
StrandHogg is a critical Android vulnerability that exploits the OS’s multitasking system. It allows malicious applications to hijack legitimate app tasks and present counterfeit screens, tricking users into divulging sensitive information such as login credentials.
A user opens a banking app. A malicious app can intercept this action and display a fake login screen identical to what would be found within a banking application. Unknowingly, users enter their credentials that are then transmitted to an attacker.
What is an “Activity”?
An Activity represents a single, focused UI component that the user can interact with. Each screen in an app is typically one activity.
Activity Example:
1. A login screen is one activity.
2. A dashboard screen is another activity.
3. A settings page is a third activity.
What is a “Task”?
Tasks are defined as any set of activities users engage in to perform an action or workflow.
Task Example:
Every time a user completes activities like Login, Dashboard and Settings Page, they are performing an action and fulfilling a task.
Android tasks are collections of activities designed to accomplish one specific action or workflow.
What is a “Back Stack”?
The Back Stack is a stack (last-in, first-out) of activities that have been launched in a task.
Back Stack Example:
1) User is performing a task where he navigates to “activity1: Loginpage”
BackStack: Loginpage
2) User authenticates and was redirected to another activity “activity2: Dashboard”
BackStack: Loginpage –> Dashboard
3) User clicks on setting button and was redirected to third activity “activity3: Settings”
BackStack: Loginpage –> Dashboard –> Settings
4) Users press back button and was redirected to previous activity “activity2: Dashboard”
BackStack: Loginpage –> Dashboard
5) Users press back button and was redirected to previous activity “activity1: Loginpage”
BackStack: Loginpage
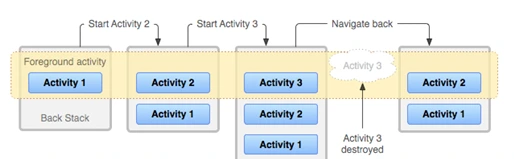
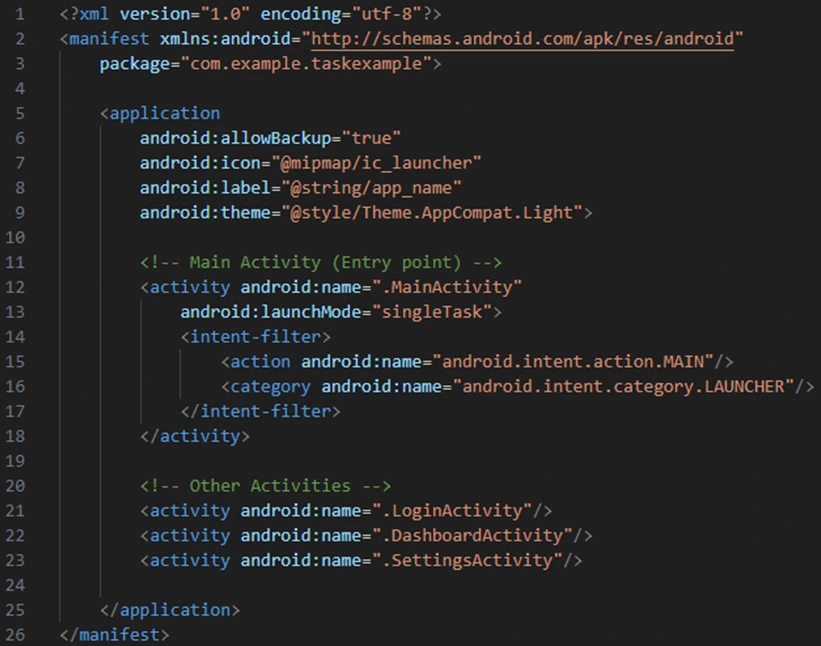
Explanation:
Activities: There are four activities in the app MainActivity as the root activity, and LoginActivity, DashboardActivity, and SettingsActivity as other activities.
Task: These activities together form a task, and as the user navigates through them,
Back Stack: The back stack stores the history of these activities, allowing the user to navigate back through the task.
What is taskaffinity?
TaskAffinity in Android is used to determine which task an activity belongs to. By setting a custom taskAffinity, activities can be placed in separate tasks. <activity android:taskAffinity=””/>
Example TaskAffinity:
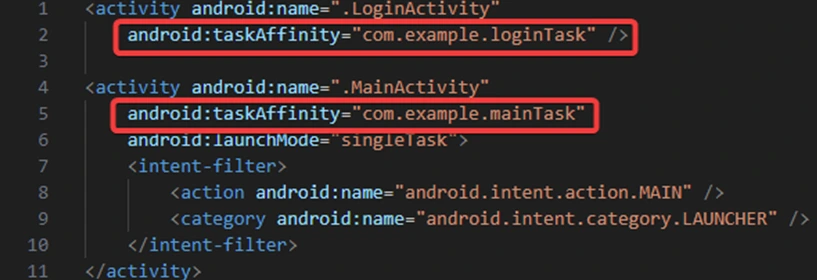
Explanation:
1) LoginActivity uses taskAffinity=”com.example.loginTask”
2) MainActivity uses taskAffinity=”com.example.mainTask”
Which confirms both have seperate task
This setup ensures that when the user logs out from MainActivity and presses back, they won’t be automatically logged in because the login process runs in a separate task
Launch mode are used to launch and manage activity in a android application
Four types of launch mode:
1) Standard: A new instance of the activity is created every time it is launched
2) SingleTop: If the activity is already at the top of the task stack, it is reused, or else new instance is created
3) Single Task: A login activity is set as singleTask to ensure only one instance is running in the task at a time
4) Single Instance: The activity is launched in a new task, and it is the only activity in that task, preventing any other activities from being added to it.
1) Launch Mode: Decompile the application using tools like ApkTool or jadx-gui. Locate the AndroidManifest.xml file and check for activities with android:launchMode=”singleTask”
2) Minimum SDK Version: In the same AndroidManifest.xml file, check the android:minSdkVersion. If it is less than 30, the application may not have protections against task hijacking vulnerabilities
2. Drag and drop the target APK file into the Jadx-GUI interface
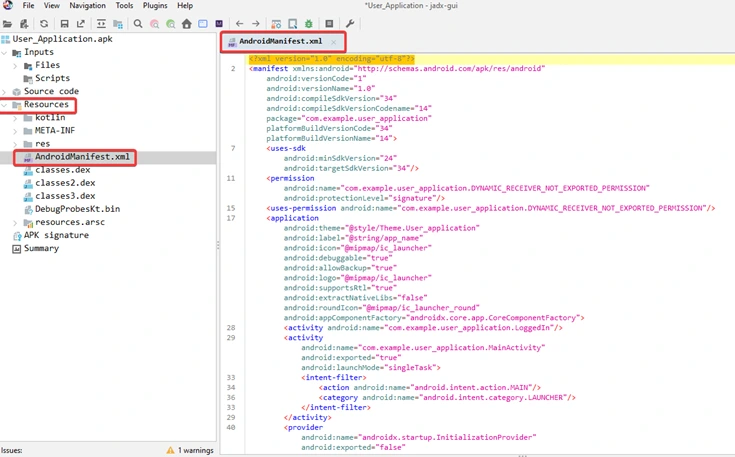
3. In the left-hand navigation pane, expand the Resources folder. Click on the AndroidManifest.xml file to view its content.
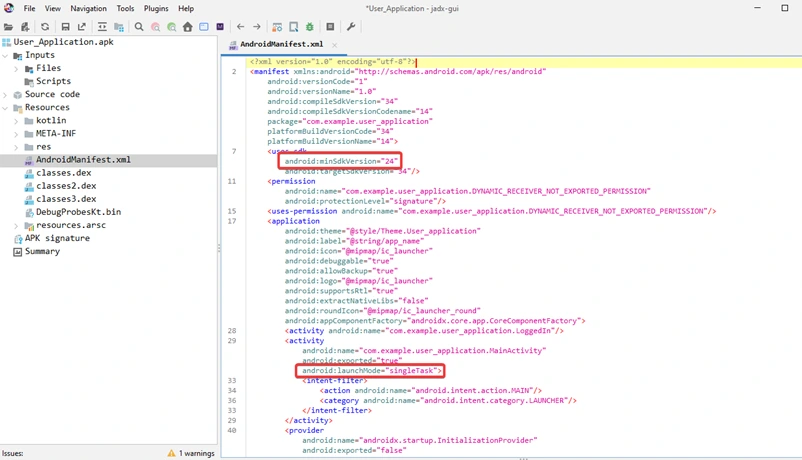
4. Look for the <uses-sdk> tag and check the android:minSdkVersion attribute. Confirm if its value is less than 30. Next Locate the <activity> tags and check if the android:launchMode attribute is set to singleTask
To dive deeper into how this vulnerability can be exploited, check out this blog: Task Hijacking (StrandHogg) Vulnerability Part 2
Attackers exploit taskAffinity to inject malicious activities into legitimate app tasks. These spoofed activities mimic real interfaces, enabling credential theft and unauthorized access.
Implications include:
This form of StrandHogg malware abuses Android’s flexibility at the expense of security.
Best Practices for Android developers:
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
Join us on our journey of growth and development by signing up for our comprehensive courses.