
In today’s digital landscape, protecting sensitive information is of utmost importance. As technology progresses, the tactics used by malicious individuals to illicitly access data also evolve. One such method is memory forensics, which involves extracting valuable information from a target device’s memory. In this guide, we will explore the process of dumping Android application memory, providing you with a comprehensive understanding of this essential security technique.
Memory forensics is a subset of digital forensics centered on extracting valuable data from the volatile memory of a target device. Unlike traditional disk forensics, which involves analysing stored data, memory forensics allows investigators to uncover information that may not be present on the disk. This includes passwords, encryption keys, network connections, and other artefacts that are only present in the device’s active memory.
Before diving into the process of dumping Android application memory, it’s essential to understand how Android handles memory management. Android applications are executed within a sandboxed environment called the Dalvik Virtual Machine (DVM) or the newer Android Runtime (ART). Each application has its own dedicated memory space, which is different from other applications running on the device.
Within an Android application’s memory, various components are stored, including the application’s code, data structures, and sensitive information. By analysing the application’s memory, security professionals can identify vulnerabilities, extract sensitive data, and understand the application’s behaviour.
To successfully dump Android application memory, several tools and prerequisites are required. Here’s a list of the essential components:
Ensure that you have a rooted Android emulator or device and have installed ADB, Frida server, and Frida-tools on your host system before proceeding.
Before we can begin dumping Android application memory, we need to set up and configure Frida. Frida provides the necessary tools and libraries to inject custom code into an Android application and extract memory data.
To install Frida, follow these steps:
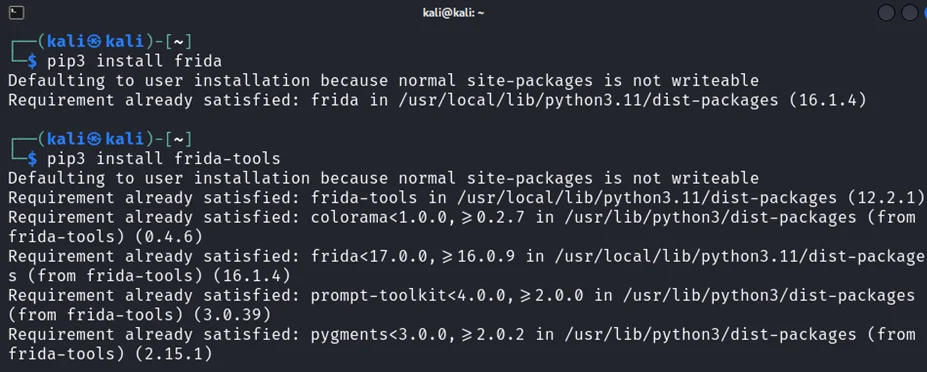
1) To install Frida, open the Kali Linux terminal and enter the following command.
pip3 install frida
pip3 install Frida-tools
You can download zipped Frida server file from the following link
https://github.com/frida/frida/releases
Download appropriate file based on your emulator version.
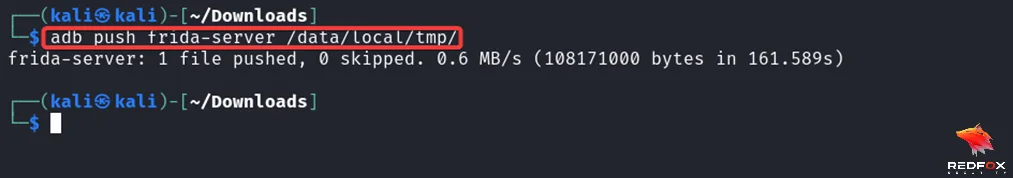
2) After building the Frida server, push it to the Android device or emulator using ADB:
adb push frida-server /data/local/tmp/
Change the permission of the frida-server file.
adb shell "chmod 755 /data/local/tmp/frida-server"
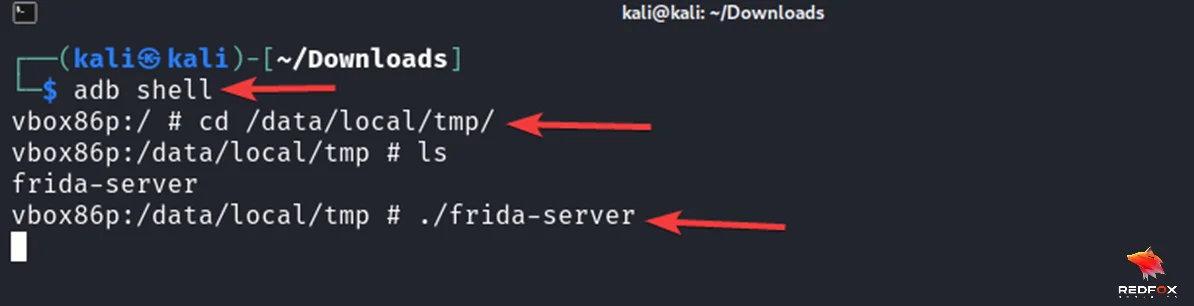
3) Finally, start the Frida server on the Android device:
adb shell "/data/local/tmp/frida-server &"
Some apps might be able to detect the frida-server location. Renaming the frida-server binary to a random name, or moving it to another location such as /dev may do the trick or You can start the Frida server straight from the emulator shell using adb.
With Frida installed and the server running on the Android device, we can proceed to dump Android application memory using Fridump.
Fridump is a powerful tool that leverages Frida’s capabilities to dump the memory of an Android application. By injecting custom code into the application’s process, Fridump can extract valuable information from the device’s memory.
To dump Android application memory using Fridump, follow these steps:
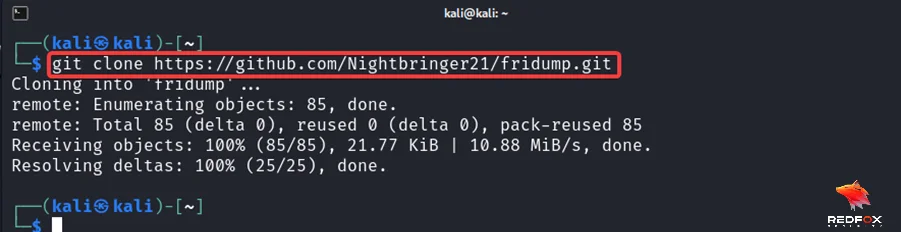
First you need to clone the Fridump repository from GitHub.
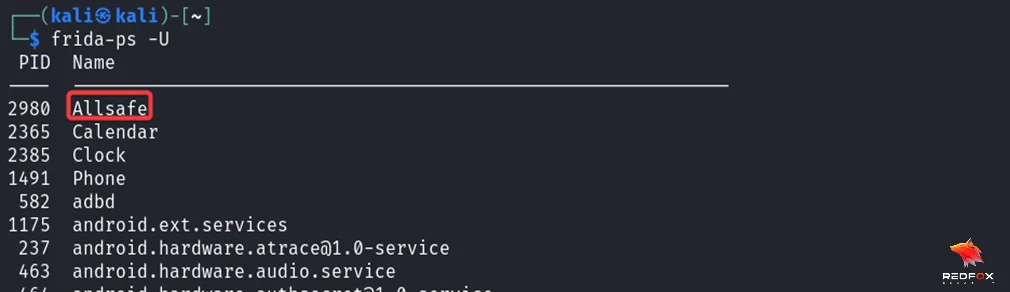
4) Identify the target application’s process name using the frida-ps command. Execute the following command in your terminal:
frida-ps -U
This command will display a list of running processes on the Android device, including the names of the applications.
5) Once you have identified the target application’s process name, execute the following command to dump its memory:
python3 fridump.py -U -s <process_name>
In this command, replace <process_name> with the actual process name of the target application.
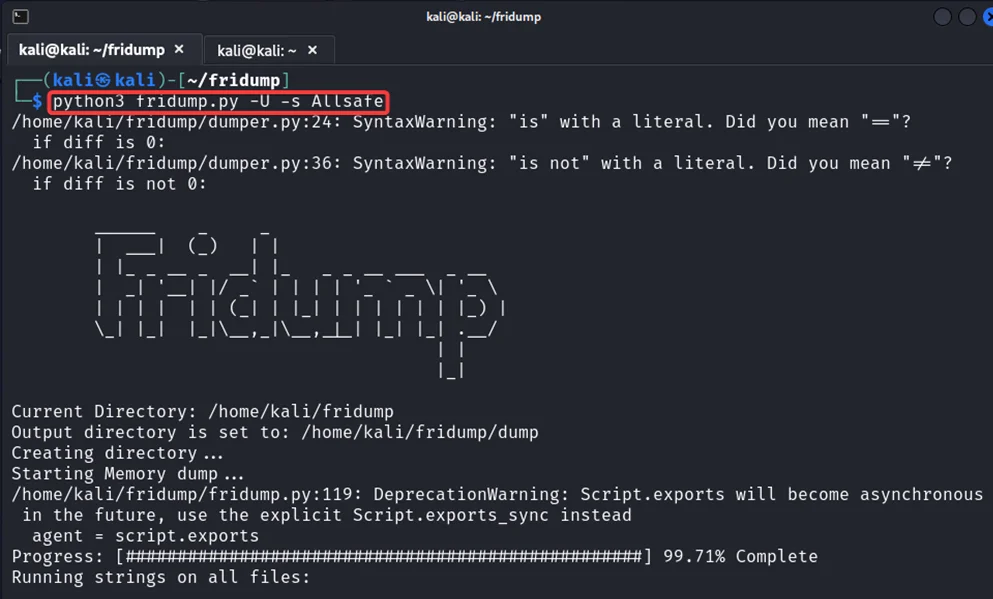
The memory dump will be saved in the dump/ directory of your current working directory.
Once the memory dump has been successfully created, it’s time to analyse its contents. The memory dump contains a wealth of information, including strings, code fragments, and sensitive data.
To analyse the memory dump, you can use various tools and techniques, including:
Through scrutinizing the memory dump, security experts can uncover valuable insights into the operational aspects of the target application and pinpoint potential security weaknesses.
One of the primary objectives of dumping Android application memory is to extract sensitive information that may be stored in memory. This includes passwords, encryption keys, and any other data that should not be accessible to unauthorized users.
To extract sensitive information from the memory dump, you can use various techniques:
By understanding and effectively applying memory forensics techniques, you can bolster your organization’s security posture and protect against the ever-evolving threats in today’s digital landscape.
Dumping Android application memory exposes the potential risks associated with storing sensitive information in memory. To mitigate these risks, it is essential to follow security best practices, including:
1) Implementing proper data encryption
Encrypt sensitive data stored in memory to protect it from unauthorized access.
2) Minimizing data retention
Only keep sensitive data in memory for the minimum amount of time required. Once the data is no longer needed, it should be promptly cleared from memory.
3) Secure coding practices
Follow secure coding guidelines to minimize the risk of vulnerabilities that could expose sensitive information in memory.
4) Regular security assessments
Conduct regular security assessments, including memory forensics, to identify and address any vulnerabilities or weaknesses in the application’s memory handling.
By implementing these measures, organizations can significantly reduce the risk of sensitive information being exposed through memory forensics.
To ensure the success of memory forensics and the effective extraction of valuable information, it is crucial to follow best practices. Here are some key recommendations:
By following these best practices, you can enhance the effectiveness and reliability of your memory forensics investigations.
In this guide, we have explored the process of dumping Android application memory as a crucial aspect of memory forensics. By leveraging tools such as Fridump and following best practices, security professionals can extract valuable information from the volatile memory of Android devices. This information can be used to identify vulnerabilities, analyse application behaviour, and enhance overall security.
Remember, memory forensics is a powerful technique that requires expertise and adherence to legal and ethical guidelines. Stay informed, keep your skills up to date, and always prioritize the security and privacy of sensitive information.
By understanding and effectively applying memory forensics techniques, you can bolster your organization’s security posture and protect against the ever-evolving threats in today’s digital landscape.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems, and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“