
Static program analysis is the analysis of computer software performed without executing any programs, in contrast with dynamic analysis, which is performed on programs during their execution.
Static code analysis is a process for programmatically examining the application code on the disk, rather than while it is running. Static analysis is performed on the code in order to “regenerate” it from smali/byte code. This is important to understand since code is only a representation, which implies that the actual code may change, resulting in many false-positives when employing automated tools like MobSF.
Some common security issues to check for in Android applications are: excessive permission, hardcoded credentials, weak cryptographic functions, workflow bypass, hidden features, inappropriate log management, unsecured storage, and so on.
Let’s go over some fundamental principles before we get into the analysis section.
The process of reviewing the source code of an APK (android application) file is known as static analysis. This can be carried out using many reverse engineering tools such as apktool, dex2jar, jd-GUI, and other automation tools like mobSF to decompile the APK file. Let us look at one such reverse engineering tool in more detail.
To decompile the APK file, run the following command:
apktool d <example.apk>
Manifest files, Dexfiles, Smali files, and other non-human-readable forms are among the apktool output. Tools like dex2jar and JD-GUI, on the other hand, can assist in the conversion of such files to human-readable forms. For more information refer to Android Pentesting Methodology (Pt. 2).
Let’s see the most important file in the APK – AndroidManifest.xml. During a mobile application penetration test, we can find most of bugs by reviewing the android manifest file.
The Android manifest file is an XML file that specifies the names of application packages as well as the program’s essential parts, such as broadcast receivers, services, and content providers. It contains information about the Android operating system and other useful information. It also aids in defining permissions so that other applications can or cannot access the data.
For Android mobile application development, it is necessary to define the manifest file:
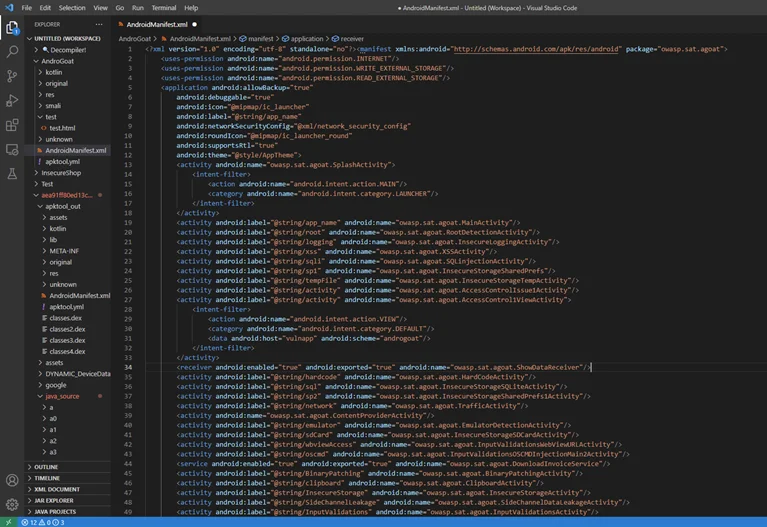
Here we are using AndroGoat application. Every Android application will have a package name that will uniquely identify it on the device and in the app store. While performing static analysis, the package name will assist us in identifying source code-related issues in the application.
The AndroGoat application’s package name is “package=owasp.sat.agoat” according to the manifest file.
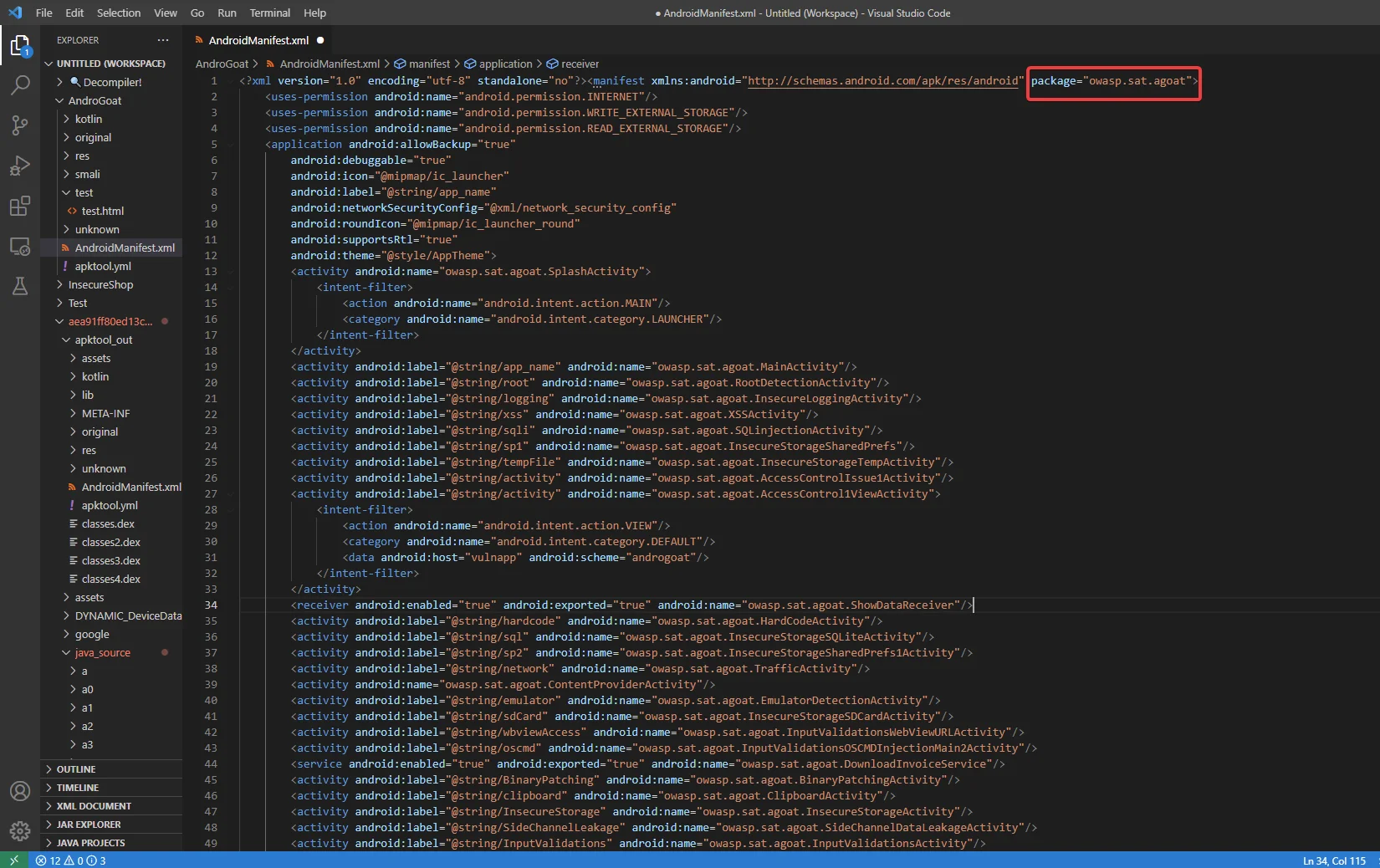
All activities, services, broadcast receivers, and content providers that are key components of any android application are included in the app’s components. Each component will have its own functionality, which will specify the device configurations that it can manage.
Let us now learn some fundamental details about each Android APK component.
Activities are the visual elements, or screens, that you see when instructing with android applications as a user. They can be vulnerable to attacks when they allow access to user data without proper authentication.
An activity is a depiction of a single screen with a user interface, or it can be characterized as the screen’s performance action. In web applications, it’s similar to web pages. An e-commerce application, for example, could have one activity that displays a list of orders, another action that adds things to the cart, and still another activity that Wishlist’s the products.
The following activities are declared in our sample manifest file:
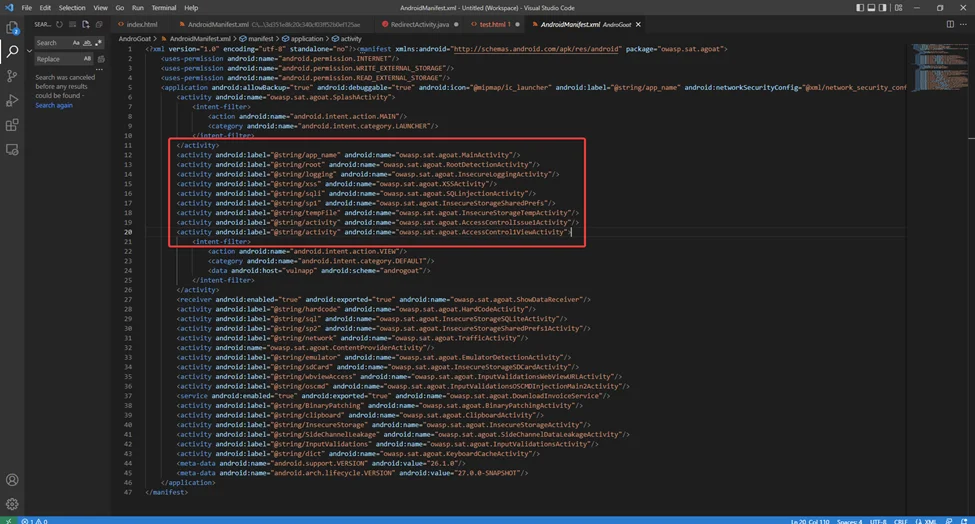
If access to an exported Activity is not controlled, any application on the phone/device can launch it. An attacker can get total authorization to the application’s sensitive information this way. They can even change the internal state of the application or fool the user into interacting with the victim application.
A service is often used in the backend to do tasks that do not require user input. For example, a service could be playing music in the background while another application is being used.
The following service are defined in our manifest file:
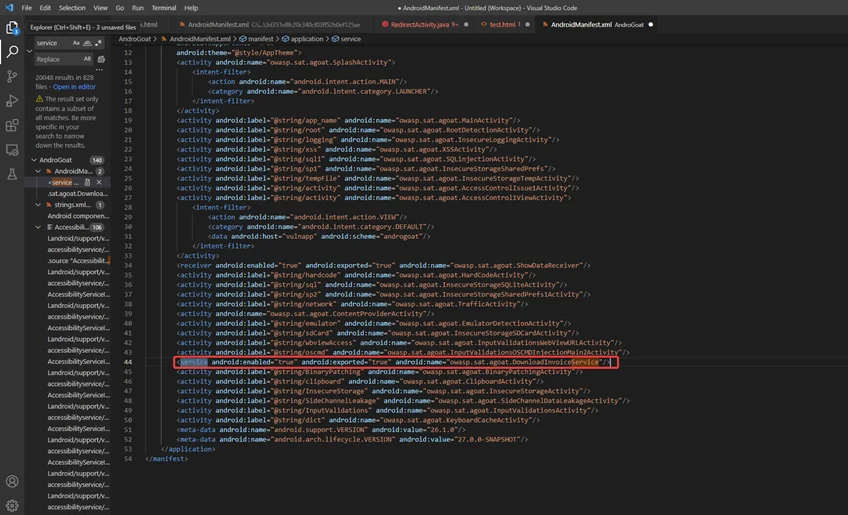
If access to an exported Service is not controlled, any application in the phone/device that can start is tied to the service. As a result, it enables an attacker/malicious application to perform illegal activities, get sensitive information, or damage the internal state of the victim’s application.
Another Android component that listens to broadcast messages from another application or the same system is the Broadcast Receiver. It can even send broadcasts to apps that are not currently operating.
For instance, the user receives a low battery notice. Android programmers can utilize broadcast messages within the app or outside of the normal flow.
The manifest file declares the following broadcast receivers:
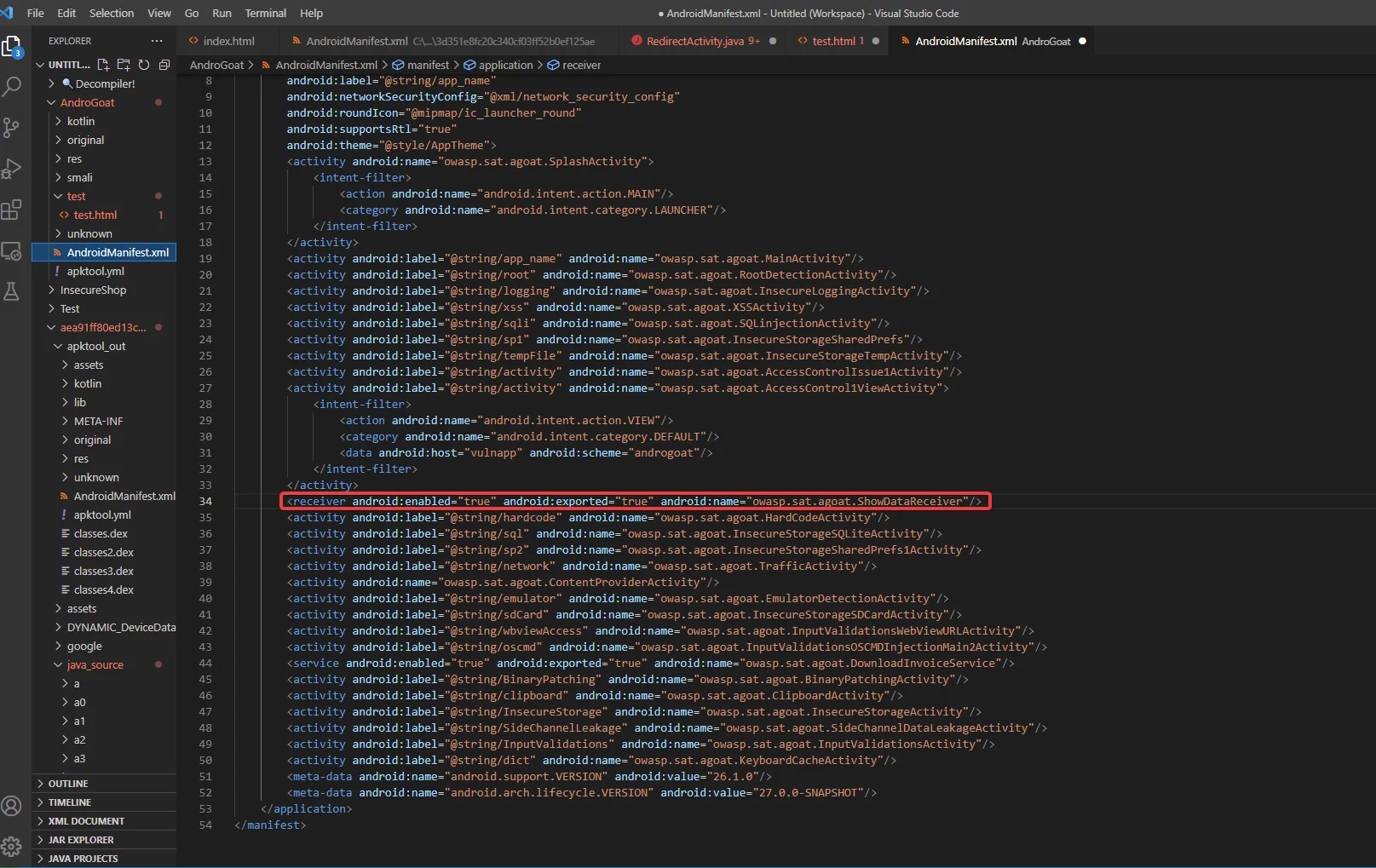
It masks the database’s details, which are used to read and write private application data that is not shared. As a result, without content providers, accessing data from other apps is difficult.
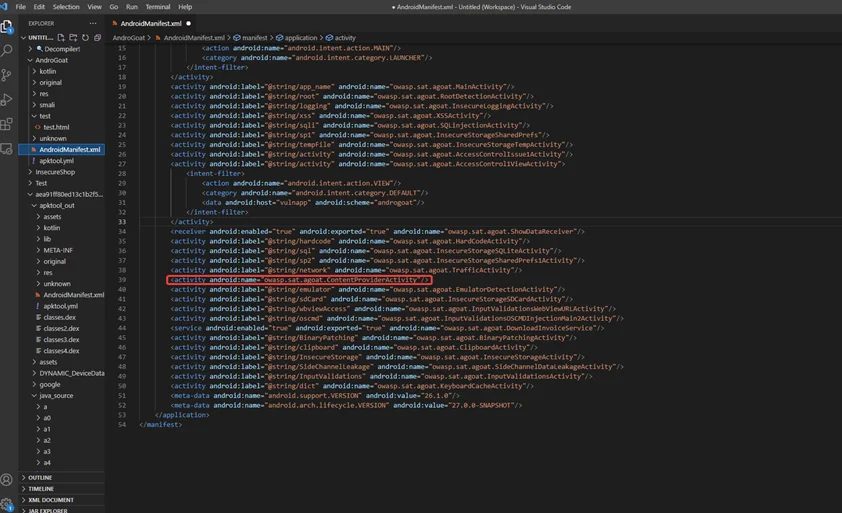
Consider looking for contact information in the contact list or requesting photographs from Content Provider’s gallery. If Content Provider access is not restricted to only a few apps, malicious apps might gain access to important data.
The property “android: exported = true/false” will be present in all android components, with the default value of “false.”
android:exported=true
If the exported property is set as true, the application, activity, service, or content provider can get access to other application components (like intent, layout, resources, etc.). The ADB utility can be used to start it.
We can use the following command to invoke the activity (which implies we can launch the exported activities without logging into the application):
adb shell am <package name>/.<activity name>
android: exported=false
This means that you can start Android components from within the same application using the same user ID.
The app requires access to restricted areas of the system or other applications. It can also provide any permissions that other apps must have in order to access the application’s content. Access to the internet, contacts, and the camera, for example, are all possible permissions.
Note: We need to see if the application has harmful permissions like WRITE and READ External Storage enabled.
The manifest file (in this case) declares the following permissions:
Additionally, there are two crucial options in the manifest file that we must be aware of: the Allow Backup and Debug values, both of which are set to false by default.
As can be seen below, allowBackup is set to true.
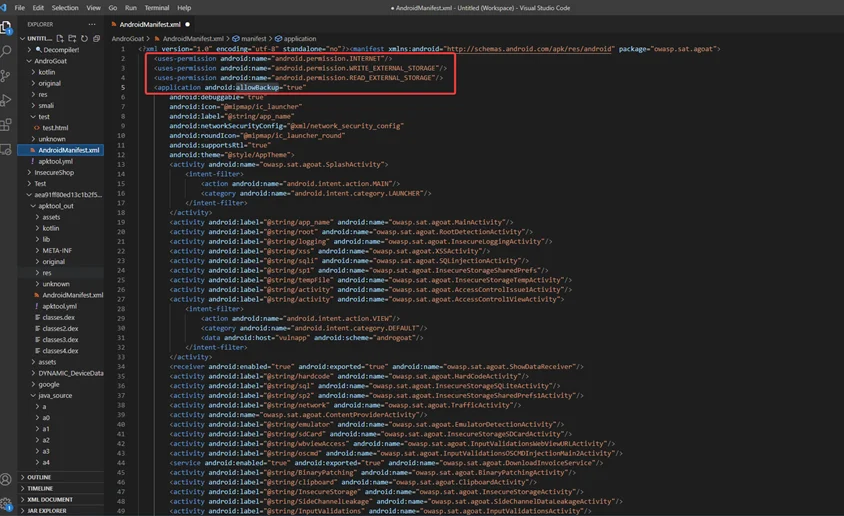
Applications can be backed up to external storage or another device via backup. The attacker can obtain backup information directly from an application sandbox without rooting the device if the user replaces or wipes their phone storage.
If this flag is set to true, an attacker can inject code to carry out this method in the background of a susceptible application process, allowing sensitive data from the application to be collected.
The minimum SDK version for any Android application must be greater than 18. Any application with a value less than 18 is insecure and subject to a variety of security issues, potentially risking the security of other apps.
Some basic security checks to carry out when examining the Android manifest file are listed below:
In this blog, we discussed static analysis and the various components of the Android manifest file (AndroidManifest.xml). In the upcoming blog we’ll briefly discuss dynamic analysis along with a basic walkthrough on Mobile Security Framework (MobSF).
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“