
As technology continues to advance, so do the methods used by hackers and security enthusiasts to explore vulnerabilities in everyday devices. One such device that has attracted the attention of hackers is the wireless doorbell. In this blog, we will dive into the world of hacking wireless doorbells, exploring the process of reverse engineering the signal, capturing and analyzing the transmission, and even replicating the signal for a replay attack. So, fasten your seatbelts and get ready to unlock the secrets of home security!
Wireless doorbells have become a popular choice for homeowners due to their convenience and ease of installation. These devices typically consist of a transmitter button placed near the door and a receiver that emits a sound or light alert when the button is pressed. The communication between the transmitter and receiver is done wirelessly, using radio frequency (RF) signals.

While wireless doorbells offer convenience, they may also pose security risks. Hackers can exploit vulnerabilities in these devices to gain unauthorized access to your home or compromise your privacy. By hacking a wireless doorbell, you can better understand the potential weaknesses and take steps to enhance its security.
Reverse Engineering the Signal
To begin the hacking process, you need to reverse engineer the signal used by the wireless doorbell. This involves identifying the frequency and modulation of the signal, which can vary depending on the region and manufacturer. Let’s explore the steps involved in this process.
Step 1: Finding the Frequency
The first step is to determine the frequency at which the wireless doorbell operates. This can be done using a Software Defined Radio (SDR) and SDR software such as SDR# or GQRX. These tools allow you to scan and identify the RF signals in your vicinity.
Step 2: Analyzing the Signal
Once you have identified the frequency, you can capture and analyze the signal using tools like rtl_433 or Universal Radio Hacker. These tools enable you to record the signal and examine its waveform, decoding the binary representation of the signal.
Step 3: Replicating the Signal
Now that you have decoded the signal, you can replicate it using an Arduino or a Hack RF device. By connecting a transmitter module to the Arduino, you can send the captured signal, effectively replicating the wireless doorbell’s transmission.
To capture and analyze the signal, you will need some additional tools and software. Let’s explore the steps involved in this process.
Step 1: Choosing the Right Tools
To capture the signal, you will need an SDR device such as the Hack RF One or an RTL-SDR dongle. These devices allow you to receive and analyze RF signals. Additionally, you will need software such as GQRX or SDR# to visualize and record the signal.

Step 2: Identifying the Frequency
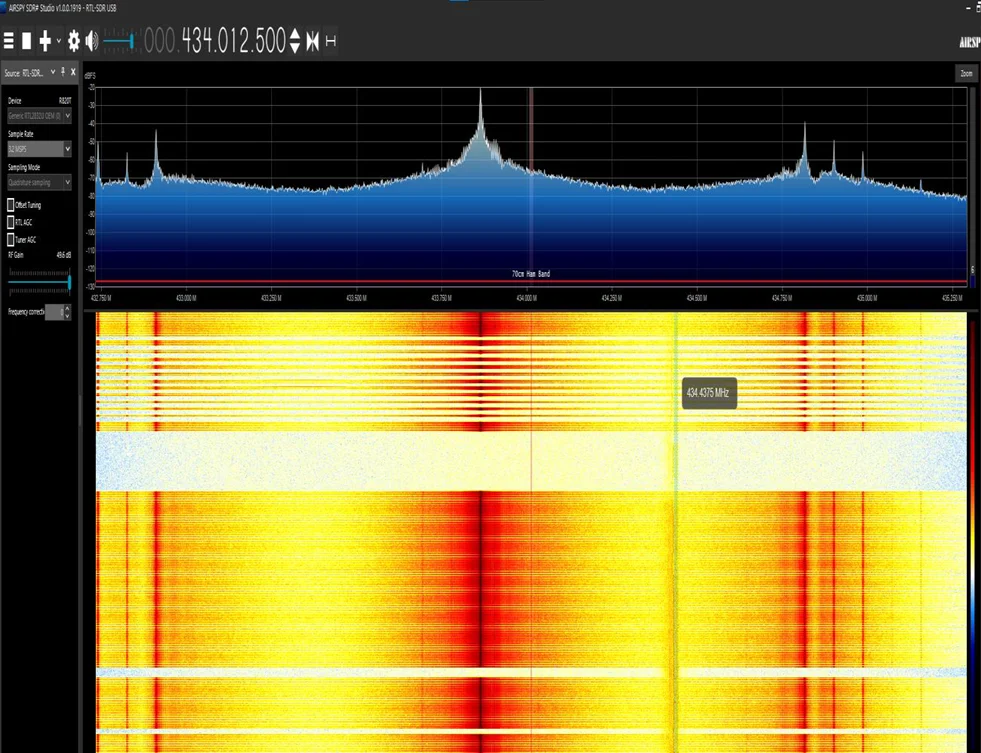
Using the SDR device and software, scan the RF spectrum to identify the frequency at which the wireless doorbell operates. This information is crucial for further analysis and replication of the signal.
Here are the common frequencies consumer RF equipment generally operate on:
Step 3: Recording the Signal
Once you have identified the frequency, start recording the signal using the SDR software. Make sure to save the recorded signal in a format that can be analyzed later, such as a RAW file.
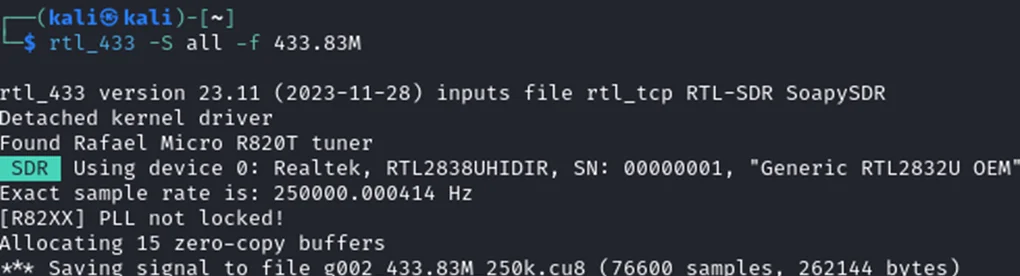
Step 4: Analyzing the Signal
To analyze the captured signal, you can use software such as Audacity or Universal Radio Hacker. These tools allow you to visualize the waveform, isolate button presses, and decode the binary representation of the signal.
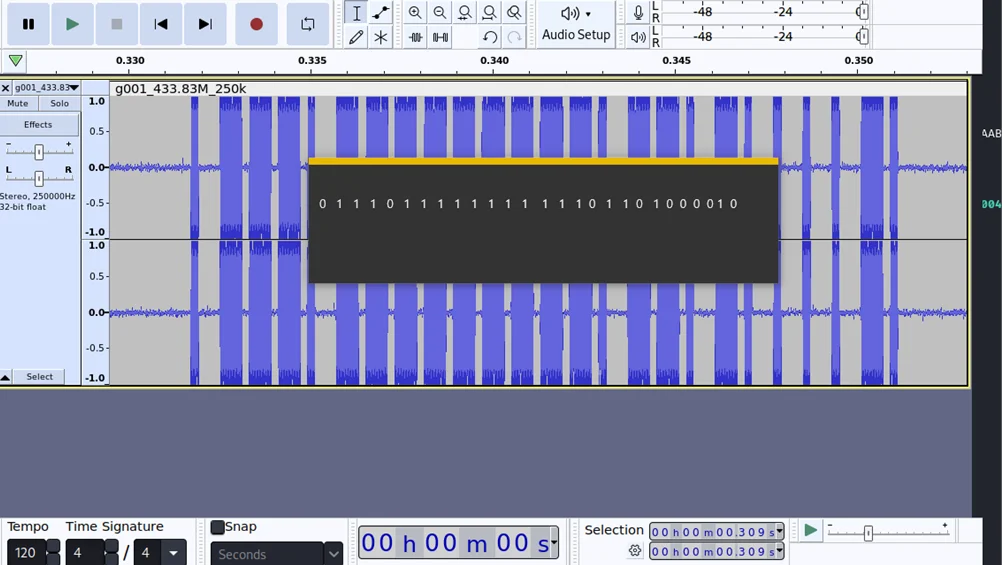
Now that you have captured and analyzed the signal, it’s time to replicate it and perform a replay attack. Let’s explore the steps involved in this process.
Step 1: Choosing the Right Hardware
To replicate the signal, you will need an Arduino or a HackRF device. The Arduino is a versatile microcontroller board that can be programmed to transmit the captured signal. Alternatively, the HackRF device offers more advanced capabilities for signal replication.
Step 2: Wiring the Transmitter Module
Connect the transmitter module to the Arduino or HackRF device following the wiring diagram provided by the module manufacturer. Make sure to provide the necessary power supply to the transmitter module.
Step 3: Writing the Code
Using the Arduino IDE or other programming software compatible with the chosen device, write the code to transmit the captured signal. This code will control the transmitter module to replicate the wireless doorbell’s signal.
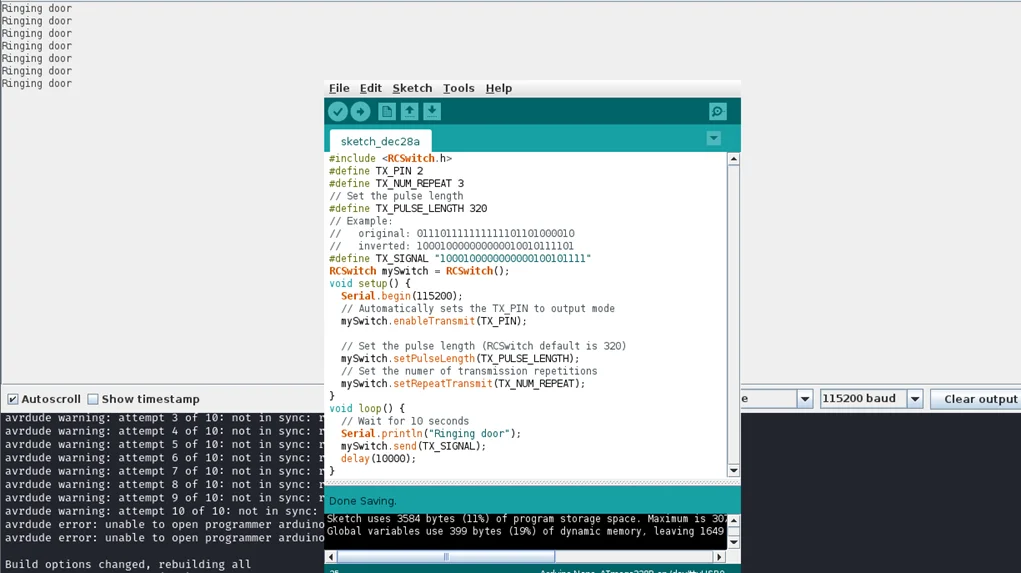
Step 4: Testing the Replication
Upload the code to the Arduino or configure the HackRF device to transmit the replicated signal. Test the replication by observing the behavior of the wireless doorbell when the replicated signal is transmitted.
While hacking wireless doorbells can help you understand their vulnerabilities, it’s equally important to enhance their security. Here are a few tips to improve the security of your wireless doorbell:
Hacking wireless doorbells can be a fascinating and educational experience. By reverse engineering the signal, capturing and analyzing the transmission, and replicating the signal for a replay attack, you can better understand the vulnerabilities of these devices and take steps to enhance their security. Remember to always practice responsible hacking and use this knowledge to protect your own home and educate others about potential security risks.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“