
A blockchain is a shared distributed ledger between computer network nodes. It serves as an electronic database for storing data in digital form. Blockchain keeps a secure and decentralized record of transactions and are best recognized for their critical role in cryptocurrency systems such as bitcoin. The innovation of a blockchain is that it fosters confidence without the necessity for a reliable third party by ensuring the accuracy and security of a record of data.
Before diving deeper, let us understand some fundamental terminologies related to blockchain. You can follow along through the demo here.
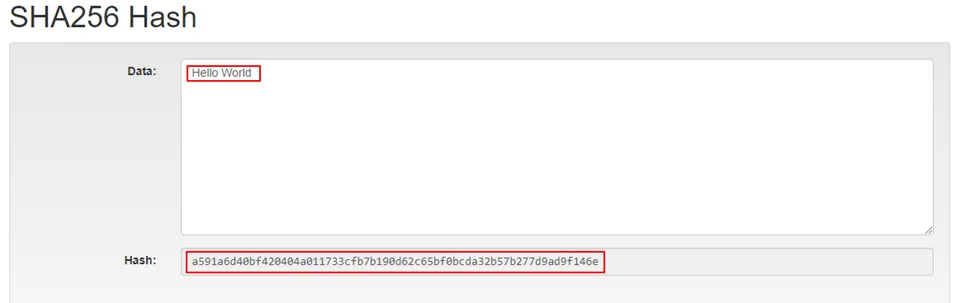
Hash: A hash is a representation or fingerprint of the data. The data is processed through a certain algorithmic function to get a one-way, non-reversible hash (i.e., we cannot get the original data back from the hash) and with a fixed size(the length of the hash remains the same regardless of the length and contents of the data provided). Same data always produce the same hash; but any change in the data, whether it be small or big, changes the entire hash. Hashes are used to protect the integrity of the data, as any tampering of the data changes the value of the hash drastically. Usually, password are stored in the form of hashes in a database, since it cannot be reversed.
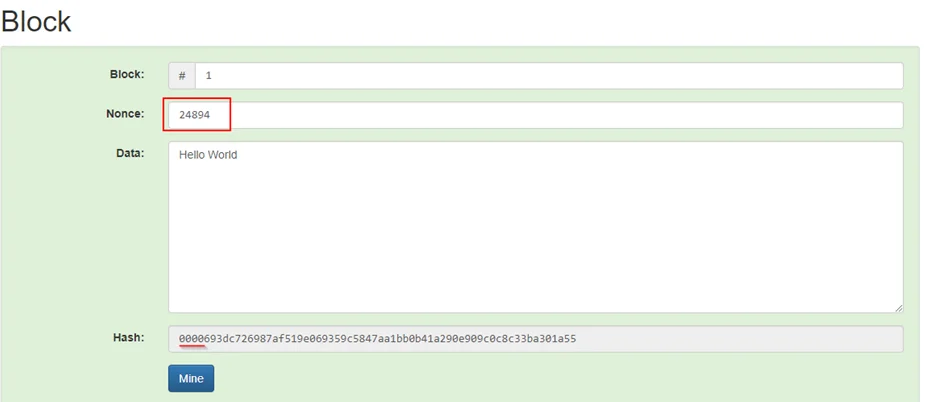
Block: A block is, in a simplified term, a block of some data and its corresponding hash. It is broken down into a few fields: a block number, a nonce (an arbitrary number), and the data(transactions). The hash of the block must be of a certain pattern for the block to be valid (in our example, let us assume that the hash of every valid block should start with 4 zeros). Since the block number and the data cannot be changed, the nonce is calculated to get to the hash pattern. This is called mining and requires high compute power to iterate through the nonce to get the desired hash pattern. When the hash reaches the specified pattern, the block is said to be signed.
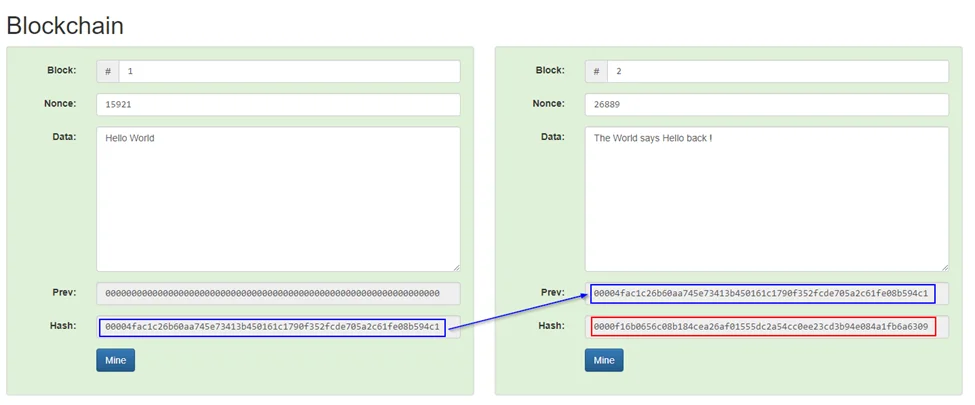
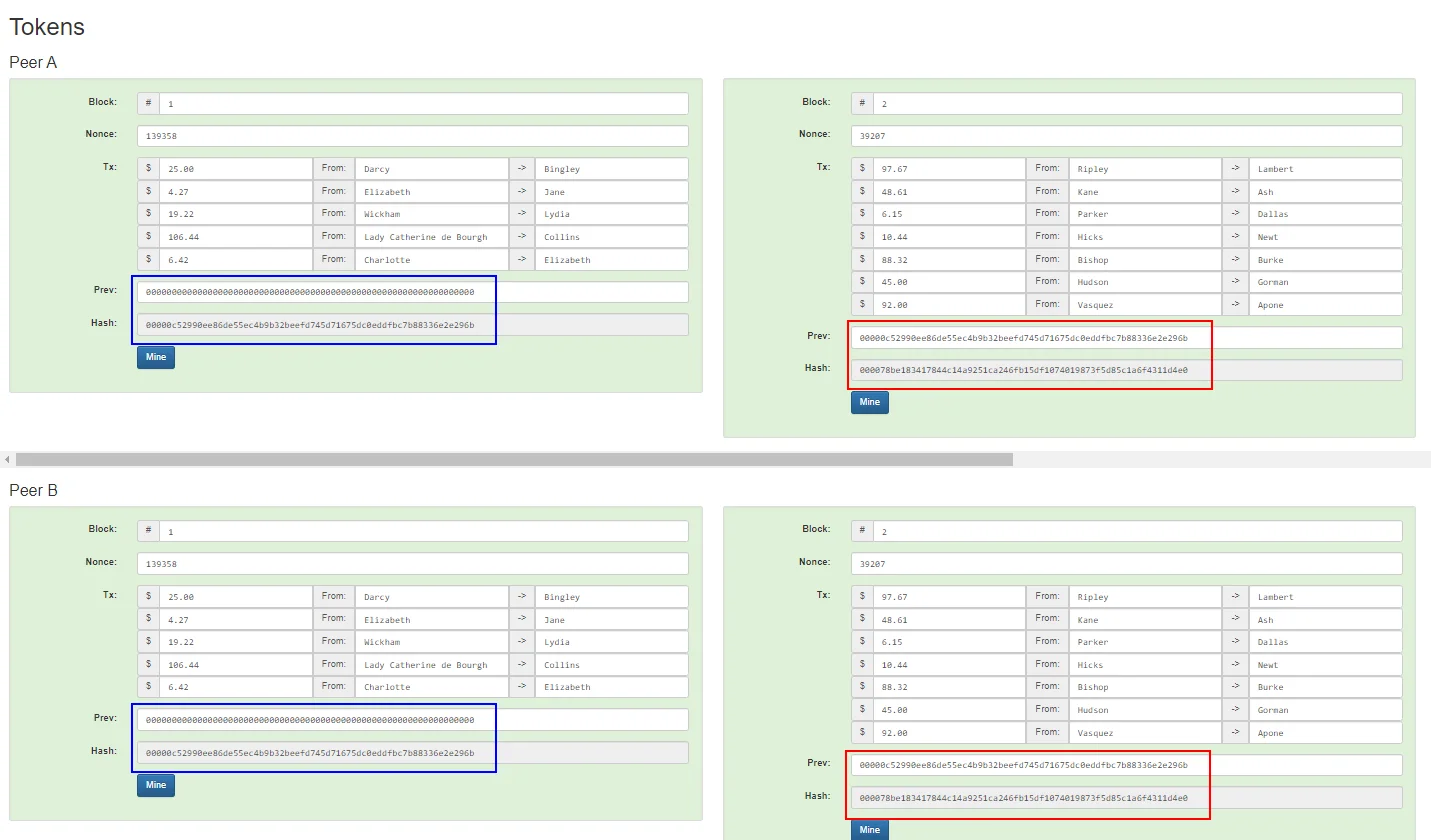
Blockchain: A blockchain is exactly what is sounds like; a chain of blocks. Blocks are linked together to form a blockchain. The hash of the previous block is included in the current block along with the block number, the nonce and the data. Then the hash of the current block is calculated. This is to provide immutability or non-susceptibility to change.
If any data in any of the previous blocks are changed, its hash changes and so does the hashes of all the corresponding blocks, thus making all the blocks after it invalid. The more the blocks are in the past, the harder it is to make changes to them.
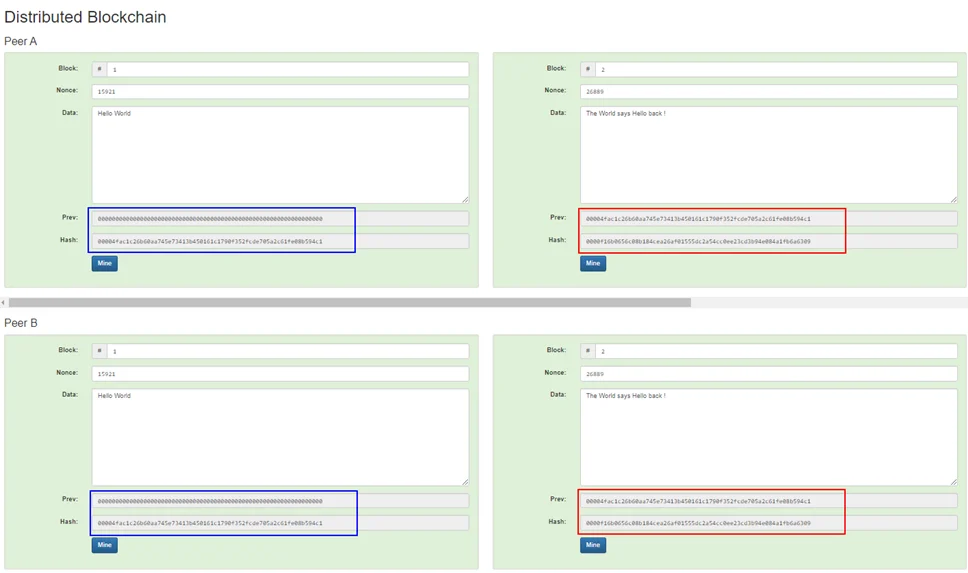
Distributed blockchain: A blockchain does the job of immutability on its own, but if any data is changed in any of the blocks and all the hashes are re-calculated again, how would we know which data was the right one-the initial data or the changed data? Thus comes the concept of distributed blockchain, where the exact copy of the blockchain is distributed to all the peers (machines or nodes using the blockchain). So, any change in the blockchain of a peer is compared with other peers and if the final hashes does not match, the change is considered invalid and rejected.
Token: Till now we have been referring to a data field in the block, but what does it actually contain? In order to understand that, let us first learn about tokens. Tokens are an arbitrary representation which is used as a medium of transaction. For example, a rupee is considered as a token and can be transferred from one person to another. It can be transferred through a bank account and the bank keeps the copy of the transaction in a ledger, thus verifying the transaction to be complete. But this is a centralized method where only the bank has the copy of the ledger with all their users’ transactions, which is not transparent. But in a decentralized blockchain, everybody has access to all the transactions done and that is exactly what is represented in the data field; a ledger of peer-to-peer transaction using a token. Here, immutability comes into play; since anybody has access to the transaction’s records, it prevents them from tampering its values. So, a permanent record of all the transaction is represented in the blockchain. Bitcoin and ether are examples of such tokens.
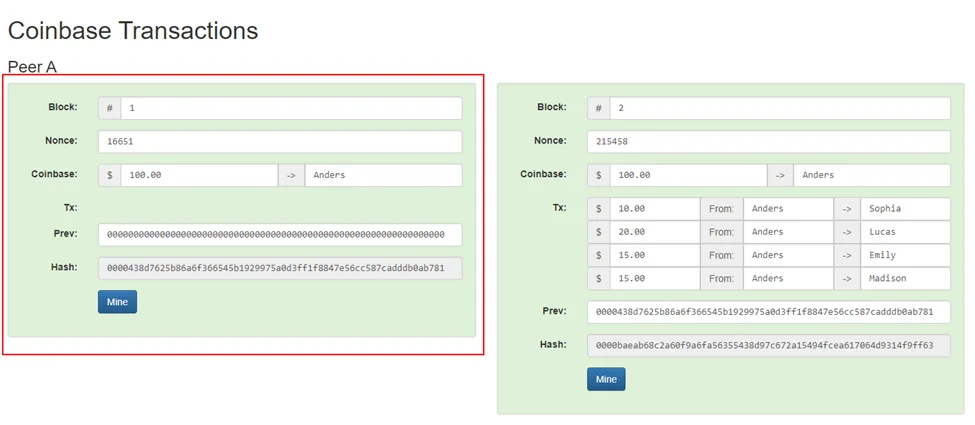
Coinbase Transactions: As mentioned above, blocks are linked together using the hash of the previous block to provide immutability, but what happens to the first block? When the first block is mined, how are the transactions verified and validated? Since there are no previous blocks, how can we be sure that the initial transactions are legit? Does the person doing the first transaction really have the amount specified in the transaction? Coinbase addresses all these questions.
Coinbase adds another block before the first block, which contains no transaction ledger. Instead, it creates a certain number of new tokens and gives them to someone on the blockchain to start the transactions. Since the transaction creates new tokens, there is no need for validation. Although the underlying mechanism of token distribution is much more complex than this, this is the gist of it. The Coinbase transaction is also the first transaction when a new block is created; a certain number of tokens are distributed to further the transactions. An example of a Coinbase transaction can be found here.
Proofs are algorithms that allow blockchains to operate securely. These consensus mechanisms keep blockchains secure by allowing only genuine users to add new transactions. It also determines which nodes in the network can add the next block to the blockchain. The number of tokens distributed also depends on the proof. The two prevalent consensus mechanisms are Proof-of-Work(PoW) and Proof-of-Stake(PoS). There are other mechanisms such as Proof of Work (PoC), Proof of Elapsed Time (PoET), Proof of Activity (PoA), Proof of History(PoH) and more.
1 Proof-of-Work (PoW)
Proof of work is a system where computers (nodes) compete against each other to validate a block. The first node (or group of nodes) that gets the hash pattern and creates a block in the blockchain gets rewarded in tokens (Coinbase transaction). It is a highly energy-intensive process, as it requires a lot of compute power to calculate the hash and validate a block. This process is called mining. A proof-of-work system is used for Bitcoin (BTC) and Ether (ETH). This system is purely based on the amount of compute resources, energy spent and a hint of chance, on a first come-first serve basis.
2 Proof-of-Stake (PoS)
Proof of stake addresses some issues of PoW. Here, a certain node(validator) is chosen to validate the next block. Staking, or the deposit of tokens in the blockchain as a security deposit, determines the likelihood of validator(s) selection. Blocks are validated by more than one validator, and when a certain number of validators confirm that the block is correct, it is finalized and closed. This increases efficiency and lowers the barrier of entry. If the validator is found to misbehave in any way, their tokens get taken away or slashed. Cardano (ADA) and Solana (SOL) are some PoS-based coins.
Cryptocurrencies are digital currencies or tokens distributed in a blockchain.
Bitcoin
Bitcoin, created by Satoshi Nakamoto in a 2008 white paper, is the world’s first widely-adopted cryptocurrency. With Bitcoin, people can securely and directly send each other digital money on the internet. BTC (Bitcoin) is the native cryptocurrency of the Bitcoin network. It works on a proof-of-work consensus.
Ethereum
Ethereum, which was launched in 2015, is the second-biggest cryptocurrency after Bitcoin. While Bitcoin was a purely decentralized transactional blockchain, Ethereum is a decentralized compute platform. The nodes in the blockchains are also used to run codes that anyone can deploy. ETH (Ether) is the native token of the Ethereum network.
In order to complete a transaction in the Ethereum network, a fee (in ETH) called “gas fees” should be paid to the miners to execute the transaction since the number of transactions that can be done at a time is limited. Higher demand increases the gas fees.
Ethereum is planning to shift from a proof-of-work consensus to a proof-of-stake. This process, termed “the merge,” is scheduled to take place in September 2022.
ERC -20
ERC-20 is a standard that is used to create apps on the Ethereum blockchain to make them compatible with each other. It is used for all smart contracts on the Ethereum blockchain and provides a list of rules that all Ethereum-based tokens must follow. Tokens implemented using the ERC-20 standard make it easier to interact with other tokens, applications, and platforms on the Ethereum network. Since ETH existed before the ERC-20 standards, an ERC-20 compliant version of ETH called wrapped ether, or WETH, was created.
Crypto wallets, just like regular wallets, are used to keep your assets safe and facilitate their transfer. They do this by securing it with a key pair (a public and a private key). The public key (accessible by anyone) is usually your wallet address, whereas the private key is your wallet password (which only you should know). Wallets do not store your crypto assets; they just secure the assets stored on the blockchain and restrict their access. You cannot access the assets of a wallet without the private key.
There are mainly three types of crypto wallets:
Smart Contracts
Smart Contracts are applications stored on the blockchain and run when certain conditions are met. They follow simple if/when statements to verify the conditions agreed upon by the contract, executes the transaction and updates the blockchain. Most smart contracts are written in one of the programming languages directly suited for such computer programs, such as Solidity.
In this blog, we discussed how Blockchain allows digital information to be distributed over multiple nodes in the network. It powers the backbone of bitcoin and cryptocurrency. For more on Smart Contract attacks, click here.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and a thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. With a combination of data-driven, research-based, and manual testing methodologies, we proudly deliver robust security solutions.
“Join us on our journey of growth and development by signing up for our comprehensive courses, if you want to excel in the field of cybersecurity.”