This is a continuation of the previous blog post – see SSL Pinning Bypass for Android Apps. If you haven’t already, please go check it out. Assuming you’ve set up Frida, we can proceed further to bypass Android root detection using Frida.
What is a rooted Android device?
Android rooting is a technique that allows one to easily gain unrestricted access to the system files. Access here means – being able to change, delete, or modify things as needed. In IOS, this is equivalent to JAIL Breaking. It gives the ability to modify the device’s software code or install other software that the manufacturer would not normally allow for good mobile security reasons. Rooting can provide significant advantages over a standard Android device, but gaining access to sensitive files can cause a variety of issues for both the user and the Android device.
What is Android Root Detection Bypass?
When creating an application, developers include a root detection mechanism to prevent users from using it on a rooted Android device. When a user attempts to install an application, it generates an error message and refuses to allow the application to be installed on a rooted device. During the root bypass, we make changes to the code that prevent the application from closing, resulting in the running of the application on a rooted Android device. So, to accomplish this, we will first install Frida and then bypass the root detection.
What do we need?
- Rooted device or Emulator
- Platform-tools
- Frida Packages for Python
- InsecureBankv2 app
We have already installed the first three (see SSL Pinning Bypass for Android Apps) so let’s start with the “InsecureBankv2” application.
InsecureBankV2
Dinesh Shetty (creator) has created the InsecureBankv2 Android application. The purpose of this vulnerable Android application is to teach developers and security enthusiasts about Android vulnerabilities by testing a purposefully vulnerable Android application.
First, we need to setup the AndroLab Sever. For that we need to clone or download the application from the GitHub repository to our machine. Then, open the folder AndroLabServer.
Use pip to install the prerequisites. Run the following command:
pip install -r requirements.txt
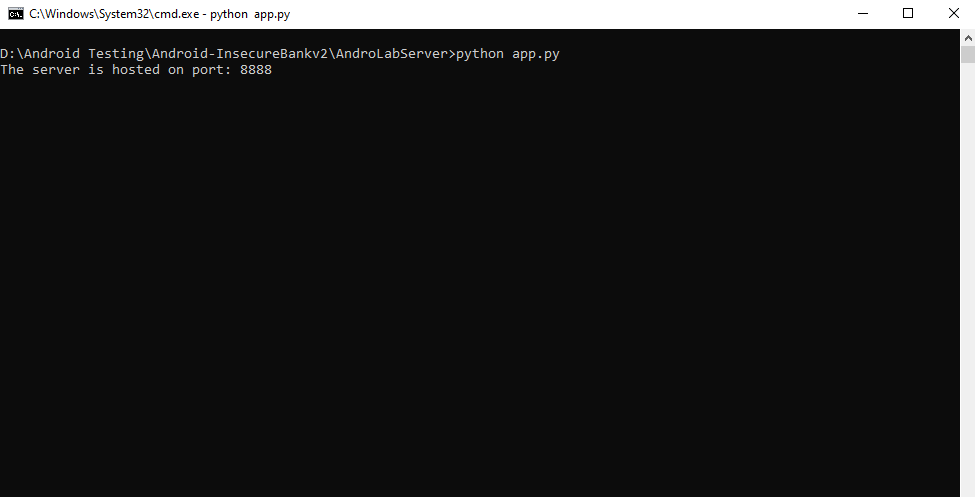
After installing the prerequisites, we will start the HTTP server. Issue the following command:
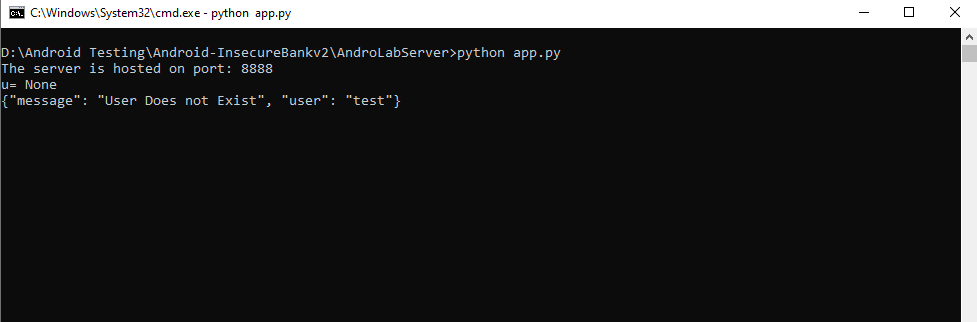
python app.py
Note that app.py will host the server on by default on port 8888. Next, connect to the emulator with Android Debug Bridge (ADB) and install the InsecureBankv2 application using the relevant APK file.
adb connect "your-host-only-ip-address"
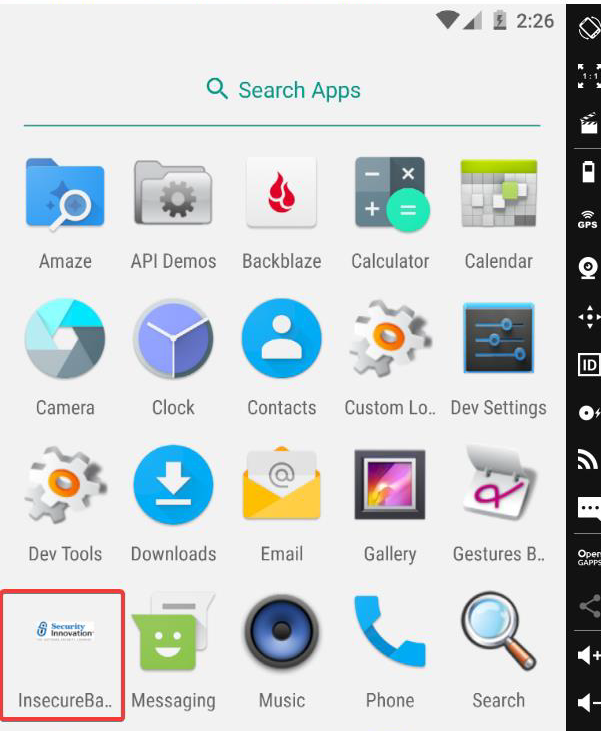
adb install InsecureBankv2.apk
The application icon appears on the emulator after it has been successfully installed.
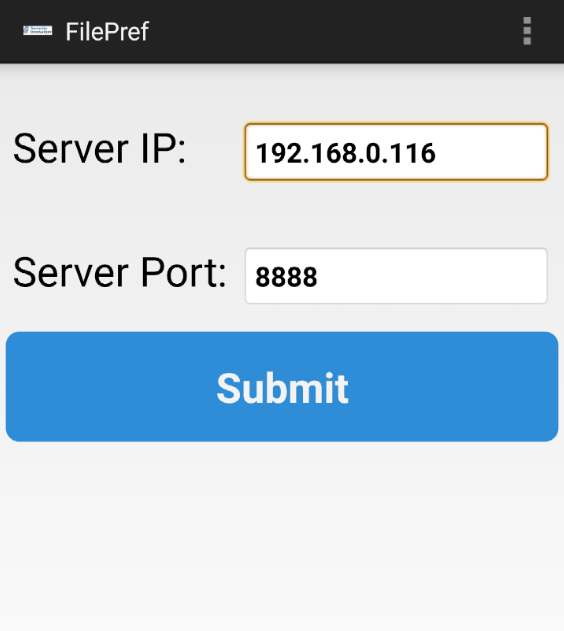
The final step is to launch the app and navigate to the IP address and port where the AndroLab server is running. In this case, we’ll punch in the IP address of the machine’s host-only network adapter, as well as port 8888.
The network preferences setting will be successfully configured after you click submit. We can try logging in with incorrect and correct credentials to see if the app is connected to the server. When we attempt to login, the following output is generated, indicating that the app is communicating with the AndroLab server.
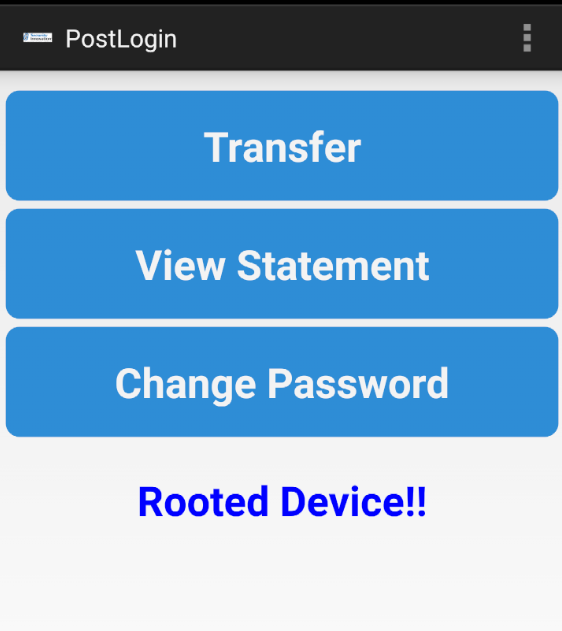
Try to login with the correct credentials i.e., jack/Jack@123$. We can see that this is “Rooted Device!!”.
All Hail Frida!
Now that we’ve installed the application in the Genymotion android emulator, we can easily connect to the Frida server via the command line. We’ll use the following command to list all the processes that are currently running.
frida-ps –U
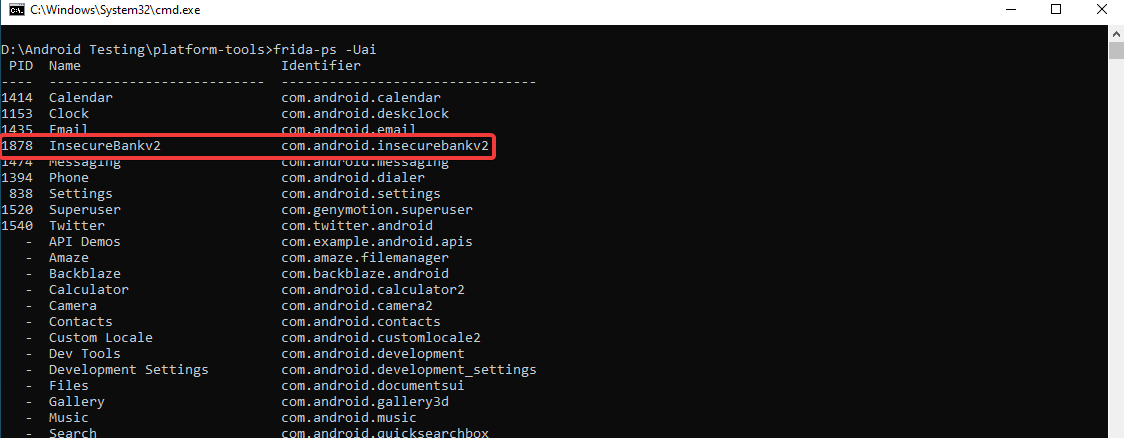
By using the following command, we can list all the installed application processes and find our test application along with its binary.
frida-ps –Uai
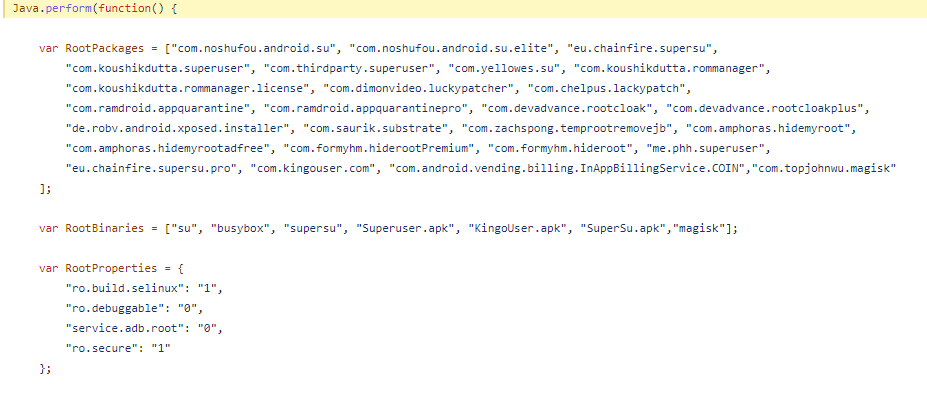
Injection Script (fridantiroot.js) For Root Bypass
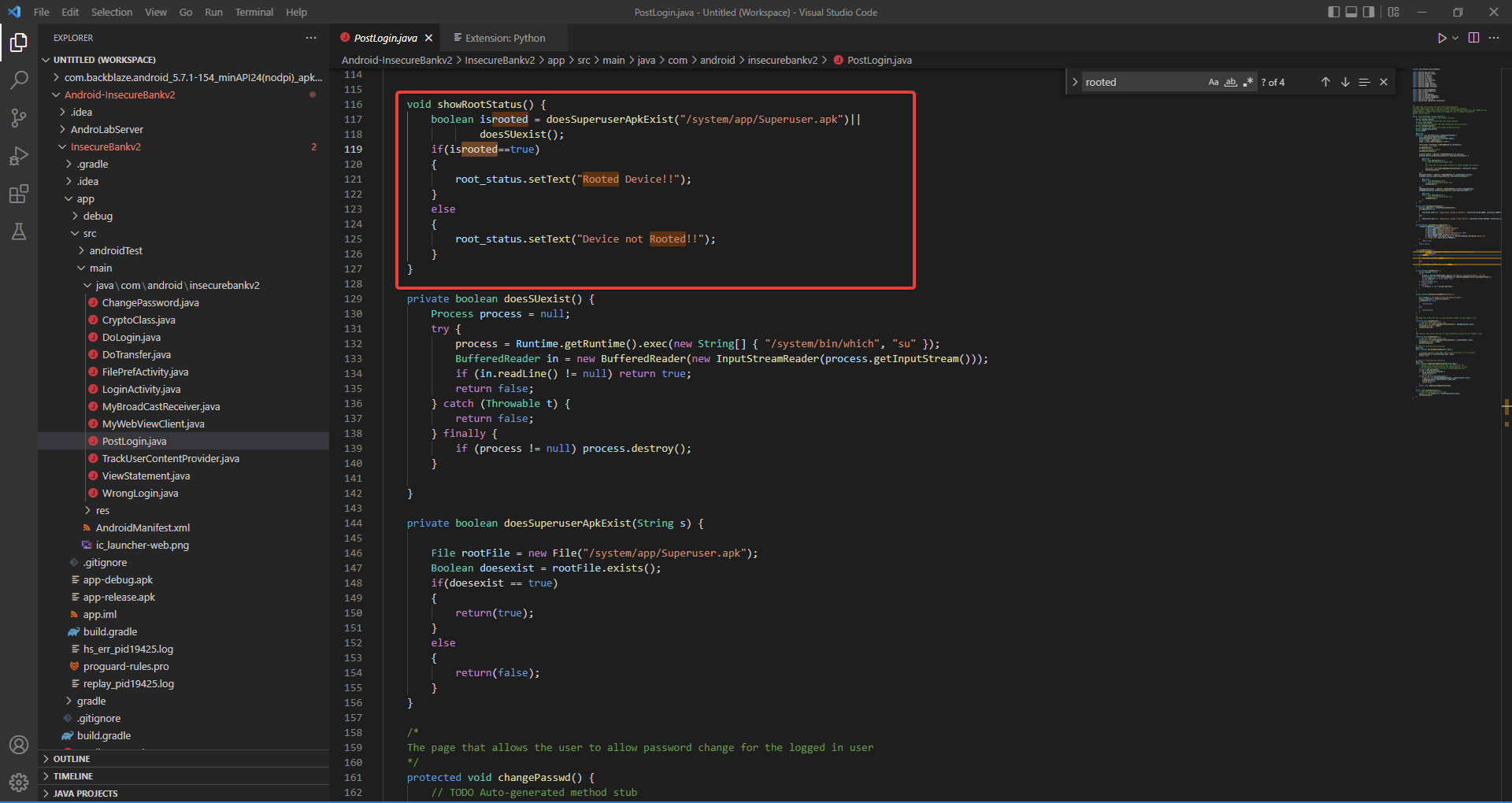
Below, we can see that if any suspicious package or system change is detected, the variable “isrooted” will return true, which will prevent the application from running when root access is detected, and if the value is returned as false, the application is allowed to run because root access is not detected.
In the JS script below, we will try to force the value “isrooted” in the code above to be returned as false, causing the application to believe it is running on a non-rooted device. As a result, the application will now run on a rooted device.
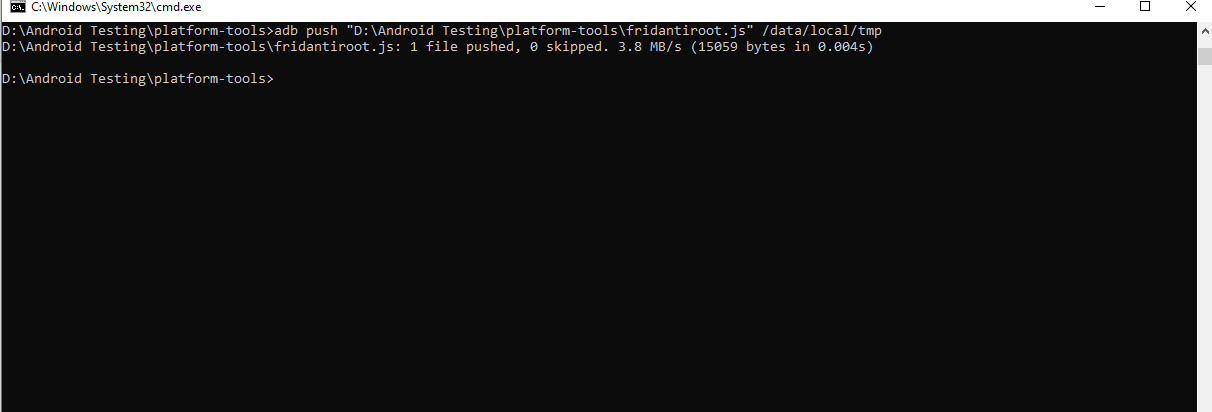
To inject into the target application, we’ll need to download the injection script from this link here and rename the script name to fridantriroot.js and push it onto the device..
Step 1) We are using the fridantiroot.js script to disable pinning on the target application. To push the fridantiroot.js script onto the device, copy it to the adb folder and run the following command:
//adb push <path_to_ fridantiroot.js _folder> /data/local/tmp adb push "D:\Android Testing\platform-tools\fridantiroot.js" /data/local/tmp
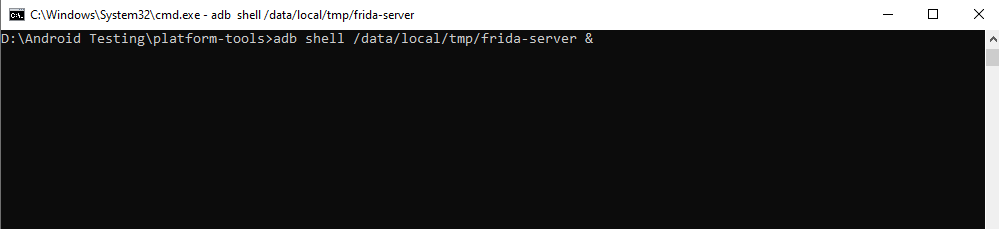
Step 2) Run the following command on the device to start the frida-server:
adb shell /data/local/tmp/frida-server &
This starts Frida on the device.
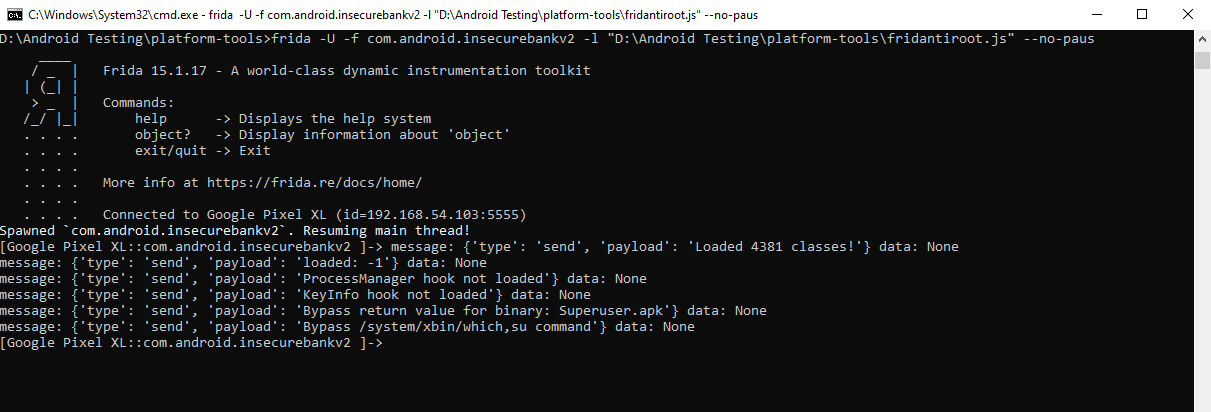
Step 3) Inject the fridantiroot.js script into the target application.
Finally, we’ll use the following command to inject the fridantiroot.js script into the native application:
//frida -U -f <your_application_package_name> -l <path_to_fridantiroot.js_on_your_computer> --no-paus frida -U -f com.android.insecurebankv2 -l D:\Android Testing\platform-tools\fridantiroot.js --no-paus
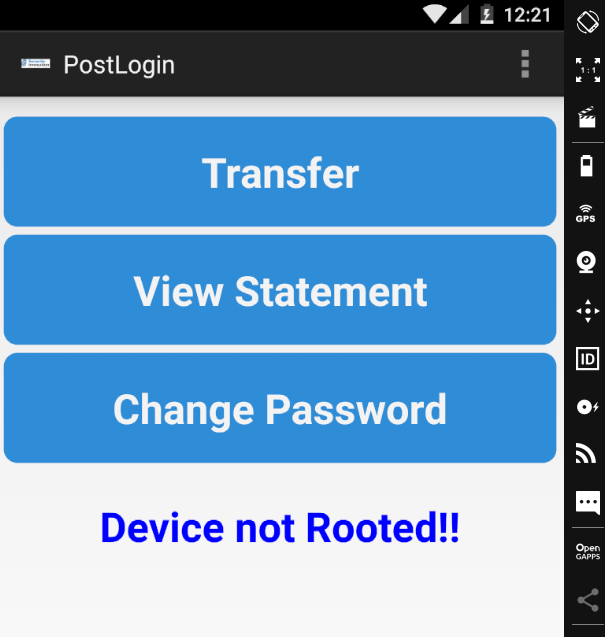
Now if we log in again in the application we see this – “Device not Rooted!!”. That’s it! We got around the root validations!
TL;DR – https://youtu.be/O8jC6aOGyEY
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“