
In this blog, we are going to talk about Tapjacking and how it operates. In addition to that, we are going to learn about free-floating windows.
The Android operating system is based on the Linux operating system and was designed with great aspirations. Android is typically seen to be at least as secure as a regular Linux computer, if not more so. A safe Android remains a pipe dream. Tapjacking, an Android attack, is one good example. Tapjacking is a term that combines the words “tap” and “jacking,” and refers to someone taking control of what a user taps on his smartphone. It’s one of the most dangerous Android hacks since it doesn’t need any external tools or libraries, and it doesn’t even require specific permissions! Let’s start with the basics to grasp what Tapjacking is and how it works.
The tapjacking attack works by cleverly arranging a non-tappable foreground layer to fool the user into tapping on an object in the background layer. As a result, any user input will be applied to the background layer, which is hidden from view. It’s simply a delivery system, and the attacker may customize the payload. Because the exploit is payload and aspect ratio dependent, the exploit code must be updated based on the payload sought by the attacker as well as the aspect ratio of the target device. The assault is also restricted by the device’s screen real estate.
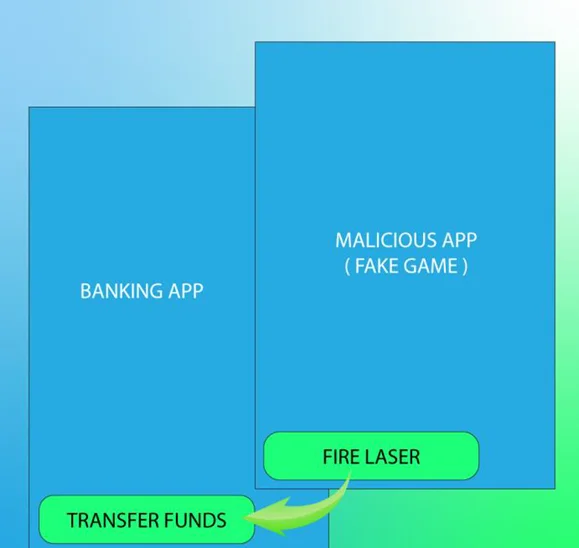
Let’s take an example of a malicious video game, where you’re asked to tap on a moving shape in the app to score points. Now imagine if, underneath the supposed video game, all of your taps are transferred to your banking app which is running in the background. Each time you tap in the game you could actually be selecting menu items or clicking buttons in the banking app underneath it. In theory, with the right design, the malicious app could make you tap in the correct way to execute a transfer of funds or similar undesired function. The following diagrams show what tap jacking looks like. The fire Laser button of the Malicious App is aligned in a way that it overlays the transfer funds button of the banking app.
The SYSTEM ALERT WINDOW (SAW) permission was introduced in API level 1 (Android 1), and the system quietly authorized it until API level 22 (Android 5.1). The developer was allowed to use the permission without any form of disclosure in all versions of Android, including Lollipop (Android 5.1). Except in the scenario when the target SDK version is set to less than 23, Marshmallow (Android 6) needs the user to expressly request this permission through a management page.
A free-floating window, as the name indicates, is a type of window that appears independently by itself and can appear above any other application. Additionally, the developer may fully customize and manage its behavior and look using the Window Manager. The type attribute of Layout Parameter class may be used to request a priority in the mobile’s display layer, and the flags attribute can be used to customize the event process.
An application is authorized to establish a TYPE APPLICATION OVERLAY window type once the SYSTEM ALERT WINDOW permission is granted. Because the generated window is prioritized between FIRST APPLICATION WINDOW and LAST APPLICATION WINDOW, it will appear above other activities but below crucial system ones (e.g., status bar). As previously stated, a flag property affects a window’s event processing behavior. For example, a flag NOT TOUCHABLE will dispatch events to the window behind it, but a flag WATCH OUTSIDE TOUCH will alert the app about the event but withhold specifics such as the touch coordinates. Of course, a complete variety of aesthetic parameters for the view that will be added to the window, such as visibility, size, and position, are still accessible.
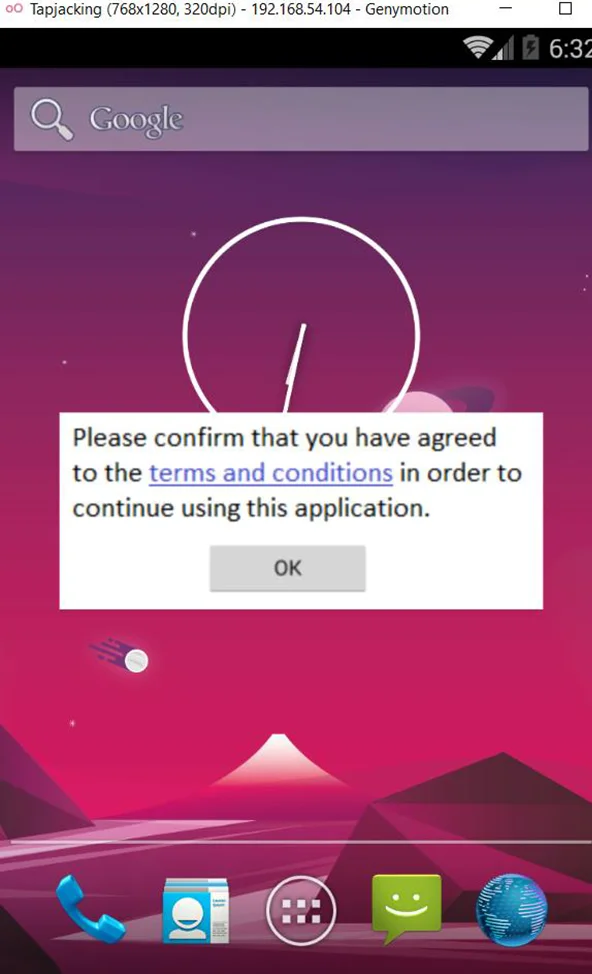
Screen overlays are the translucent UI layers that appear on your screen from time to time. If you’re running Android 6 and you’re installing an app for the first time, you’ll be prompted to confirm-grant all of the app’s key permissions. A screen overlay is the dialogue box that appears at that point, causing the rest of the screen to grey out but still enabling you to see what’s below. For the example we are using Android 4.4.

Screen overlays are now a very useful tool. Do you recall Facebook Messenger’s floating conversation bubbles? Can you figure out what allows them to exist? It’s screen overlays, of course!
The essence of the notion is that no screen overlay should be active when you’re providing a key permission to an app. We say “should not” because the implementation of this security concept is horribly flawed.
When enabled, this security feature prevents you from interacting with the underlying UI while an overlay is active.
Make sure that filterTouchesWhenObscured is set to true in your app, or that the function onFilterTouchEventForSecurity() is used. We recommend that you do not provide “Permit drawing over other apps” permission to app that you do not completely trust. This permission is the only option for malicious applications to exploit this vulnerability. And also upgrade android to Android 6.1 or more
Also, always make sure that the programs you download are from a reputable developer and source.
In this blog, we discussed Tapjacking and how it works and its prevention. For learning more about Android pentesting, check out our Android Pentesting Methodology series. Don’t forget to stay connected with Redfox Security for more insights into mobile application penetration testing.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and a thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. With a combination of data-driven, research-based, and manual testing methodologies, we proudly deliver robust security solutions.
“Join us on our journey of growth and development by signing up for our comprehensive Courses, If you want to excel in the field of cybersecurity”.