
Deep links are a powerful tool for enhancing user experience in Android applications. They allow users to navigate directly to specific content within an app, bypassing the need to navigate multiple screens. However, this convenience comes with a vulnerability that malicious actors can exploit. This blog will explore the potential risks associated with deep links and provide practical strategies to protect your Android app from exploitation.
Deep links are URLs specifically designed to open a particular activity within an app. They can be triggered from various sources, such as web pages, push notifications, or other apps. In Android can be classified into Scheme URLs, App Links, and Intent URLs. Scheme URLs were the initial implementation and allowed any app to register a custom scheme, host, and path. This lack of validation opens the door for link hijacking, where a malicious app intercepts links intended for another app.
App Links, introduced in Android 6.0, added a layer of security by restricting deep links to HTTP or HTTPS URLs. However, misconfigurations and improper verification processes can still leave apps vulnerable to link hijacking and data interception. Intent URLs are the least common type of deep links but provide an extra layer of protection by explicitly specifying the target app’s package name.This prevents link hijacking and ensures the app opens the directly without user intervention.
Deep links can expose your app to various risks and exploitations if not properly secured. Let’s explore some of the common vulnerabilities and their potential impacts.
Link hijacking occurs when a malicious app intercepts deep links intended for another app. This can lead to phishing attacks where users are tricked into entering sensitive information on a fraudulent login screen. For example, a user may install a game app that registers a deep link similar to a banking app’s deep link. When the user clicks on a legitimate deep link from their bank, the malicious game app intercepts it and displays a fake login screen to steal their credentials.
Deep links can transmit sensitive data, such as authentication tokens. If the deep link is not properly secured, an attacker can intercept this data and gain unauthorized access to the user’s account. For example, an app that uses deep links to communicate authentication tokens may be vulnerable to data interception if the deep link is hijacked.
Improperly implemented deep links can lead to traffic hijacking, where apps register schemes associated with popular apps to redirect users to their apps. This can result in a loss of traffic and potential revenue for the legitimate app.
Apps can register deep links associated with competitors to divert users to their apps. This unethical practice can harm the reputation and user experience of the targeted app.
Deep links can be exploited to access arbitrary components within an app. This can lead to unauthorized access to sensitive data or the execution of malicious actions.
Some apps handle deep links before local authentication, which can lead to a bypass of security measures such as passcodes or biometrics. Attackers can exploit this vulnerability to access certain app functionalities directly without going through the proper authentication process.
Deep links often allow users to provide local actions or API request parameters. If these parameters are not properly validated, an attacker can manipulate them to perform unauthorized actions or exploit vulnerabilities within the app.
In this demonstration, we will use AllSafe application. It is an intentionally vulnerable Android application that helps beginners explore some vulnerabilities in Mobile Applications.
Open the apk file in jadx. Click on the AndroidManifest.xml file
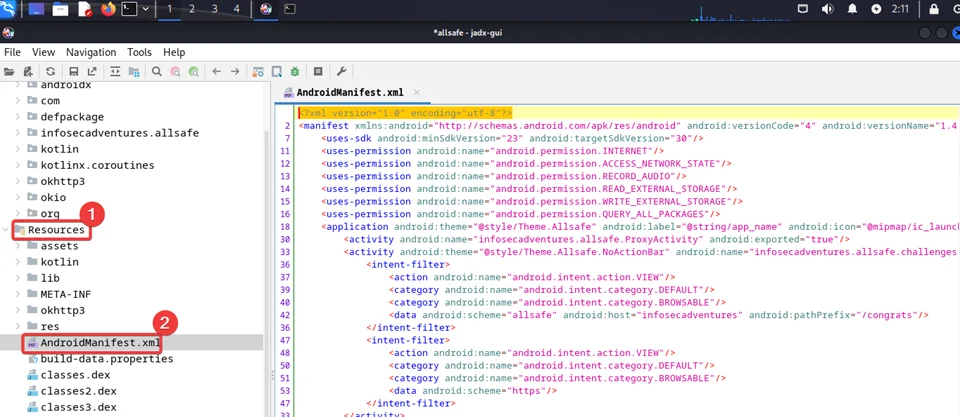
In the next step, press Control + F to open the search box and look for “android:scheme”. The reason we are searching for android:scheme is that minimum, the <data> tag must include the android:scheme attribute.
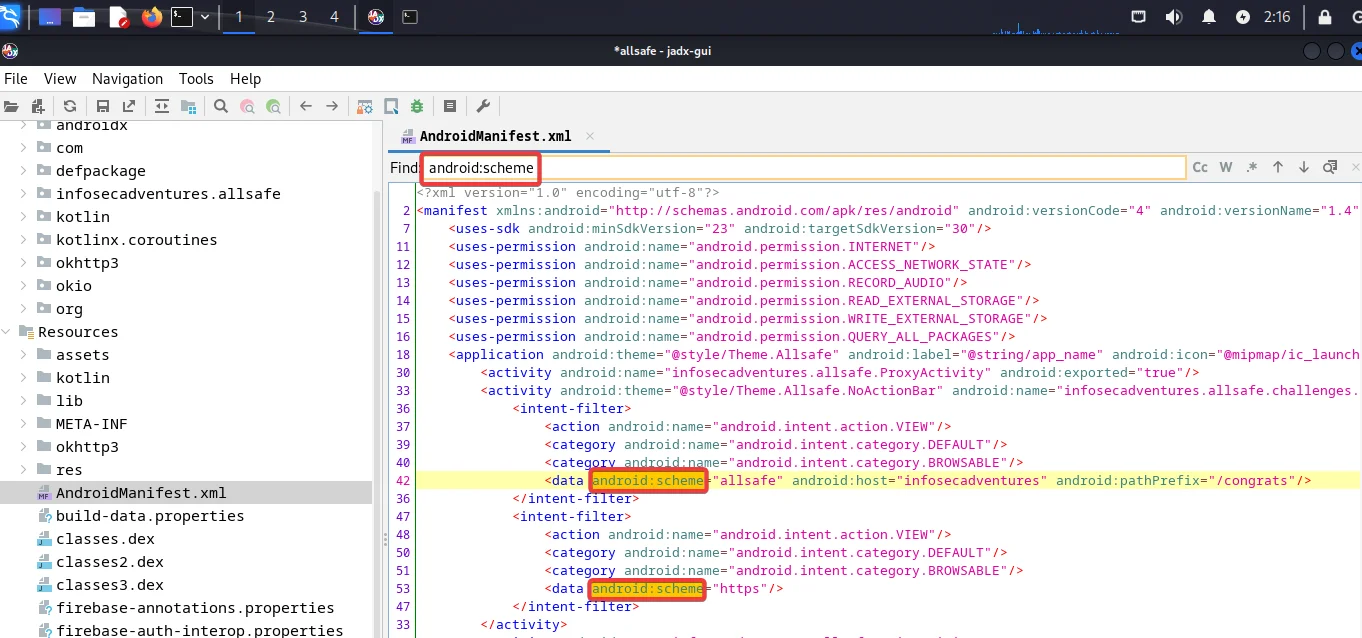
To address this challenge, we can resolve it by pinpointing the specific scheme associated with the application’s registration. As depicted in the screenshot above, the application has revealed the existence of two distinct schemes (allsafe:// and https://).
Understand the code:
Double click on the infosecadventures.allsafe.challenges.DeepLinkTask.
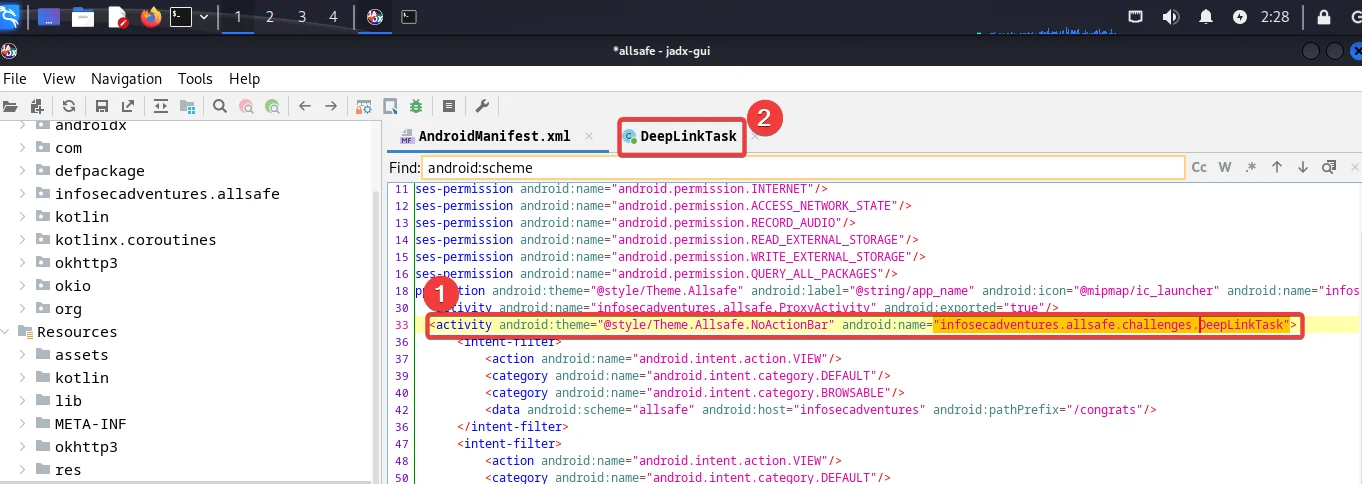
Navigate to the Deep Link File. Upon examining the code, it becomes evident that the intent’s data validation is contingent on the presence of a parameter labeled “key” and a corresponding comparison to a value stored in strings.xml, which is also labeled “key.” Our primary objective is to ensure that this “if” condition yields a true result. Therefore, prior to initiating any exploitation, our initial step is to obtain the “key” value, which is conspicuously stored within strings.xml.
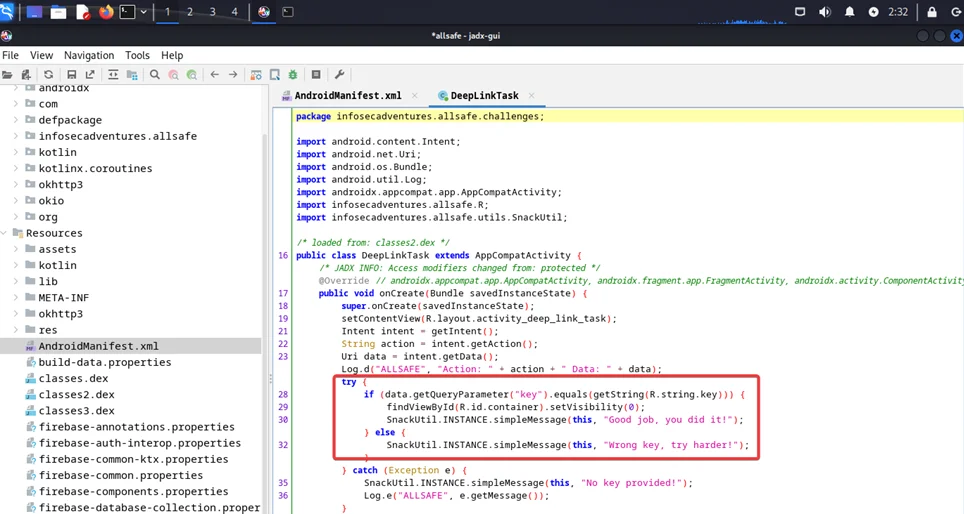
Now, navigate to the resource. arsc folder, under res, by clicking on values and open the strings.xml file
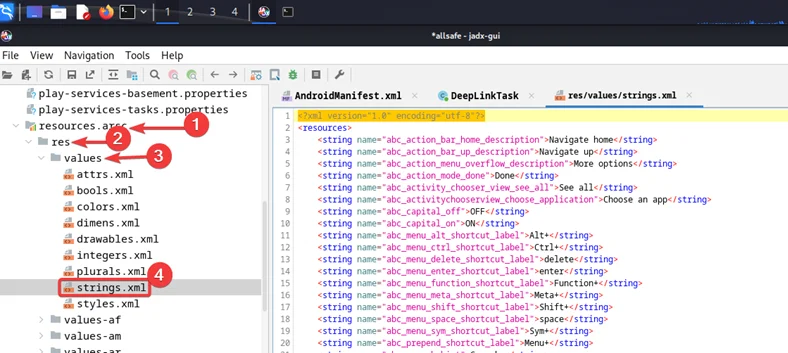
Now, for the next step, activate the search box and input “Key.” As you can see, we have successfully retrieved the “key”.
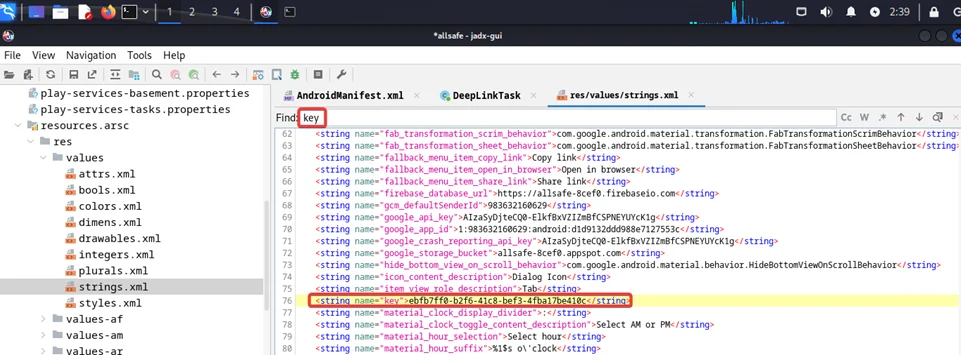
In the first scheme, you can notice that the Scheme is “allsafe”, the Host is “Infosecadventures,” and the PrefixPath is “/congrats.”
So, the link will be: allsafe://infosecadeventures/congrats?key=ebfb7ff0-b2f6–41c8-bef3–4fba17be410c
In the second scheme, only one attribute is called the scheme, meaning that no host or path is mandatory for opening the deep link in the Allsafe application.
So, the link will look something like this: https://<any URL>?key=ebfb7ff0-b2f6–41c8-bef3–4fba17be410c
We can use the adb (Android Debug Bridge) tool to exploit this vulnerability:
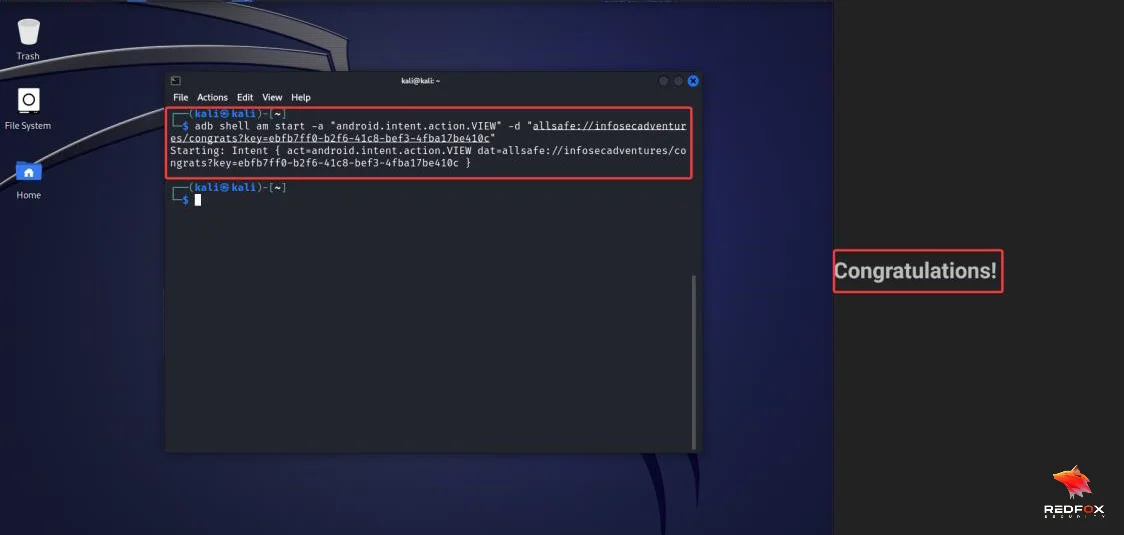
adb shell is start -a "android.intent.action.VIEW" -d "allsafe://infosecadventures/congrats?key=ebfb7ff0-b2f6-41c8-bef3-4fba17be410c"
Note: Before running the command open the emulator and headover to Deep Link exploitation challenge section.
b) After executing the command, you can see we have successfully exploited the Deep Link.
c) We’ve identified two schemes, but so far, we’ve only utilized the first one.
d) Let’s now focus on exploiting the second scheme, which we mentioned earlier.
https://<any URL>?key=ebfb7ff0-b2f6–41c8-bef3–4fba17be410c
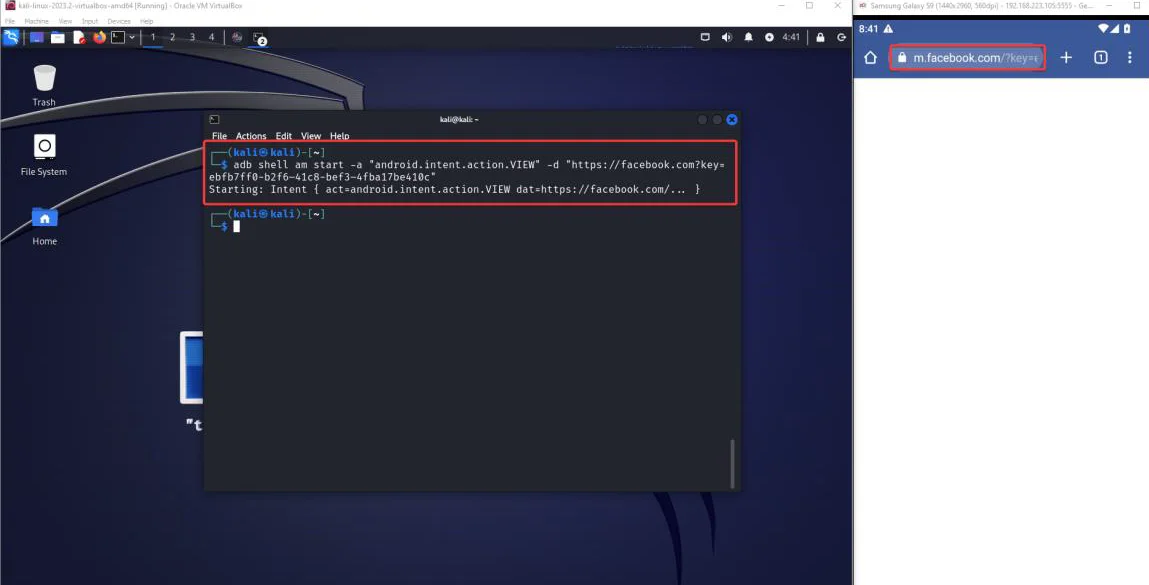
e) Rather than using any URL, we’re incorporating facebook.com. The final URL will look like the following:
adb shell am start -a "android.intent.action.VIEW" -d
f) Now, execute this command in the same manner as before.
Now that we understand the potential risks associated with deep links let’s explore some best practices for securing them and protecting your Android app.
It is crucial to implement proper validation and verification processes for deep links to prevent link hijacking. Use a secure verification mechanism, such as App Link Association. This involves hosting a Digital Asset Links JSON file on your website and declaring the relationship between your website and intent filters in your app’s manifest.
Consider using Intent URLs instead of Scheme URLs or App Links for enhanced security. Intent URLs explicitly specify the target app’s package name, eliminating the possibility of link hijacking. By using Intent URLs, you can ensure that your app directly handles the deep link without any user intervention.
Implement proper input validation for deep link parameters to mitigate the risk of arbitrary component access and insecure parameter handling. Validate and sanitize all user-provided input to prevent malicious actions or unauthorized access to sensitive data.
To prevent bypassing local authentication, ensure that deep links are handled only after proper app-specific authentication. This ensures that users are authenticated before accessing sensitive functionalities or performing critical actions.
If your app transmits sensitive data via deep links, ensure that the data is encrypted and protected. Use secure communication protocols such as HTTPS to prevent data interception and implement additional encryption measures if necessary.
Perform regular security testing and vulnerability assessments to identify weaknesses or vulnerabilities in your app’s deep link implementation. Use penetration testing tools and techniques to simulate real-world attacks and address security gaps.
Educate your users about the potential risks of deep links and how to identify legitimate ones. Provide clear instructions on verifying the authenticity of deep links and encourage users to report any suspicious activities.
Deep links can greatly enhance the user experience in your Android app, but they also introduce potential security risks. By implementing proper validation, verification, and security measures, you can protect your app from exploitation and ensure the safety of your users’ data. Stay proactive in monitoring and addressing any vulnerabilities, and regularly update your app to incorporate the latest security practices.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems, and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“