
All Apple mobile devices, including the iPhone, iPad, and iPod, run on iOS, a platform jointly developed with the Darwin foundation.
With iOS, the hardware device is managed and the technology needed to create applications for the platform is provided, unlike other significant operating systems.
A few commonly used system apps are included as part of the device’s basic software package. These include Mail, Calendar, Calculator, Phone, Safari, and others.
For security and commercial reasons, it is not possible to run iOS and Mac OS X on any hardware other than Apple’s, and it is prohibited to use iOS on any other mobile device other than Apple’s. As we will discuss in the iOS Jailbreaking blog, this has made it easier for jailbreakers to discover iOS jailbreak attacks. With over 1 million apps available on the App Store, the attack surface for applications has greatly increased.
The layering of the iOS architecture involves packaging of technology into frameworks. A framework normally includes header files, pictures, and all the dynamically shared libraries that are required. The layers of the iOS software stack are shown in the following image:
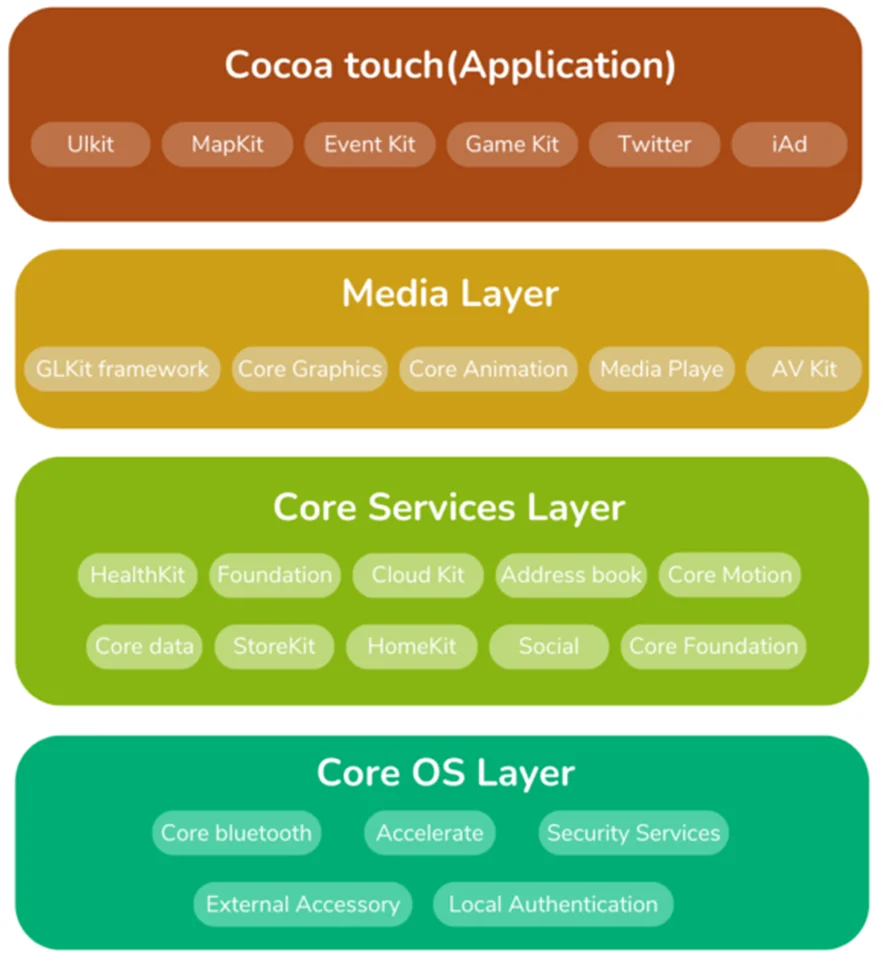
There are four abstraction levels in it.
Because of several reasons, including object-oriented abstractions, the ease of writing code with fewer lines, and the ability to encapsulate other features, majority of developers choose higher-level frameworks as development gets started. One must, however, take care to prevent their higher-level frameworks from exposing them if they use lower-level frameworks. Because those frameworks are used in the majority of development operations, they have a larger attack surface than lower-level frameworks. Let’s now investigate the various abstract layers.
The final layer in the iOS stack, it resides immediately atop the hardware of the device. Low-level features that form the basis of all iOS features are provided by the Core OS layer. In addition to the standard functions of a fundamental operating system, such as memory management, file system handling, and threads, it also offers a number of services, including low-level networking and access to external accessories.
The bottom level features that most other technologies are based upon are stored in the Core OS layer.
iOS 7’s 64-Bit support facilitates the creation of 64-bit applications and speeds up their performance.
The services offered by the Core OS layer are abstracted by the Core Services layer. It provides basic services that all apps can use. The core services layer, like the other layers, provides a set of frameworks:
You can use multimedia services from the Media layer on your iPhone. It makes the system’s entire graphics, audio, and video technology possible. It enables the developer to work with graphics-like elements like animations, photographs, movies, and audio. Apple frequently offers feedback on multimedia experiences, especially about the audio and video quality. The iOS stack’s media layer, which gives the iOS access to audio, video, graphics, and AirPlay (over-the-air) capabilities, essentially fills this duty. Similar to the Cocoa Touch layer, the media layer has a number of frameworks that programmers can use:
The Cocoa Touch layer offers an abstraction layer that makes the various libraries for iPhone and other iOS device programming accessible. A vital group of Objective-C frameworks that were created using the Mac OS X Cocoa API is included with the Cocoa Touch layer. Any iOS app you encounter has an aesthetic that was created with the Cocoa Touch framework. This layer supports notifications, multitasking, touch-specific inputs, all high-level system services, and other important technologies. It also offers fundamental infrastructural support for an app.
The list of significant frameworks that are frequently used in this layer is as follows:
Understanding how iOS architecture works is an excellent place to start when it comes to iOS penetration testing. We will be talking more about iOS app and device security in upcoming blogs. .
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. With a combination of data-driven, research-based, and manual testing methodologies, we proudly deliver robust security solutions.
“Join us on our journey of growth and development by signing up for our comprehensive courses, if you want to excel in the field of cybersecurity.”