
In the realm of mobile app security, iOS penetration testing plays a pivotal role in identifying and mitigating vulnerabilities. This comprehensive guide combines iOS vulnerabilities with Objection, an essential tool for assessing and securing iOS applications. We will explore common iOS vulnerabilities in-depth, provide thorough explanations, and offer Objection commands with practical examples to detect and address these security issues effectively.
Objection is a powerful open-source runtime mobile application security assessment framework designed for assessing and interacting with iOS applications during runtime. It operates as a dynamic instrumentation toolkit built on top of Frida, offering a user-friendly command-line interface that security professionals and penetration testers can utilize to assess iOS app security.
Objection provides a wide range of features that facilitate runtime analysis, manipulation, and inspection of iOS apps. These features are instrumental in identifying security vulnerabilities and weaknesses within applications, making Objection an indispensable tool in the mobile app security testing toolkit.
Before you can leverage the capabilities of Objection, you need to ensure that it is correctly installed on your macOS system and that your target iOS device is properly configured. Here’s how you can get started:
Commands: Install Objection
pip install objection
This command uses Python’s package manager, pip, to install Objection. Ensure that you have pip installed on your system. Once Objection is installed, you can access its features from the command line.
Jailbreaking your iOS device provides the required level of access to apps for security testing. Frida-server must be installed on the iOS device to establish communication between Objection on your computer and the target app on the iOS device.
Keep in mind that the exact process may vary depending on your iOS device and jailbreak status. Refer to relevant documentation and guides for your specific device and iOS version to ensure proper setup.
With Objection correctly installed and your iOS device set up for testing, you’re ready to delve into the world of iOS penetration testing and security assessment.
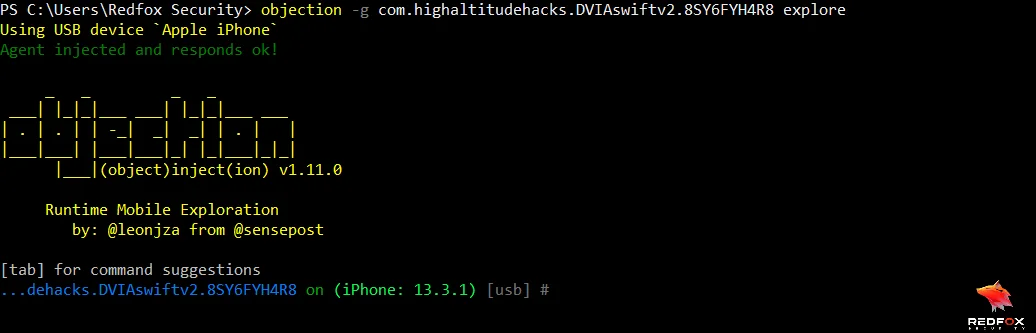
Understanding Objection and its installation and setup process is the foundation for effectively using this powerful tool to identify and address security vulnerabilities in iOS applications. In the following sections, we’ll explore common iOS vulnerabilities and demonstrate how Objection can be employed to detect and mitigate these issues, providing practical examples and commands for each vulnerability.
Vulnerability 1: Insecure Data Storage
Insecure data storage refers to storing sensitive information, such as passwords or API keys, in an unprotected manner, making it accessible to attackers.
Example: Suppose an iOS app stores user passwords in plaintext within a local file. An attacker gaining access to the device’s file system can easily extract and misuse these credentials.
Command: Check for Insecure Data Storage (plist)
ios plist cat <file>.plist
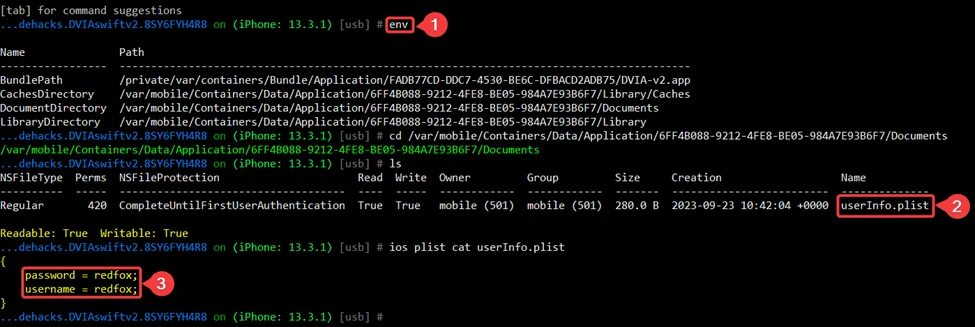
This command command is used to display the contents of a property list (plist) file on an iOS device. A property list is a structured data format commonly used in iOS and macOS applications to store configuration and other data.
Inadequate network security occurs when apps communicate without secure protocols, making data transmission susceptible to interception.
Example: An iOS app communicates with a server without using HTTPS, allowing an attacker to intercept sensitive data during transmission.
Command: Assess Network Security
ios sslpinning disable
This command is used to bypass SSL certificate pinning, which is a security feature that prevents communication with servers that use untrusted SSL certificates. This command allows testers to assess network security and identify potential vulnerabilities.
For more info, navigate to our Blog on Bypass SSL pinning on iOS Application
Weak authentication mechanisms can lead to unauthorized access to user accounts.
Example: An app allows users to have weak passwords with no complexity requirements, making it susceptible to brute force attacks.
Command: Check Authentication Weaknesses
ios jailbreak disable
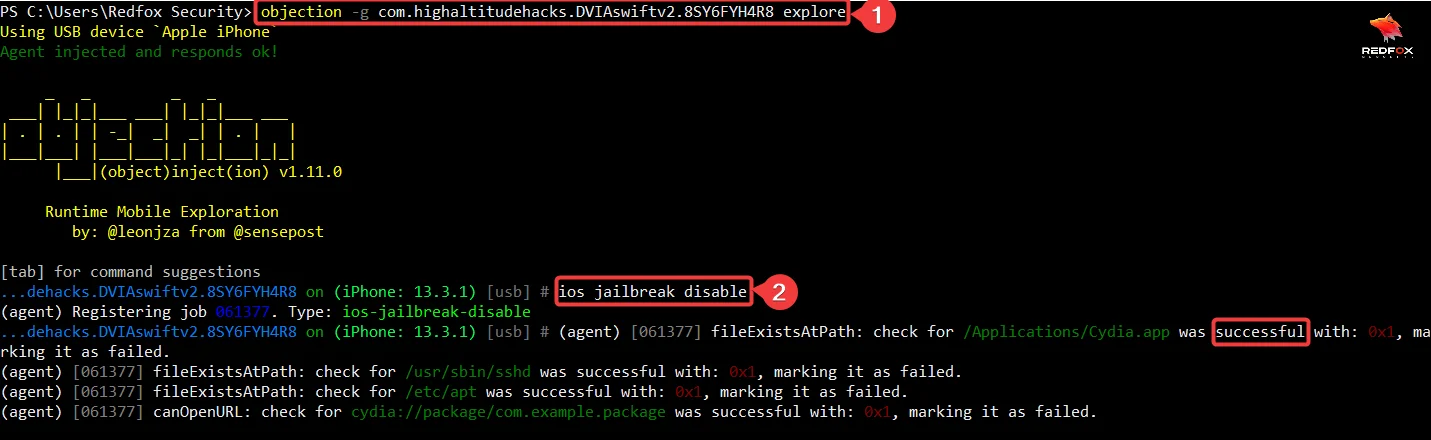
This command is used to attempt to disable or bypass jailbreak detection mechanisms within an iOS app. Jailbreak detection is a security feature that some iOS apps use to check if the device they are running on has been jailbroken.
Side channel attacks typically involve monitoring and analyzing unintended information leakage through various channels, such as timing, power consumption, or network traffic.
Example: An attacker could capture Device logs, Cookies, or other sensitive information.
Command: Inspect Data Transmission
ios cookies get --json
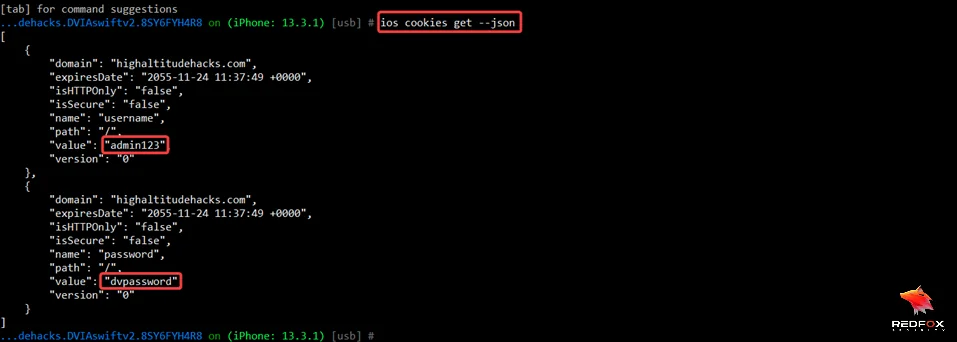
This command is used to retrieve and display the cookies associated with a specific iOS application in JSON format. Cookies are often used for session management and data storage in web applications. When used with the –json option, this command provides the cookie data in a structured JSON format, making it easier to analyze and manipulate.
Code vulnerabilities, like buffer overflows, can compromise app security.
Example: A buffer overflow vulnerability could allow an attacker to execute arbitrary code within an app’s context, potentially compromising the device or user data.
Command: Check for Code Vulnerabilities
ios hooking search "insecure function."
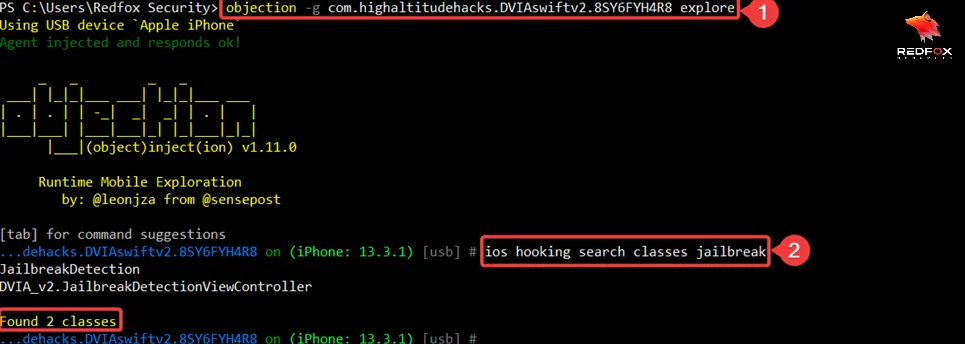
This command searches for instances of insecure or vulnerable functions within the app’s code. It helps testers identify potential code vulnerabilities that attackers could exploit.
Keychain data vulnerability involves mishandling sensitive information stored in the iOS Keychain, such as cryptographic keys, passwords, or certificates.
Example: An app stores user passwords in the Keychain without proper access controls, allowing unauthorized access to these credentials.
Command: Inspect Keychain Data
ios keychain dump
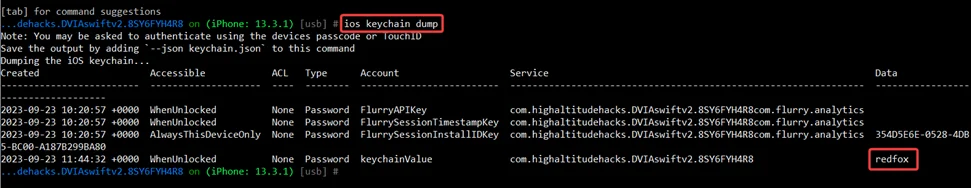
This command is used to inspect the contents of the iOS Keychain. It helps testers identify any mishandling of sensitive data stored in the Keychain, such as improper access controls or unprotected storage.
Pasteboard vulnerability occurs when sensitive data is copied to the iOS pasteboard (clipboard) and remains accessible to other apps or attackers.
Example: An app inadvertently leaves sensitive information on the pasteboard after a user action, potentially exposing this data to malicious apps.
Command: Check Pasteboard Data
ios pasteboard monitor
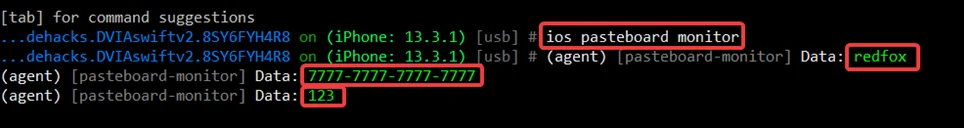
This command monitors the iOS pasteboard for any sensitive data that may be inadvertently exposed. It helps testers identify issues related to pasteboard security and data leakage.
Ethical and legal considerations are crucial when conducting iOS penetration testing with Objection.
Tips:
Keeping your tools up to date is essential for leveraging the latest features and security enhancements.
Command: Update Objection
pip install --upgrade objection
By combining iOS vulnerabilities with Objection, you can enhance your iOS penetration testing capabilities. This comprehensive guide provides insights into common iOS vulnerabilities, explanations of each issue, and Objection commands with practical examples to identify and address security risks effectively. Whether you’re a seasoned security professional or just beginning your journey, Objection is a valuable tool to include in your arsenal for robust iOS app security testing.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems, and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.