
In this blog, we’ll discuss Android architecture and the different layers of Android architecture. This blog is part 1 of the “Android Pentesting Methodology” series and forms a basis for our upcoming blog.
Before we get into the nitty-gritty of the Android Pentesting Methodology, it’s crucial to understand the inner workings of the Android platform.
Android is a Google-created mobile operating system. The majority of smartphones and tablets utilize it.
The Android operating system is built on the Linux kernel (OS). Android is open source, which means that developers may alter and modify the operating system for any device. As a result, even though Android-based devices utilize the same OS, their graphical user interfaces (GUIs) are quite different.
Android devices often come with a variety of pre-loaded apps and also allow third-party apps to be installed. The Android software development kit (SDK) is a free tool that allows developers to create apps for Android. Applications for Android are written in Java and executed on a Java virtual machine (JVM) designed specifically for mobile devices. The “Dalvik” JVM was used until Android 4.4, when it was superseded by Android Runtime, or “ART”. Android apps may be downloaded and installed via Google Play Store and other sources.
If you’re not sure what operating system your Android device is running, you can find out by going to the Settings menu and selecting “About.” This is also a fantastic approach to see if your device fulfills the system requirements for a particular app.
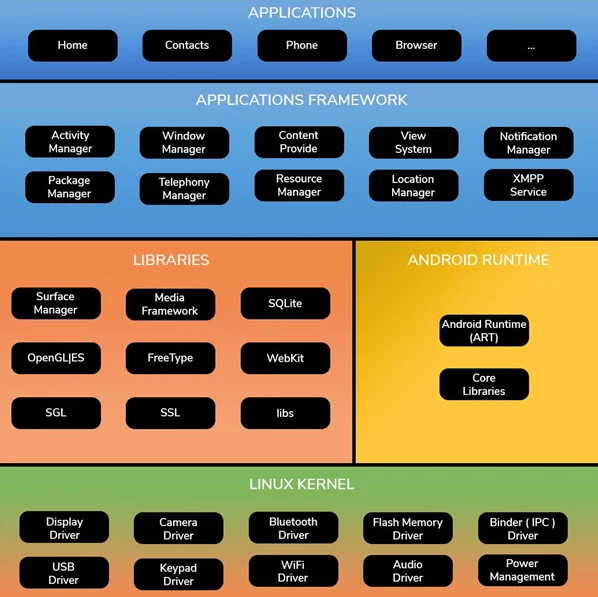
Android Architecture
As can be seen above, there are sever layers in the Android operating system, each of which has a specialized set of functionalities.
Application layer
The Application layer is where installation and running of individual applications occur. For email, SMS messaging, calendars, internet surfing, contacts, and more, the Android operating system has pre-install applications. These applications work with the end-user with the help of the application framework to operate.
The application layer uses classes and services provided by the application framework to function within the Android run time.
Application Framework
The Application Framework layer exposes system APIs for common functionality which many applications routinely use. This includes functionality to display visual elements, share data, or access things like the telephone or GPS functionality. It contains the classes needed to build Android apps and manages the user interface and application resources, as well as providing a generic hardware access layer. It simply provides functions that enable us to construct a class and make that class useful for application development.
The application framework offers services such as telephony, location, notification manager, NFC service, view system, and others that we may utilize to construct applications that meet our needs.
Libraries
The library layer contains C and C++ libraries which handle low-level processes such as graphics, drawing, network encryption, multimedia playback, and image rendering
To help with Android development, the platform comprises of several C/C++ core libraries and Java-based libraries like SSL, libc, Graphics, SQLite, Webkit, Media, Surface Manager, OpenGL, and others.
The following is a list of some of the most important Android libraries available for development.
Android Runtime
The Android Runtime consists of core libraries and the Dalvik virtual engine. The Android runtime is the engine that drives apps and libraries while also operating as the framework’s base.
The Dalvik Virtual Machine (DVM), like the Java Virtual Machine, is a register-based virtual machine (JVM). The Dalvik VM runs files in the Dalvik Executable (.dex) format, which is designed to use the least amount of RAM possible. It is particularly developed and tuned for Android to guarantee that several instances may function smoothly on a single device. The Linux kernel is in charge of threading and low-level memory management.
The libraries included in this layer consist of the following java-based libraries:
Linux Kernel
The Linux kernel layer is the underlying layer that ties all of the upper layers together. This layer arbitrates all access to the underlying device hardware, via drivers. As with any computer the kernel also handles memory, processes, and power management.
It controls all of the drivers that are necessary for the android device during runtime, such as display drivers, camera drivers, Bluetooth drivers, audio drivers, memory drivers, and so on.
Android’s key system services, including security, memory management, process management, network stack, and driver model, are all based on Linux version 2.6. Between the hardware and the rest of the software stack, the kernel serves as an abstraction layer.
In this blog, we have briefly discussed Android architecture and the different layers that make up the architecture. In the upcoming blog, we’ll get into the actual meat of the Android Pentesting Methodology. Till then stay connected with us. Stay safe, stay healthy, and hack responsibly.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“