
In recent years, the cyber threat to the healthcare industry has increased dramatically. This new era of digitization has brought many benefits to the healthcare industry, but as medical device automation becomes more complex, it becomes more susceptible to cyberattacks.
There are numerous reasons why threat actors are particularly interested in healthcare organizations, such as:
Therefore, penetration testing is of utmost importance in order to protect the healthcare industry from hackers. It can help the business meet health insurance profitability and accountability (HIPAA) compliance.
Most of the time, the IT environment of an organization determines what kinds of attacks it can be vulnerable to. Attackers can get into key systems and data through bugs in web browsers, operating systems, and server interfaces.
Therefore, while making the security plan, each network component should be taken into consideration. Penetration testing can often help identify many of the common weaknesses in application code and is the best way to find any vulnerabilities before the code is put into use.
Cybercriminals tend to target healthcare companies of all sizes. The predominant reason for the same is that it has financial private data. They hold medical records, credit card numbers, social security numbers, along with other information which can further be used by hackers for malicious purpose. Stolen health records may sell for ten times more than other data on the black market.
Most of the times healthcare issues are industry-specific. With the rise of IoT medical devices over the last decade, healthcare has faced many issues that other industries have not.
For instance, Web-enabled medical devices often save lives. Disabling them could jeopardize the life of a patient.
The HIPAA framework is governed by the Department of Health and Human Services (HHS) of the United States. The HHS collaborates with cybersecurity experts and government agencies to establish requirements that safeguard healthcare organizations, their business partners, and their patients. Although not a HIPAA requirement, penetration testing is an essential element of HIPAA compliance because it tests the strength of these requirements.
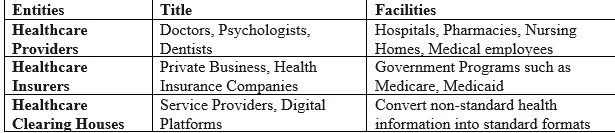
HIPAA’s Privacy and Security Rules Apply to all of the Following Entities:
The following four key principles can help healthcare organizations take a more proactive stance against malware:
As cyber security measures improve, we can better prepare for future cyber-attacks, but the smarter the attacks get, the more sophisticated our defenses must be. Nevertheless, the following measures can be taken to safeguard the security of medical devices and hospital networks:
Every hack is primarily caused by the weaknesses in an organization’s infrastructure. Regularly performing Vulnerability Assessment and Penetration Testing (VAPT) can assist in preparing all networks and devices for inevitable cyber threats by identifying and eliminating their vulnerabilities.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and a thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. With a combination of data-driven, research-based, and manual testing methodologies, we proudly deliver robust security solutions.
“Join us on our journey of growth and development by signing up for our comprehensive courses, if you want to excel in the field of cybersecurity.”