
In today’s digital landscape, mobile users often rely on the clipboard function to conveniently copy and paste sensitive information like passwords and payment details. However, the clipboard’s vulnerability makes it an attractive target for cyberattacks. Attackers can exploit the clipboard to collect valuable data or even manipulate copied information for malicious purposes. As a security-conscious individual or organization, it is necessary to understand the probable risks associated with the Android clipboard and implement effective measures to protect your information.
The Android operating system provides a clipboard framework that allows users to copy and paste various types of data, including text, images, and binary stream data. Simple text data is stored directly in the clipboard, whereas the complex data is stored as a reference that the pasting application resolves using a content provider. This functionality enables copying and pasting within an application or between applications that implement the clipboard framework.
To utilize the clipboard in an Android application, developers can instantiate a ClipboardManager object by calling the getSystemService() method. This object provides various methods for interacting with the clipboard, such as retrieving clipboard text, setting clipboard text, and checking if the clipboard contains any text.
Despite its convenience, the Android clipboard poses significant security risks. Cybercriminals can exploit these risks to gain unauthorized access to sensitive information. Two common attack vectors related to the Android clipboard are attacking through the Android Pasteboard and Android Keyboard Cache.
Attackers can leverage the Android Pasteboard to intercept and manipulate copied information. For example, an attacker could modify a copied cryptocurrency wallet address before the user pastes it into a crypto wallet app or chat message. By hijacking and replacing the clipboard contents, attackers can misdirect funds or collect valuable data.
To illustrate the severity of this vulnerability, consider a scenario where a user copies their account number from a banking application. Attackers can execute a command like “ps | grep insecure” to identify the process associated with the insecure banking application by using the command “su (PID) u0_a80 service call clipboard 2 s16 (.apk name) com.android.insecure-bank”, the attacker can retrieve the account number from the targeted application.
Mitigation strategies for this type of attack include avoiding clipboard usage whenever possible. Password managers like KeePass propose an alternative called Auto-Type, which directly fills targeted fields by simulating key presses, eliminating the need to store sensitive information in the clipboard. Additionally, configuring password managers to automatically clear the clipboard after a short amount of time further enhances security.
The Android operating system maintains a user dictionary that stores words entered by the user for future auto-correction. This dictionary is accessible to any app without requiring special permissions. Attackers can exploit this feature to retrieve sensitive information entered by the user.
For instance, an attacker could add a username to the user dictionary by selecting text and then retrieve this information from the user_dict database located in /data/data/com.android.providers. Use a dictionary/database. By querying the database with the command sqlite3 user_dict.db; select * from words, the attacker can access all the words added to the dictionary.
To mitigate this vulnerability, it is advisable to disable the auto-correct feature when it comes to any form of sensitive information, not just for password fields. Disabling caching and implementing a custom keyboard can provide additional protection against malware.
Let’s look at a practical example demonstrating the same:
1) Log in to the application using the default login credentials
Username: Dinesh
Password: Dinesh@123$
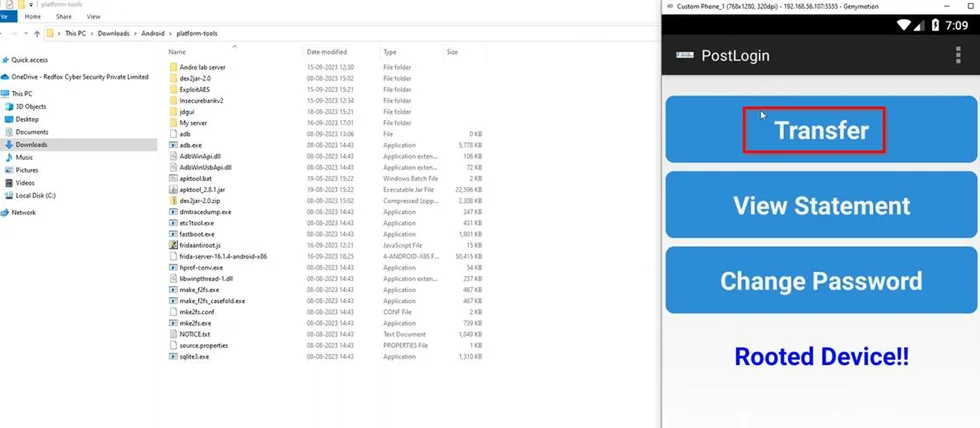
2) Click on the “Transfer” option within the application.
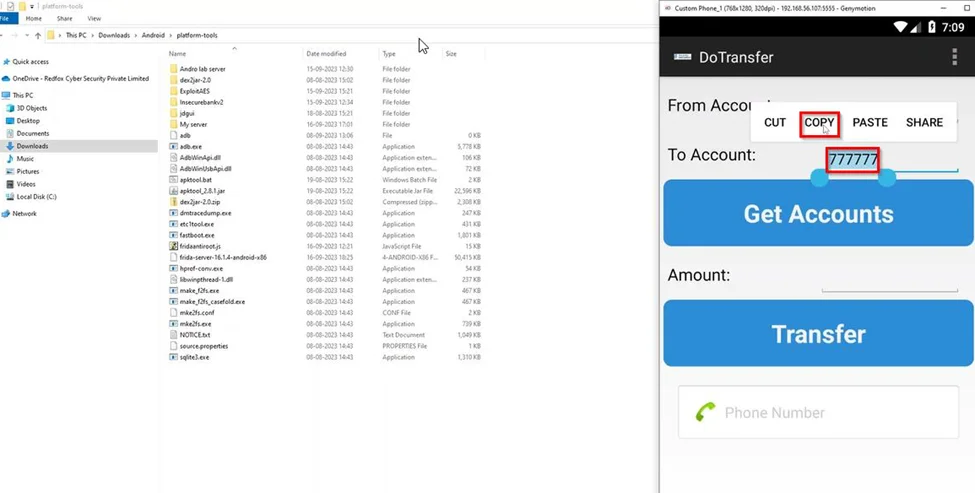
3) Enter the relevant account numbers into the designated fields for the transfer.
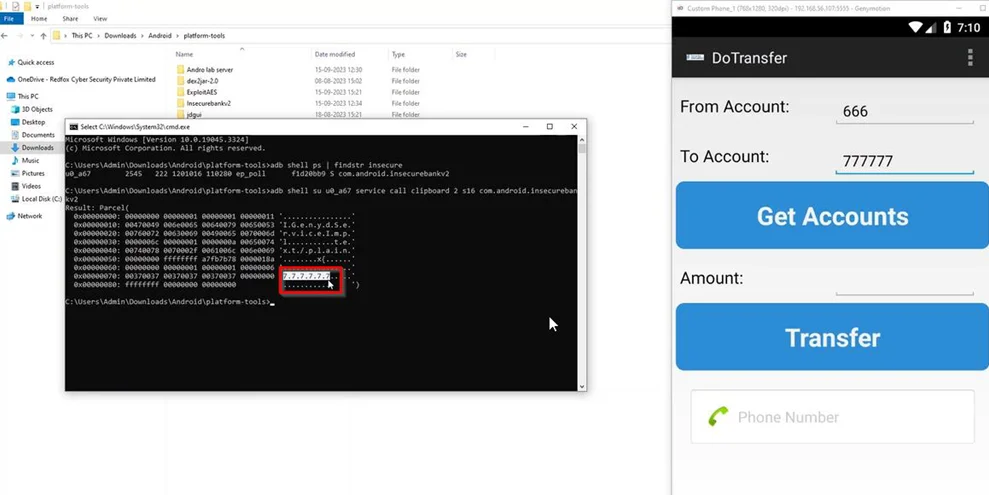
4) Select and copy the destination account number “777777” to your device’s clipboard.
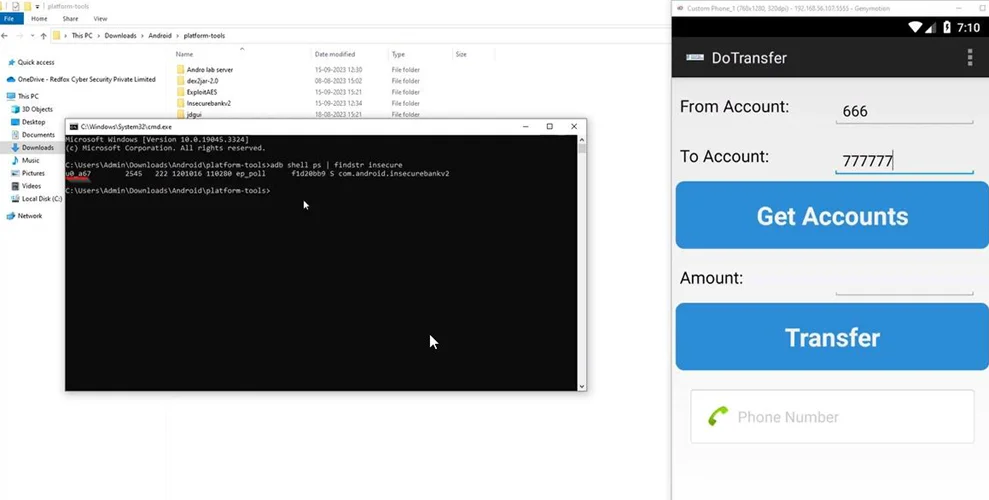
5) Open a command prompt (CMD) to utilize the Android Debug Bridge (ADB).
6) Execute the command “adb shell ps | findstr insecure” to identify any processes associated with the insecure bank application.
7) Note that command variations may exist between Windows and Linux environments.
8) Observe the process list to locate the one associated with the application, typically denoted as “u0_a67” here.
9) Next, use the command “adb shell sy u0_a67 service call clipboard 2 s16 com.android.insecurebankv2″ to access information from the user’s clipboard.
10) Observe that any data copied by the user to the clipboard is visible within the ADB shell, potentially revealing sensitive information.
To ensure the security of your sensitive information, it is essential to implement best practices for securing the Android clipboard. By following these recommendations, you can minimize the risks associated with clipboard-based attacks:
Whenever possible, avoid using the clipboard to store sensitive information. Instead, utilize password managers or other secure methods to directly input data into target fields.
If you must use the clipboard for temporary storage, configure your applications to automatically clear the clipboard after a short period. As a result, this reduces the window of opportunity for attackers to intercept copied data.
Raise awareness among users about the risks associated with the Android clipboard. Encourage them to be cautious when copying and pasting sensitive information, especially in public or shared environments.
Developers should follow secure coding practices to minimize the risk of clipboard-based vulnerabilities. This includes validating input, sanitizing data, and encrypting sensitive information before storing or sharing it.
Make sure you keep your applications and the Android operating system up to date with the latest security patches. Usually, software updates include fixes for known vulnerabilities, reducing the risk of clipboard-related attacks.
Implement monitoring mechanisms to detect any suspicious clipboard activity. By monitoring clipboard events, you can identify potential attacks and take appropriate action to mitigate the risk.
Make sure you only install applications from trusted sources such as the Google Play Store. Malicious applications from untrusted sources may contain malware designed to exploit clipboard vulnerabilities.
Install reputable antivirus and security applications on your Android devices. These applications can help detect and prevent clipboard-based attacks by scanning for known threats and suspicious behavior.
Implement two-factor authentication (2FA) wherever possible to provide an additional layer of security. Even if an attacker gains access to your clipboard, they would still require the second factor to authenticate successfully.
Regularly back up your Android device and ensure the backups are encrypted. In the event of a clipboard-related attack or data loss, having encrypted backups can help you restore your information securely.
By implementing these best practices, you can significantly reduce the risk of clipboard-based attacks and protect your sensitive information on Android devices.
The Android clipboard is a valuable tool for users, but it also presents significant security risks. Attackers can exploit vulnerabilities in the clipboard’s functionality to intercept, manipulate, or exfiltrate sensitive information. By understanding these risks and implementing the best practices outlined in this article, you can secure your Android device against clipboard-based attacks. Remember to minimize clipboard usage, educate users about security risks, follow secure coding practices, and keep your applications and operating system up to date. With these measures in place, you can confidently protect your sensitive information from unintended exposure and maintain a secure mobile environment.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems, and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“