
Organizations who don’t know the difference between penetration testing and vulnerability scanning are often losing out on an essential piece of their overall security posture.
Vulnerability scanning looks for known security flaws. A penetration test actively seeks out and exploits these security issues. While vulnerability scanning is mostly automated, a penetration test often requires varying levels of technical knowledge.
Many individuals use these two terms interchangeably, either due to misunderstanding or marketing hype. Organizations often use both to improve their overall security posture. However, their objectives and methodologies differ.
Still unsure? Read on to learn the differences between vulnerability scanning and penetration testing.
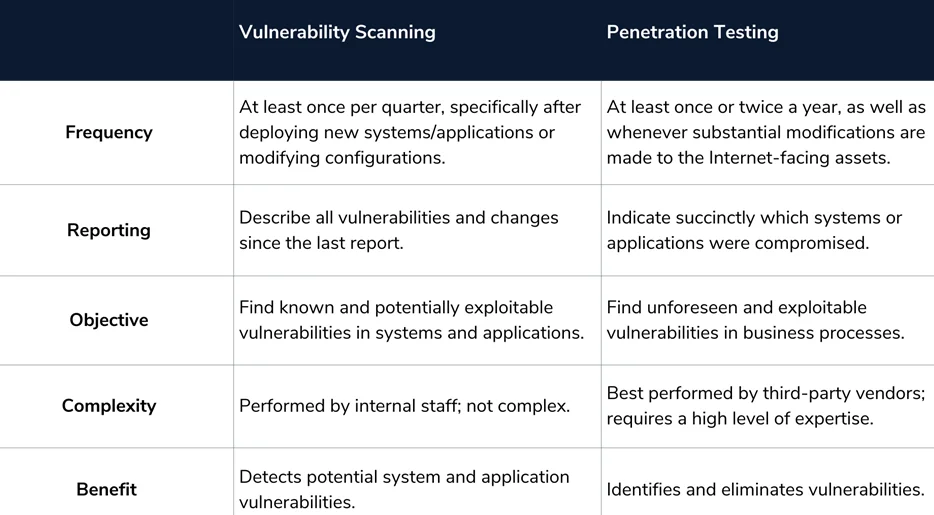
The act of using automated solutions to discover possible vulnerabilities in networks (including routers, firewalls, servers, etc.) and applications is known as vulnerability scanning. It’s automated and looks for network or application-level vulnerabilities. They simply find possible weaknesses, not exploit them. As a result, they aren’t designed to detect zero-day exploits. The breadth of vulnerability scanning is enterprise-wide, necessitating the use of automated technologies to monitor many assets. It has a broader scope than penetration testing. To utilize a vulnerability scanning product efficiently, you require product expertise. It is often administered by system administrators or security experts who are well-versed in infrastructure and application security.
Organizations should keep track of essential systems and assess trends in open ports and new services. For this reason, vulnerability scanners (e.g., Nessus) can inform internal security teams when unwanted modifications are made. Comparing observed changes to ideal states can often reveal whether the changes were authorized or if they were a result of an actual attack or a staff member breaking the rules. It is recommended to carry out a vulnerability scan at least once quarterly.
Penetration testing, on the other hand, has a defined scope and involves a human element. Assessments are conducted at an application-level or network-level, but restricted to a defined function, division, or collection of assets. The entire infrastructure can be included; however, this isn’t realistic in the actual world considering time and budget constraints. A variety of considerations, based on risk and the relative importance of assets, goes into determining the scope of your work.
It’s best that penetration testing is performed by third-party vendors as it offers an impartial perspective of the environment. It requires a high level of expertise. Competent penetration testers usually develop state-of-the-art scripts, modify attack parameters, and tweak tool settings while testing. In that sense, they work like real-world attackers. Unlike vulnerability assessments, penetration testing is meant to find and exploit vulnerabilities. Companies can then assess the effectiveness of their security controls and identify areas for improvement. It is highly recommended to carry out a penetration test at least once or twice a year.
In summary, both, vulnerability scanning and penetration testing, contribute to the risk analysis process and aid in determining which security controls are most suited for an organization. They must work in tandem. However, it is critical to understand the difference; each is significant and serves various objectives and achieves different results.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“