
Microsoft’s Xbox has evolved from a gaming console into a comprehensive entertainment ecosystem used by millions worldwide. However, like any complex software system, it is not immune to security flaws. One of the latest vulnerabilities—discovered by Filip Dragović—exposes a privilege escalation flaw in the Xbox Gaming Service component.
This blog explores the technical details, impact, and potential mitigations related to this vulnerability, highlighting how attackers could leverage a zero-day flaw to gain system-level privileges. We will also walk you through the proof of concept (PoC) demonstration and discuss the security implications for both users and system administrators.
The Gaming Service is a core subsystem responsible for managing various Xbox functionalities such as:
Game installations and updates
Save configurations and cloud sync
Access to gaming-related files and assets
Under normal conditions, this service uses impersonation—acting as the calling user—to perform directory operations and file moves using MoveFileW API calls. This design ensures that file operations respect user-level permissions.
However, the issue arises when certain directory changes or access-denied scenarios trigger unexpected fallback behavior within the service.
The Xbox Privilege Escalation vulnerability stems from how the Gaming Service handles directory change operations and impersonation reversion.
Here’s a simplified breakdown:
When a directory move operation fails under user impersonation (for example, due to access denial),
The Gaming Service reverts to performing the same operation under SYSTEM privileges.
This fallback execution is not properly validated, allowing attackers to manipulate directory structures and inject malicious code.
Essentially, an attacker can trick the Gaming Service into performing privileged file operations on their behalf—turning a low-privileged user context into a SYSTEM-level execution environment.
Attackers can exploit this flaw through directory manipulation and malicious DLL injection. The steps generally involve:
Preparing a Controlled Directory:
The attacker creates or manipulates a directory structure that will be used by the Gaming Service.
Dropping a Malicious DLL:
A crafted DLL file containing malicious payloads is placed within the controlled directory.
Applying Deny Delete ACLs:
The attacker adds an Access Control List (ACL) to prevent deletion or modification of specific files.
Triggering Directory Move:
During the Gaming Service’s directory change process, the impersonated move fails under user rights but succeeds under SYSTEM context—executing the malicious DLL as NT AUTHORITY\SYSTEM.
This sequence enables a privilege escalation attack without requiring administrative credentials.
A low-privileged user can install Xbox from the Microsoft Store and exploit it to escalate privileges and become an administrator. This can be done with the given steps:
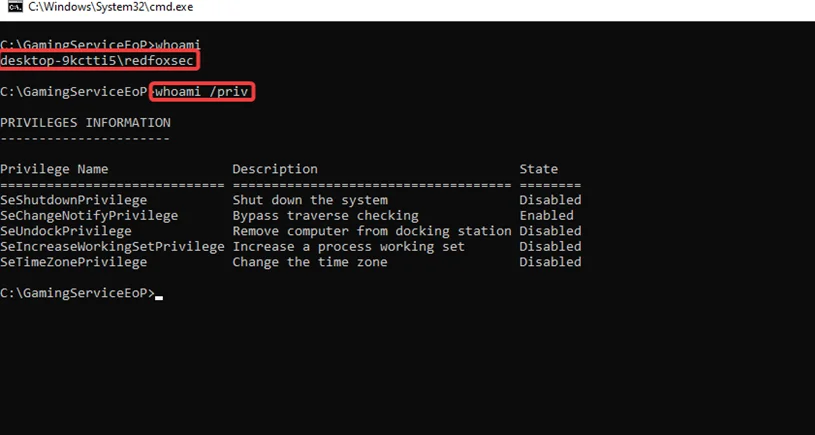
i. Install Xbox as low-privileged user named redfoxsec.
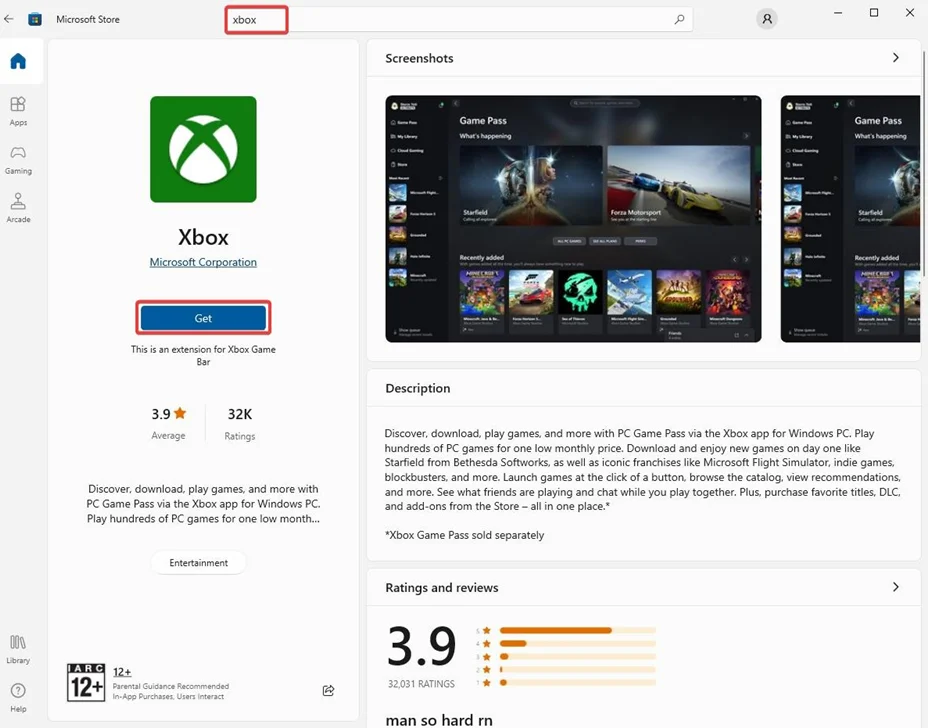
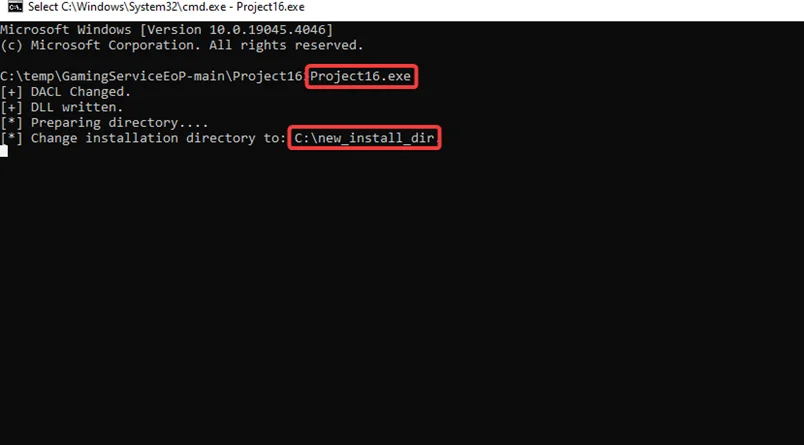
ii.After installation, run “Project16.exe” exploit and change the following Xbox Installation directory. Exploit link GamingServiceEoP.
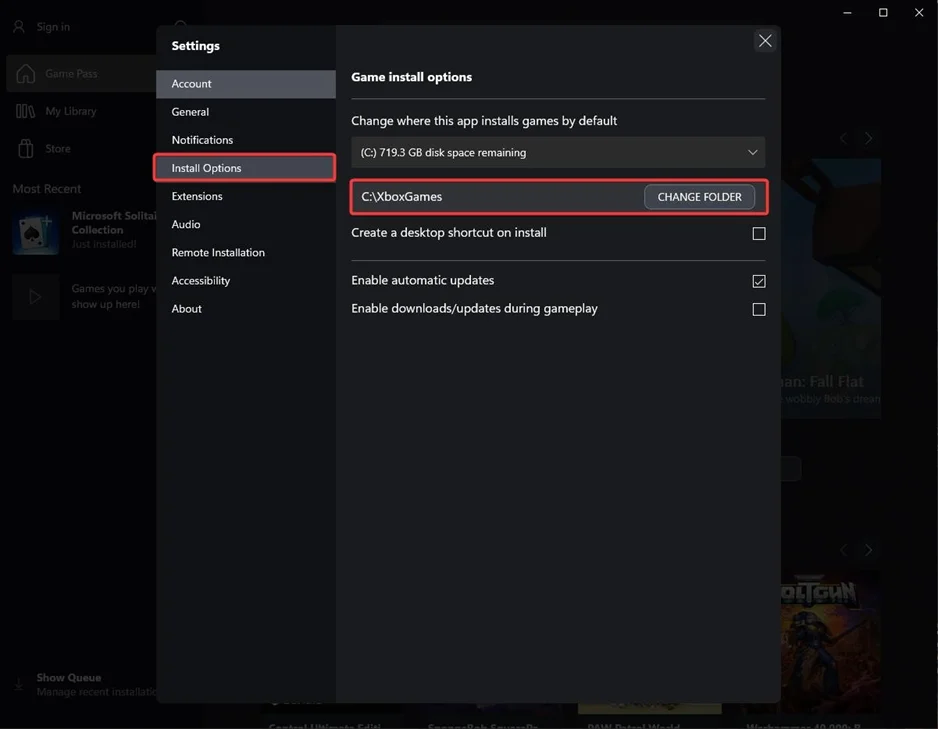
iii.Follow the steps to Change Xbox Installation directory. Open Xbox, click on “Sign In” and then open Settings.
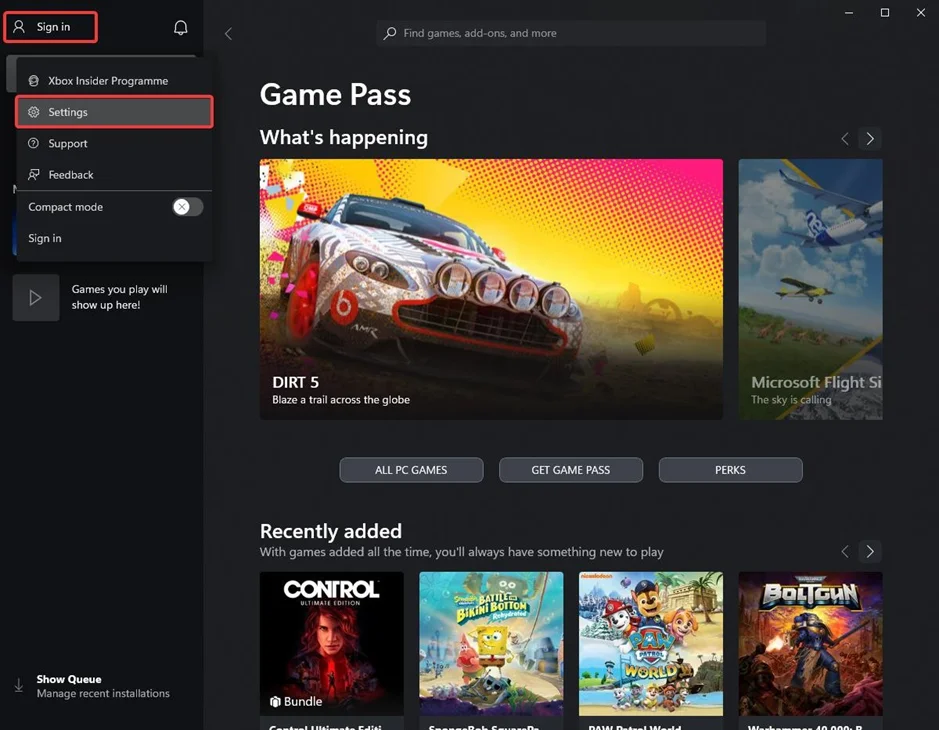
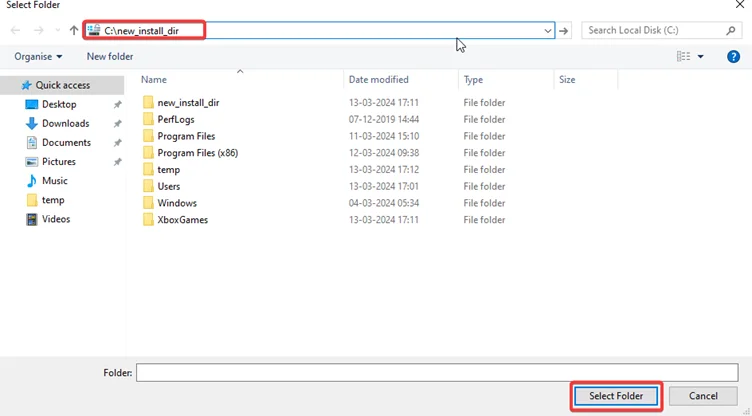
iv.After that, click on “Install Options” and “CHANGE FOLDER” to “C:\new_install_dir”.
v. After changing the Installation directory, the script gets executed and spawns new cmd as “NT AUTHORITY\SYSTEM”.
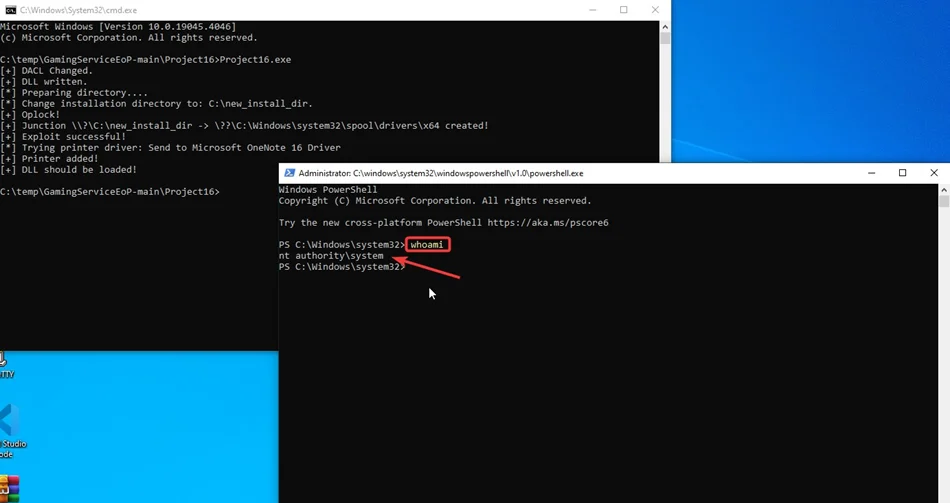
Although the PoC effectively demonstrates SYSTEM-level privilege escalation, Microsoft maintains that the exploit does not cross official security boundaries. Their reasoning is based on Xbox’s architectural model, where certain services are considered outside the traditional Windows privilege boundaries.
However, the real-world impact—allowing arbitrary code execution with elevated privileges—remains a significant concern from a security testing and ethical hacking perspective.
The consequences of exploiting this vulnerability are severe:
Full System Compromise: Attackers can execute arbitrary code as SYSTEM.
Persistence Mechanisms: Malicious code can install rootkits or backdoors.
Data Theft or Tampering: Access to sensitive system files, credentials, and tokens.
Further Network Penetration: The compromised host can be leveraged to escalate privileges across networks.
Given Xbox’s integration with Windows 10/11 services, exploitation could extend beyond gaming environments—posing broader risks to Windows-based ecosystems.
As of now, Microsoft has not released an official patch or CVE identifier for this issue. Their initial response classified it as “no security boundary crossed.”
Recommended Actions:
Update Xbox Services Regularly
Install the latest version of Xbox and Gaming Service once patches become available.
Restrict Low-Privileged User Actions
Prevent users from making directory or configuration changes that could invoke the vulnerable processes.
System Hardening
Apply Group Policy restrictions to block installation or modification of Gaming Service components by non-admin users.
Remove Xbox Components (If Unused)
In enterprise or high-security environments, remove or disable Xbox-related services from endpoints where gaming software is unnecessary.
The Xbox Privilege Escalation Zero-Day underlines a critical truth: even entertainment systems can harbor vulnerabilities with serious security implications. While Microsoft has acknowledged the issue, no official fix has yet been issued.
Staying vigilant, enforcing least-privilege principles, and monitoring abnormal service behaviors are essential defensive measures until a formal patch is released.
Redfox Security is a global network of expert security consultants dedicated to helping organizations enhance their cybersecurity posture. Our team provides comprehensive security assessments, vulnerability research, and remediation strategies across industries.
If you’re looking to improve your organization’s security posture or perform in-depth vulnerability testing, contact us today.
Join us on our journey of growth and development by signing up for our comprehensive cybersecurity courses.