
Operational technology (OT) is hardware and software that detects or causes a change, through the direct monitoring and/or control of industrial equipment, assets, processes and events. Industrial control systems (ICS) are a main component of operational technology. Operational technology is in charge of procedures that, if compromised, might result in critical service disruptions and even loss of life. The proper running of emergency services, water treatment facilities, traffic management, and other important infrastructure is dependent on operational technology solutions. While adversaries have traditionally focused on stealing data, they are increasingly targeting OT networks as they know the risk of interruption due to insufficient OT security. They’re working on more sophisticated and damaging strikes aimed squarely at operational technology firms.
The Purdue Enterprise Reference Architecture (PERA) identifies the different tiers of vital infrastructure utilized in manufacturing lines, as well as how to safeguard them. If implemented correctly, PERA could achieve the air gap between OT and IT systems. The Purdue model was adopted from the Purdue Enterprise Reference Architecture model by ISA-99. This model provided a framework for segmenting industrial control system networks from corporate enterprise networks and the internet. It’s segmented into separate levels.
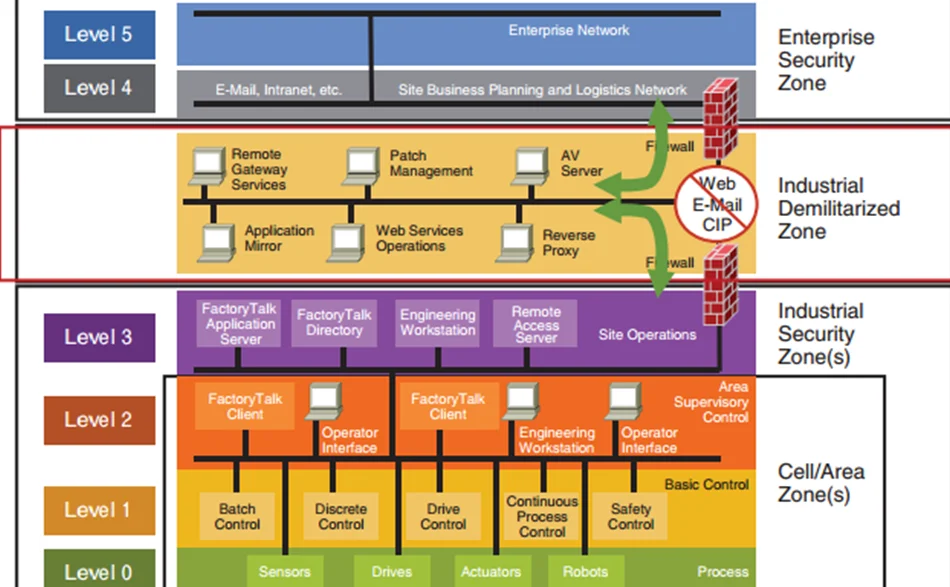
This level’s systems are typically corporate-wide and span many locations or factories. They collect data from subordinate systems in specific plants and combine it with other information. The majority of these systems are housed in corporate data centers. Plant production schedules, material usage, shipping, and inventory levels are all controlled by ERP systems present in this level.
All the IT systems that support the production process in a facility are present here. Web servers, file servers, print servers, business workstations, email clients are a few of the types of systems found in this level. Active Directory networks are also implemented in this level. These systems send production information to corporate systems, such as uptime and units produced, and they collect orders and business data from corporate systems to disseminate to OT and ICS systems.
Initially, this level was not present in the original design. Introduction of the IDMZ to segment IT networks from OT networks was due to the convergence of both over the years. IDMZ relays communications between the IT and OT networks and closely inspects the network traffic flow.
Systems that provide monitoring, supervisory, and operational support for a site or region are present here. Site operators interact with the HMI to perform tasks that affect the plant or industry. This is also where the OT systems live that report back to the IT systems. Systems found here typically include HMI servers, Microsoft Domain Controllers, file and web servers, etc.
The devices in this level target monitoring and supervisory control for a single process. Isolation of processes from one another is paramount. Level 2 functions are mostly the same as Level 3 but targets a smaller area of the overall architecture. Systems found in this level typically include HMI clients, Supervisory control systems, alarm servers, etc.
All controlling equipment are present in level 1. The devices and systems present in this level provide automated control of a process. Tasks performed by Level 1 devices are opening valves, starting motors, etc. Devices found in level 1 include PLCs, PIDs, etc.
The actual process occurs in level 0. The devices in this level are also known as Equipment Under Control (EUC). We can find sensors, pumps, motors and valves in level 0. It is important that things go without disruption in this level as that can cause serious consequences for operations.
Levels 5-4 come under the Enterprise zone (IT), and levels 3-0 under the Industrial zone (OT). There was a clear separation and a strong barrier between OT and IT in the early days of ICS. But that line has all but vanished during the last decade. From a security standpoint, one major way IT systems differ from OT systems is on the way they are protected. We are going to take a look at this from the CIA triad viewpoint.
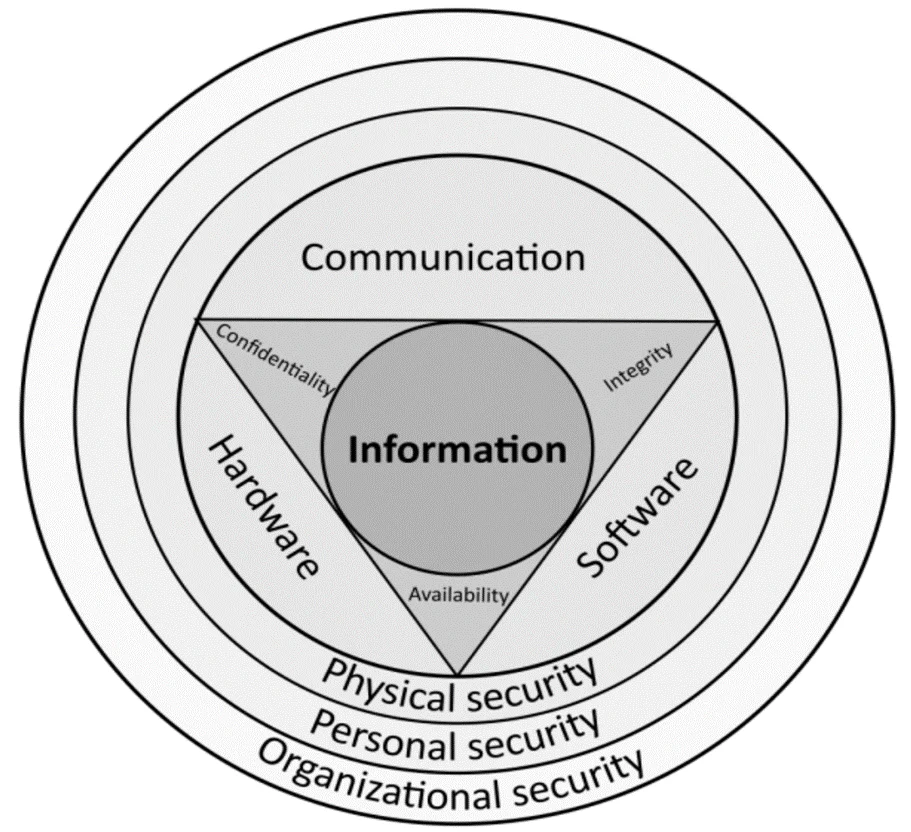
Generally, for IT systems, confidentiality is the most important factor to secure, followed by integrity and the least important asset is availability. With OT systems, availability is the most important concern of the owners of an OT system, followed by integrity, and finally confidentiality. Due to this difference, it’s imperative to have a strict segmentation between OT and IT networks while still allowing for the communication of critical data between them.
In this blog, we have gone through the differences between IT and OT, the Purdue reference model, and the need for OT security. We’ll be delving more into OT/ICS security in upcoming blogs.
By partnering with Redfox Security, you’ll get the best security and technical skills required to execute an effective and thorough penetration test. Our offensive security experts have years of experience assisting organizations in protecting their digital assets through penetration testing services. To schedule a call with one of our technical specialists, call 1-800-917-0850 now.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“