
With this comprehensive guide, we aim to demonstrate how the Joint Test Action Group (JTAG) interface can provide hardware security. Created during the 1980s by the Joint Test Access Group, JTAG revolutionized PCB testing and debugging processes; using our multi-part series, you’ll learn to harness its power for security research, firmware extraction, and memory manipulation.

JTAG stands for Joint Test Action Group and was created to address hardware testers’ difficulties in testing increasingly miniaturized PCBs. Traditional methods, like bed-of-nails and external probing, had become ineffective and time consuming; JTAG provides an efficient means of programming, debugging and testing PCBs without incurring these limitations.
JTAG is widely utilized for boundary scan testing. This technique facilitates efficient interconnect testing on complex PCBs. JTAG utilizes a shift register to facilitate comparison between input and output data to detect faults and ensure electrical connectivity between components.
To fully comprehend JTAG, it’s crucial to gain an in-depth knowledge of its architecture and signals that drive its interface. The architecture for JTAG boundary scanning typically includes a shift register, multiple cells, and a Test Access Port (TAP). Let’s delve further into each component.
The shift registers act as a crucial link between the components connected to JTAG. It facilitates the movement of data in a serial manner, enabling testing and manipulation of interconnects.
Cells strategically positioned within an integrated circuit’s core logic serve as the link between its shift register and I/O pins or balls of the chip. Created using multiplexer and latch circuits, these cells produce an uninterrupted serial data path for testing purposes.
The Test Access Port acts as the gateway to the shift register. JTAG technology allows external devices to connect directly with its interface and begin testing, debugging or programming operations.
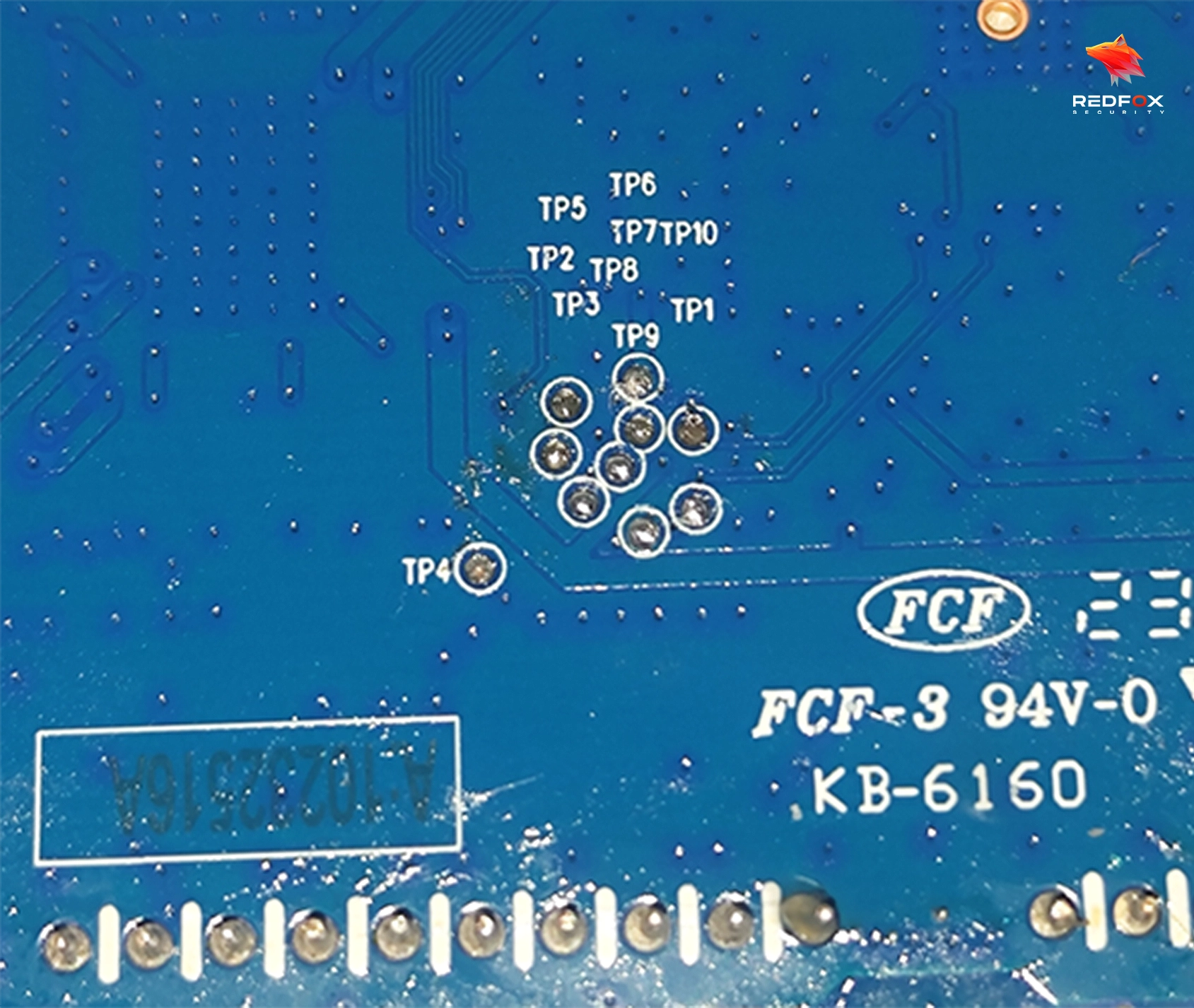

To take full advantage of JTAG, it is crucial to identify and connect to a target device using its pinout. The pinout refers to the physical arrangement and configuration of JTAG interface which may change depending on device design, vendor selection and chip architecture.
When attempting to identify the pinout, several methods can prove useful. One approach involves tracing the JTAG header to the corresponding chip on the PCB. By identifying the chip architecture, it is often possible to map it to one of the standard pinouts, such as ARM, MIPS, or vendor-specific configurations.
Another method involves measuring the voltages and resistances of the pins to identify key signals like GND, VCC, and pull-up or pull-down resistors. By comparing these measurements to known JTAG port configurations, it becomes possible to determine the correct pinout.
In conclusion, JTAG is a powerful tool that unlocks the potential of hardware hacking. JTAG was originally developed to assist testers and debuggers with debugging complex PCBs, but has become an indispensable asset in hardware security research. By understanding its architecture, signals, and vulnerabilities, it allows researchers to use JTAG to extract firmware, manipulate memory or perform other security research actions.
While insecure JTAG interfaces pose significant security threats, their full power should still be utilized while mitigating potential dangers. By identifying pinout and creating a secure connection, JTAG’s potential can be fully realized while minimizing risks associated with its usage.
Never misuse JTAG! Remember its power responsibly and ethically for best results. Use what you learn about JTAG to increase security, protect devices and contribute to advancement of hardware hacking techniques. Stay tuned for part two of our JTAG series where we will explore Identifying and verifying JTAG in hardware security research.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
Join us on our journey of growth and development by signing up for our comprehensive courses.