
BloodHound is a powerful security tool that uses graph theory to reveal the relationships between users, groups, and computers in a domain. In this comprehensive guide, we’ll take a deep dive into BloodHound and its companion tool SharpHound, providing you with the knowledge and skills needed to navigate and utilize these tools to their fullest potential.
BloodHound is an open-source tool that allows you to map out the relationships between users, groups, and computers in a domain. It uses graph theory to analyze the data it collects and visually represents the relationships between different entities. BloodHound can be used to identify potential attack paths, misconfigured permissions, and other security weaknesses in your Active Directory environment.
To start with BloodHound, you must install it on your system and connect it to your Active Directory domain. Once connected, you can use BloodHound to perform a variety of tasks, including:
SharpHound is a companion tool to BloodHound to gather data from Active Directory. It provides various enumeration options that allow you to collect information about users, groups, and computers in a domain. These options include:
To use SharpHound effectively, you need to specify connection and performance options. These options include:
SharpHound provides several options for outputting the data it collects. These options include:
SharpHound also provides options for looping through the enumeration process. These options include:
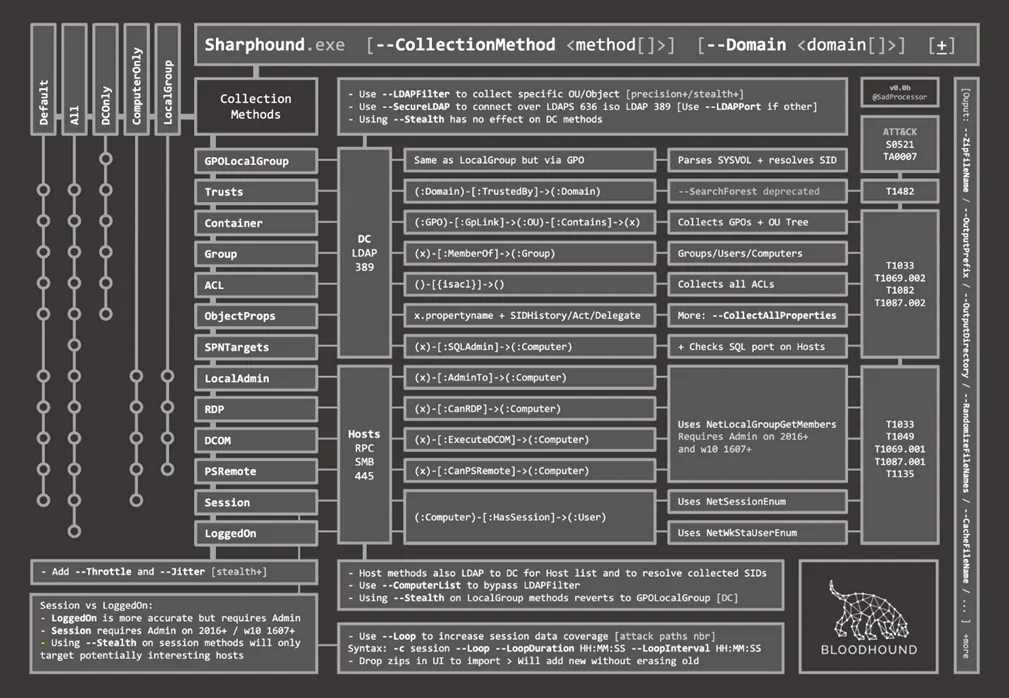
Once you’ve collected data using SharpHound, you can utilize BloodHound to visualize the relationships between different entities. BloodHound uses a query language called Cypher to query the graph database. Here are some handy DB queries that you can use to analyze the data:
Count the LAPS status of all computers
MATCH (c:Computer) RETURN c.haslaps, COUNT(*)
Get a list of all OS versions with a count
MATCH (c:Computer) RETURN DISTINCT c.operatingsystem, COUNT(c.operatingsystem)
Get a list of all OS versions containing ‘Server’
MATCH (c:Computer) WHERE c.operatingsystem CONTAINS ‘Server’ RETURN DISTINCT c.operatingsystem
Get all Windows 2008 computers and sort by last logon timestamp descending and human-readable
MATCH (c:Computer) WHERE c.operatingsystem CONTAINS ‘2008’ RETURN c.name, c.operatingsystem, datetime({ epochSeconds: toInteger(c.lastlogontimestamp) }) AS rdate ORDER BY rdate DESC
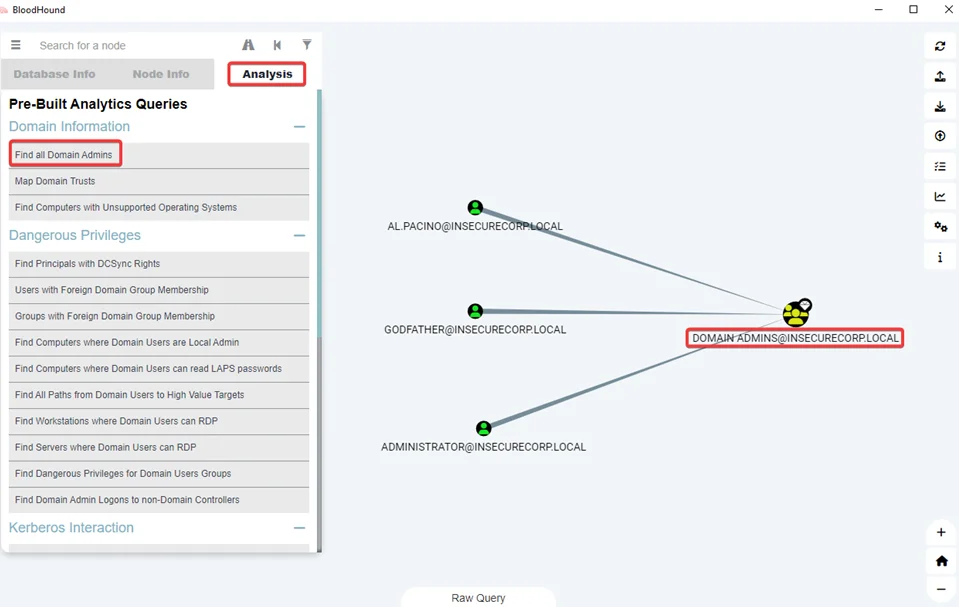
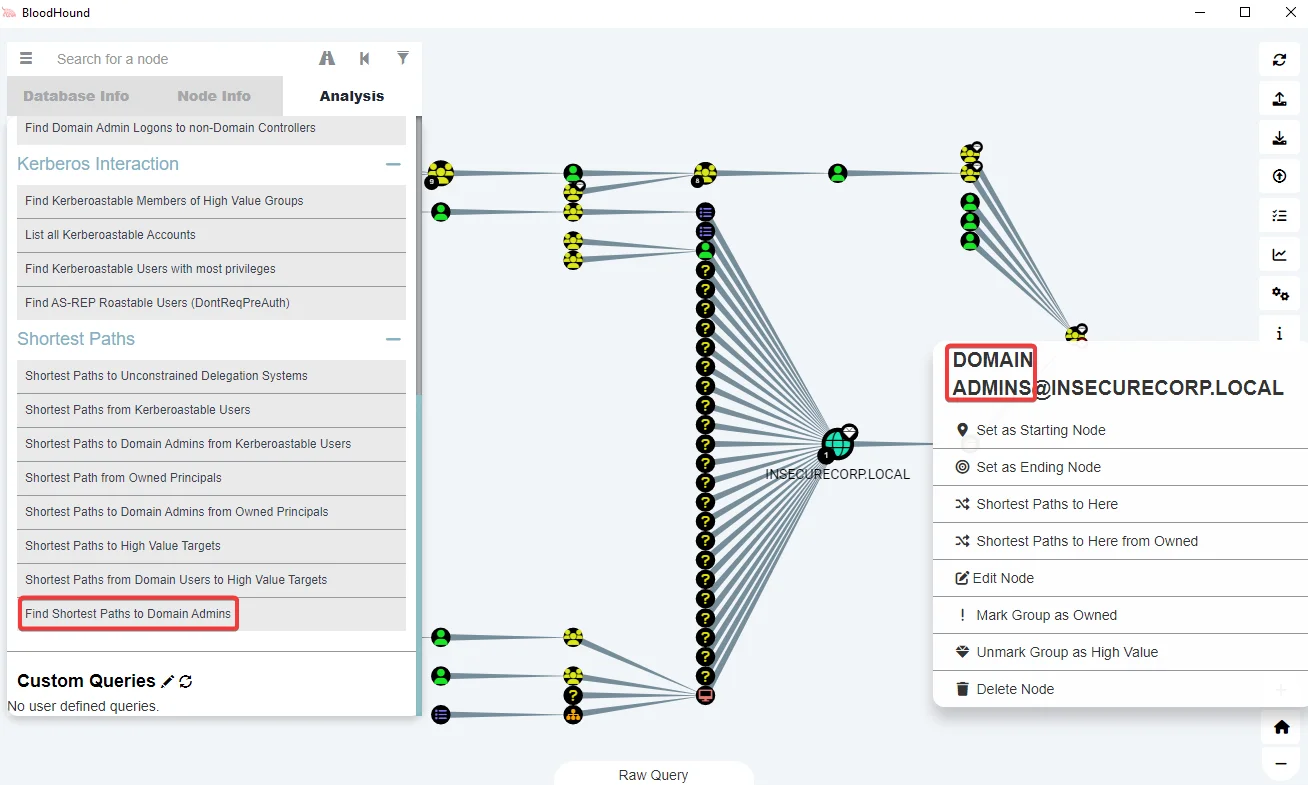
Get all Domain Admins
MATCH (g:Group) WHERE g.name =~ “(?i).*DOMAIN ADMINS.*” WITH g MATCH (g)<-[r:MemberOf*1..]-(a) RETURN a.name
Get active sessions of Domain Admins
MATCH (u:User)-[:MemberOf*1..]->(g:Group) WHERE g.objectid ENDS WITH ‘-512’ MATCH p = (c:Computer)-[:HasSession]->(u) RETURN c.name, u.name
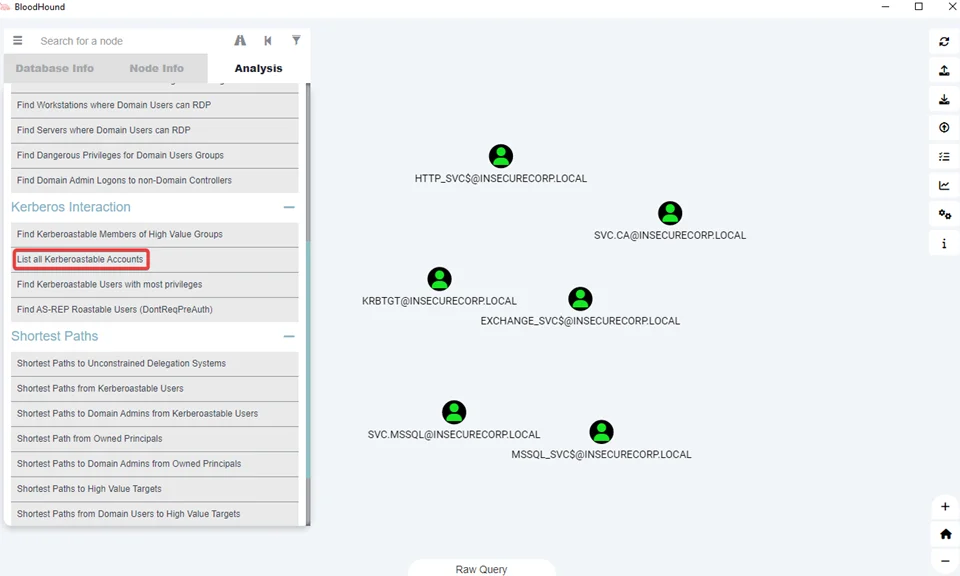
Find all Kerberoastable users
MATCH (u:User) WHERE u.hasspn=true RETURN u.name
Find all AS-REP-roastable users
MATCH (u:User {dontreqpreauth: true}) RETURN u.name
Get the local admins to all computers
MATCH p=(u:User)-[r:AdminTo]->(c:Computer) RETURN u.name, c.name ORDER BY u.name
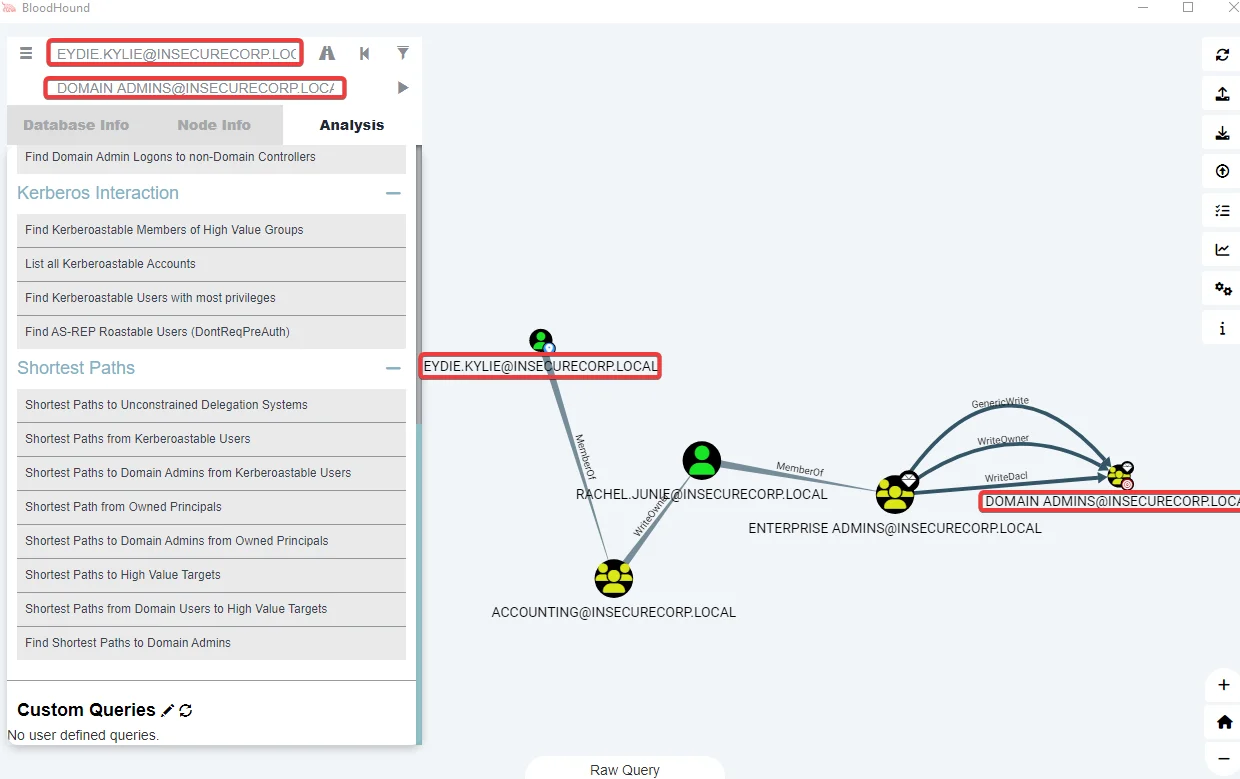
Find all Kerberoastable users with the path to DA
MATCH (u:User {hasspn:true}) MATCH (g:Group) WHERE g.name CONTAINS ‘DOMAIN ADMINS’ MATCH p = shortestPath( (u)-[*1..]->(g) ) RETURN p
Find all computers domain users can RDP to
MATCH p=(g:Group)-[:CanRDP]->(c:Computer) WHERE g.objectid ENDS WITH ‘-513’ RETURN p
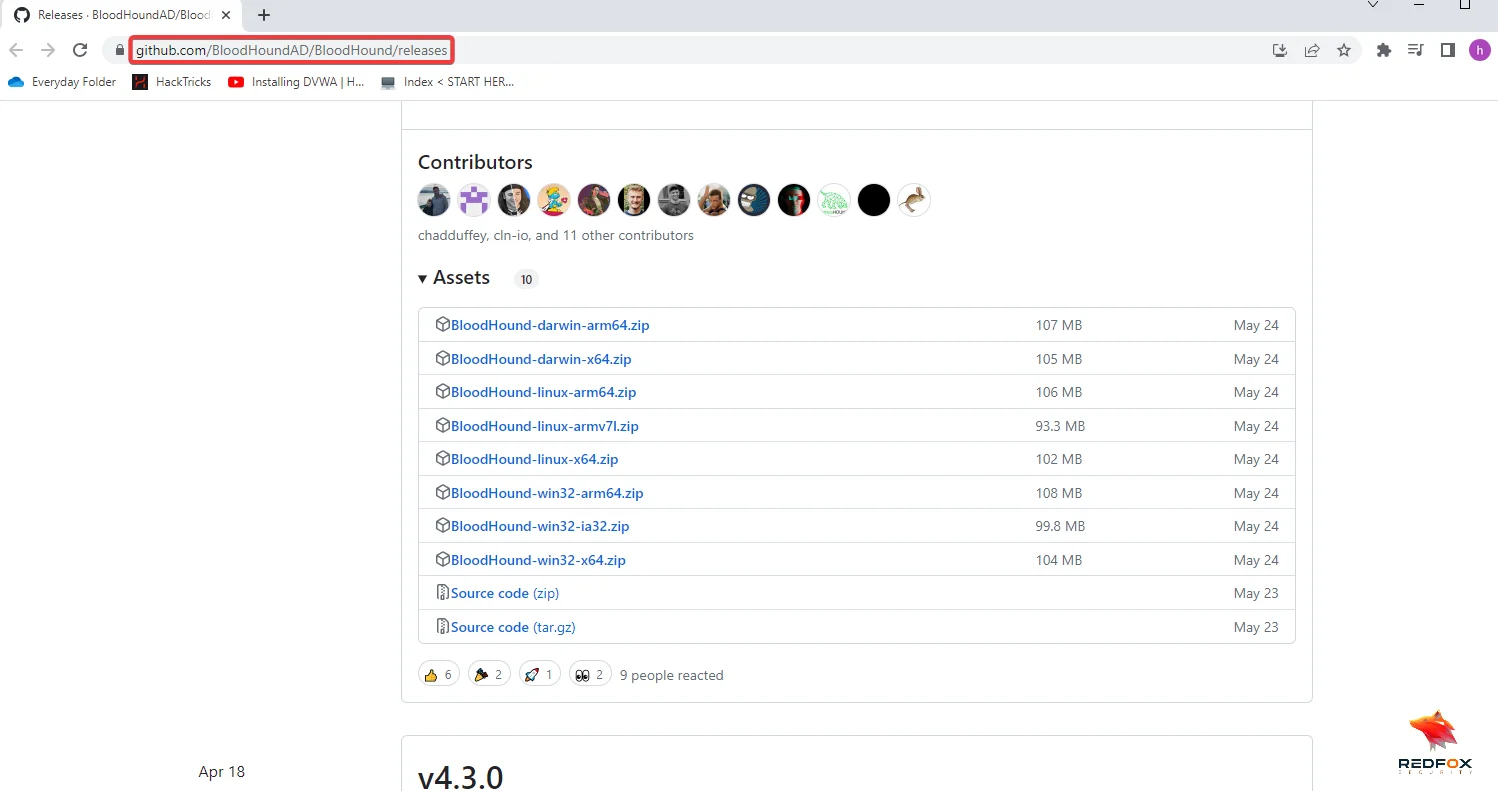
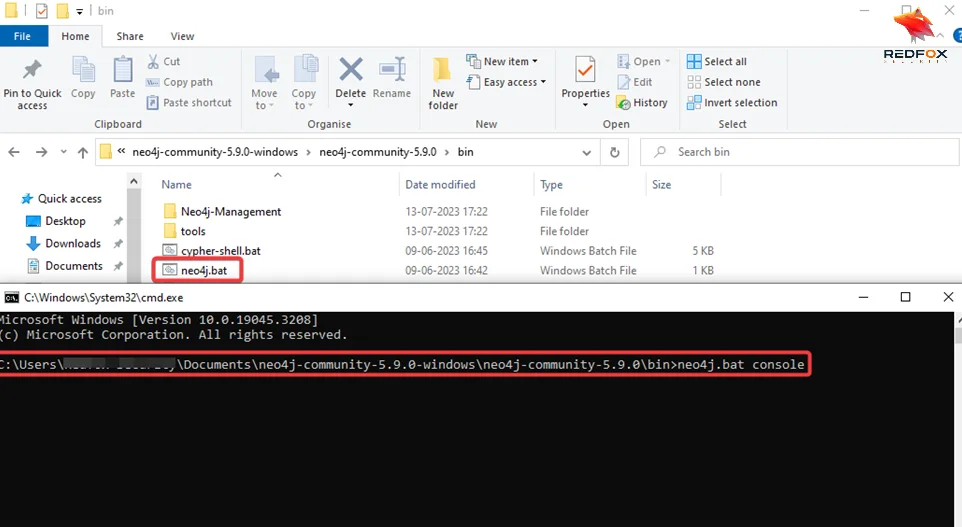
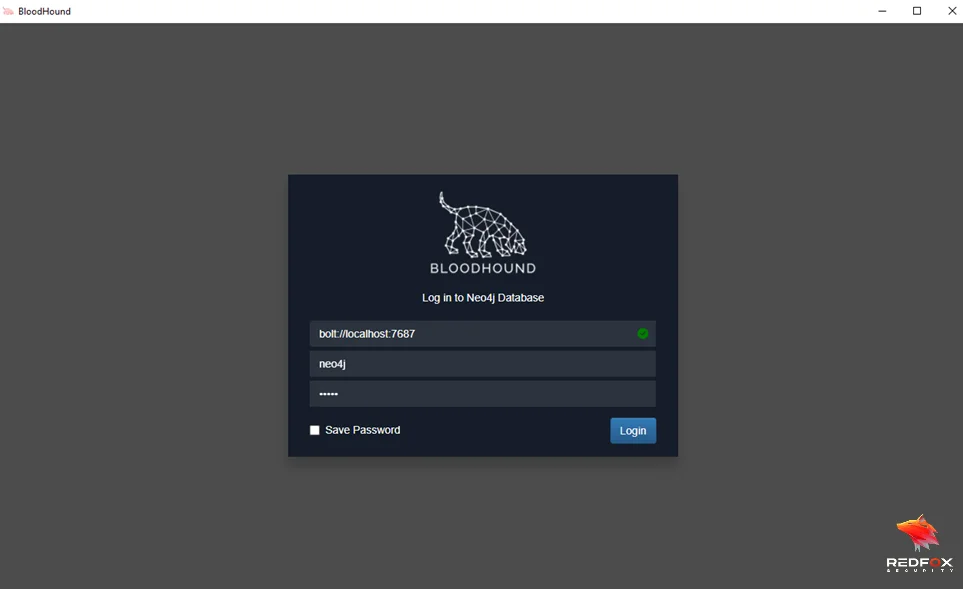
BloodHound and SharpHound are powerful tools to help you identify potential security weaknesses in your Active Directory environment. By utilizing the query language Cypher and the visualization capabilities of BloodHound, you can gain valuable insights into the relationships between different entities in your domain. With the knowledge and skills gained from this comprehensive guide, you’ll be well on your way to becoming a skilled, innovative, and reliable security expert who values efficiency and creativity, able to cater to various security needs with practical solutions.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems, and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.