In this blog, we are going to discuss jailbreaking, its advantages and disadvantages, as well as types and the steps for carrying out a successful jailbreak.
The technique of circumventing a smart device’s internal defenses to get total control of the operating system is known as rooting or jailbreaking, but it puts the device’s security at risk. The sole distinction between these two concepts is that rooting refers to Android devices, whereas jailbreaking refers to iOS devices. So, whereas rooting an Android device implies getting beyond Google’s security limits, jailbreaking an iOS device involves getting around Apple’s restrictions. However, due to Apple’s “Walled Garden“ Strategy, the jailbreaking procedure necessitates pulling down these “walls” or “jails” before attempting to get root access. It is frequently accomplished by locating and exploiting a flaw in the operating system. Rooting grants the user administrative privileges, allowing them to totally replace the operating system if they so wish. Jailbreaking does not confer admin powers, but it does give users additional access to their device through the use of tweaks, which are included in supplementary applications such as Cydia.
Why jailbreak an iOS device?
To acquire more control.
The attractiveness of jailbreaking derives from the user’s ability to have total control over their gadgets. These are the following things you will get after jailbreak.
App installation: Apple is passionate about security, thus only those apps that pass their severe security tests are allowed into the app store. On an iOS device, only apps from the app store may be installed. Users can install third-party applications after jailbreaking their devices.
Uninstalling pre-installed apps: Some apps come pre-installed, and while the majority of users never use them, they are not permitted to be removed. Users with root privilege can remove these unwanted apps.
Switch carriers: Apple isn’t keen on changing its default network providers. Jailbreaking might be useful for unlocking, changing networks, or switching to a different carrier temporarily.
Controls: People also jailbreak their gadgets because they despise being told what they can and cannot do with their devices.
Customization: Apple is committed to providing a high-quality user experience to all of its customers. And they do so by ensuring that everyone utilizes their standard features while providing little space for customization. Users with root access have the ability to modify all of this.
Types of jailbreaks
Tethered: This is a temporary jailbreak and requires the device to be connected to a computer every time the device needs a restart. The jailbreak is reversed otherwise.
Semi-tethered: This jailbreak can’t be re-applied unless the device is connected to a computer during reboot. The device can also boot into non-jailbroken mode on its own.
Semi-untethered: These jailbreaks allow the device to boot on its own, but the kernel patches (or user-land modifications) for disabling code signing aren’t applied automatically. The user must re-jailbreak the device by starting an app or visiting a website (not requiring a connection to a computer, hence the term untethered).
Untethered: This is the more sought-after solution, where the device only needs to be connected to the computer at the time of initial jailbreak. Rebooting the device does not reset the jailbreak.
Risks of jailbreaking
he following are some of the risks associated with jailbreaking:
- The Device warranty will be revoked.
- Upgrade of software will stop until a jailbroken version is released.
- Security flaws have increased.
- Battery life has been reduced.
- The device’s volatility has increased.
- Built-in features aren’t working as they should.
- There’s a chance you’ll get infected with malware.
- Because of the OS differences between jailbroken and non-jailbroken smartphones, they are more vulnerable to hackers.
- Dropped calls, unreliable data connections, and erroneous or delayed location data.
- It has the potential to brick the gadget.
Steps to jailbreak an iPhone device
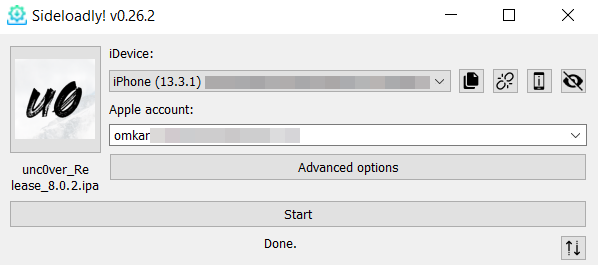
Step1: Install Sideloadly on a Windows machine.
Step 2: Download the unc0ver IPA file.
unc0ver Jailbreak is a semi-untethered jailbreak tool, which implies that the installed jailbreak applications will crash if you reboot your iOS device. unc0ver is the only jailbreak tool that is being updated right now, and it works with iOS 11 to iOS 14.8.
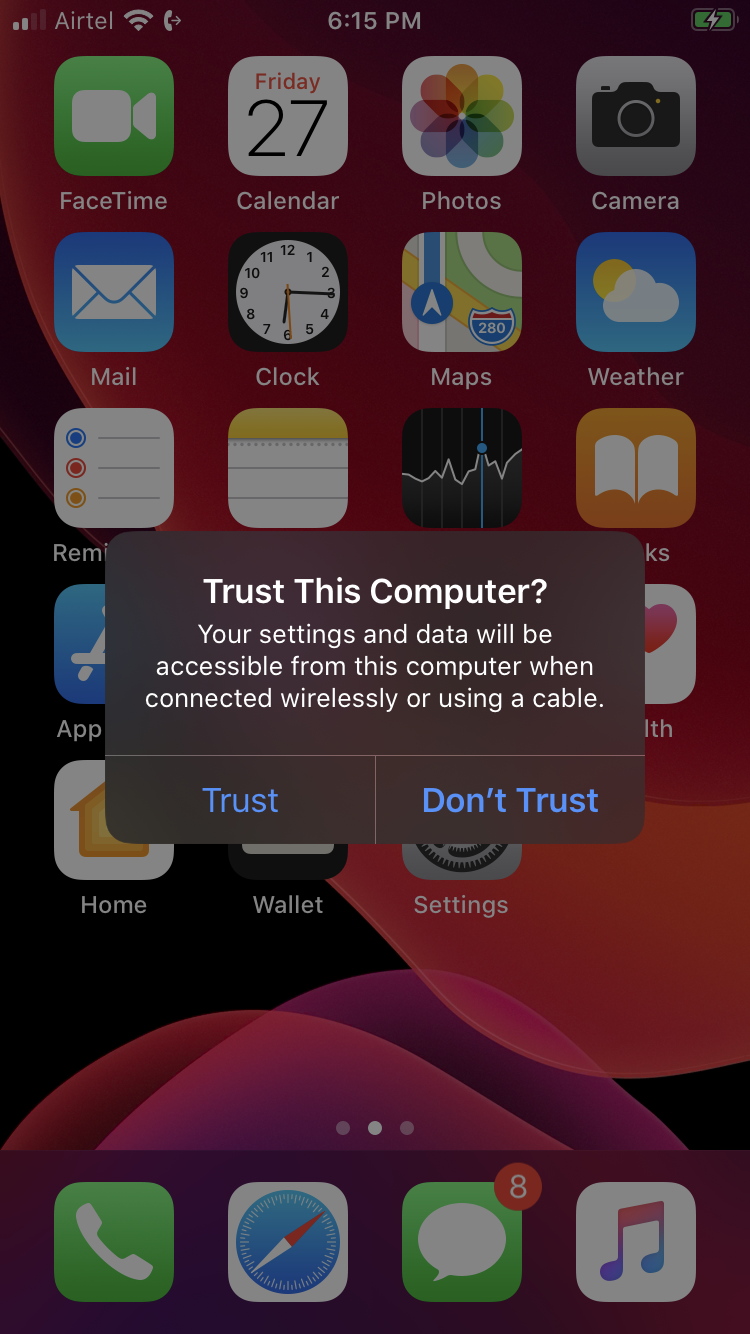
Step 3: Connect the iOS device to the Windows machine and give access as a trusted user.
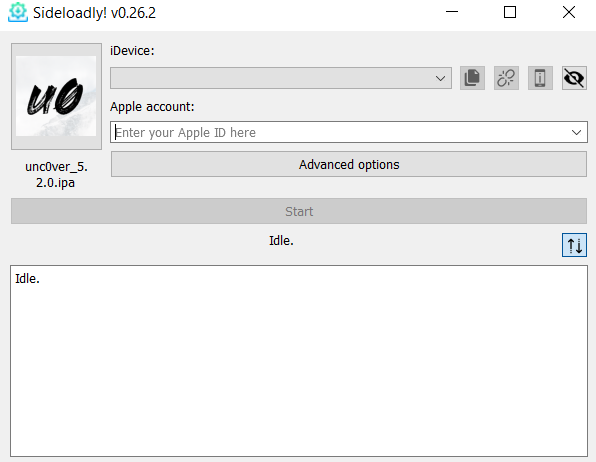
Step 4: Upload the unc0ver IPA in Sideloadly.
Step 5: Select the device and enter the Apple ID username and password.
Step 6: Press the start button. This loads the uncover application on your device.
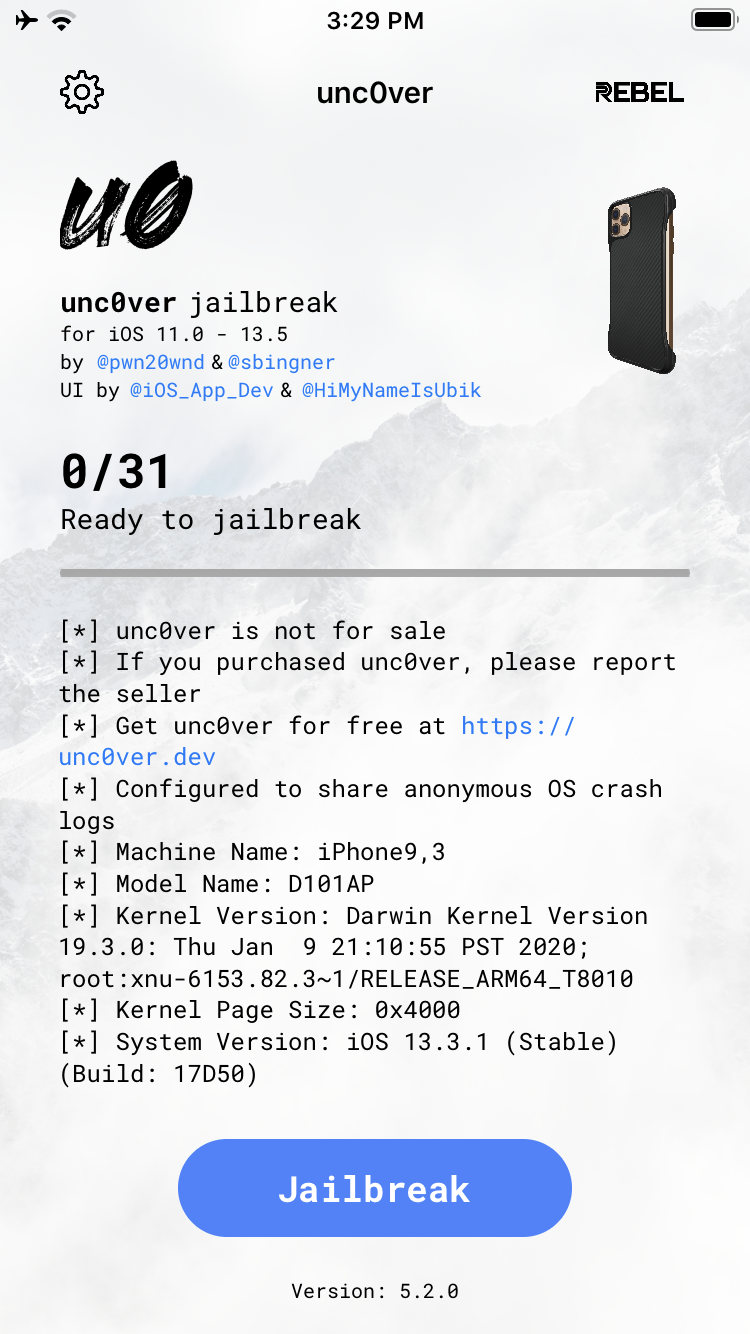
Step 7: Now open the unc0ver application on your device.
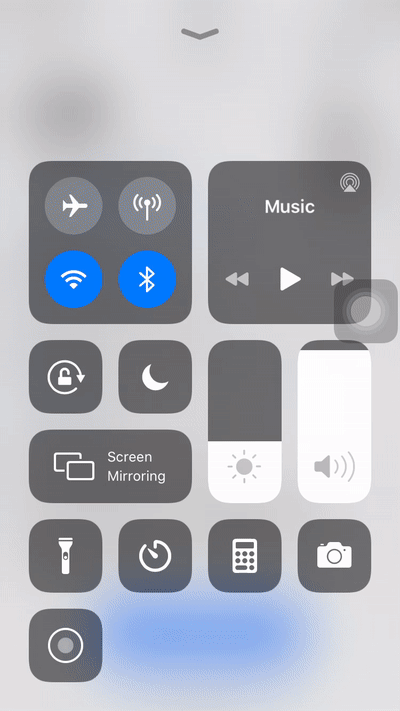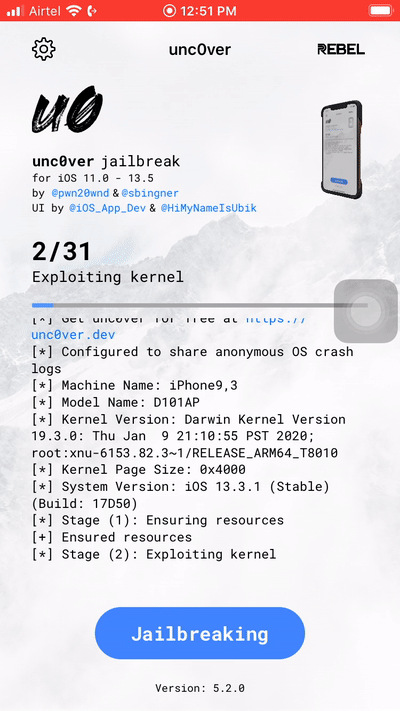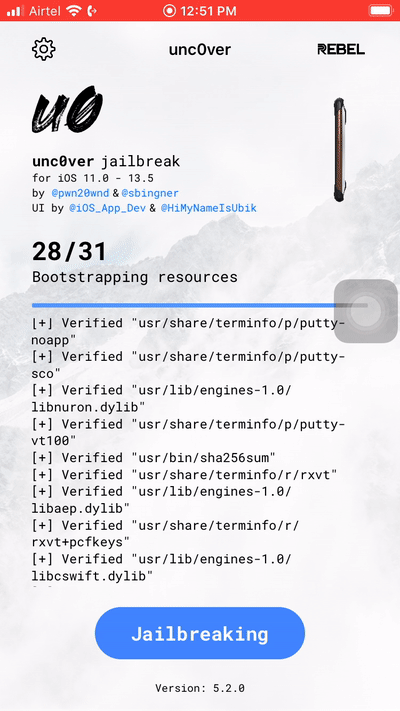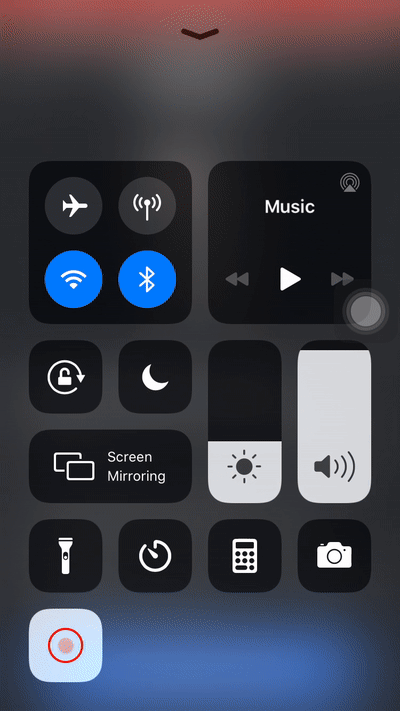
Step 8: Press the jailbreak button and wait till the device reboots a few times.
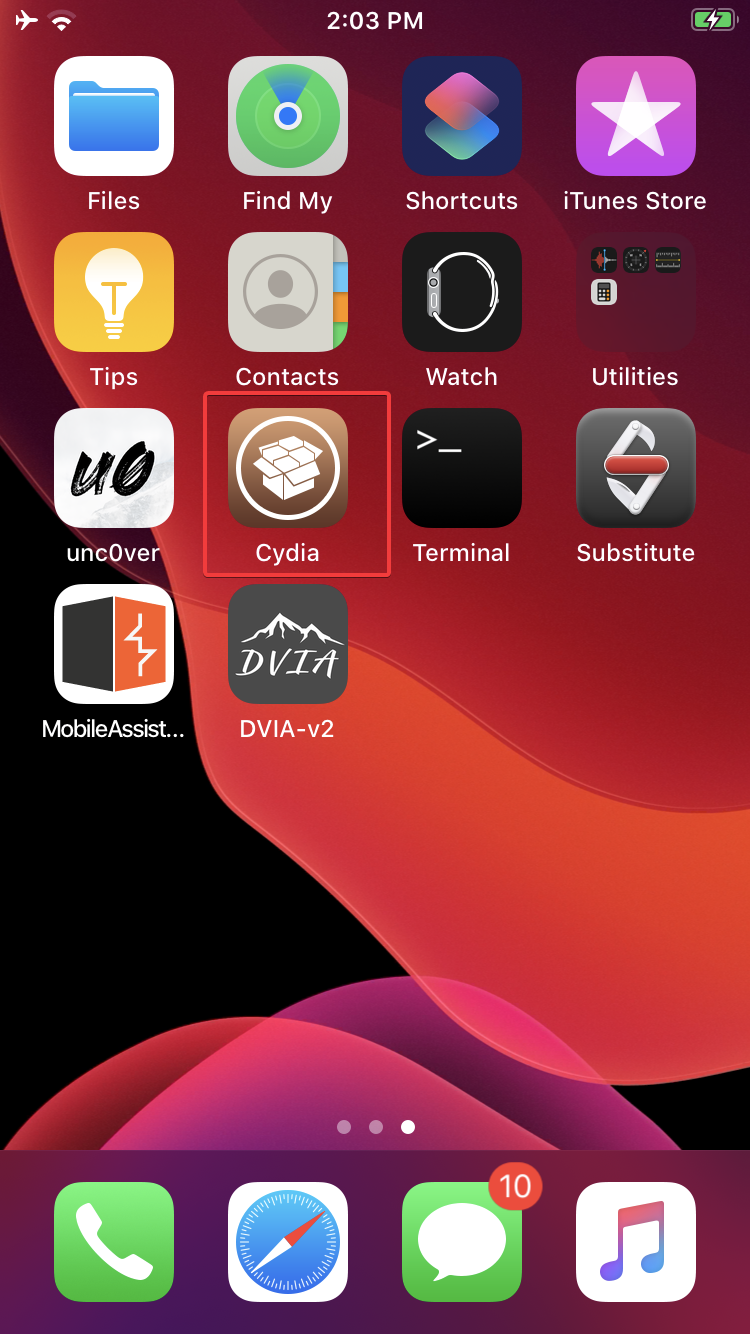
Step 9: After the final reboot observer that Cydia has been installed on your device.
Cydia is a graphical user interface of APT (Advanced Package Tool) for iOS. It enables a user to find and install software not authorized by Apple on jailbroken devices. It also refers to digital distribution platform for software on iOS accessed through Cydia software.
In this blog, we discussed jailbreaking, its advantages and disadvantages, as well as its types and the steps for carrying out a successful jailbreak. Stay connected with Redfox Security for more insights into iOS penetration testing.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. With a combination of data-driven, research-based, and manual testing methodologies, we proudly deliver robust security solutions.
“Join us on our journey of growth and development by signing up for our comprehensive courses, if you want to excel in the field of cybersecurity.”