
SWD stands as one of the lesser-noticed vulnerabilities of hardware security. Used for debugging and programming embedded systems, SWD allows developers to communicate directly with microcontrollers located on hardware devices – offering convenience during development but providing an attack surface that malicious actors could exploit. We will delve into its depths here in this article while exploring vulnerabilities as well as best practices for protection.
Serial Wire Debug (SWD) and Joint Test Action Group (JTAG) are both protocols used for debugging and programming microcontrollers. However, there are several key differences between them:
| Interface | Pin Count | Functionalities | Supported CPU Architectures | Topology | Special Features |
|---|---|---|---|---|---|
| SWD | 2 | Only programming and debugging | Only ARM | Star | Printing debug info via debug port |
| JTAG | 4 | Programming, debugging, and Boundary scanning for production tests | Many architectures not just limited to ARM as JTAG is an independent group | Daisy chained | Not supported |
In summary, the choice between SWD and JTAG depends on your specific needs and the nature of your project. If you’re working with ARM-based systems and pin count is a concern, SWD might be the better choice. If you need to perform boundary scans or if you’re working with non-ARM architectures, JTAG could be more suitable.
Understanding how the SWD interface operates is necessary for understanding its vulnerabilities. SWD consists of two wires: the clock line (SWCLK) and the data line (SWDIO), connecting the debugger and target device, respectively. Unauthorized access could enable attackers to extract sensitive data or inject malware into device firmware.
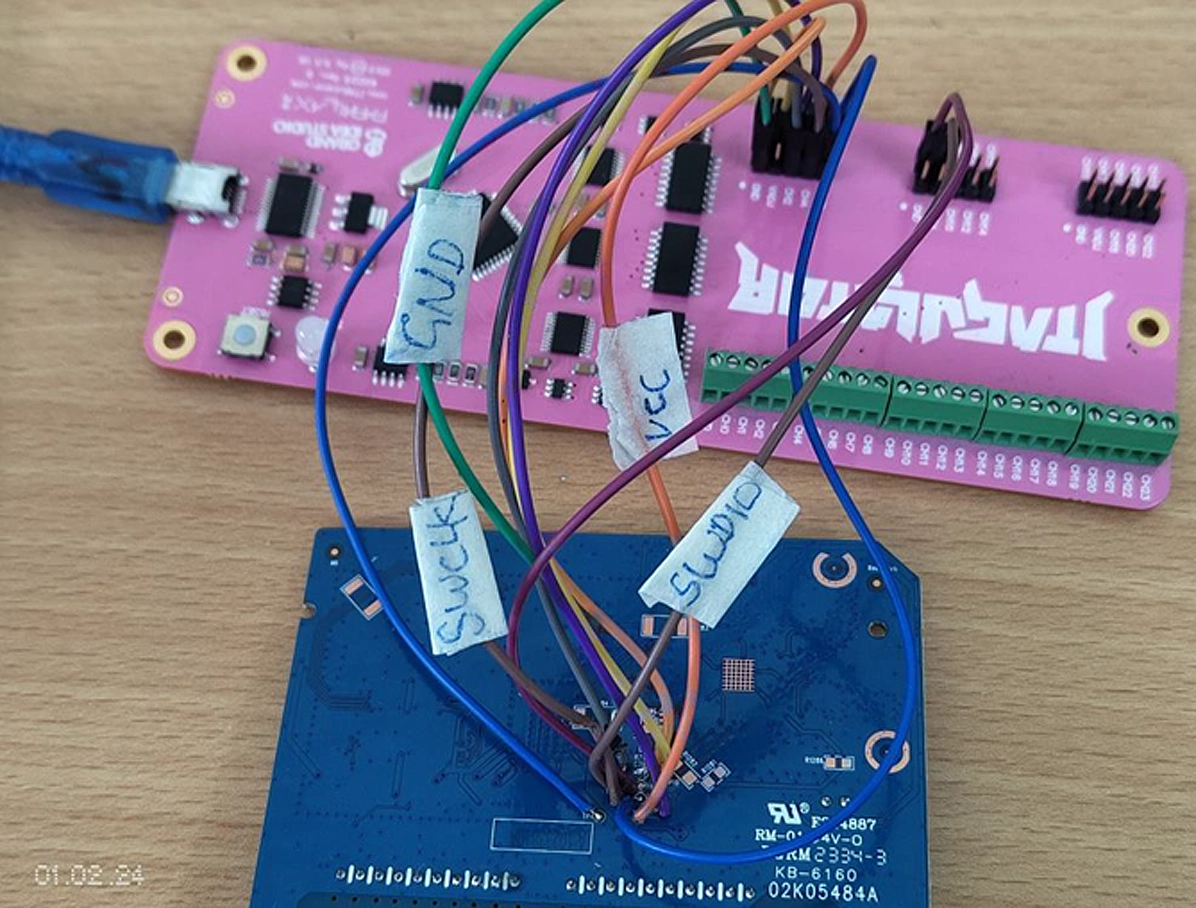
One key aspect of SWD attack surfaces is the ease of physical access to its debug interface. Though other attacks require sophisticated techniques, SWD can pose significant threats when installed in environments like public kiosks or industrial control systems where physical access may be limited or non-existent.
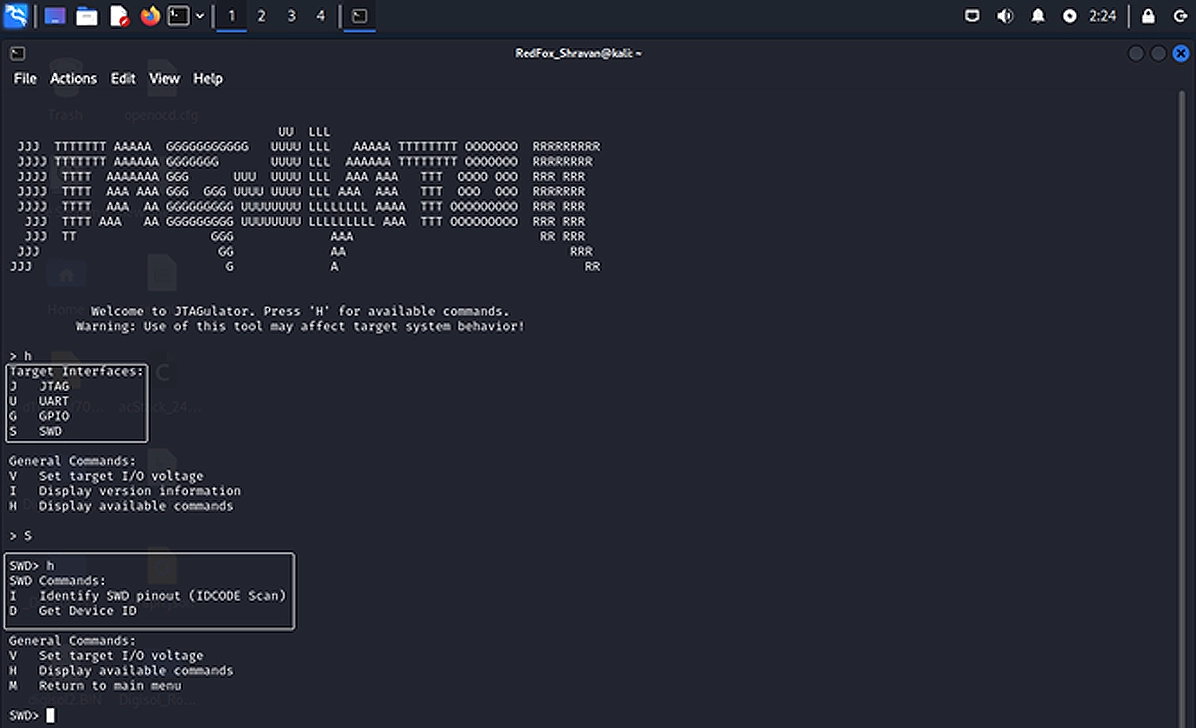
Adversaries employ various tools designed specifically for SWD attacks in order to conduct them successfully. Such tools typically come equipped with features designed to simplify exploitation.
A prime example is an SWD programmer, enabling attackers to read and write memory and registers of devices; another such tool is an SWD debugger, which allows them to halt execution on devices, analyse their state, and modify behaviour as part of an exploit process.
Attackers also utilize SWD probe adapters, which act as intermediaries between their machine and target device, and SWD emulators in order to leverage SWD attack surfaces to compromise hardware device security.
SWD attack surfaces contain several vulnerabilities that adversaries can exploit.
One such vulnerability is its lack of authentication and authorization mechanisms in its protocol; without proper authentication measures in place, an attacker could gain unauthorized access to your debug interface and then potentially compromise your device’s memory and registers, potentially jeopardizing its security.
Another source of vulnerability arises due to production devices leaving their SWD interface enabled; this oversight enables an attacker to connect to its debug interface even after it has been deployed and take advantage of it to access firmware or implant malicious code, leading to various security breaches.
Physical accessibility makes the SWD interface vulnerable to attacks such as side-channel analysis.
By regularly monitoring power consumption or electromagnetic emissions during communication via SWD, an attacker could obtain sensitive data such as encryption keys or authentication credentials, that would allow them to extract sensitive data such as encryption keys.
To minimize vulnerabilities caused by an SWD attack surface, various best practices and techniques should be utilized.
One essential measure is to disable or lock SWD once production begins, significantly reducing the risk of unauthorized access.
Implementing authentication and authorization mechanisms into SWD protocol can further bolster device security by only permitting trusted entities access to its debug interface, thus decreasing the risk associated with any unauthorized manipulation of device memory and registers.
Physically protecting an SWD interface by taking tamper-resistant measures can also be an effective strategy.
Sealing debug ports with epoxy seals or placing them where they cannot be reached directly is another means of physical safeguards that will make it harder for attackers to gain physical access to an SWD interface.
Hardware-level security measures may also help strengthen SWD attack surfaces.
One such measure is using secure microcontrollers that feature built-in protection against SWD attacks; such microcontrollers usually include secure boot capabilities, debug interfaces, and memory protection units that guard against unauthorized access or tampering.
Hardware security modules (HSMs) are another effective hardware-level solution to secure sensitive information.
By employing secure cryptographic algorithms and key management mechanisms, these components ensure the confidentiality and integrity of data during SWD communication.
Continuous monitoring and auditing of the SWD interface can also assist in detecting and preventing potential attacks, including by scanning debug ports for any unauthorized attempts or anomalous behaviour.
Furthermore, updating firmware with known vulnerabilities improves device security.
Firmware and software updates play an essential role in mitigating SWD vulnerabilities. For hardware manufacturers to offer timely updates to address any known flaws in either their SWD protocol or device firmware updates must include easily deployable patches that contain security patches or bug fixes for end-users to use immediately.
Developers should ensure that the SWD interface is enabled by default in production firmware to reduce the risk of unauthorized access. While this setting can be adjusted during development/debugging stages, it must be locked down before being distributed to end-users.
Firmware and software updates of hardware devices are essential in order to stay ahead of emerging threats and vulnerabilities, protecting the SWD attack surface, and offering more secure products to their customers.
The vulnerability associated with SWD presents substantial risks not just to consumer electronics but also to numerous sectors dependent on embedded systems, such as the automotive industry.
Exploiting SWD weaknesses could empower attackers to manipulate a vehicle’s firmware, potentially endangering crucial safety systems like brakes and steering.
Adversaries aiming to alter patient data or disrupt device functionality could target healthcare devices utilizing SWD interfaces.
Furthermore, vulnerabilities in smart grid systems utilizing SWD interfaces could allow access by third parties, potentially leading to widespread power outages.
Aerospace, defence, industrial automation and telecom industries also pose risks from SWD attack surfaces. Therefore, organizations in these sectors must prioritize hardware security measures that protect against SWD attacks.
Since technology develops and more devices become connected, the SWD attack surface in hardware remains of primary concern. Recognizing vulnerabilities introduced by this interface and taking effective precautionary steps against potential exploits is paramount to protecting both integrity and security in hardware devices.
Future advances in hardware security techniques to counter SWD attacks will include:
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
Join us on our journey of growth and development by signing up for our comprehensive courses.
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.