
As the use of IoT devices increases, ensuring their security becomes crucial. Unauthorized access should never occur due to proper protection measures in place on these devices. In this blog, we’ll take a closer look at a specific aspect of IoT security called hardware hacking, understanding its methods, benefits, and components to see how it helps keep IoT devices secure.
Hardware hacking involves altering existing hardware to identify weaknesses, gain unauthorized access, or extract critical information. Those who do hardware hacking use their skills to find security holes in IoT devices and exploit them.
As the use of IoT devices increases, the prevalence of hardware hacking has also risen. Ethical security assessments of hardware are crucial to protect data and networks. Security experts, using hacking techniques, can find weaknesses in IoT devices to make them safer from possible dangers. This helps protect user data and keeps systems safe from potential harmful attacks. This proactive approach protects user data while upholding system integrity while shielding it from possible attacks by adversaries.
Hardware hacking involves various components that contribute to its effectiveness as an IoT security practice. These components include:
This experimental method of hacking involves trial and error, where hardware components are replaced to achieve desired results. It is often used in Circuit Bending, a technique that explores the artistic possibilities of repurposing electronic devices.
This approach focuses on analyzing the communication between different hardware components. By connecting a hardware hacking tools to a circuit board, hackers can record and interpret signals, gaining insights into the functioning of the device.
In this method, hackers physically access debug ports that are meant to be inaccessible or closed. Hackers often gain access to a device through ports like JTAG, SWD, and UART that provide low-level access. Hackers using these ports may manipulate firmware updates, gain control of systems, exploit vulnerabilities, and compromise vulnerabilities.
Now that we have a fundamental understanding of hardware hacking, let us delve deeper into each of these components and explore the methods employed in IoT security assessments.
1) Exploring the Experimental Approach
Part/component replacement is a method often employed in hardware hacking to explore the possibilities of repurposing existing hardware. It involves replacing original components with alternative ones to achieve desired outcomes. This approach is highly experimental and relies on trial and error to discover new functionalities or exploit vulnerabilities.
2) Circuit Bending: Pushing Boundaries
A popular application of part/component replacement is Circuit Bending. This technique involves rewiring and modifying electronic devices to create new sounds, visuals, or behaviours. By manipulating the electrical connections within a device, hackers can generate unique and unexpected results. Circuit Bending pushes the boundaries of creativity and highlights the potential for unconventional uses of hardware.
3) Experimental Testbeds for IoT Security
In the context of IoT security assessments, part/component replacement serves as a valuable tool for creating experimental testbeds. By swapping out certain components, security professionals can simulate various attack scenarios, evaluate security measures’ effectiveness, and pinpoint potential vulnerabilities. This technique enables the creation of robust security protocols and ensures IoT devices remain resilient against potential threats.
1) Probing the Communication Channels
Analyzing inter-component communication is a fundamental method used in hardware hacking. By connecting a logic analyzer to the circuit board, hackers can tap into the communication channels between different hardware components. This allows them to observe and interpret the signals being transmitted, gaining valuable insights into the device’s inner workings.
2) Leveraging the Logic Analyzer
A logic analyzer is an indispensable part of a hardware hacking toolbox. By capturing digital signals, recording them, and visually representing data flow through analysis of these signals, hackers can gain insight into communication protocols, patterns, vulnerabilities, or weaknesses that could otherwise go undetected.
3) Unravelling the Device’s Behaviour
Through the analysis of inter-component communication, hackers can unravel the behaviour of the device under examination. Professional security analysts can gain invaluable knowledge of how various components interact, the flow of data and identify any points of vulnerability. With this insight comes an ability to strengthen defences against possible attacks while strengthening device defences against attacks from hackers.
The goal of hardware hacking is to dissect and analyze the internal components of the targeted device, particularly focusing on an IP camera. Our objective is to understand its structure, identify vulnerabilities, enhance capabilities, and contribute to hardware security research. In this case, we have considered an IP camera. Let’s take a closer look inside to understand how it works in more detail (after disassembling the camera module).

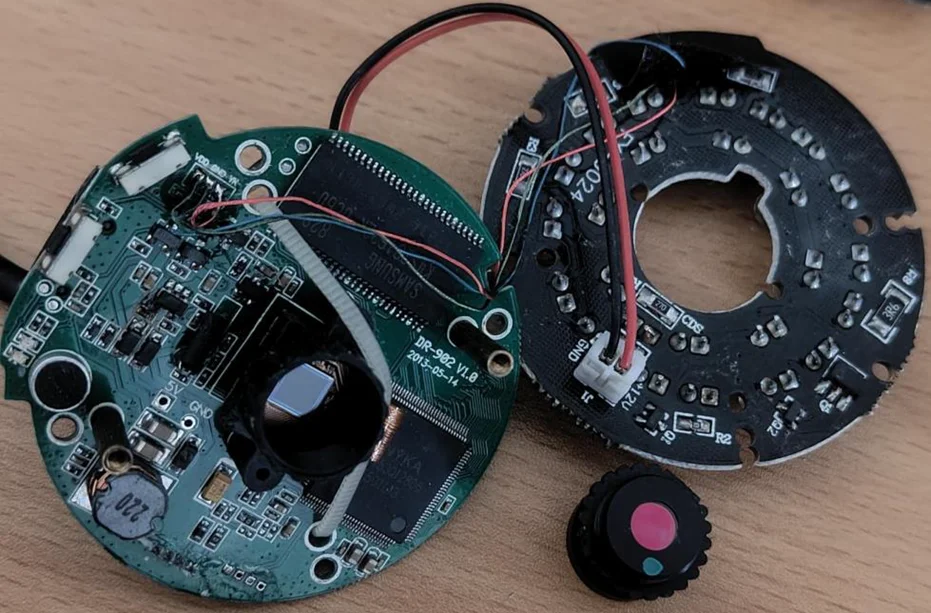
This interface facilitates communication, connecting the device to the broader virtual world, including the sensor network, cloud infrastructure, and mobile devices. The hardware interfaces responsible for network communication may incorporate dedicated microcontrollers or firmware to facilitate communication functionalities. In terms of potential vulnerabilities, the attack surface in this scenario resides within the firmware or driver code governing low-level communication.
Wi-Fi
The Wi-Fi interface is not without its known issues. From an attack surface perspective, targeting the Wi-Fi chip becomes intriguing, presenting possibilities for damaging it, initiating Denial-of-Service (DOS) attacks, bypassing security restrictions, or executing arbitrary code.
Ethernet
Similar to the Wi-Fi interface, the Ethernet interface has its vulnerabilities, encompassing low-level TCP/IP stack vulnerabilities and hardware implementation flaws, leading to similar attack vectors.
Radio
The Radio interface has gained significance as a primary attack surface, especially considering the widespread adoption of radio communication in many IoT products.
When talking about volatile memory, the word RAM immediately pops up in our minds.
RAM, widely utilized in PCs and embedded systems, stores code and data during run-time. However, the data is lost when the device is powered off. Two common types of RAM include:
Anyka (ANYKA and Samsung SDRAM)
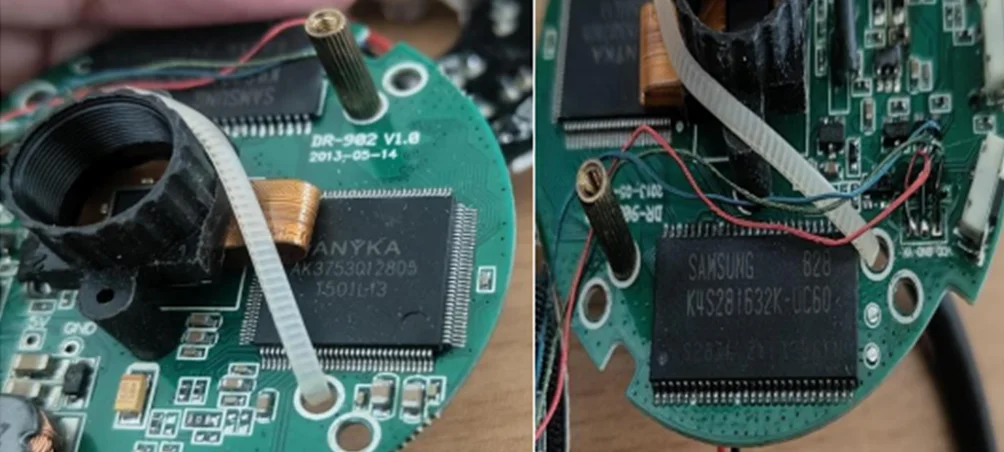
Datasheet for SDRAM – K4S281632K Datasheet(PDF) – Samsung semiconductor (alldatasheet.com). The figure below is a PCB that has various components. Let’s explore one by one and the function of each.

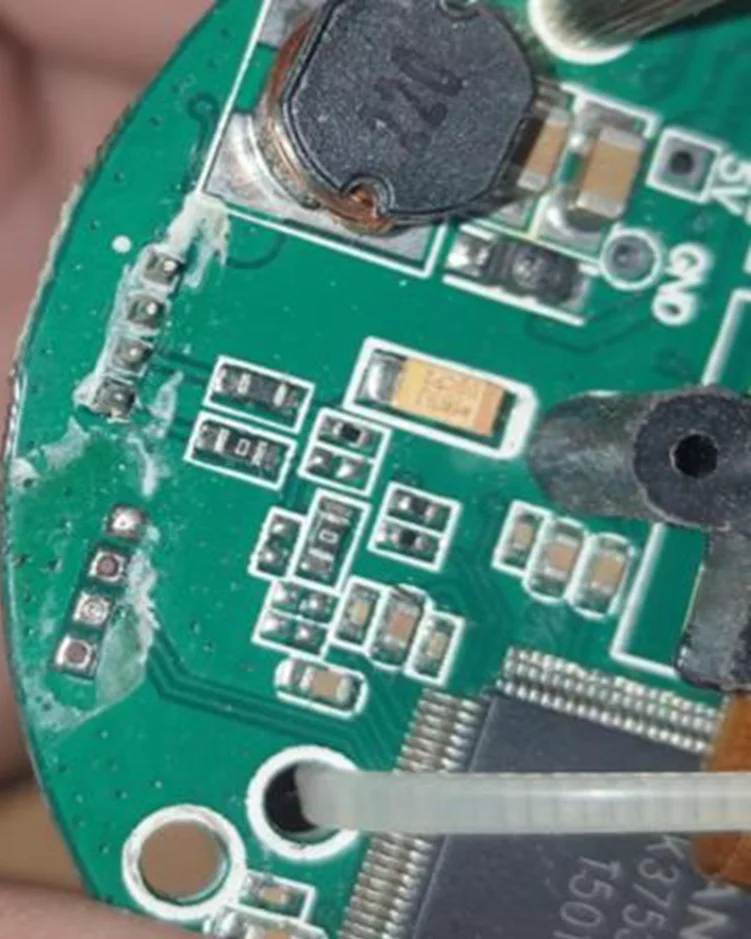
TD1410 is a monolithic step-down switch mode regulator with a fixed frequency of 380 KHz and an integrated internal Power MOSFET. The storage allocation is designated for the Memory Card slot on the right side.
The flash chip is an EMMC chip for the storage of data like firmware and other important data. (25Q16BSIG Datasheet, PDF – Alldatasheet).

Serial communication utilizes the following pins for UART connections (UART for debugging).
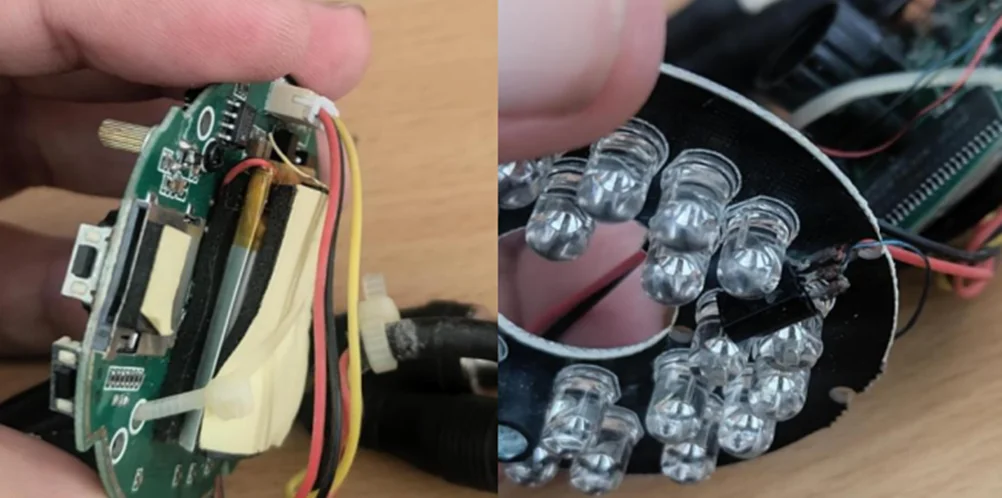
1) Gaining Physical Access
To do hardware hacking, you need to physically reach the debug ports. These ports are usually closed or hard for regular users to get to. People don’t usually use ports like JTAG, SWD, and UART, even though they let you get into the inside of devices. By disassembling hardware enclosures and directly accessing these debug ports, hackers can attain unprecedented control over a system.
2) Exploring JTAG as an Effective Debugging Tool
Widely used for testing and debugging microcontrollers and PCBs, the Joint Test Action Group (JTAG) protocol offers direct access to memory registers of chips without requiring interaction with external system interfaces. Hackers using JTAG ports to connect can exploit them to extract firmware, reverse engineer logic, or inject malicious code into devices.
3) SWD Debugging Solution
Serial Wire Debug (SWD) is an alternative to JTAG that offers a more compact interface for debugging microcontrollers. By employing just two pins, SWD enables bi-directional data transfer and clock synchronization. Its functionality, akin to JTAG but with a reduced pin count, renders SWD an attractive choice for hardware hackers.
4) UART: Your Gateway to Low-Level Control
The Universal Asynchronous Receiver Transmitter (UART) serves as a serial communication hardware interface widely employed in low-level device control. It offers hackers access to console and command line interfaces, facilitating direct communication with devices, viewing log outputs, and modifying system parameters through serial communication. Hackers can directly connect to UART ports to interact with devices, view log outputs, or even make modifications to system parameters.
The exploration of closed or inaccessible debug ports provides hardware hackers with unparalleled access and control over IoT devices.
Security professionals can utilize these ports to uncover vulnerabilities, analyze firmware, and enhance the overall security of the device.
As our global society has become more dependent on Internet-of-Things devices, ensuring their security has become of vital importance. Hardware hacking provides security professionals with an invaluable way to detect vulnerabilities, assess security measures, and bolster IoT devices against potential threats. By exploring replacement techniques for parts/components, analyzing inter-component communication patterns, and opening closed debug ports, hackers can gain insight into how IoT devices function from within. With their knowledge, hackers can develop secure protocols, protect sensitive information, and maintain the integrity of the IoT ecosystem. With technology rapidly progressing forward, hardware hacking will remain an integral component of securing the Internet of Things.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.