
The number of resources such as users, databases, or servers managed in organizations poses questions about accountability as firms adjust to industry needs and norms. Additionally, the dispersed structure of managing the infrastructure and its procedures makes it challenging for enterprises to monitor employee activity. This makes it simpler for attackers to access the network’s resources and leads to a significant loss of sensitive data. Windows started the Active Directory Domain Service in Windows Server 2000 and developed it until Windows Server 2012 to manage organizational resources in the network.
Active Directory is a central repository containing information related to all the resources in the organization’s network, ranging from employees to devices, ensuring efficient information management. AD has a Windows server (Domain Controller), working in compatibility with the Windows Operating System to provide centralized management, scalability and security.
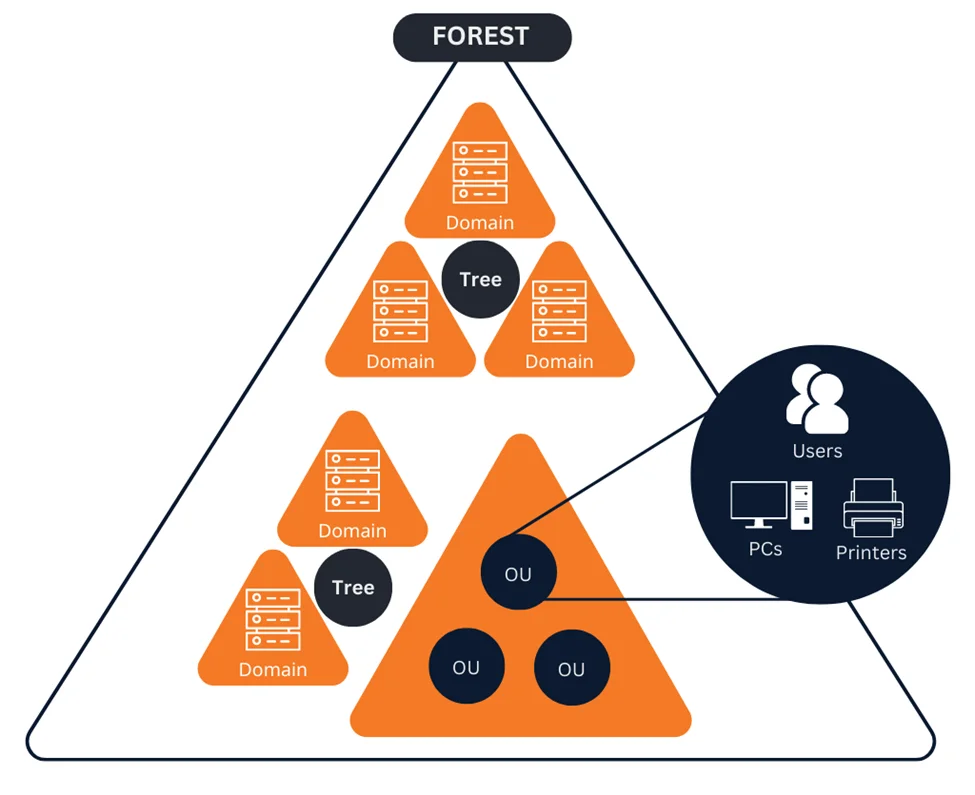
Active Directory uses a hierarchical, tiered layout of domains, trees, and forests to coordinate networked elements.
AD Authentication is a process that typically follows Kerberos protocol since Windows 2000, where users have to log in using their credentials to gain access to resources. Before Kerberos, the NTLM protocol was used to authenticate the users. NTLM is still present in all Windows devices for fallback and legacy uses.
The main difference between NTLM and Kerberos is in authentication mechanisms. NTLM relies on a three-way handshake between the client and the server for authentication. Kerberos uses a two-part process with a key distribution center and the service. Another huge difference is that NTLM uses password hashing (without salting), whereas Kerberos leverages encryption.
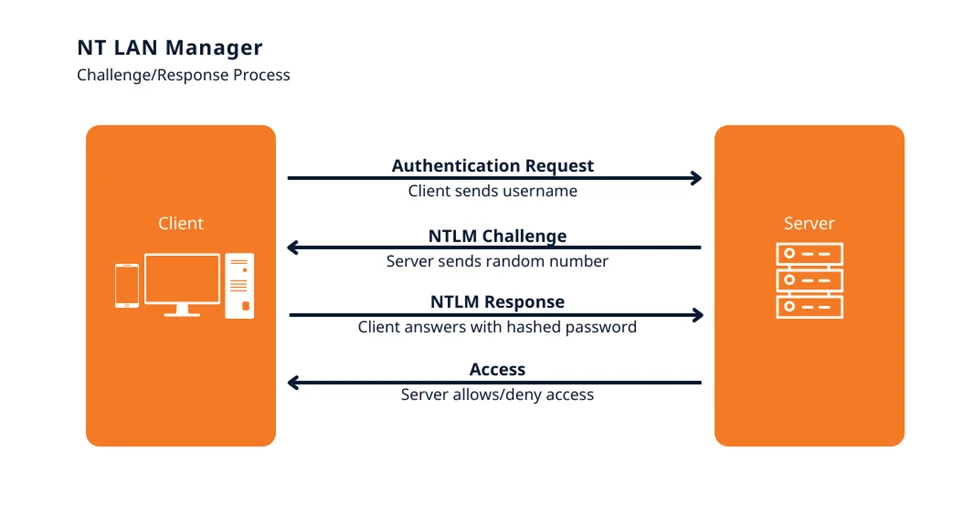
New Technology LAN Manager (NTLM) was the primary security protocol used to authenticate users’ identities in AD before Windows 2000. NTLM can be used for authentication with the help of a challenge-response-based scheme. When the client requests access to a service, the service sends a challenge to the client, where the client has to perform a mathematical operation using its authentication token and then return the result to the service. The service will send the result to the Domain Controller (DC) for validation. If the DC confirms that the client’s response is correct by verifying with its databases, the service allows access to the client.
Here is an outline of the NTLM authentication process once the user provides their credentials during logon:
Eventually, the domain controller compares the encrypted challenge it computed to the response computed by the client. If they are identical, authentication is successful.
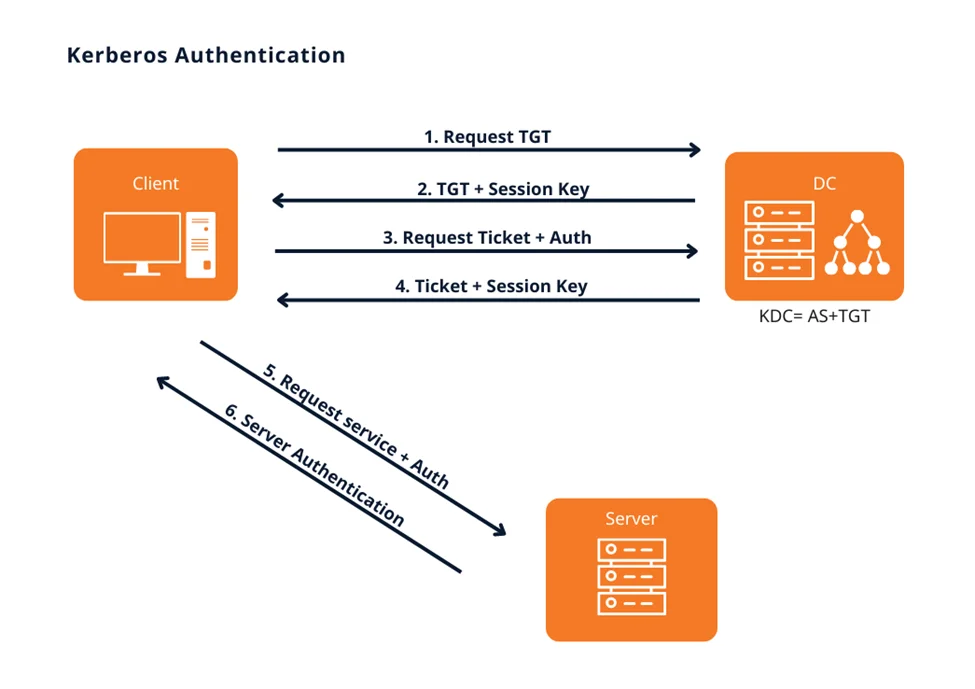
Kerberos provides a centralized authentication server that authenticates users to servers and vice-versa. In Kerberos, an authentication server and a database are used for client authentication. Kerberos runs as a third-party trusted server, the Key Distribution Center (KDC). Each user and service on the network is a principal.
There are two main components in the KDC:
Kerberos Overview:
You can watch this video for a deep dive into Kerberos. We will delve into Active Directory attacks in our upcoming blogs.
By partnering with Redfox Security, you’ll get the best security and technical skills to execute a practical and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. We proudly deliver robust security solutions with a combination of data-driven, research-based, and manual testing methodologies.
“Join us on our journey of growth and development by signing up for our comprehensive courses if you want to excel in cybersecurity.”