
Our security research has uncovered multiple high-risk vulnerabilities in the Syrotech SY-GPON-1110-WDONT router. These issues pose serious risks, including unauthorized access, data exposure, and weakened authentication mechanisms.
Below is a breakdown of each identified vulnerability, their impact, and proof of concept (PoC) summaries.

The router variant impacted is the Syrotech SY-GPON-1110-WDONT, with the firmware iteration.
Hardware Version: 3.7L
Firmware Version: 3.1.02-231102
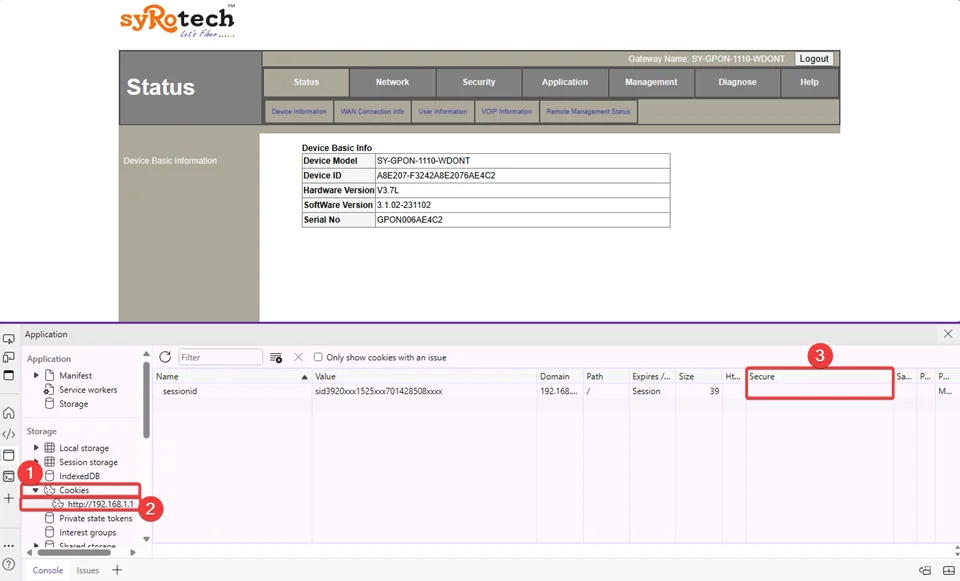
1. Cookie Without secure flag set (CVE-2024-41684)
Description:
The Syrotech SY-GPON-1110-WDONT router fails to set the “Secure” flag for cookies, making sensitive data vulnerable to interception over unencrypted connections. This flaw allows attackers to access session identifiers and other sensitive information, potentially leading to unauthorized access and manipulation of the router or network.
Impact:
Without the “Secure” flag on cookies, sensitive data, including session identifiers, is exposed and can be intercepted by unauthorized individuals. This vulnerability could enable attackers to access and compromise the router and network.
POC:
The router’s failure to set the “Secure” flag results in the transmission of sensitive information over unencrypted connections. Attackers can intercept these cookies via packet sniffing or man-in-the-middle attacks, posing a significant security risk.
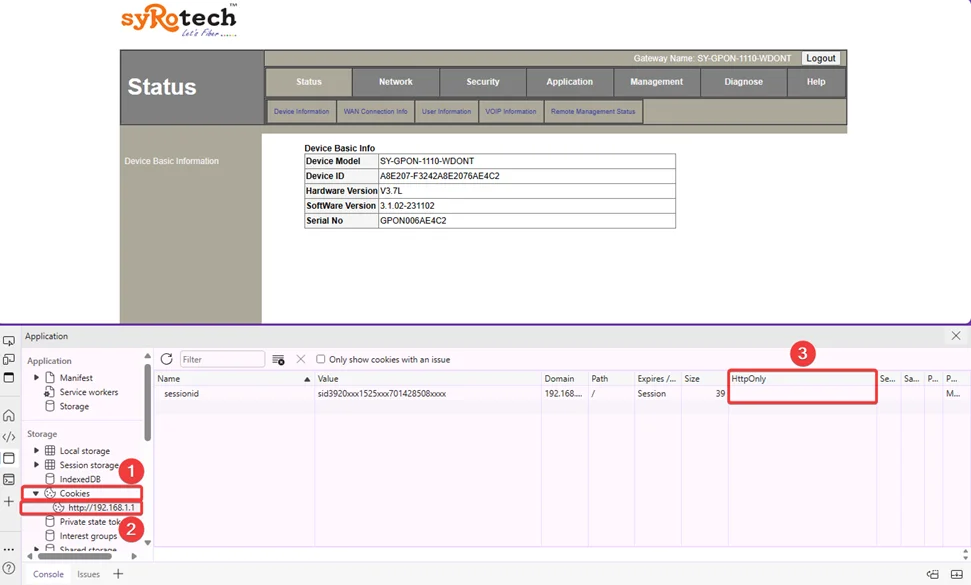
2. Cookie Without HTTPOnly flag set (CVE-2024-41685)
Description:
The router’s lack of “HTTPOnly” flag for cookies allows sensitive information to be intercepted over unencrypted connections. Attackers can exploit this to access and manipulate session data, posing significant security risks to the router and network.
Impact:
The Syrotech SY-GPON-1110-WDONT router fails to set the “HTTPOnly” flag for cookies, exposing session identifiers and other sensitive data to interception by unauthorized users. This vulnerability can lead to unauthorized access and compromise the network.
POC:
Due to the missing “HTTPOnly” flag, sensitive cookies are transmitted unencrypted and can be intercepted via techniques like packet sniffing or man-in-the-middle attacks. This vulnerability allows unauthorized access to user accounts and administrative interfaces, emphasizing the need for immediate remediation.
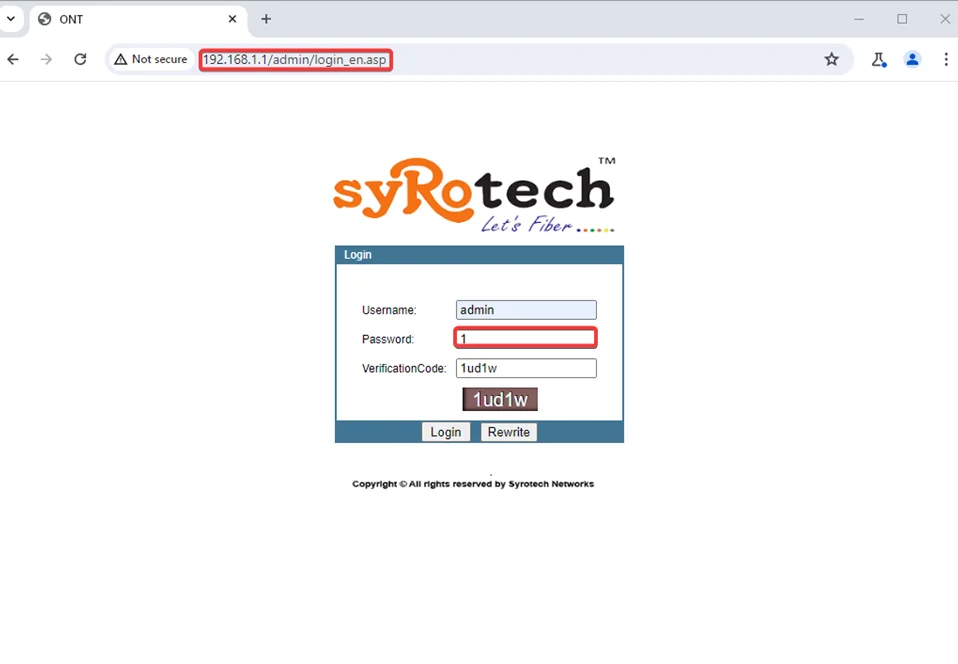
3. Password Policy Bypass (CVE-2024-41686)
Description:
The Syrotech SY-GPON-1110-WDONT router’s password policy bypass allows users to set passwords that do not meet security standards, weakening security and potentially exposing the router to unauthorized access and threats.
Impact:
Syrotech SY-GPON-1110-WDONT router vulnerability allows insecure passwords, risking unauthorized access, network manipulation, and potential data exposure. Immediate action is essential for remediation.
POC:
Users can bypass Syrotech’s password policies by setting a single-digit password on the SY-GPON-1110-WDONT router.
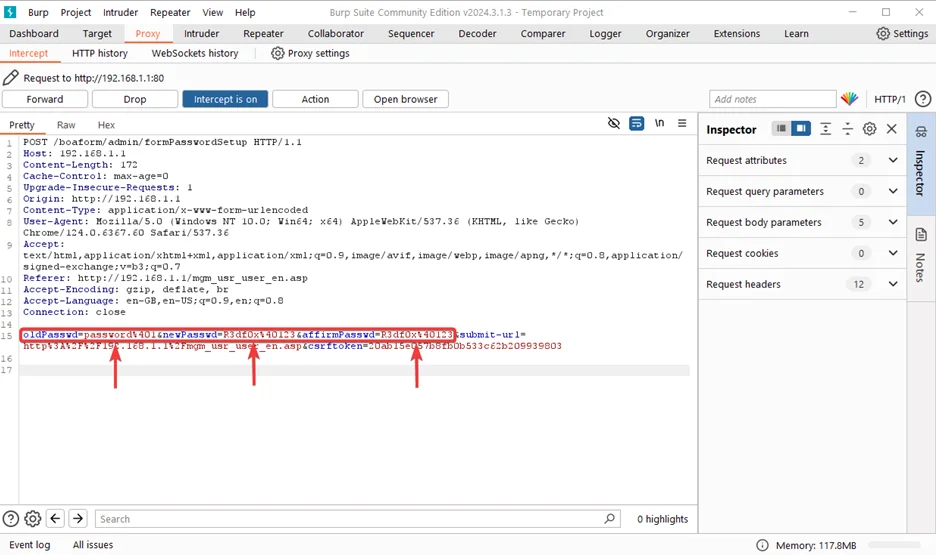
4. Cleartext Transmission of Sensitive Information (CVE-2024-41687)
Description:
The router’s critical vulnerability, “Unencrypted Credentials,” arises from storing passwords in cleartext. This flaw allows attackers to access and manipulate router settings if they gain access to the backend.
Impact:
The Syrotech SY-GPON-1110-WDONT router stores credentials in cleartext, leading to unauthorized access and manipulation risks. Immediate action is needed to mitigate these security threats.
POC:
Passwords are stored in cleartext, making them readable if an attacker accesses the router’s firmware or database. This flaw allows unauthorized access and manipulation, highlighting the need for urgent remediation.
5. Cleartext Storage of Sensitive Information (CVE-2024-41688)
Description:
Sensitive credentials are stored in cleartext, exposing the router to unauthorized access and manipulation. Immediate action is needed to fix this security flaw.
Impact:
The Syrotech SY-GPON-1110-WDONT router stores sensitive credentials in cleartext, risking unauthorized access and data exposure. Immediate remediation is required.
POC:
Credentials stored in cleartext can be read if an attacker gains access to the router’s firmware or database, leading to unauthorized access and potential manipulation.
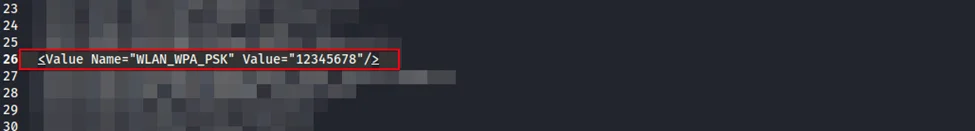
6. Hard-Coded Credentials (CVE-2024-41689)
Description:
Sensitive WLAN_WPS_PSK password is stored insecurely in the router’s code, allowing attackers to steal credentials if they access the script. Immediate action is required.
Impact:
The Syrotech SY-GPON-1110-WDONT router stores the WLAN_WPS_PSK password in the code, risking unauthorized access and network compromise. Immediate remediation is needed.
POC:
The WLAN_WPS_PSK password is exposed in the source code, enabling attackers with firmware access to bypass WPS PIN and gain Wi-Fi network access.
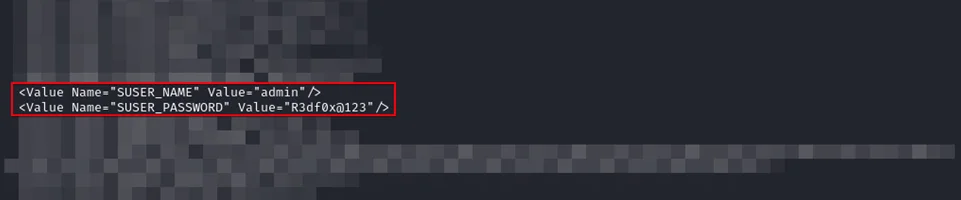
7. Default Credential Storage in Plaintext (CVE-2024-41690)
Description:
Default web UI credentials are stored in cleartext, exposing the router to unauthorized access and control. Immediate action is needed to address this security issue.
Impact:
The Syrotech SY-GPON-1110-WDONT router stores default web UI credentials in cleartext, risking unauthorized access and router manipulation. Immediate remediation is necessary.
POC:
Default credentials in plaintext can be accessed if an attacker gains entry to the router’s firmware or database, allowing them to manipulate settings and access the router.

8. Insecure Storage of Sensitive Information (CVE-2024-41691)
Description:
Sensitive FTP credentials are stored improperly, allowing unauthorized access to the router’s FTP service. This flaw in authentication controls can expose sensitive files and configurations.
Impact:
The Syrotech SY-GPON-1110-WDONT router stores FTP credentials insecurely, risking data security, network integrity, and user privacy. Immediate action is needed.
POC:
Credentials stored in cleartext in the firmware or database can be read by unauthorized users, enabling them to manipulate settings and access the router.
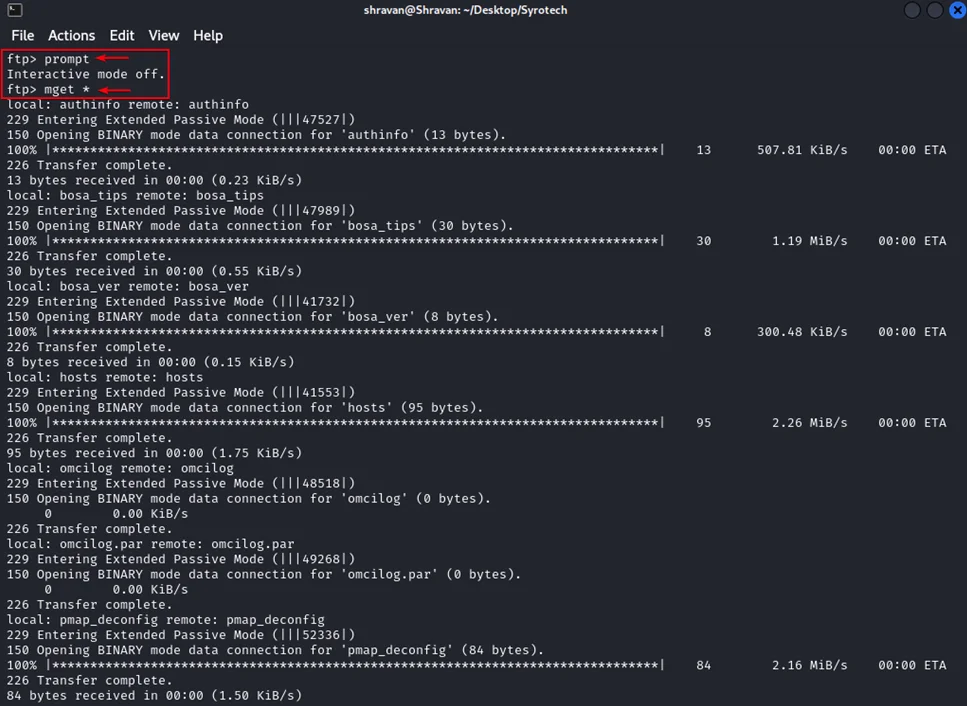
9. Incorrect Access Control (CVE-2024-41692)
Description:
The Syrotech SY-GPON-1110-WDONT router has an unsecured UART/Serial interface (Rx, Tx, Vcc, Gnd) at TTL-level and 115200 baud, exposing log output and a root terminal.
Impact:
Physical access allows attackers to fully compromise the device, potentially exposing sensitive data.
POC:
Accessing the device’s UART interface reveals sensitive log output and root terminal access.

These vulnerabilities have been addressed and detailed on CERT-IN’s website. right here: CERT-IN Advisory CIVN-2024-0225
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
Join us on our journey of growth and development by signing up for our comprehensive courses.