
IoT (Internet of Things) devices have revolutionized our lives and workplaces in unimaginable ways, from smart homes to industrial automation systems. But as more devices connect online, additional security requirements arise; Bluetooth Low Energy and ZigBee protocols are discussed as key protocols protecting IoT devices in this article.
Bluetooth Low Energy (BLE) is an energy-saving communication protocol developed specifically to support Internet of Things devices. BLE enables seamless data transmission among devices – ideal for wearables, home automation systems, and healthcare devices. BLE technology can also be subject to security threats from hackers and cybercriminals who

exploit its vulnerabilities for their gain.
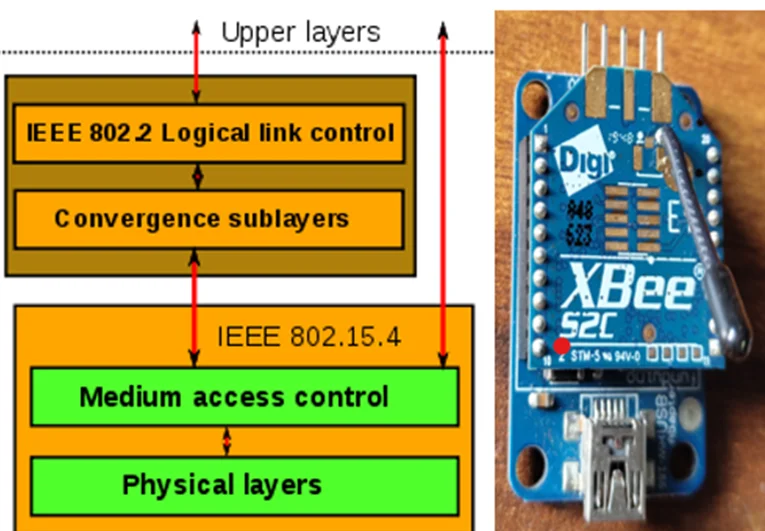
IEEE 802.15.4 protocol stack & Digi XBee S2C
ZigBee stands out with its self-healing network architecture, which enhances reliability, scalability, and multiple layers of protection (encryption algorithms and access controls to prevent unapproved devices from joining, making it suitable for healthcare monitoring systems and smart cities) while making deployment simple for deployment teams.
Securing IoT devices using BLE and ZigBee protocols requires taking an integrated approach. Here are a few best practices IoT device manufacturers and developers should enact to increase the security of their devices:
Updating the software on your IoT devices is really important for keeping them safe from possible security issues. Owners should make sure to check for and install updates regularly to stay protected from new types of attacks. This helps keep both you and your devices safe from potential security threats.
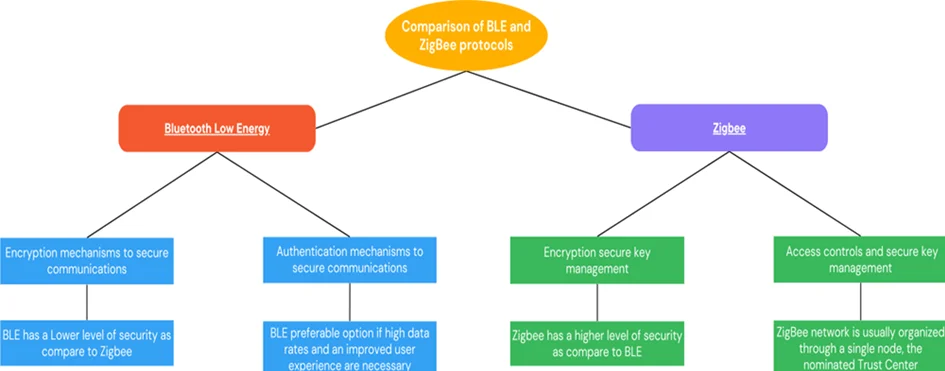
BLE and ZigBee protocols each offer security features to safeguard Internet of Things devices; however, their implementations of such features may differ significantly.
BLE offers encryption and authentication mechanisms to secure communications between devices; however, this type of communication could potentially open them up to spoofing attacks.
ZigBee boasts numerous robust security features, including encryption, access controls, and secure key management that further secure communication among devices. Mesh network topologies also add another layer of protection by enabling devices to communicate directly or via neighboring devices.
Both protocols can effectively safeguard IoT devices, but achieving optimal results requires strict adherence to the best practices and considerations specific to each protocol.
Numerous high-profile IoT security breaches have underscored the significance of protecting these devices. Attackers exploited BLE smart locks for unauthorized home entry, highlighting the need for robust authentication and encryption. Criminals recently breached a ZigBee home automation system, underscoring the importance of key management and access controls in ZigBee deployments. Such cases underscore the significance of BLE/ZigBee protocols as integral IoT device security protocols; manufacturers/developers must implement best practices while prioritizing security to reduce breach risks and protect end-user privacy.
Implement these steps to increase IoT security with BLE and ZigBee protocols:
With IoT ecosystem growth comes increasing concern about protecting IoT devices. BLE and ZigBee protocols play an essential role in protecting devices by offering encryption, authentication, and access controls that prevent unauthorized access to sensitive information. Elevating device security requires the adoption of best practices, regular security audits, staying current with updates, and auditing device inventories. Given the ever-changing threat landscape, adapting security measures is paramount. Prioritizing IoT security through protocols like BLE and ZigBee contributes to the overall strength of the IoT ecosystem.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2025 Redfox Cyber Security Inc. All rights reserved.