Legacy home and SOHO routers remain attractive targets for attackers. They sit at the network edge, handle all inbound/outbound traffic, and often expose a browser-based admin interface that’s reachable from local—sometimes even remote—networks. Once these devices are retired by the vendor, security updates slow to a trickle or stop entirely, leaving long-lived flaws unpatched. Default or weak credentials, dated web stacks, WPS weaknesses, and permissive configurations (e.g., UPnP, remote management) compound the risk for small offices and home labs that depend on “set-and-forget” gear.
During a recent assessment, we reviewed the Netgear WNR614 (JNR1010V2) N300 and identified several critical issues that could enable unauthorized access, configuration tampering, and leakage of sensitive information. This post explains what we found, who’s affected, why it matters, and the exact steps you should take now.
In this blog, we will explore the specific vulnerabilities we discovered, how they can be exploited in real-world scenarios, the potential business impact, and both immediate hardening actions and long-term replacement guidance.
Our assessment uncovered multiple vulnerabilities in the Netgear WNR614 (JNR1010V2) N300 running firmware V1.1.0.54_1.0.1. Exploitation could allow attackers to bypass security controls, access the administrative interface, and obtain sensitive information.
Note: The Netgear WNR614 N300 reached End of Service(EOS) in 2021 and no longer receives official patches or support. Where possible, replacement with a currently supported device is strongly recommended.

Model: Netgear WNR614 (JNR1010V2) N300
Firmware: V1.1.0.54_1.0.1
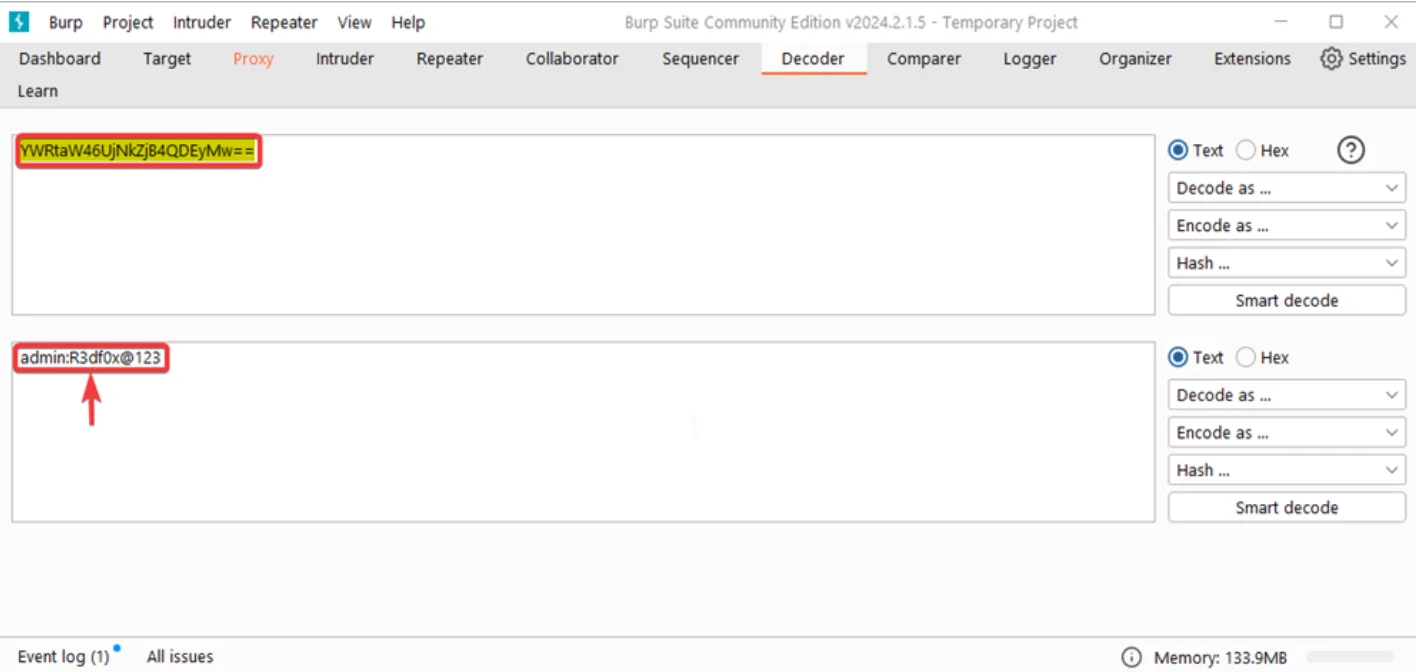
1. Improper Authentication / Broken Access Control (CVE-2024-36787)
Description: Authentication weaknesses may allow access to the administrative interface via unspecified vectors.
Impact: Enables unauthorized administration, configuration tampering, and potential loss of confidentiality/integrity.
Mitigation: Upgrade to the newest available firmware for your device. If none is available due to EOS, replace the router.
Observed Behavior: Weak auth protections make credential guessing/derivation far easier than intended.
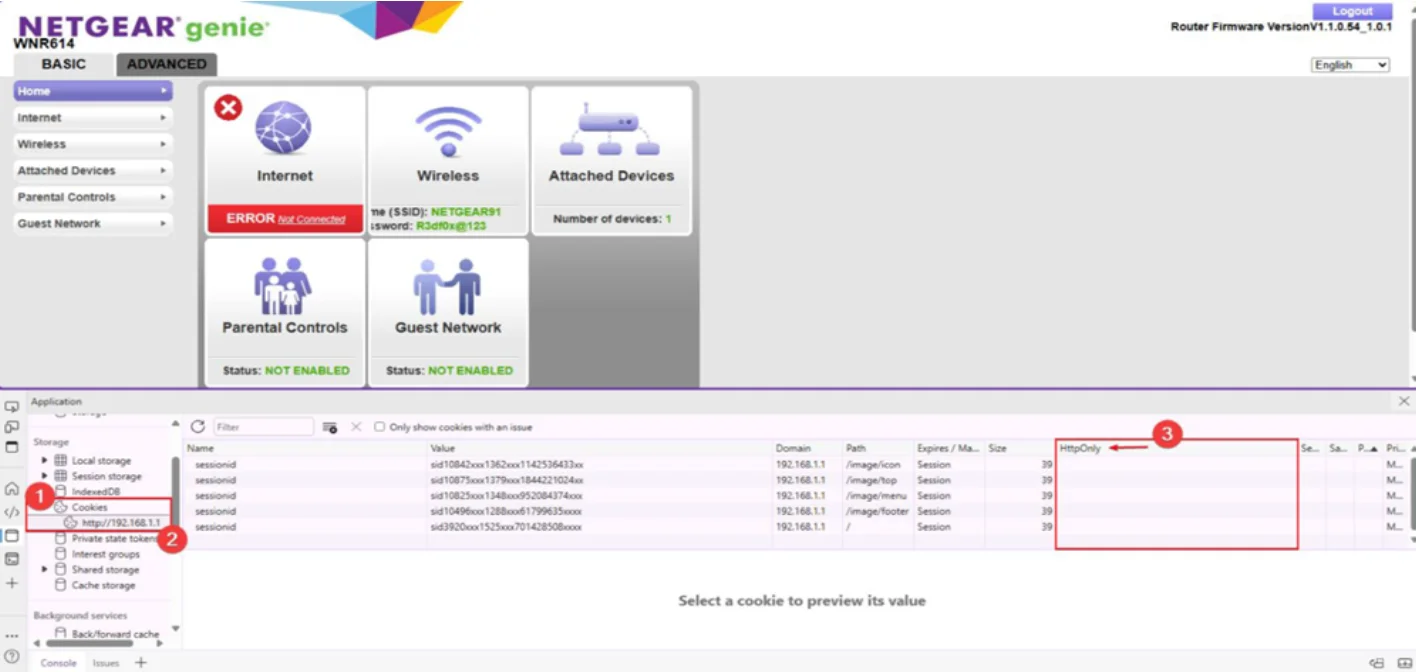
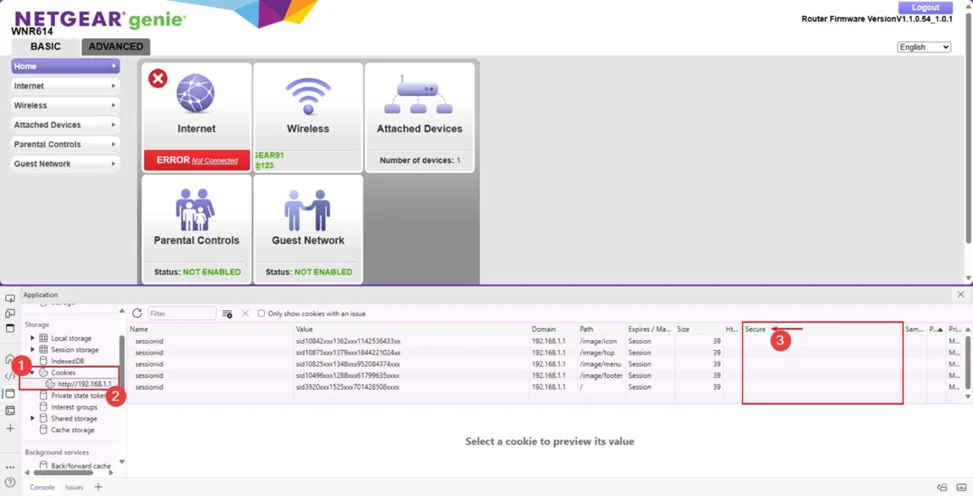
2. Cookie Without HTTPOnly / Secure Flag Set (CVE-2024-36788)
Description: Session cookies are not consistently set with HttpOnly (and may lack Secure), increasing the risk of client-side access.
Impact: Potential session exposure and hijacking, especially on untrusted networks.
Mitigation: Update firmware if possible. Place the admin interface behind a trusted management network or VPN; avoid administering over HTTP; disable remote management.
Observed Behavior: Incomplete cookie flags could allow client-side scripts or intermediaries to access session data.
3. Password Policy Bypass (CVE-2024-36789)
Description: Password complexity checks can be bypassed, allowing creation of trivially weak credentials.
Impact: Elevated risk of unauthorized login via guessing or brute force.
Mitigation: Update firmware where available. Enforce strong, unique passwords via process/policy; disable default accounts; limit login attempts with upstream controls (e.g., management VLAN + ACLs).
Observed Behavior: The device accepted extremely weak passwords that do not meet standard complexity requirements.
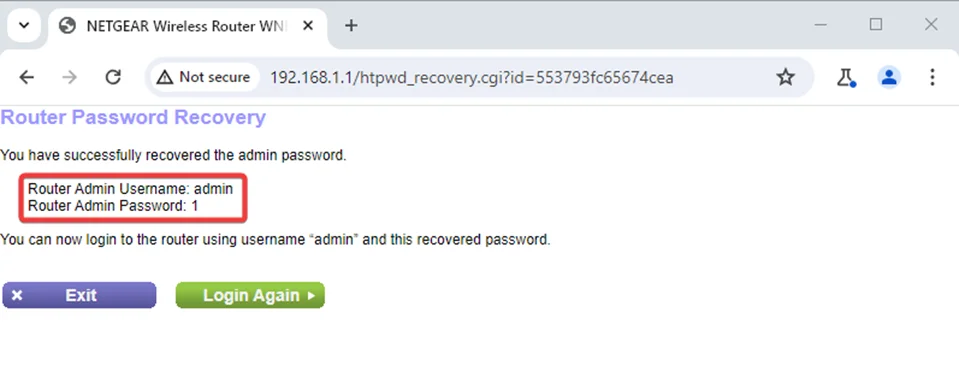
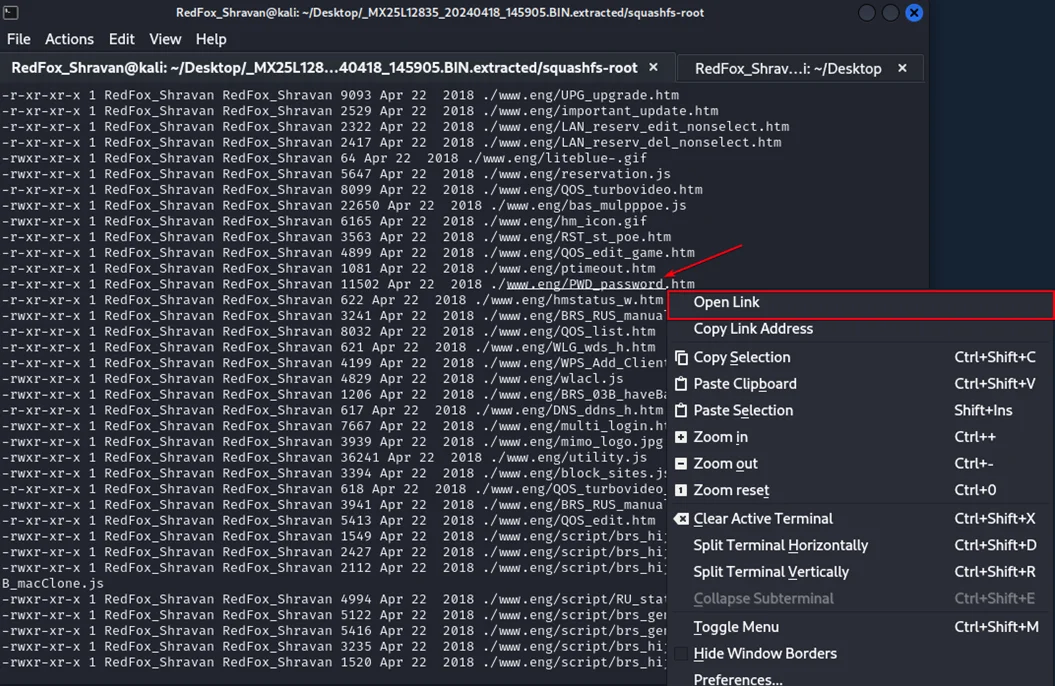
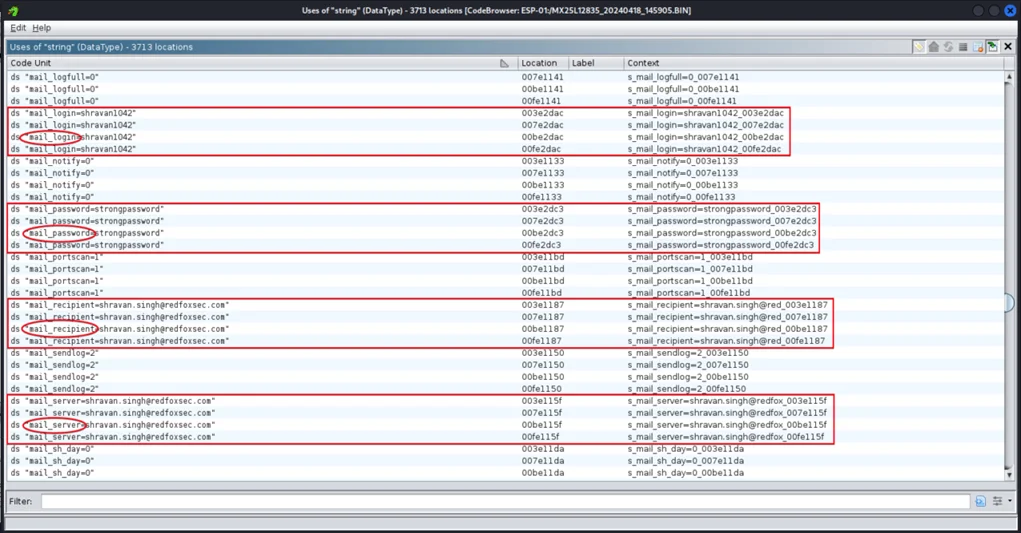
4. Password Storage in Plaintext / Incorrect Access Control / Cleartext Storage of Sensitive Information / Information Disclosure (CVE-2024-36790)
Description: Credentials are stored in plaintext in firmware or configuration, increasing the blast radius of any file/system access.
Impact: Credential disclosure leading to further compromise of network services and devices.
Mitigation: Update firmware if possible; rotate all credentials (admin, Wi-Fi, services) after remediation; restrict and monitor access to backups/config exports.
Observed Behavior: Sensitive authentication material was accessible in an unencrypted form.
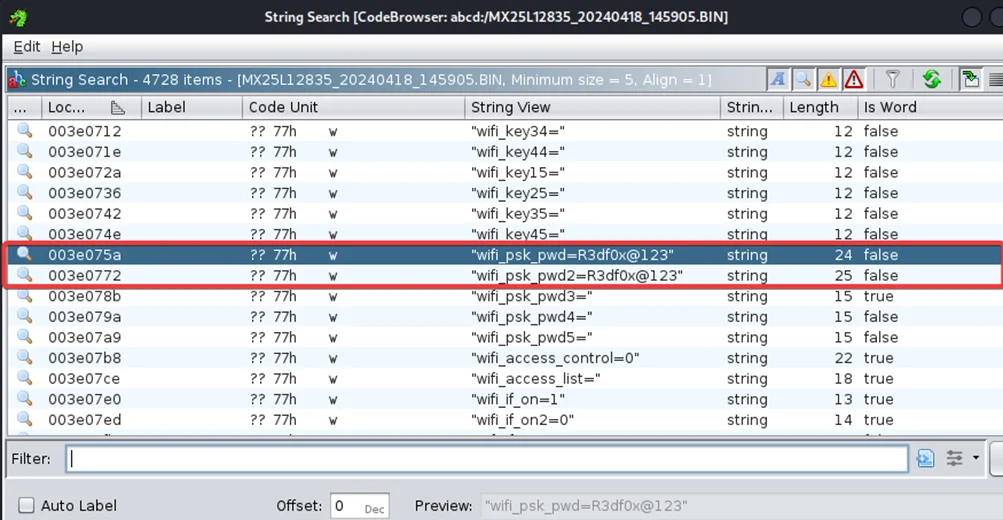
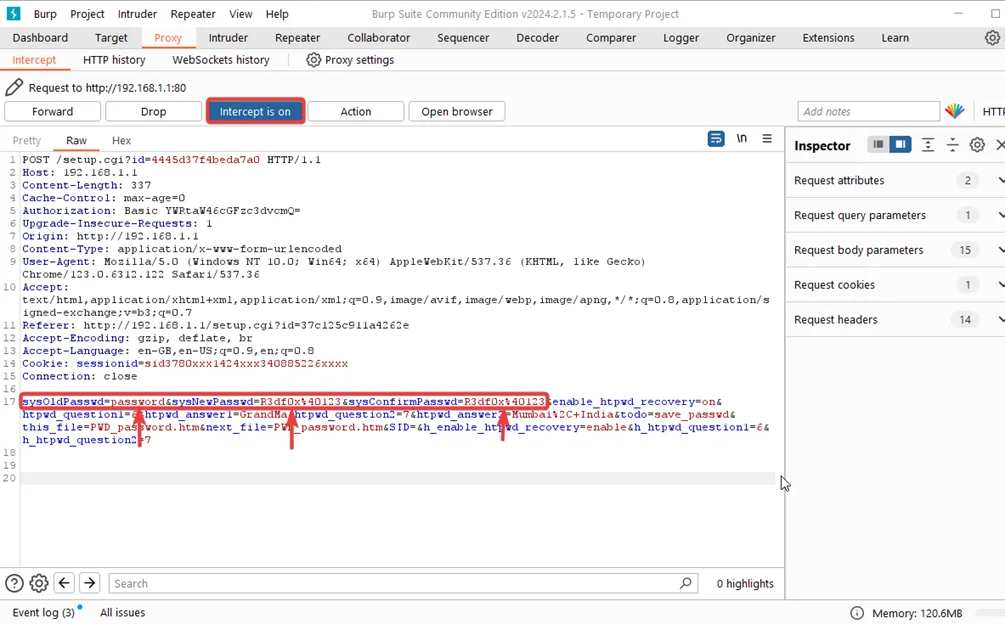
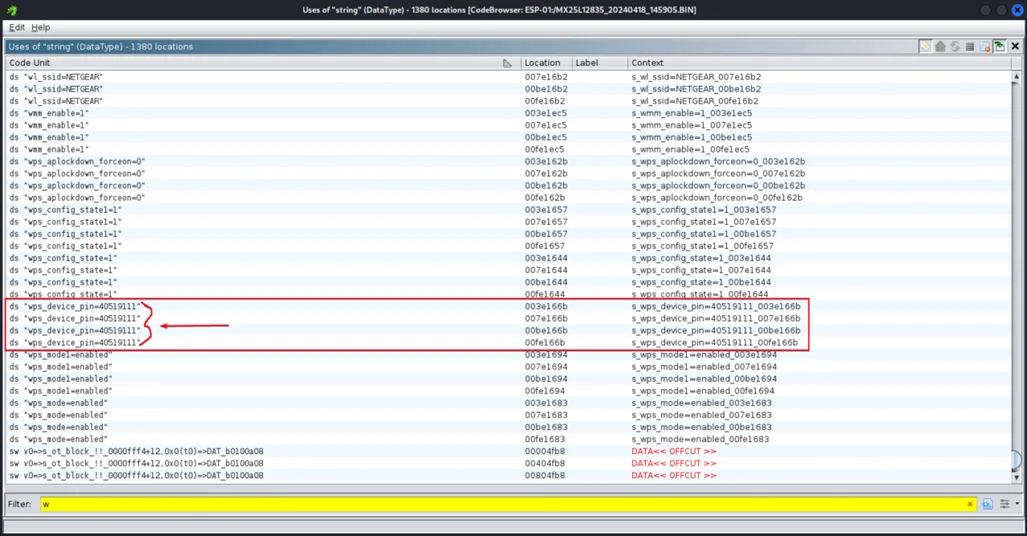
5. WPS PIN Exposure (CVE-2024-36792)
Description: Weaknesses in WPS implementation could reveal or allow misuse of the router’s PIN.
Impact: Unauthorized network access via WPS and subsequent configuration changes.
Mitigation: Disable WPS entirely; update firmware if available; prefer WPA2/WPA3-PSK with strong passphrases.
Observed Behavior: WPS handling could expose or permit abuse of the PIN mechanism.
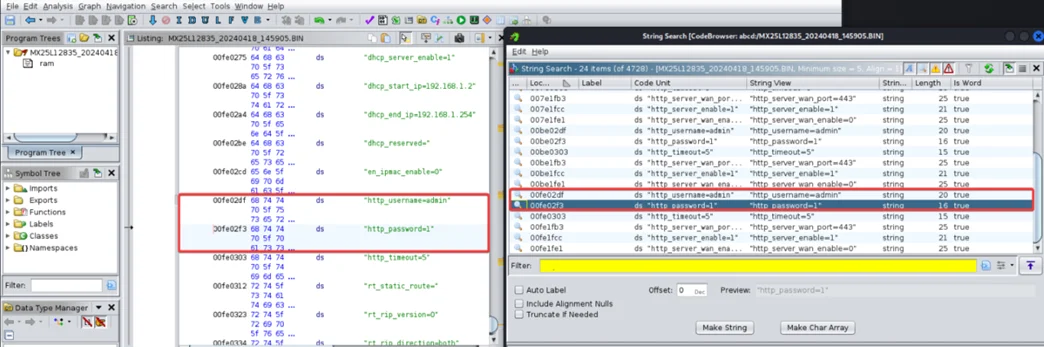
6. Insecure Permissions (CVE-2024-36795)
Description: Insecure permissions allow access to URLs and directories embedded in the firmware via unspecified vectors.
Impact: Exposure of sensitive data (e.g., service credentials) and increased likelihood of full administrative compromise.
Mitigation: Update firmware where available; restrict management access to a dedicated network; block WAN-side management; monitor for unusual requests.
Observed Behavior: Sensitive paths were accessible in ways that could leak configuration details.
1. Short Term (Immediate Hardening)
Disable remote/WAN management and WPS.
Restrict admin access to a management VLAN or site-to-site/host VPN.
Change all admin and Wi-Fi credentials to strong, unique values; rotate any credentials stored in backups/exports.
Use HTTPS for management where supported; avoid administering over untrusted networks.
Place the router behind an upstream firewall with ACLs to limit management ports.
2. Medium Term (If You Must Keep the Device)
Apply the latest available firmware (if any).
Export configuration, review for sensitive data, and purge/rotate exposed secrets.
Increase monitoring and logging for admin logins and configuration changes.
Consider disabling unused services (UPnP, Telnet, legacy ciphers) and closing unneeded ports.
3. Long Term (Best Practice)
Replace the WNR614 with a currently supported model that receives routine security updates and offers WPA3, modern TLS, and robust policy controls.
The Netgear WNR614 (JNR1010V2) N300 on firmware V1.1.0.54_1.0.1 contains multiple high-impact vulnerabilities (auth bypass, weak session handling, password policy flaws, plaintext secret storage, WPS PIN exposure, and insecure permissions). Because the product reached EOS in 2021, the most reliable fix is to replace the router. Until then, apply any available updates, disable WPS and remote management, lock down admin access, and rotate credentials.
Redfox Security is a global team of seasoned security consultants helping organizations find and fix vulnerabilities before attackers do. We deliver hands-on assessments, clear remediation paths, and training that builds lasting capability.
Need help? If you’re concerned about your network’s exposure, reach out to discuss a tailored test plan. Join our comprehensive security training programs and gain the practical expertise to defend your environment effectively.