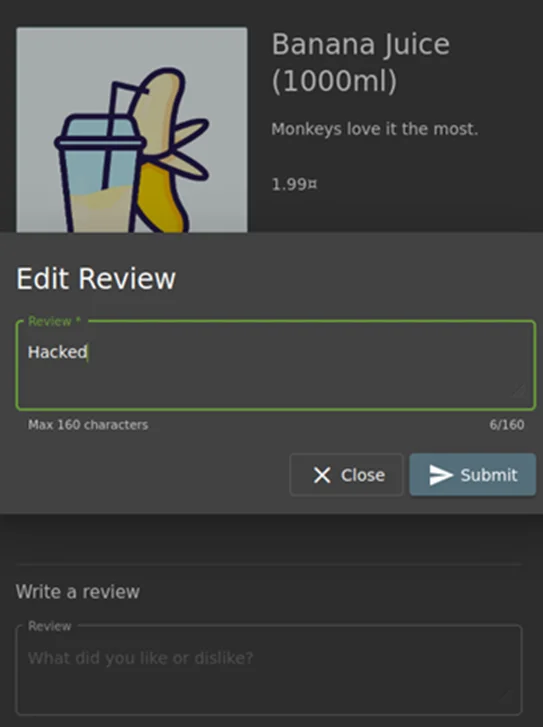
Step 2: After submitting the review, user clicks on edit and make changes in the proposed review.
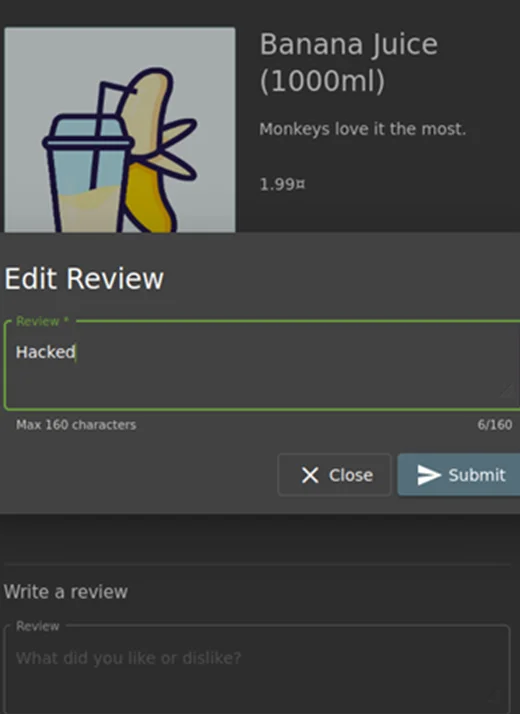
Step 3: Intercept the request using Burp Suite i.e., after editing the review. By looking at the request, notice that each review has its own unique alphanumeric ID value:
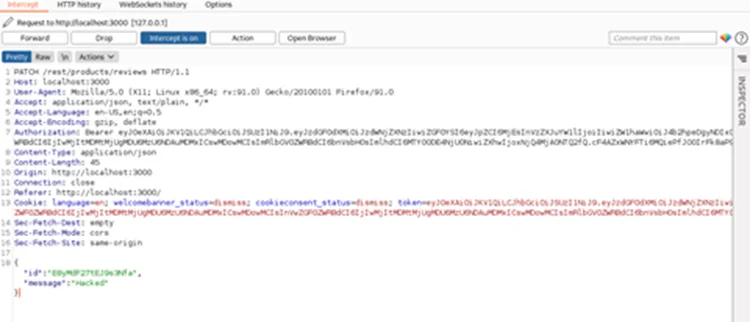
Step 4: Remove the Id parameter and add a simple NoSQL injection payload ($ne:-1). This will ensure that the Id supplied is not equal to the Id value specified, i.e., -1.
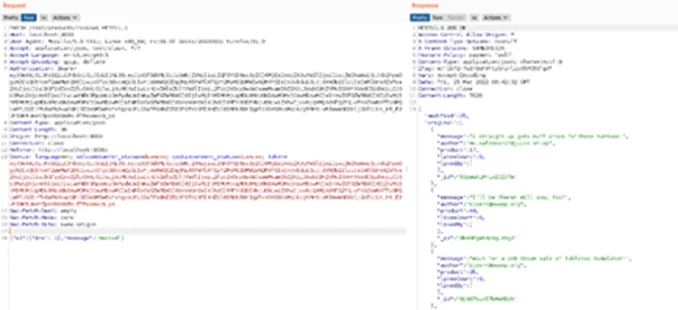
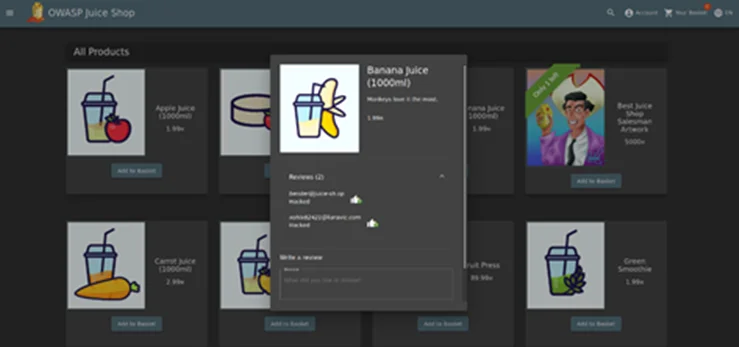
Step 5: Refresh the web page. Note that the NoSQL injection payload executes and alters all reviews, that were previously submitted by other users of the application.
From MongoDB documentation:
You can express most queries in MongoDB without JavaScript and for queries that require JavaScript, you can mix JavaScript and non-JavaScript in a single query. Place all the user-supplied fields directly in a BSON field and pass JavaScript code to the $where field.
You can disable all server-side execution of JavaScript in MongoDB by passing the –noscripting option on the command line or setting security.javascriptEnabled in a configuration file.
Stay safe, stay healthy and hack responsibly.
To learn more about SSRF and other web vulnerabilities, check out our course, Web Hacking Basics. We have thoroughly covered this topic as well.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through Penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. With a combination of data-driven, research-based, and manual testing methodologies, we proudly deliver robust security solutions.
“Join us on our journey of growth and development by signing up for our comprehensive courses, if you want to excel in the field of cybersecurity.”